Peep-proof password device and password peep-proof method
A cipher device and password technology, applied in the field of cipher devices, can solve the problems of operation risk, password easy to be stolen by prying eyes, password peeping and theft, etc., and achieve the effect of reducing risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
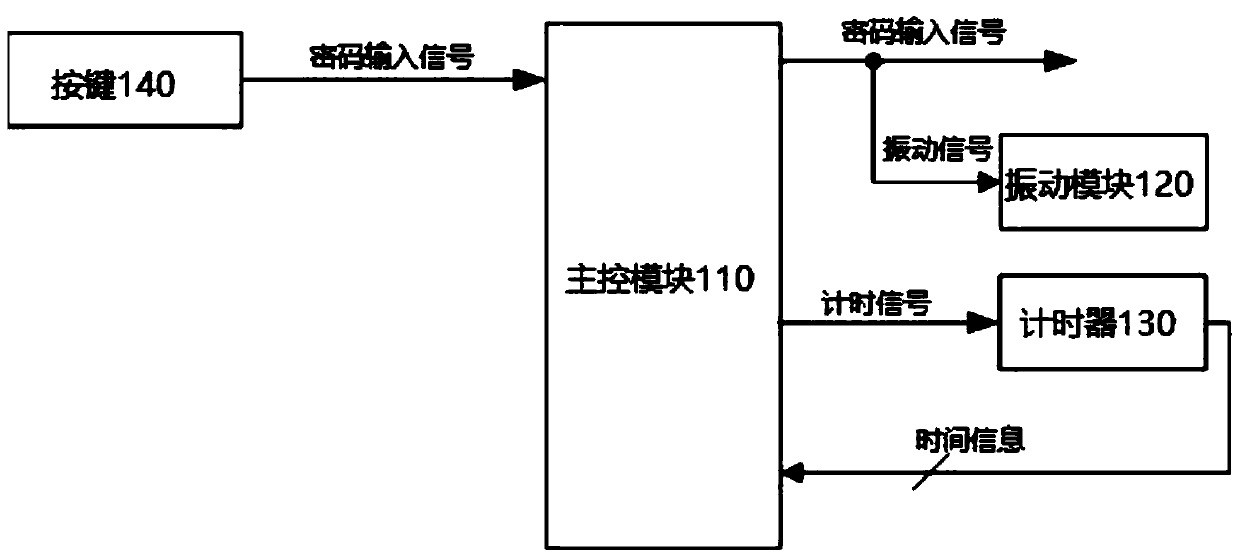
[0023] see figure 1 , figure 1 It is a schematic circuit diagram of an anti-peeping cipher provided by an embodiment of the present application.
[0024] The application provides an anti-peeping cipher, including: a main control circuit 110, a vibration module 120 and a timer 130, and the main control circuit 110, the vibration module 120 and the timer 130 are all arranged on the cipher body (not shown in the figure). )internal.
[0025] Wherein, the main control circuit 110 receives the password input signal generated by the user operating the key 140, and controls the timer 130 to record the duration of the password input signal.
[0026] Specifically, the main control circuit 110 is electrically connected with the key 140 of the cipher body to receive the password input signal sent by the user operation (for example: pressing) the key 140 of the cipher body; When the main control circuit 110 receives the password input signal generated by the user through the operation b...
