Terminal registry security protection method and system based on windows driving technology
A security protection and registry technology, applied in computer security devices, platform integrity maintenance, instruments, etc., can solve problems such as failure to protect the registry, untimely protection of illegal host behavior, and inability to restrict malicious programs from modifying the registry. Timely interception to meet real-time effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The embodiments described below with reference to the accompanying drawings are exemplary and are only used to explain the present invention, but not to be construed as a limitation of the present invention.
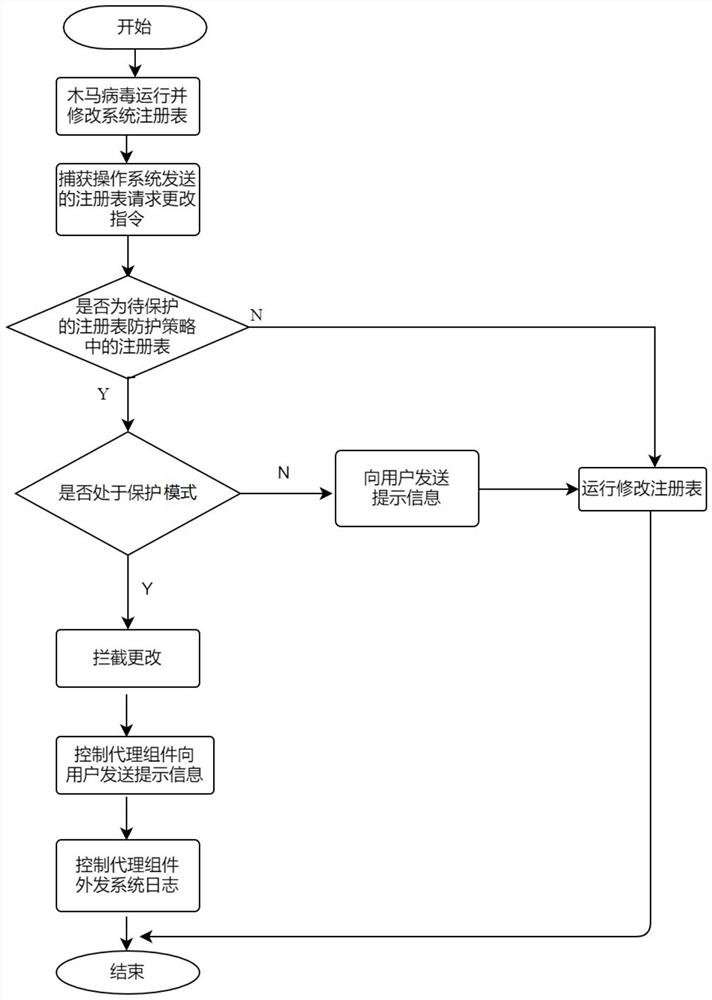
[0045] Embodiment of the present invention: as figure 1 As shown, a terminal registry security protection method based on windows driving technology is disclosed, including the following steps:
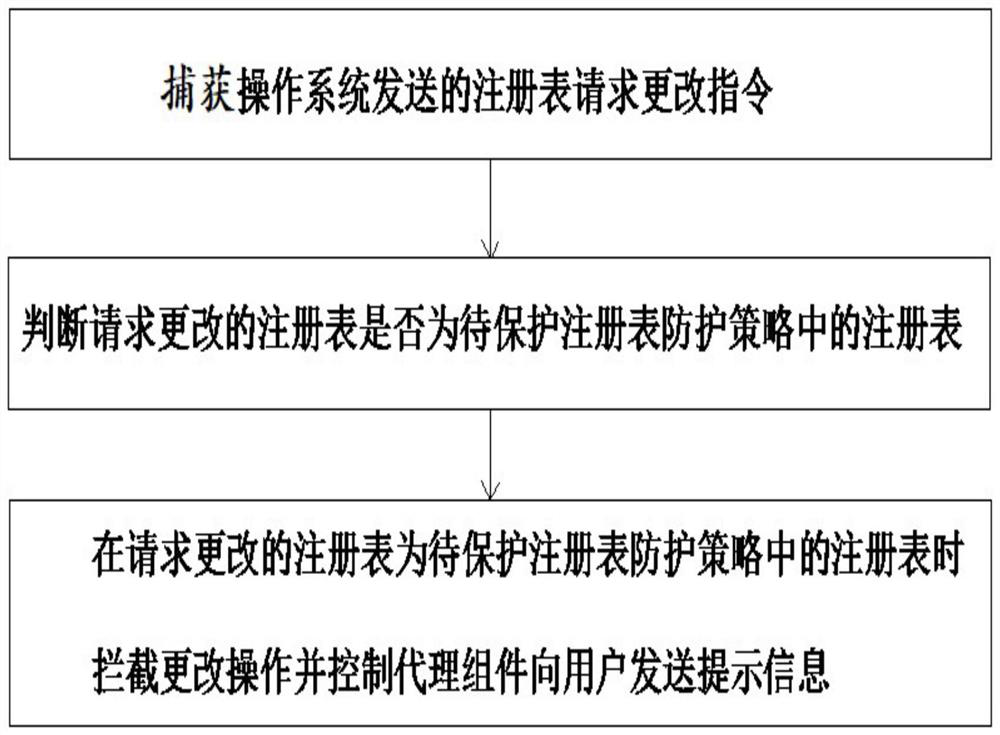
[0046] Capture registry request change instructions sent by the operating system;
[0047] Determine whether the registry requested to be changed is the registry in the registry protection policy to be protected;
[0048] Intercept the change operation and control the agent component to send a prompt message to the user when the requested registry is the registry to be protected in the registry protection policy.
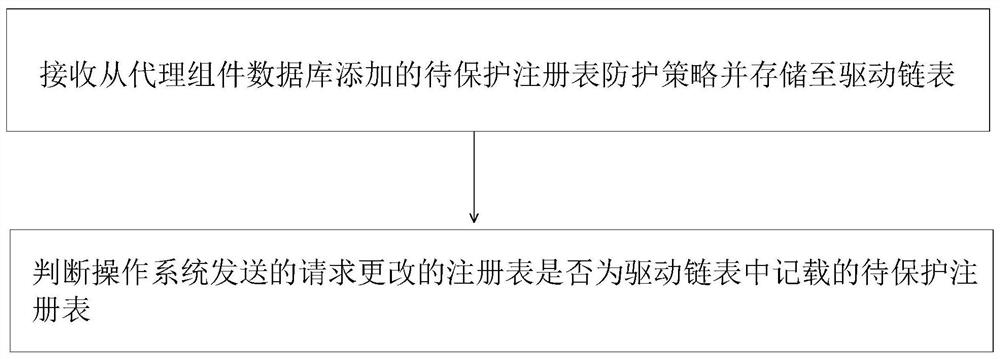
[0049] The operating system receives the request for changing the registry operation and sends the request to the receiving unit of the driver component, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com