A method and system for anonymous authentication of trust in decentralized mobile crowdsourcing
An anonymous authentication and decentralized technology, applied in the field of data processing, can solve the problems of anonymous trust authentication in mobile crowdsourcing systems, lack of data privacy protection related to node trust, and inability to prevent attackers from tracking node behavior, etc., to achieve high efficiency and protect trust Evaluate, protect node identity privacy, and ensure the effect of trusted execution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
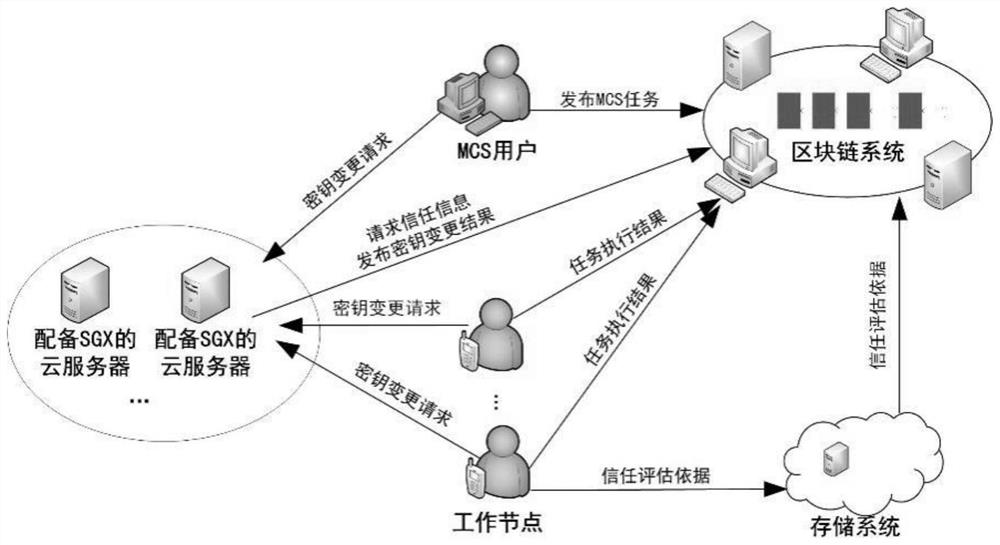
[0104] figure 2 It is a node (including mobile devices, personal computers, and servers), including mobile devices, personal computers, and servers, including mobile devices, personal computers, and servers, including mobile devices, personal computers, and servers. Connected together, mainly including five types of nodes, namely MCS users, operating nodes, miners, data storage nodes, and cloud servers configured to configure SGX. The user is a node that cannot complete the data collection task, so the mission is assigned to a set of mobile users (ie, the working node) using the MCS system to perform the task; the working node is the mobile device to complete the task as the data collection sensor. Users; miners jointly maintain the block chain system. In order to facilitate expression, the present invention uses BC = {B 0 , B 1 , ..., B k } Represents the block chain, where B i (0 ≤ i ≤ k) represents the i-th block of the block chain. The present invention uses the block chain t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com