Patents
Literature
64results about How to "Intercept in time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
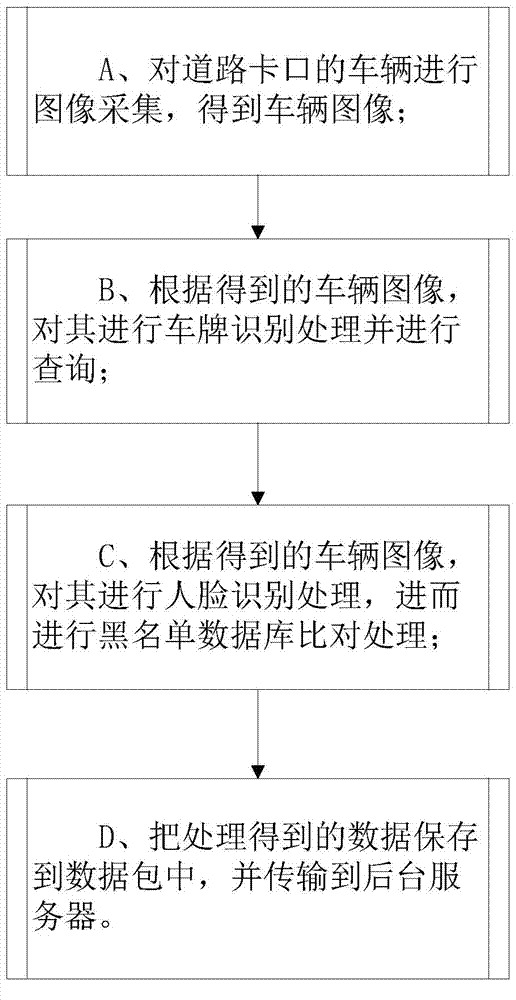
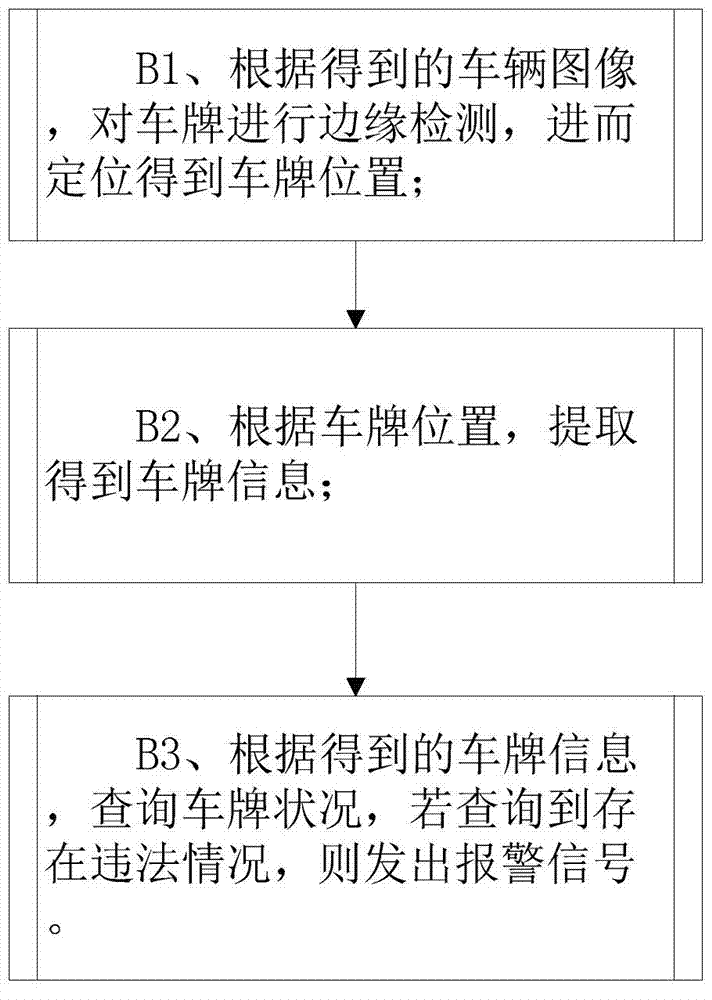
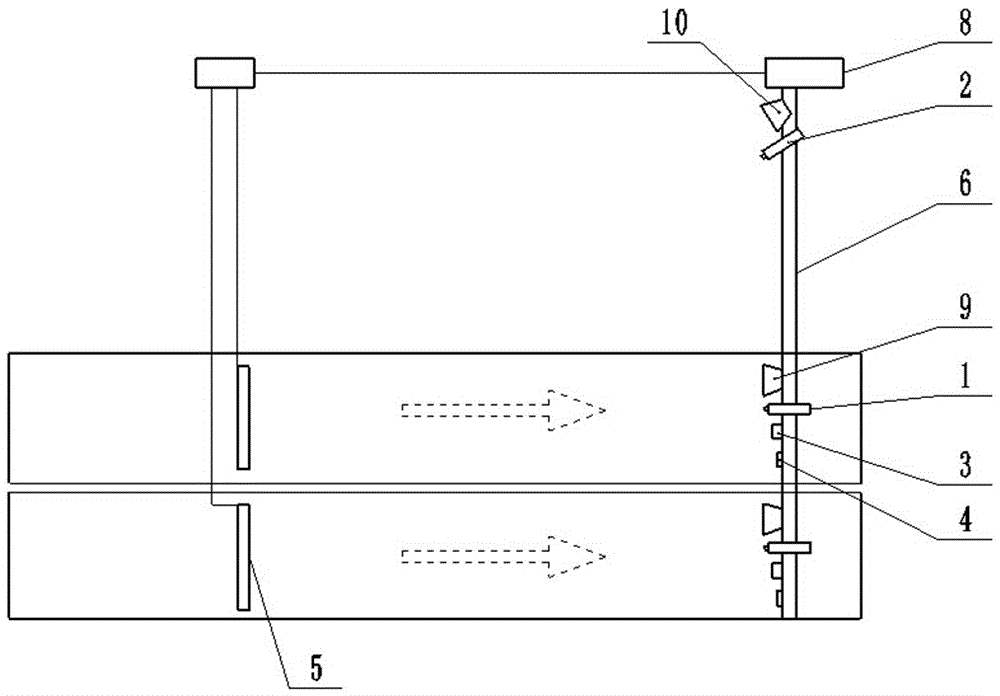
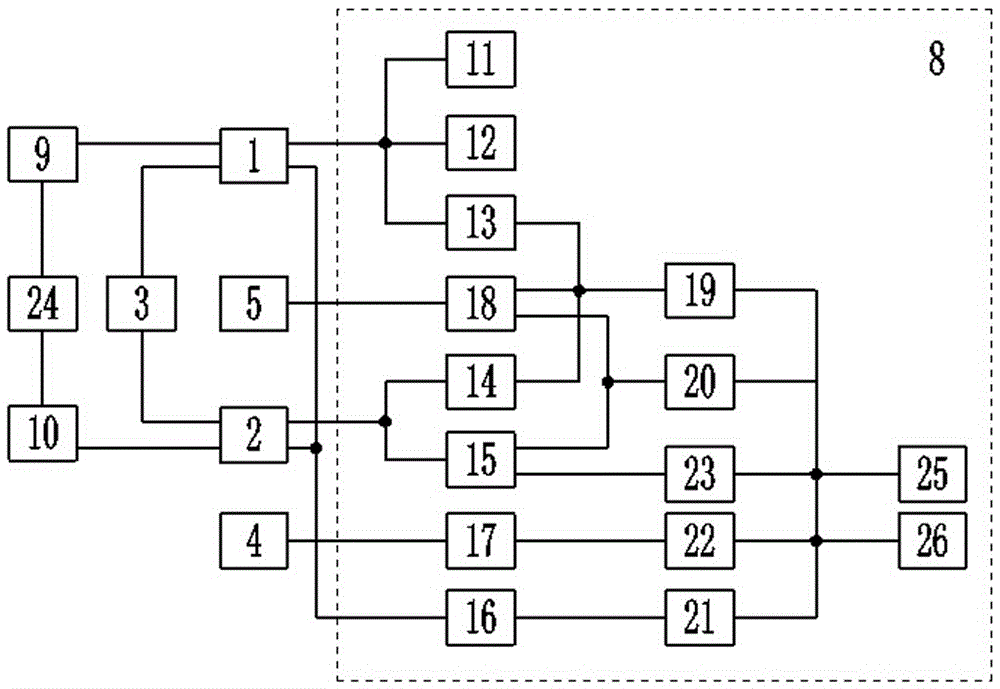
Road gate monitoring method and system based on human face recognition
InactiveCN103544481AIntercept in timeEasy to deployCharacter and pattern recognitionPattern recognitionNetwork packet
The invention discloses a road gate monitoring method and system based on human face recognition. The method comprises the steps that image collection is carried out on vehicles of a road gate to obtain vehicle images; according to the obtained vehicle images, vehicle license plate recognition processing is carried out on the vehicles, and query is carried out; according to the obtained vehicle images, human face recognition processing is carried out, and then blacklist database comparison processing is carried out; data obtained through processing are stored in a data package and are transmitted to a background server. The system comprises an image collecting module, a vehicle license plate recognition module, a human face recognition module and a storage module. According to the road gate monitoring method and system based on the human face recognition, suspicious personnel can be stopped in time, surveillance over the suspicious personnel by public security officers is facilitated, manpower and material resources are saved, and working efficiency is improved greatly. The road gate monitoring method and system based on the human face recognition can be widely applied to monitoring systems.
