A Method of Preventing Differential Cryptanalysis Attacks
A cryptanalysis and differential technology, applied in the protection of internal/peripheral computer components, etc., can solve problems such as leakage of personal privacy information, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0026] This embodiment improves on the problem of difficulty in protecting encryption chips from differential cryptanalysis attacks, and innovatively implements an effective method for preventing differential cryptanalysis attacks through plaintext analysis.
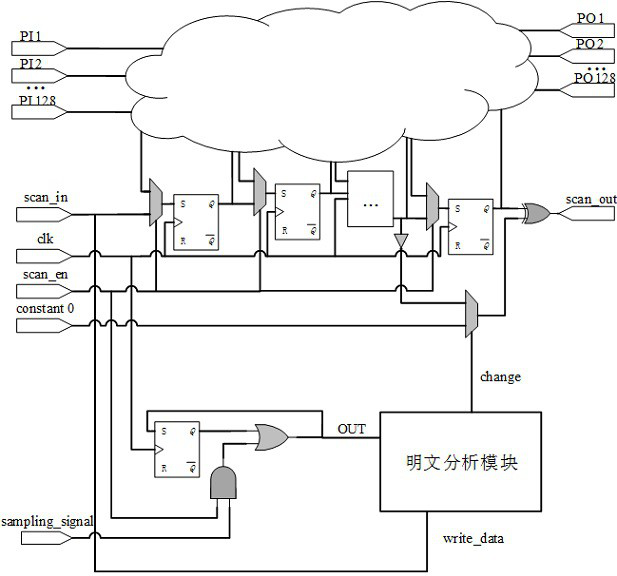
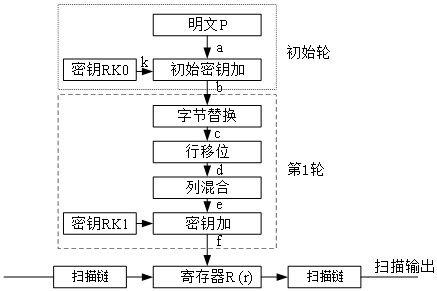
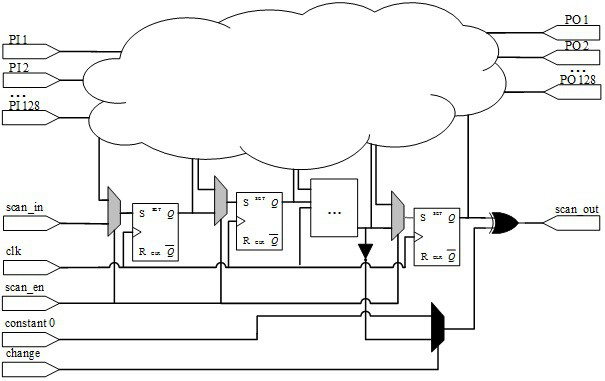
[0027] In order to prevent differential cryptanalysis attacks, a plaintext analysis module is proposed. When the chip is only running in the functional mode, the plaintext analysis module will not work to prevent additional power consumption. Once it is detected that the chip has entered the test mode, there is a threat of key information leakage. At this time, the plaintext analysis module starts to work. The three modules proposed in this embodiment are all modeled by verilog code and passed vcs verification. The overall block diagram of the design is as follows figure 1 As...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap