A method of srv6-based inter-domain source address verification
A source address and verification code technology, applied in the Internet field, can solve the problems of magnifying the scale of attacks, attacks, and the inability to judge whether the message has been tampered with, and achieve the effect of solving the problem of forgery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
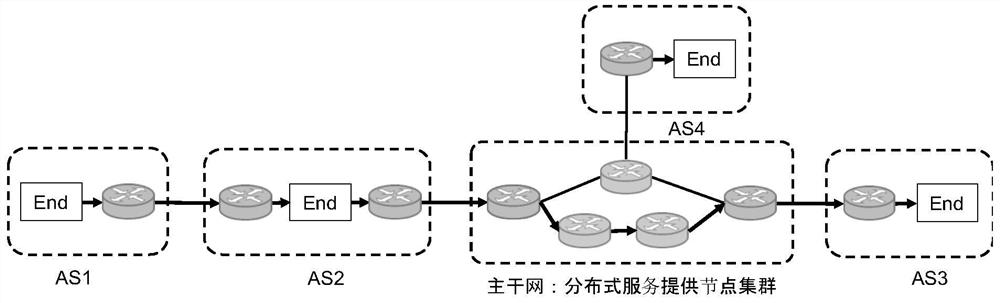
[0066]In the present invention, the source address verification service node needs to distribute the key for each trusted AS, requiring upgrades to support new Function: source address verification End.va. Request Source Address Verification Service AS boundary router and source address verification service node needs to enable SRV6.
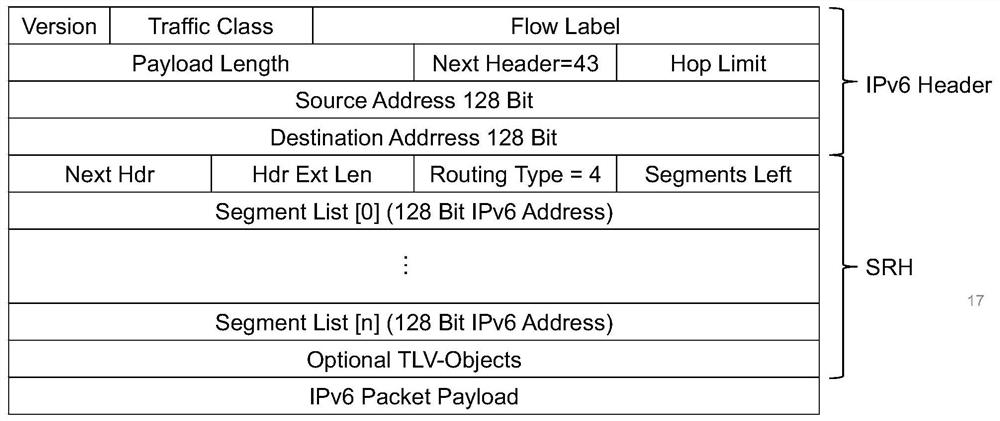
[0067]Take the flow from the AS1 to the AS3, the AS1 adds a SRH expanded head in the boundary router A1, and the SRH expansion head contains the position and service function of the service node that needs to be obtained. (Segment) For the source address verification service, you also need to add a verification code to the source address verification in the optional field of the SRH extension. The source site verification node of the main network checks the verification code to determine if the source address is true and whether the content is tampered.
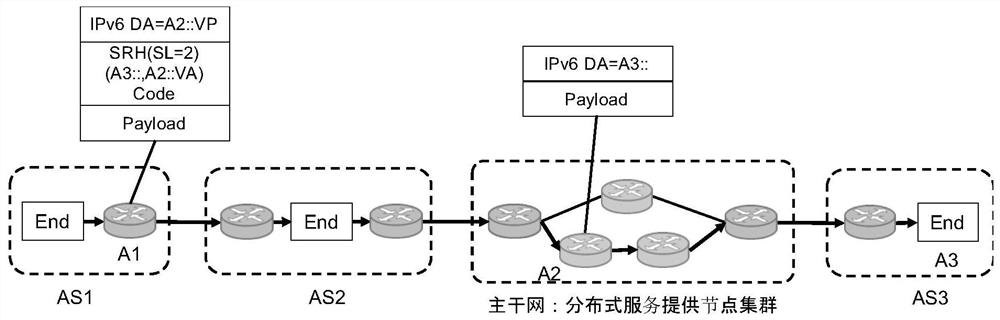
[0068]Such asimage 3 As shown, the SRH is added to the data packet from the A0 to A3 at A1. A2 is the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com