Owner:FIRS INTELLIGENT TECH SHENZHEN
Dynamic vehicle information collecting device
ActiveCN105719482ARealize automatic identificationIntercept in timeDetection of traffic movementEngineeringTraffic management
The invention relates to the technical field of vehicle information collection, in particular to a dynamic vehicle information collecting device which automatically recognizes various kinds of information of a normal-driving vehicle and monitors various illegal acts of the vehicle in a unified mode.The device comprises a capturing camera, a side face capturing camera, a speed measuring radar, a laser altimeter, a weight sensor and an intelligent terminal manager.The intelligent terminal manager comprises a vehicle license plate recognition module, a height recognition module, a weight recognition module, an overman module, an overload module, an overspeed module, an overheight module, a forbidding judging module, a photosensitive module, an alarm module and a display module.The dynamic vehicle information collecting device is mainly applied in the aspect of traffic management.
Owner:TAIYUAN GREAT TIMES TECH CO LTD
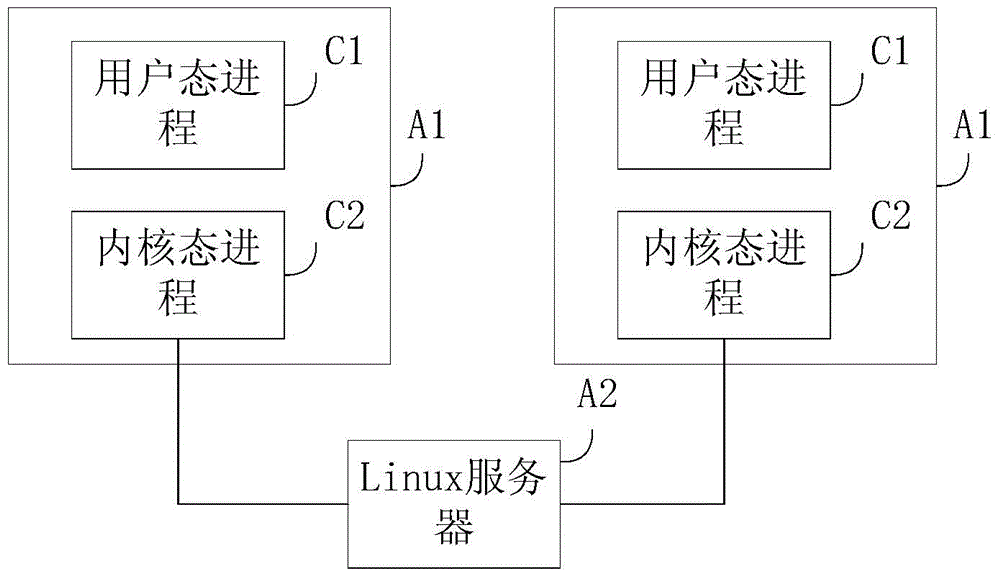
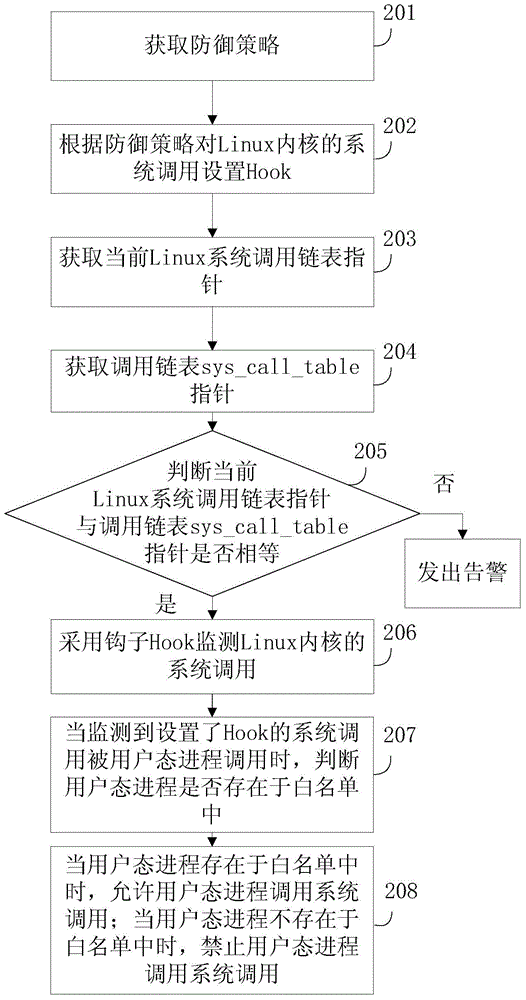
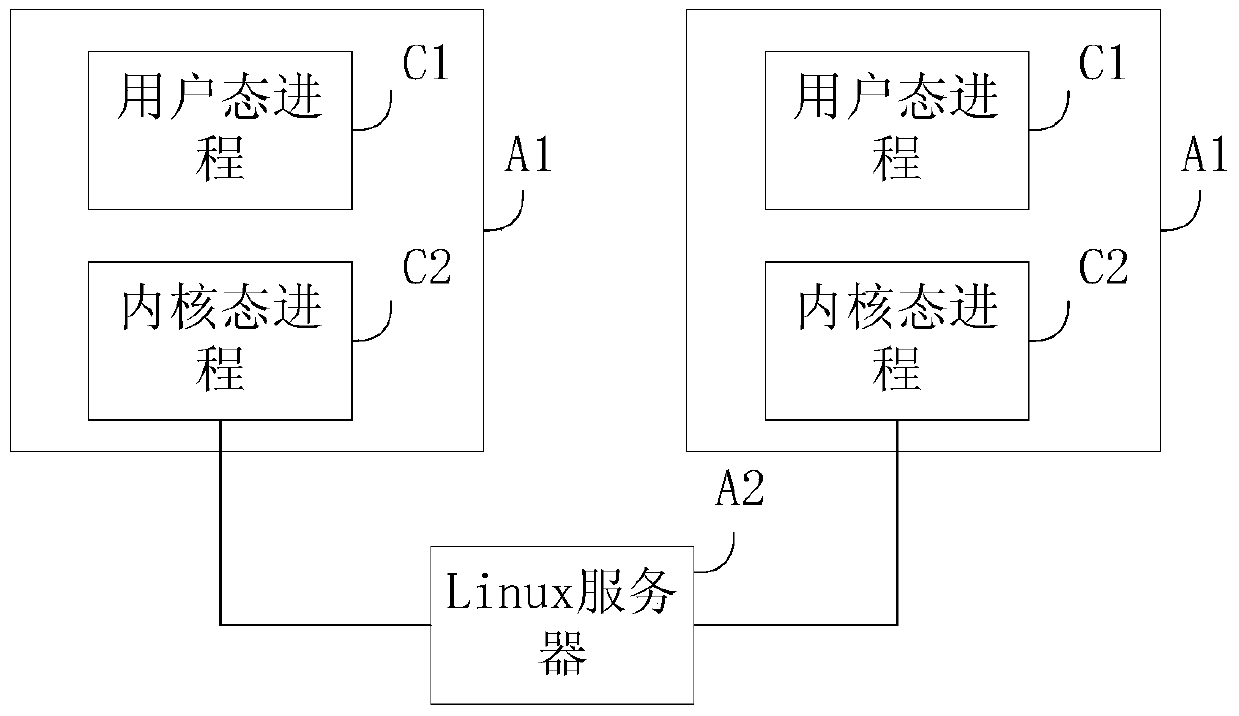
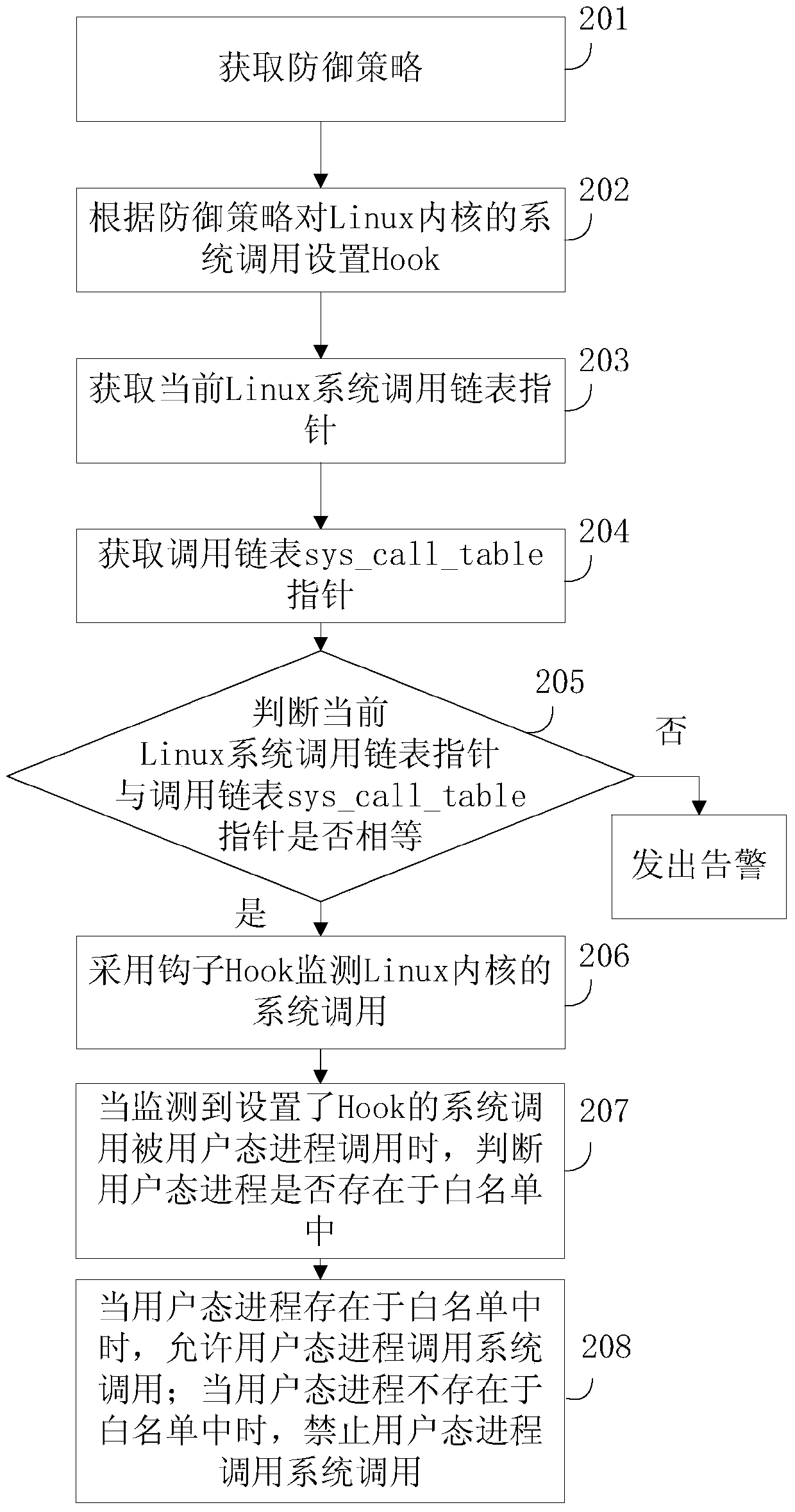
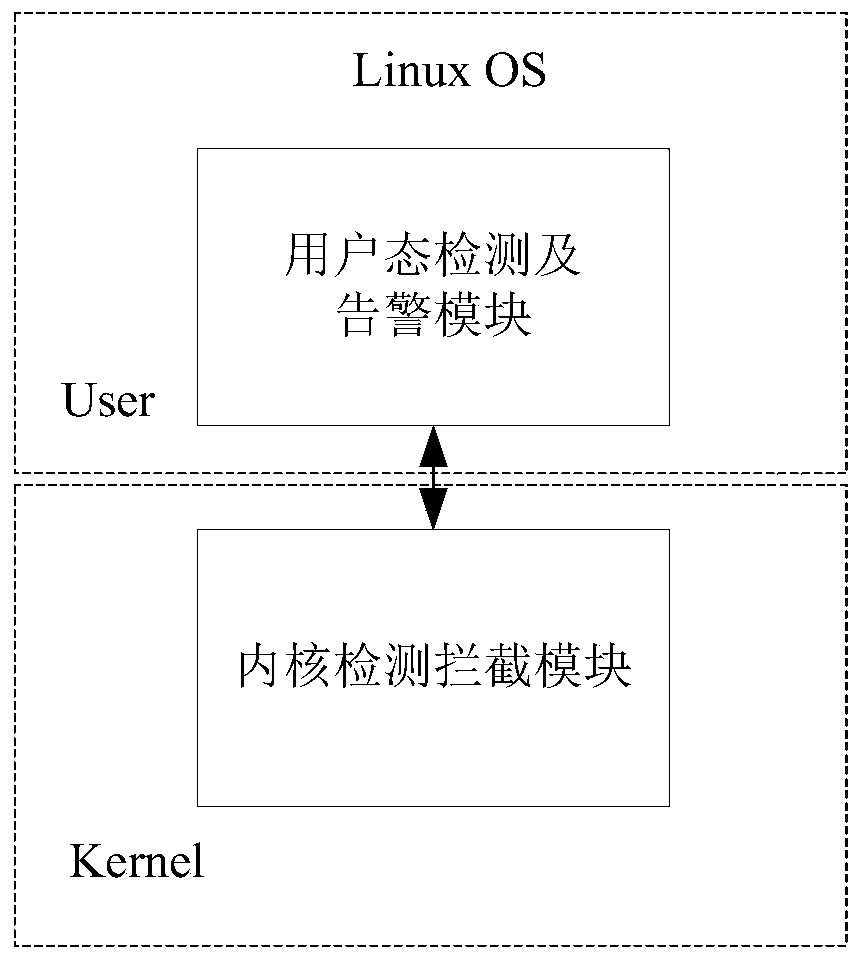
Active defense method and device based on Linux system
ActiveCN104008337AIntercept in timeEffective active defensePlatform integrity maintainanceGNU/LinuxSystem call
The invention discloses an active defense method and device based on a Linux system, and belongs to the field of system security. The method includes the steps that system call of a Linux kernel is monitored through a Hook; when it is monitored that the system call provided with the Hook is called by a user mode course, whether the user mode course exists in a white list or not is judged; when the user mode course exists in the white list, the user mode course is allowed to call the system call; when the user mode course does not exist in the white list, the user mode course is forbidden