Encryption method for preventing application program from being reversely engineered
An application and reverse engineering technology, applied in the direction of program/content distribution protection, instruments, electrical digital data processing, etc., can solve the problems of AndroidApp theft, tampering, debugging, etc., to prevent log leakage, prevent dynamic debugging, prevent The effect of being backed up
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
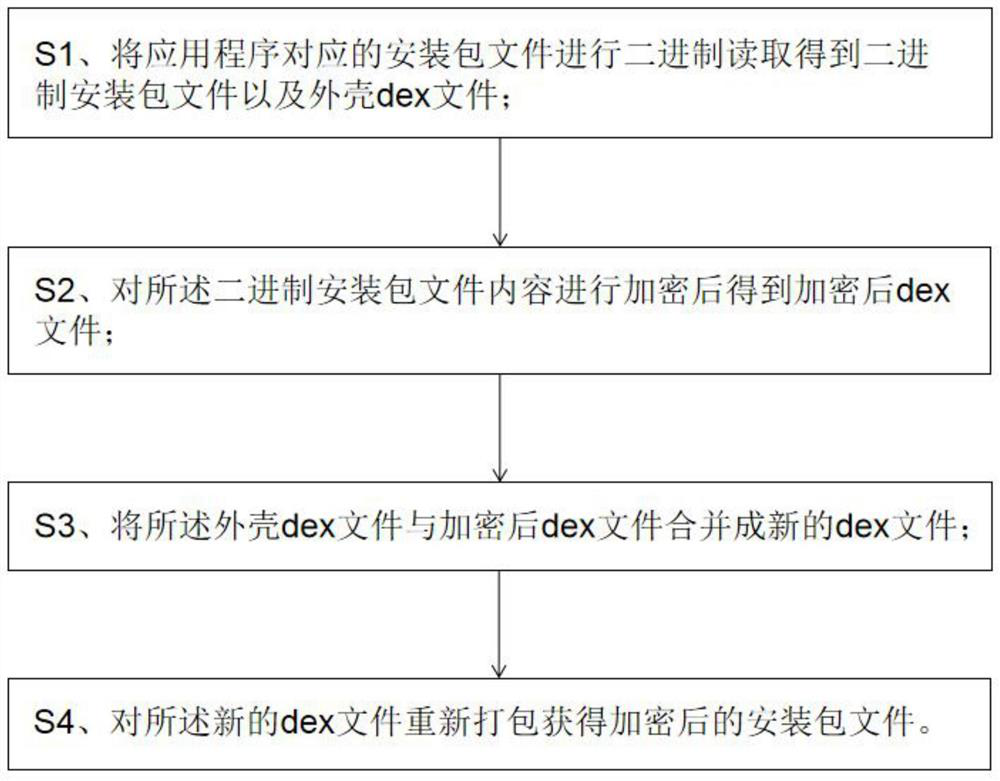
[0026] Embodiments of the present invention provide an encryption method for preventing applications from being reverse engineered, such as Figure 1-2 shown, including the following steps:
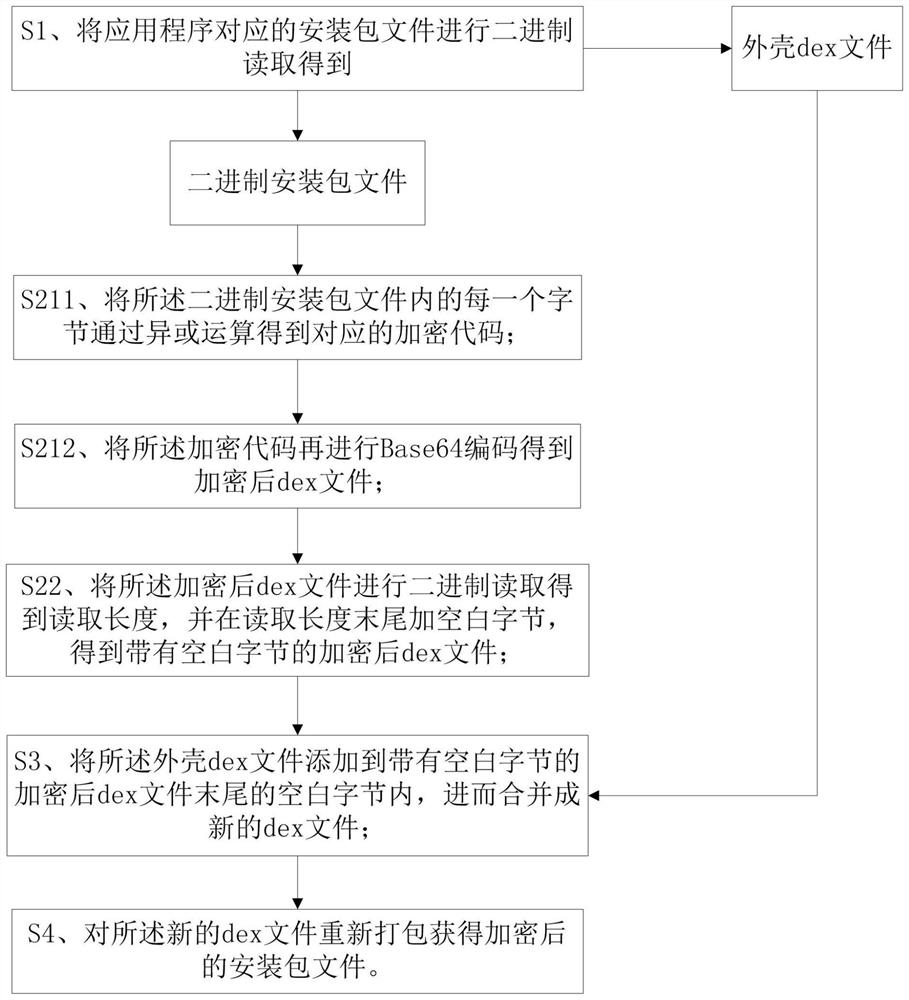
[0027] S1. Perform binary reading of the installation package file corresponding to the application program to obtain the binary installation package file and the shell dex file;
[0028] S2. Encrypting the content of the binary installation package file to obtain an encrypted dex file;
[0029] S3, merging the shell dex file and the encrypted dex file into a new dex file;
[0030] S4. Repackage the new dex file to obtain an encrypted installation package file.
[0031] In this way, the binary installation package file and the shell dex file are obtained by binary reading the unencrypted installation package file in the application, and the encrypted dex file is obtained after encrypting the contents of the binary installation package file; the encrypted shell dex file and the encrypted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com