Content monitoring method, device, equipment and medium
A technology for content and display content, applied in the field of information security, can solve problems such as low accuracy, inability to accurately locate and analyze, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
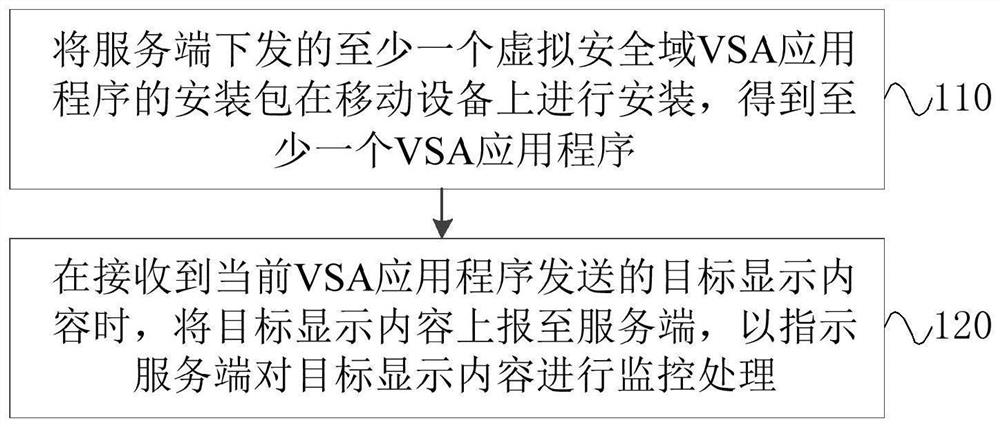
[0042] figure 1 It is a flow chart of a content monitoring method in Embodiment 1 of the present invention. The technical solution of this embodiment is applicable to the situation where the VSA application is managed through the mobile management platform. This method can be executed by a content monitoring device, and the device It can be implemented by software and / or hardware, and can be integrated in various general-purpose computer devices, specifically including the following steps:
[0043] Step 110, installing the installation package of at least one virtual security domain VSA application program delivered by the server on the mobile device to obtain at least one VSA application program;
[0044] Wherein, the VSA application program is used to monitor the set display content in the application program interface, and send the monitored display content to the mobile management platform.
[0045] In this embodiment, the virtual security area (Virtual Security Area, VSA...
Embodiment 2
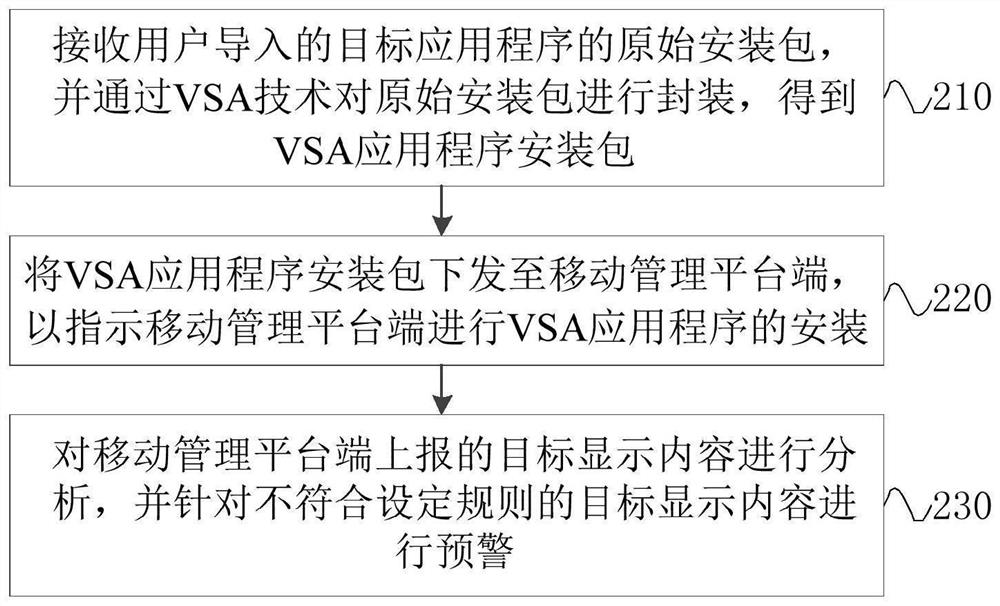
[0062] figure 2 It is a flow chart of a content monitoring method in Embodiment 2 of the present invention. The technical solution of this embodiment is applicable to the situation where the display content obtained by the VSA application program is analyzed and warned by the server. This method can be implemented by the content monitoring device Execution, the device can be implemented by software and / or hardware, and can be integrated in various general-purpose computer equipment, specifically including the following steps:
[0063] Step 210: Receive the original installation package of the target application program imported by the user, and encapsulate the original installation package through VSA technology to obtain a VSA application installation package.
[0064] In this embodiment, after receiving the original installation package of the target application imported by the user, the server encapsulates the original installation package through VSA technology to obtain ...
Embodiment 3
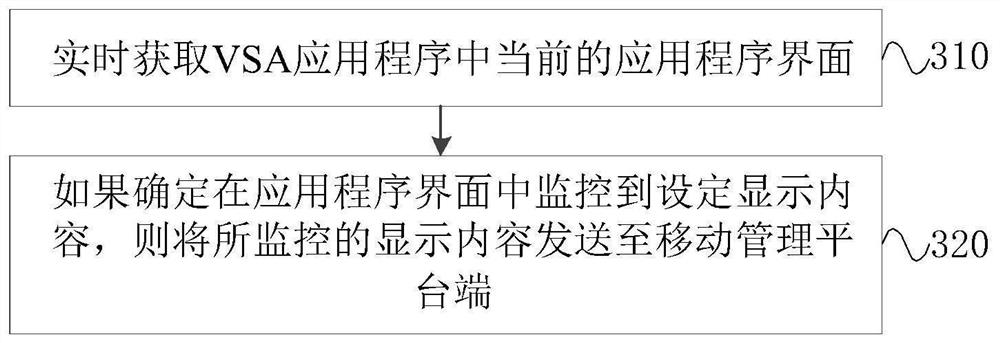
[0078] image 3 It is a flow chart of a content monitoring method in Embodiment 3 of the present invention. The technical solution of this embodiment is applicable to the situation of monitoring the content displayed by the application program through the VSA application program. The method can be executed by a content monitoring device, which can It is realized by software and / or hardware, and can be integrated in various general-purpose computer devices, specifically including the following steps:
[0079] Step 310, obtain the current application program interface in the VSA application program in real time.
[0080] In this embodiment, the VSA application program obtains the current application program interface in the VSA application program in real time during the running process, so as to monitor the display content of the current VSA application program. Among them, the VSA application program can be started after receiving the start instruction from the user, or it ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com