from calling the system call, wherein the white list comprises one or more user mode courses allowing execution of the system call. Running programs of the Linux system can be effectively detected, running malicious programs of the Linux system, back door Trojan horse programs and the like can be intercepted in time, and the active defense method is an effective active defense method based on the Linux system.
Owner:GUANGZHOU HUADUO NETWORK TECH
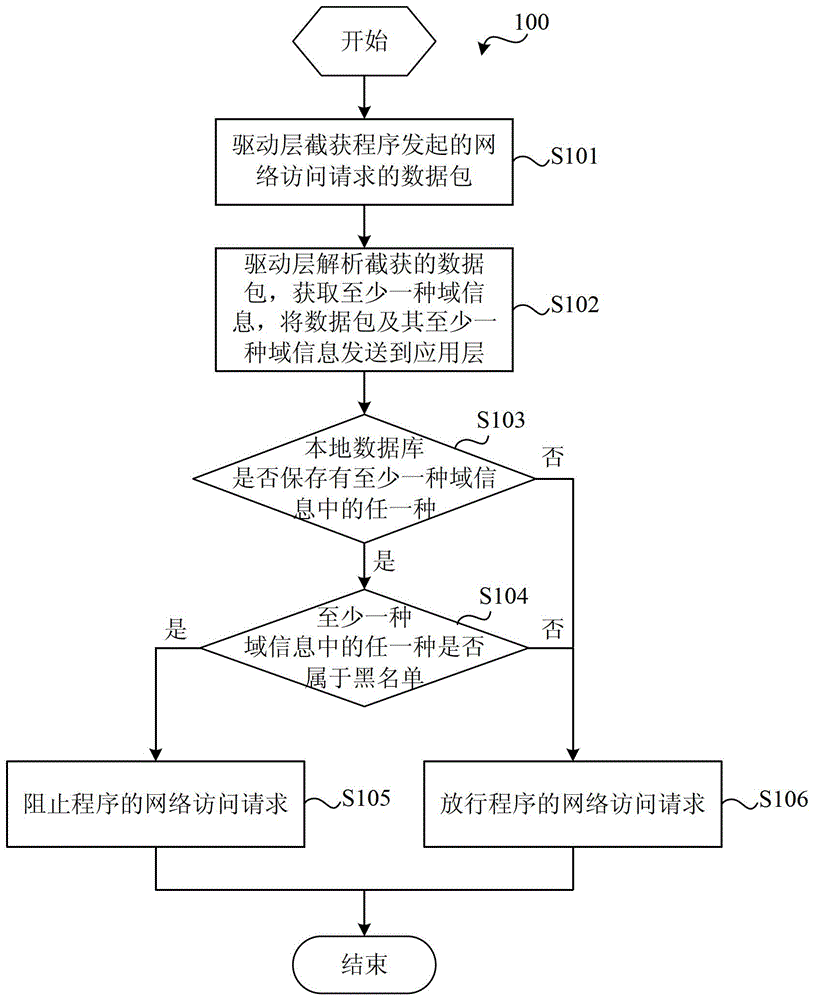
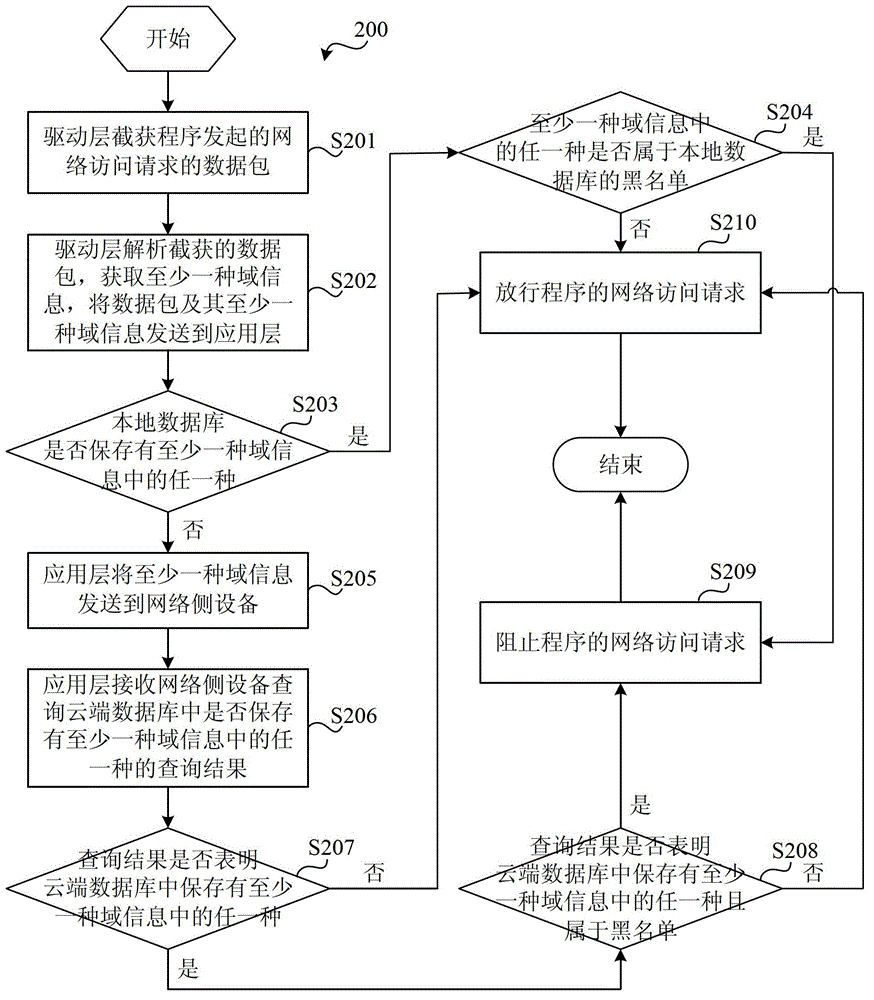
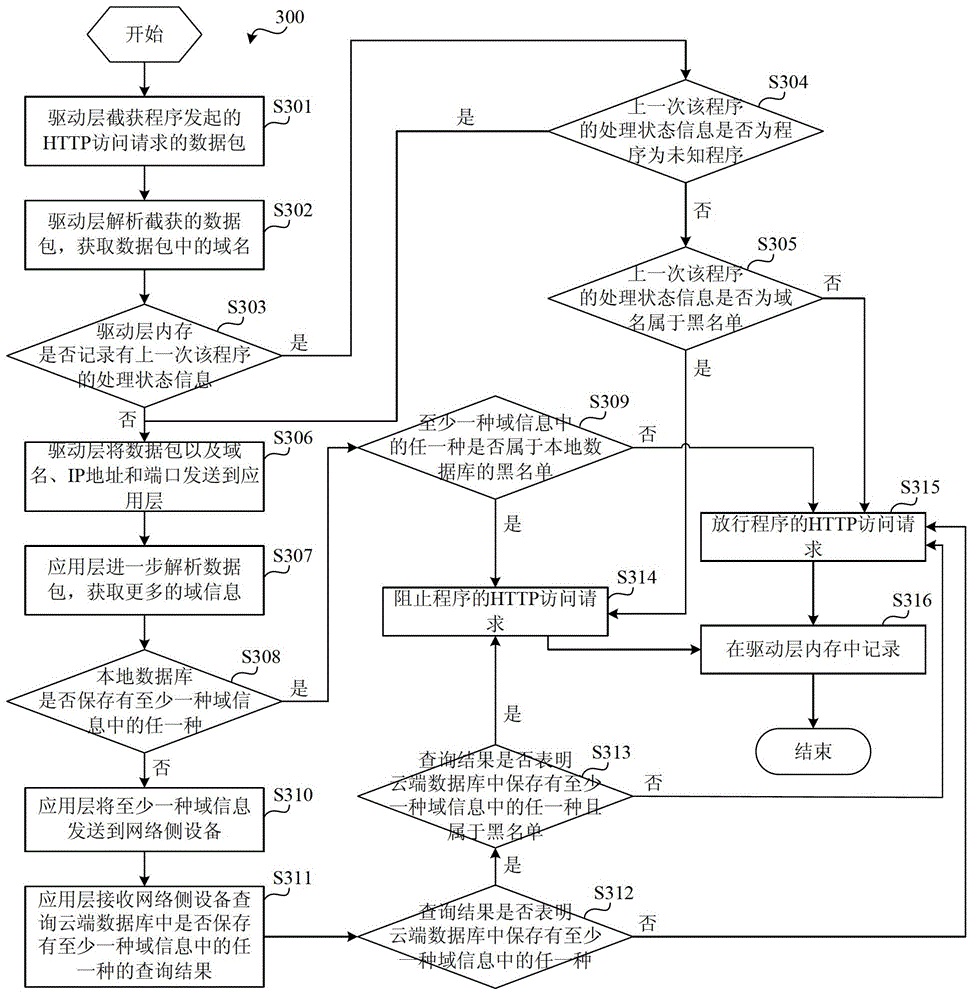
Protection system for network access behavior
The invention discloses a protection system for network access behavior. The system comprises a client device and a network side device; the client device comprises a protection apparatus for network access behavior; the network side device comprises a cloud database, a network side receiving module suitable for receiving at least one kind of domain information transmitted by the client device, a network side inquiry module suitable for inquiring whether the cloud database stores any type of the at least one type of domain information, and obtaining the inquiry result, and a network side transmitting module suitable for transmitting the inquiry result to the client device; and the protection apparatus for network access behavior comprises a driver layer module and an application layer module. The system provided by the invention directly uses the targets of these high layer protocols to judge whether the network access request is safe, thereby intercepting the network access behavior of rogue programs more effectively.
Owner:三六零数字安全科技集团有限公司
Vehicle-mounted road traffic automobile violation correcting black box
InactiveCN103366412AModify speed limit in real timeReal-time adjustment and modification of safe driving distanceRegistering/indicating working of vehiclesRemote controlGps positioning system