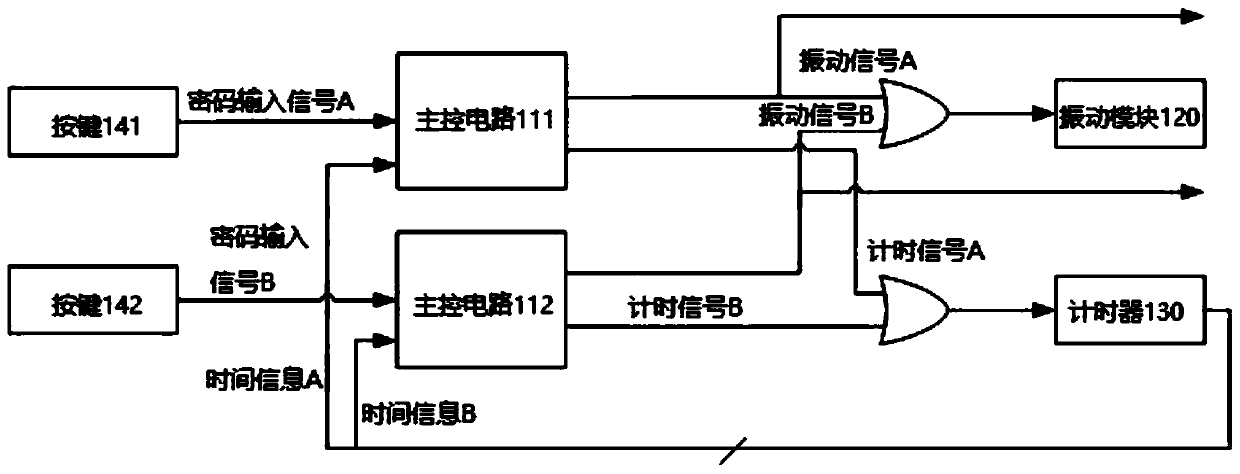
Embodiment 2
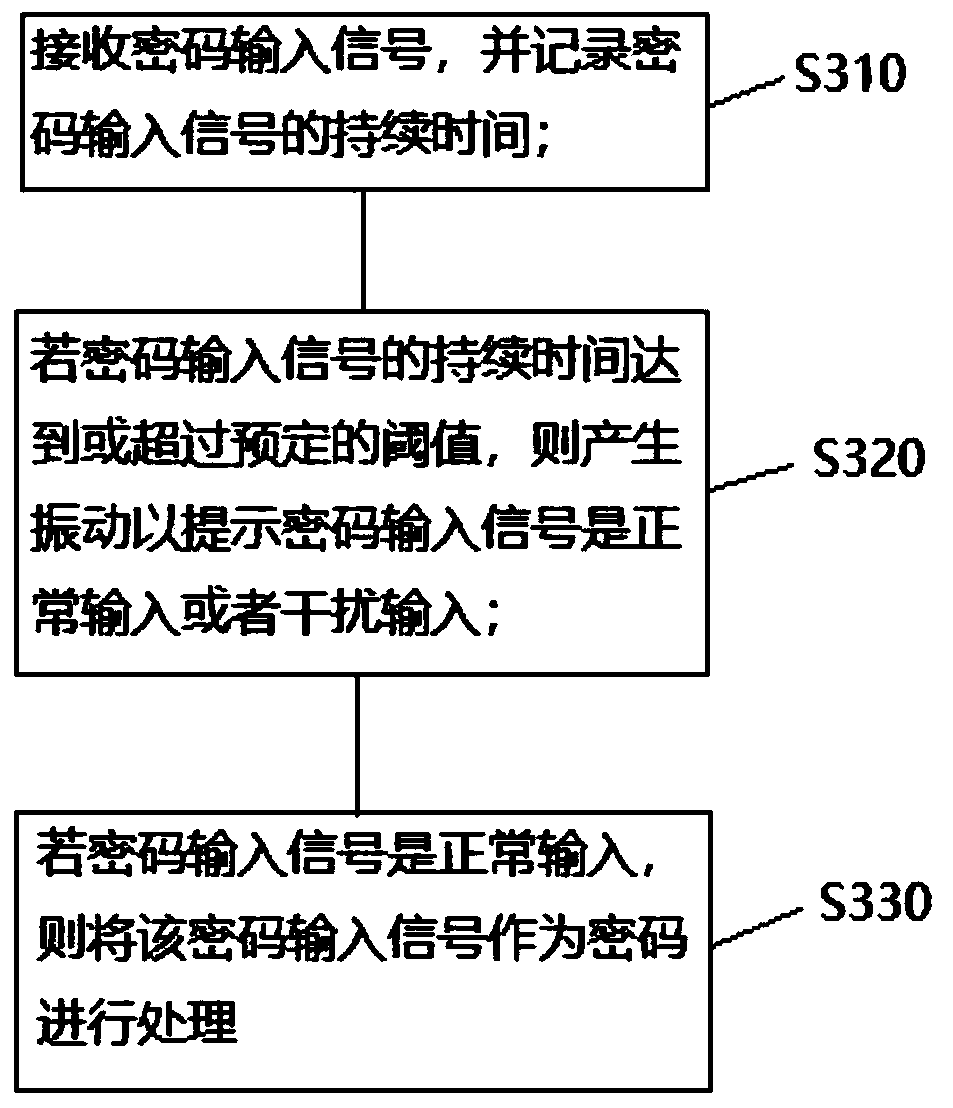
[0041] See image 3 , image 3 It is a flow chart of the password anti-peeping method provided by the implementation of this application.
[0042] The present application also provides a password anti-peeping method, including the following steps:
[0043] Step S310, receiving the password input signal, and recording the duration of the password input signal;
[0044] When the user presses the button of the cipher device, the button sends a password input signal to the main control circuit. After the main control circuit receives the password input signal, it sends a timing signal to the timer to reset the timer and start counting. Press the button, the timer stops counting.
[0045] On the basis of the above, after receiving the password input signal, the button sound of pressing the button starts to be issued, so as to prompt the user to press the button while disturbing the observation of the peeping person.
[0046] Step S320, if the duration of the password input sign...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com