An authentication method, device and storage medium
A technology of authentication request and authentication response, applied in the security field, can solve the problem of reducing the overhead of synchronization requirements, and achieve the effect of reducing the overhead of time and space, reducing the occupied bandwidth, and low time synchronization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
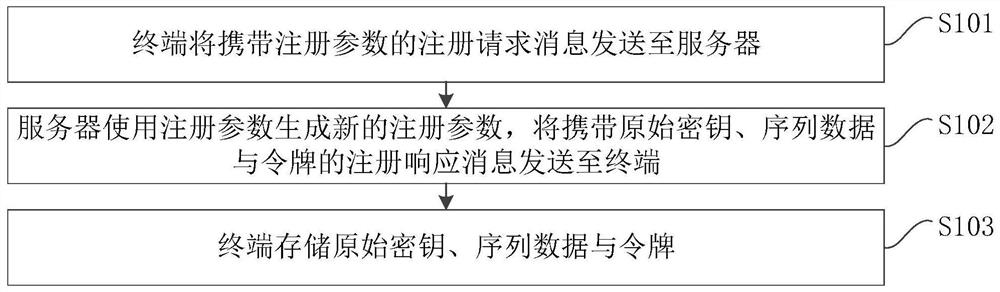
[0076] S101, the terminal sends a registration request message carrying the registration parameters to the server.
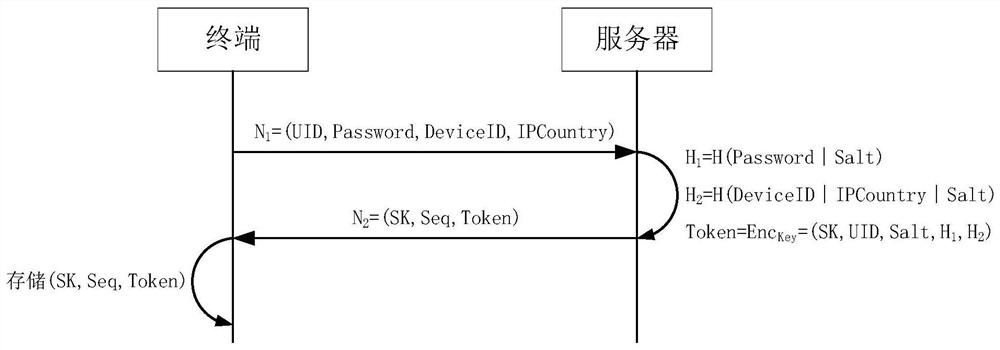
[0079] Wherein, the user identification UID is a piece of information that uniquely identifies the user, such as the user's ID.
[0080] The environment information is the information that identifies the authentication environment, for example, the device identification DeviceID used to represent the device environment
[0091] 3. The original key SK is randomly generated.
[0101] S103, the terminal stores the original key, sequence data and token.
Embodiment 2
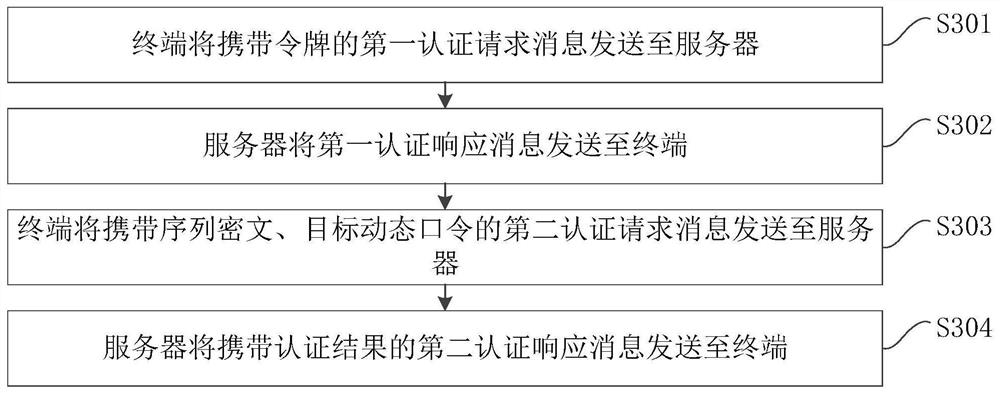
[0105] S301, the terminal sends the first authentication request message carrying the token to the server.
[0110] S302, the server sends the first authentication response message to the terminal.
[0115] The user identification UID in the first authentication request message can be compared with the user identification UID decrypted by the token Token
[0118] The safety parameter Salt and the second numerical value N
[0119] S303, the terminal sends the second authentication request message carrying the serial ciphertext and the target dynamic password to the server.
[0120] In this embodiment, after receiving the first authentication response message from the server, the terminal can extract the local
[0121] In one embodiment, the registration parameters include the user password password and / or contextual information (such as device identification
[0128] Determine the length L of the third hash value digest.
[0131] Convert the format of the second data Val to an unsig...
Embodiment 3
[0171] FIG. 5 is a flowchart of an authentication method provided in Embodiment 3 of the present invention, and this embodiment is applicable to
[0172] S501. Send the first authentication request message carrying the token to the server.
[0178] Send the first authentication request message to the server.
[0179] S502, receive the first authentication response message sent by the server.
[0184] Send the first authentication response message to the terminal.
[0185] S503, sending the second authentication request message carrying the serial ciphertext and the target dynamic password to the server.
[0187] In an embodiment, the first authentication request message includes a first value, a first reference time, and the first authentication
[0188] obtain user password password and / or environmental information;
[0192] The target dynamic password OTP and the sequence ciphertext Enc
[0193] The second authentication request message is sent to the server.
[0203] Derive usin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com