The invention belongs to a vehicle-mounted road traffic automobile violation correcting device, which is based on technologies of modern communication, a computer network, GPS (Global Position System) positioning, video detection and recognition, micro electronic control, and the like. The device can be used for automatically amending regulated road traffic limit parameters and automatically recording automobile travelling states according to actual automobile travelling states, geographical sections, time zones, driver states, automobile passengers / cargoes, road environments and the like on the basis of a current automobile black box by means of high integration of an information system and monitoring equipment. The vehicle-mounted road traffic automobile violation correcting device provided by the invention is aimed at effectively managing and controlling three-exceed and one-fatigue, and is capable of realizing remote intervention, reminding, remote control, warning, regulation and control on the operation of a driver in the travelling process of an automobile and even forcing the automobile to pull over, Meanwhile, a GPS positioning system is used to notify a jurisdiction department of a automobile travelling road section and nearest police in real time in a mass texting and group calling manner so as to pre-dispose, timely correct violation of, intercept, timely investigate and timely capture illegal automobiles and drivers.
Owner:西安纳兴电子科技有限公司
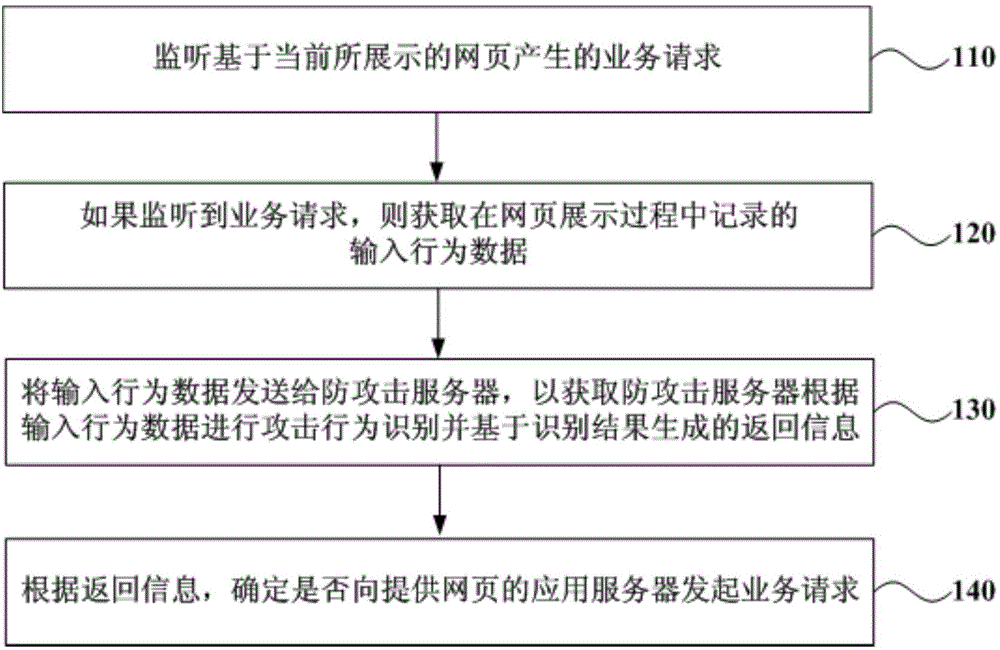
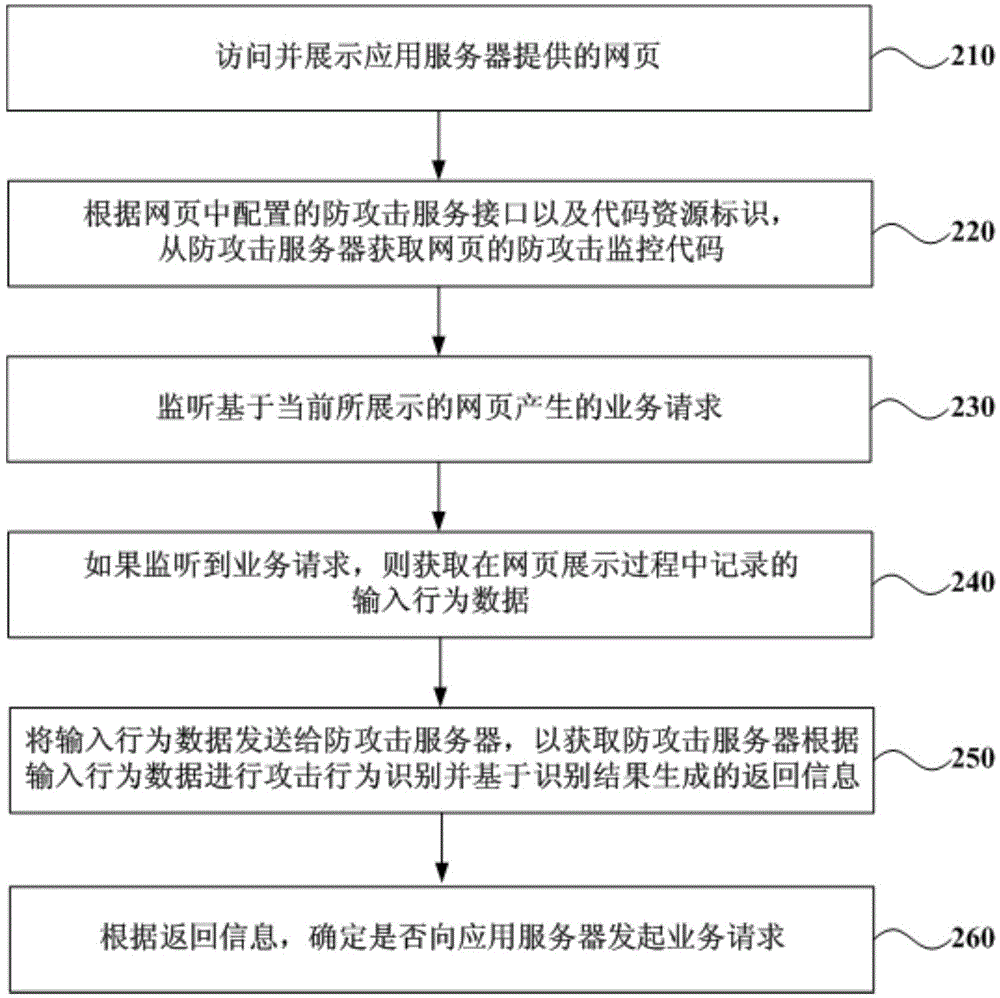
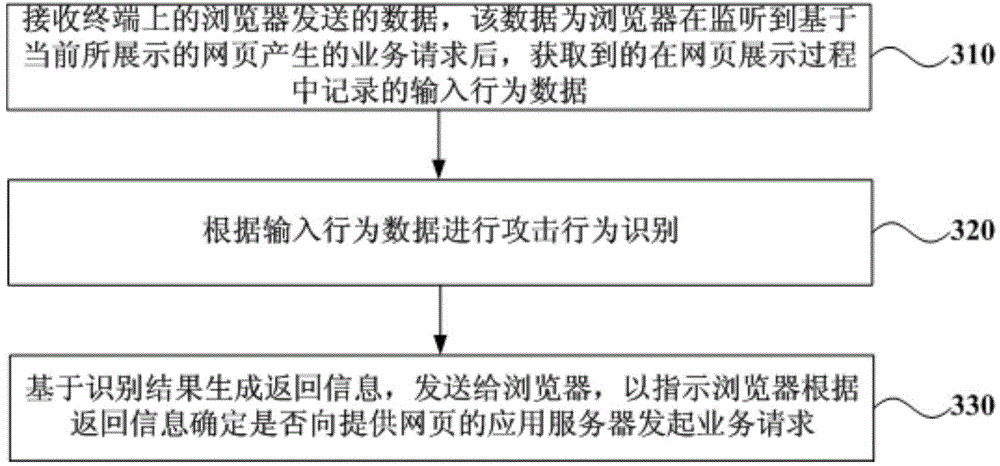
Service request processing method, terminal browser and anti-attack server
ActiveCN104994092AAvoid attackReduce the burden of business request processingTransmissionApplication serverWeb page
The embodiment of the invention discloses a service request processing method, a terminal browser and an anti-attack server. The service request processing method implemented by a browser comprises the following steps: monitoring a service request generated on the basis of a currently-displayed webpage; if the service request is monitored, acquiring input behavior data recorded in the display process of the webpage; transmitting the input behavior data to the anti-attack server in order to obtain return information generated on the basis of an identification result after the anti-attack server performs attack behavior identification according to the input behavior data; and determining whether or not to initiate a service request to an application server providing the webpage according to the return information. Through the technical scheme provided by the embodiment of the invention, service request attacks triggered by non-human operation can be intercepted in time.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
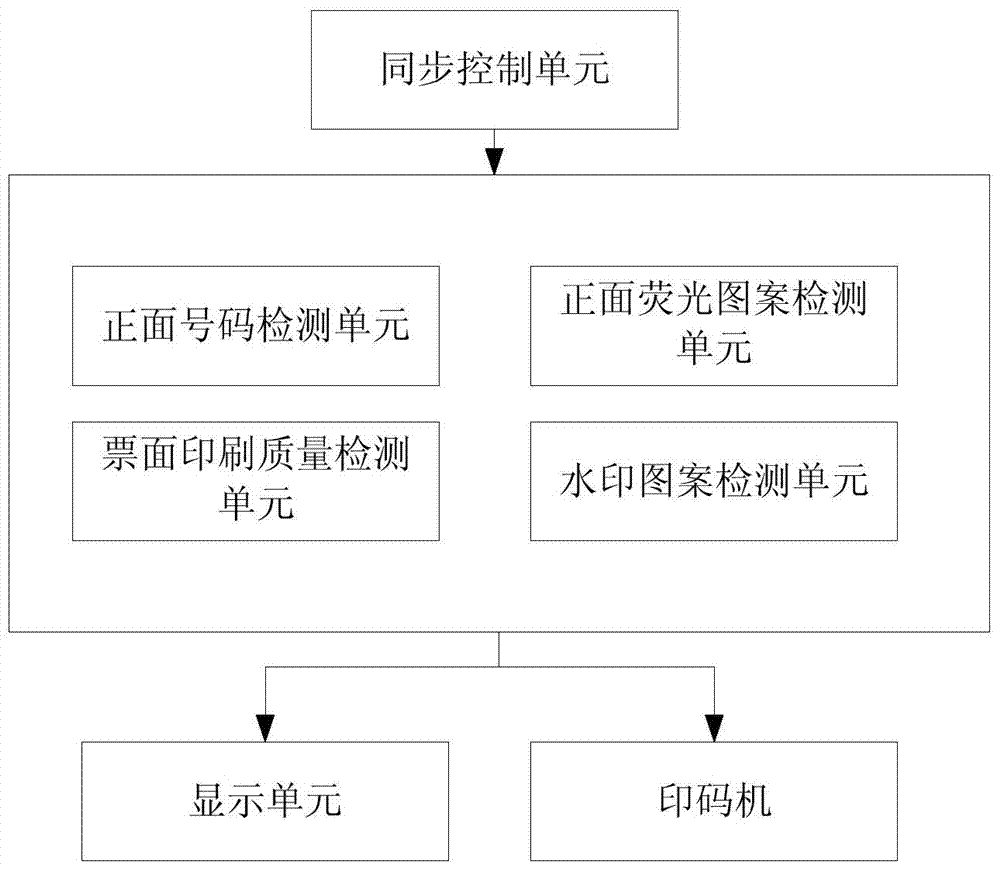
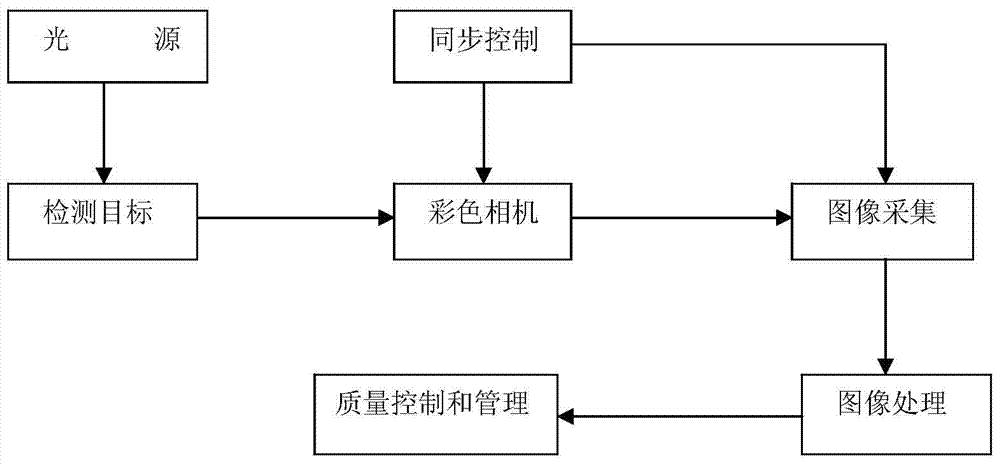
Online imprinting detection method and system
ActiveCN103679916AIntercept in timeQuality assuranceCharacter and pattern recognitionFluorescenceDisplay device
The invention discloses an online imprinting detection method and system. The system employs multiple colorful CCD (Charge Coupled Device) cameras and multiple parallel high-speed image collecting, operating and processing systems to detect and timely monitor printing qualities, including the front-side number printing quality, the front-side fluorescent pattern printing quality, the front and back side nominal value printing quality and the watermarking pattern printing quality (inverted note defect detection), for large RMB note products which are printed online; and the detection system emits a related command and an acousto-optic alarm signal the moment that continuous wastes or severe wastes are detected, thereby controlling an imprinting machine to stop running. Operation interfaces of different detection functions are integrated in a terminal display with a big screen for concentrated display, wherein the interfaces are clear, and operation is convenient. Number printing is the last procedure for RMB note printing, the printing quality detection after number printing can be used to verify defects detected in the previous procedures and intercept products missed in detection, thereby ensuring the quality of delivered products, and improving the production efficiency.
Owner:BEIJING BANKNOTE PRINTING +2
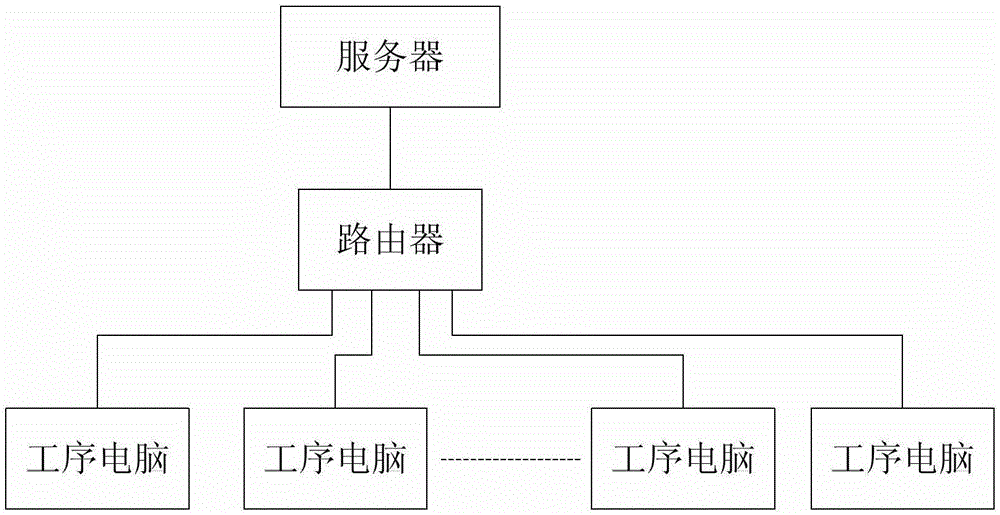
Intelligent management and control system and method of manufacturing technique
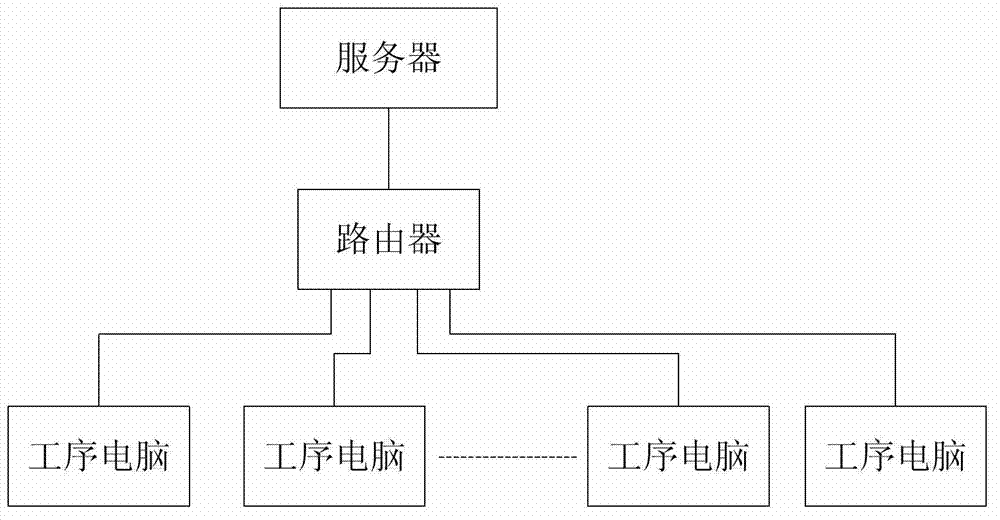
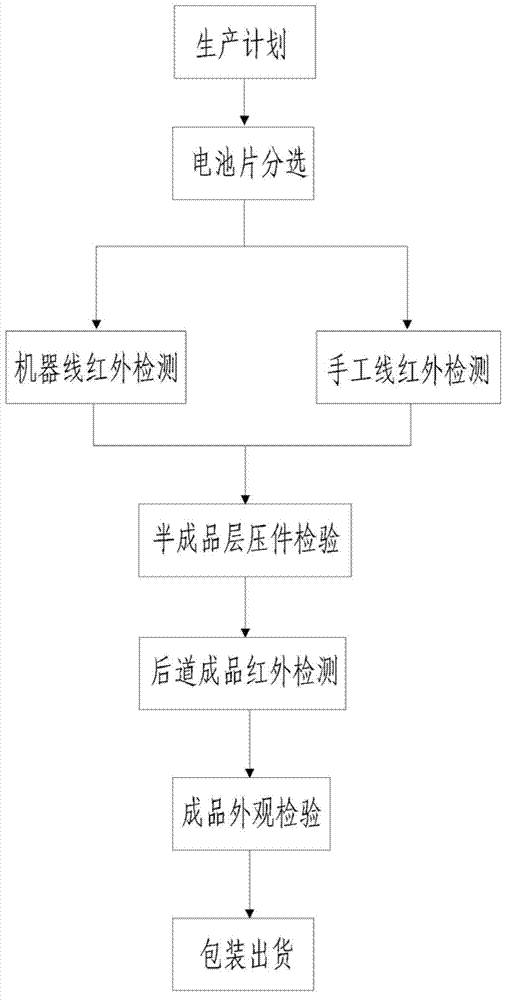
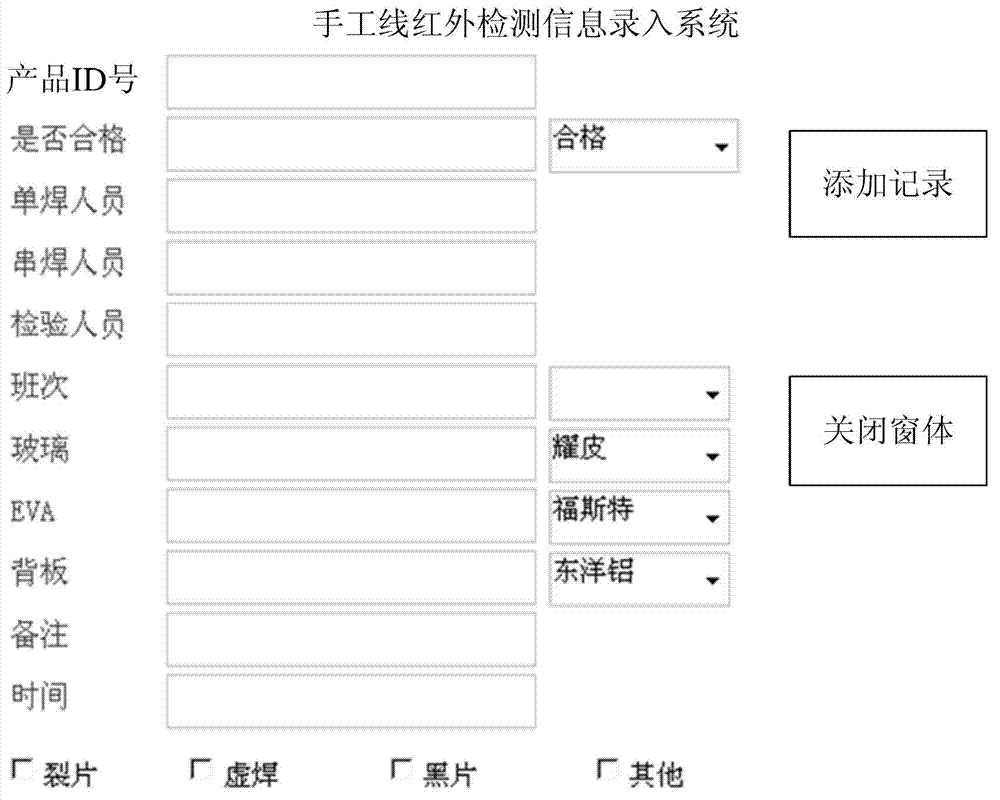
ActiveCN103197640AExtend your lifeImprove integrityTotal factory controlProgramme total factory controlUser inputControl system
The invention provides an intelligent management and control system of a manufacturing technique. The intelligent management and control system comprises one or a plurality of working procedure computers corresponding to each manufacturing working procedure, the working procedure computers are connected with a server through a router to form a local area network; client ends of a working procedure data base are installed on the working procedure computers, entering interfaces corresponding to working procedures are provided, and each entering interface at least comprises an input box of product ID numbers; a user inputs production information corresponding to the working procedures after the working procedures are finished, and then the working procedure computers send the production information corresponding to the working procedures to the server through the local area network; and data bases of each working procedure are installed on the server, and data bases of each working procedure are mutually connected. The server receives the production information which corresponds to the working procedures and is sent from each working procedure computer, checks and tests validity of contents in the production information, feeds back mistake contents in the production information to the corresponding working procedure computers, gives an alarm and prompts. The intelligent management and control system is used for managing and controlling a manufacturing process.
Owner:江苏润达光伏无锡有限公司
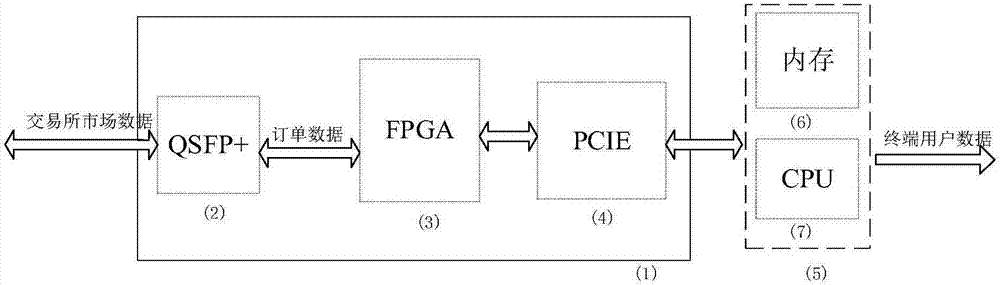
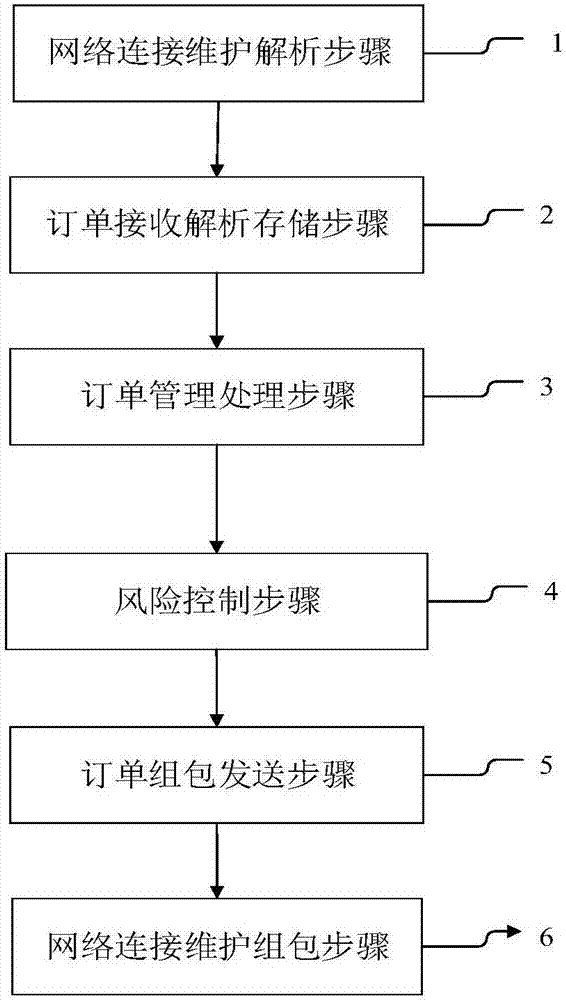
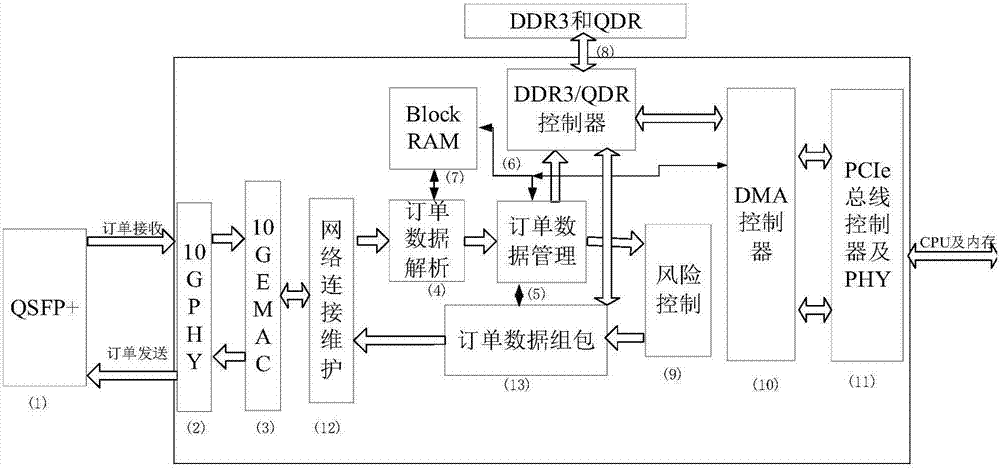
FPGA-based futures trading system and method
The invention belongs to the technical field of finance communication and discloses an FPGA-based futures trading system and method. The system comprises order data reception and analysis, order management, risk control, order package and network protocol stack realized based on FPGA. According to the FPGA-based futures trading system and method, the transaction order data is analyzed and packaged by utilizing FPGA hardware; and compared with a scheme of processing the order trading through a software-only method, the method prevents delay caused by computer kernel software data analysis, and solves the problem that an existing common futures trading system cannot meet users' requirements for high-frequency trading speed.
Owner:武汉旷腾信息技术有限公司
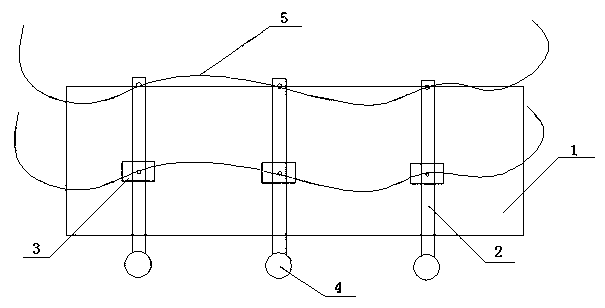
Water intercepting device
The invention relates to a water intercepting device, which comprises a fishing net (1), a plurality of poles (2) capable of floating in water, a plurality of floating objects (3) and a plurality of heavy objects (4), wherein each heavy object (4) is arranged at one end of the corresponding pole (2), and each floating object (3) is arranged in the middle of the corresponding pole (2), so that each pole (2) can vertically float in water; and each pole (2) is arranged on the fishing net (1), and the fishing net (1) vertically floats in water through the poles (2). The device can timely intercept garbage in a river and is convenient for workers to clean the garbage in the river.
Owner:WUXI INST OF COMMERCE
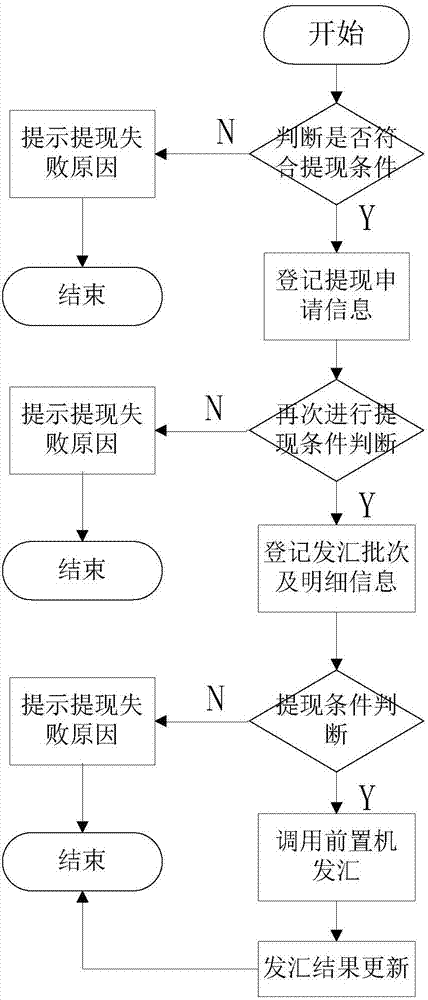
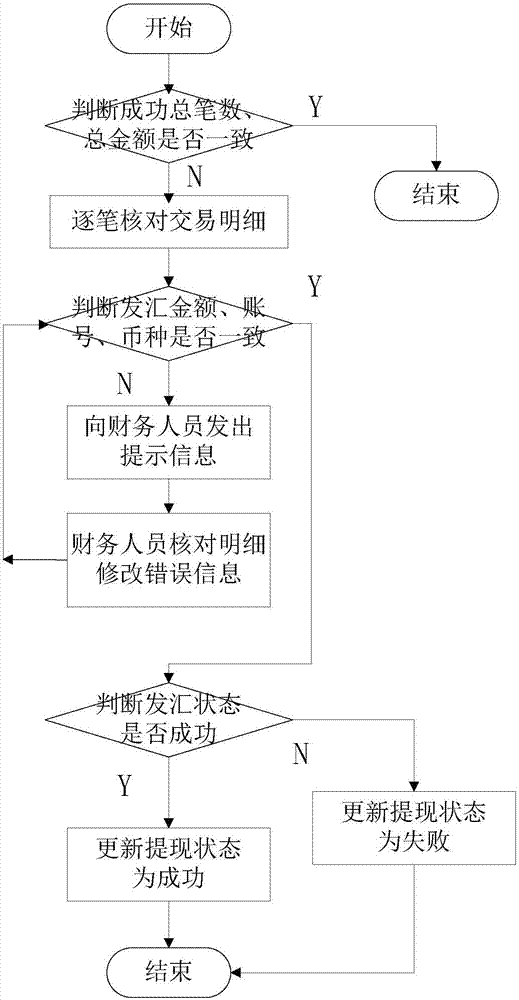
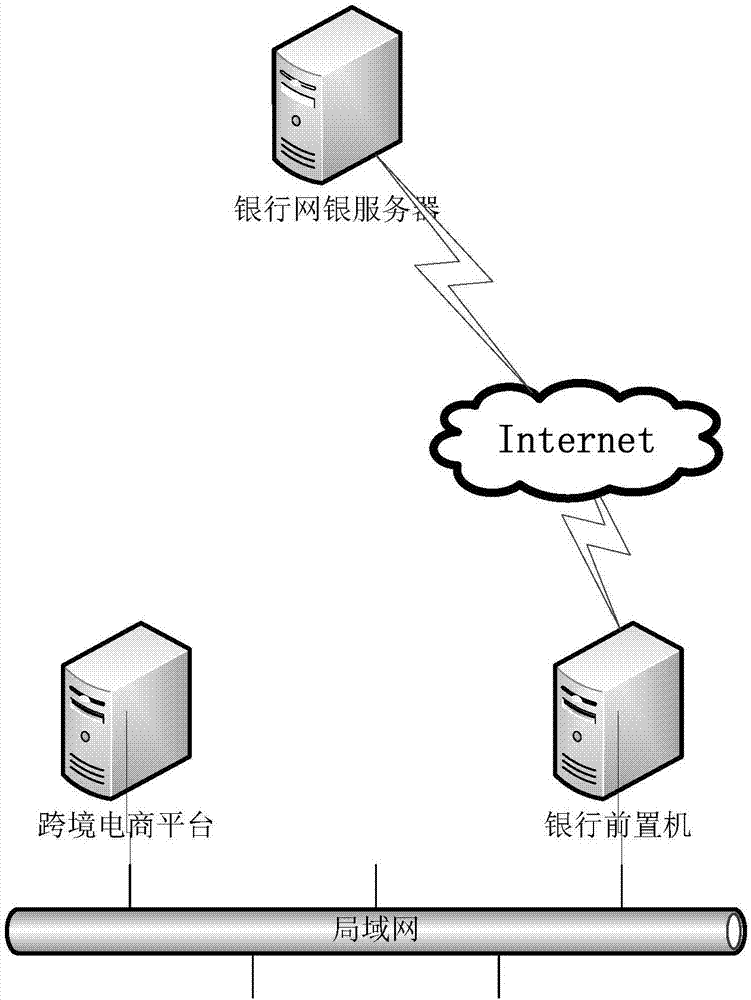
Bank-corporate direct linkage method and system on cross-border e-commerce platform
InactiveCN106897869AReduce artificial ginsengReduce process linksFinanceBuying/selling/leasing transactionsOperational costsBank account
The present invention relates to a bank-corporate direct linkage method and system on a cross-border e-commerce platform. The method comprises that: the e-commerce platform receives the application for withdrawal and checks the application for withdrawal, and if the application for withdrawal meets the conditions of withdrawal, a bank-corporate direct linkage front-end processor is invoked by the e-commerce platform to remit to the application account; according to the total amount of remittances and the bank account balance, the financial operator carries out corresponding allocation of funds, clicks for checking after the corresponding allocation of funds is completed, and still carries out determination on the conditions of withdrawal; and for the records that pass the determination condition, the bank-corporate direct linkage front-end processor is invoked for issuing. According to the bank-corporate direct linkage method and system on the cross-border e-commerce platform disclosed by the present invention, in the process from generating the withdrawal data to registering the issuing batch, systematic processing is realized, steps of manual participation are reduced, and without uploading an issuing file to the e-bank, the financial operating costs are reduced and the operational risk is reduced.
Owner:数贸科技(北京)有限公司
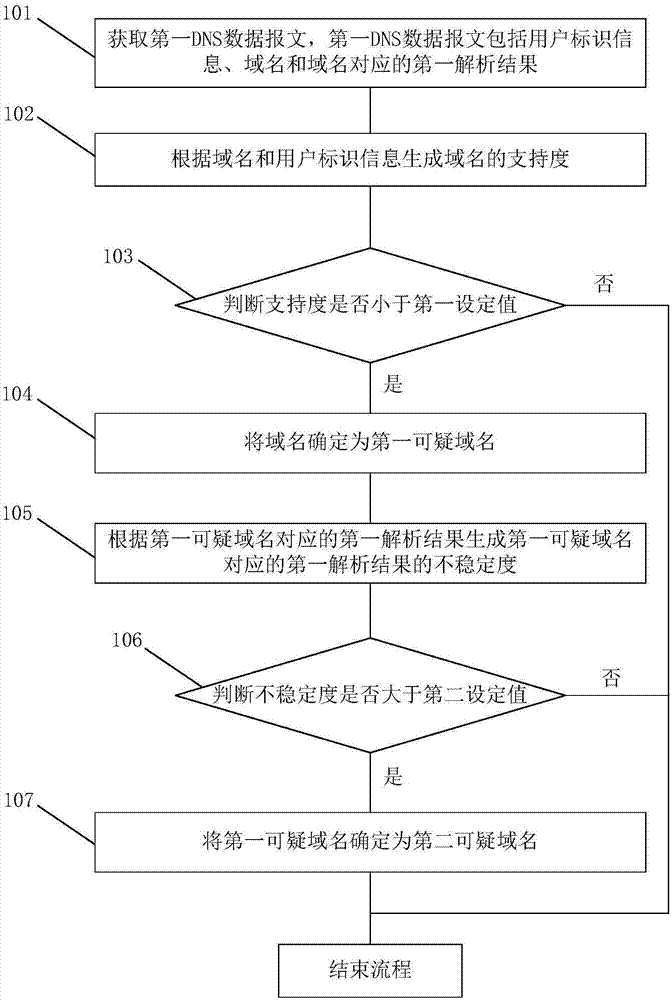
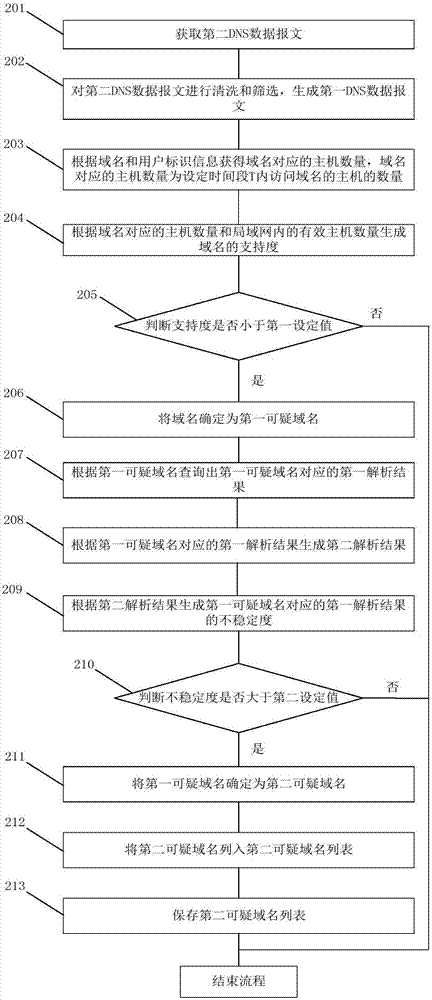
Suspicious domain name detection method and system
The invention discloses a suspicious domain name detection method and system. The suspicious domain name detection method comprises the following steps: obtaining a first DNS data message, wherein the first DNS data message comprises user identification information, a domain name and a first analysis result corresponding to the domain name; generating support degree of the domain name according to the domain name and the user identification information; judging whether the support degree is smaller than a first set value; if judging that the support degree is smaller than the first set value, determining the domain name as a first suspicious domain name; if judging that the domain name is the first suspicious domain name, generating the degree of instability of the first analysis result according to the first analysis result corresponding to the first suspicious domain name; judging whether the degree of instability is larger than a second set value; and if judging that the degree of instability is larger than the second set value, determining the first suspicious domain name as a second suspicious domain name. The suspicious domain name detection method and system realize dual verification of the domain names and realize real-time automatic update and timely interception of the suspicious domain names.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
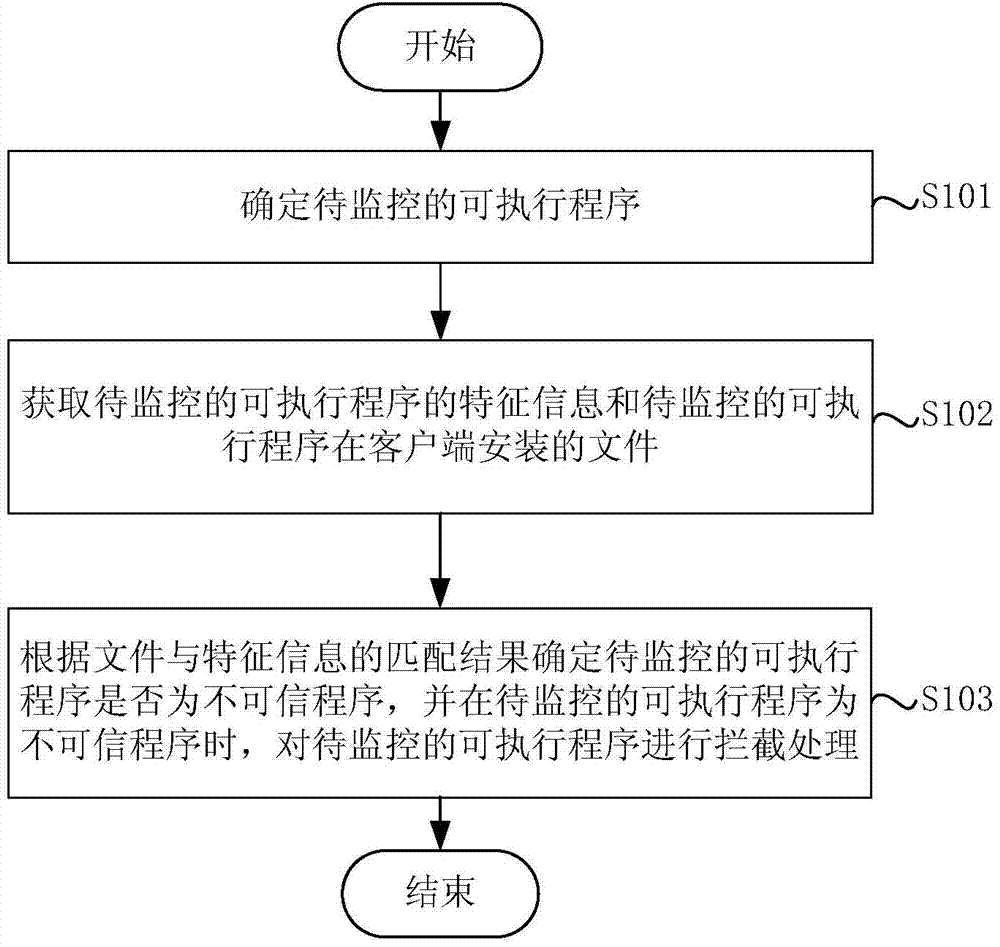
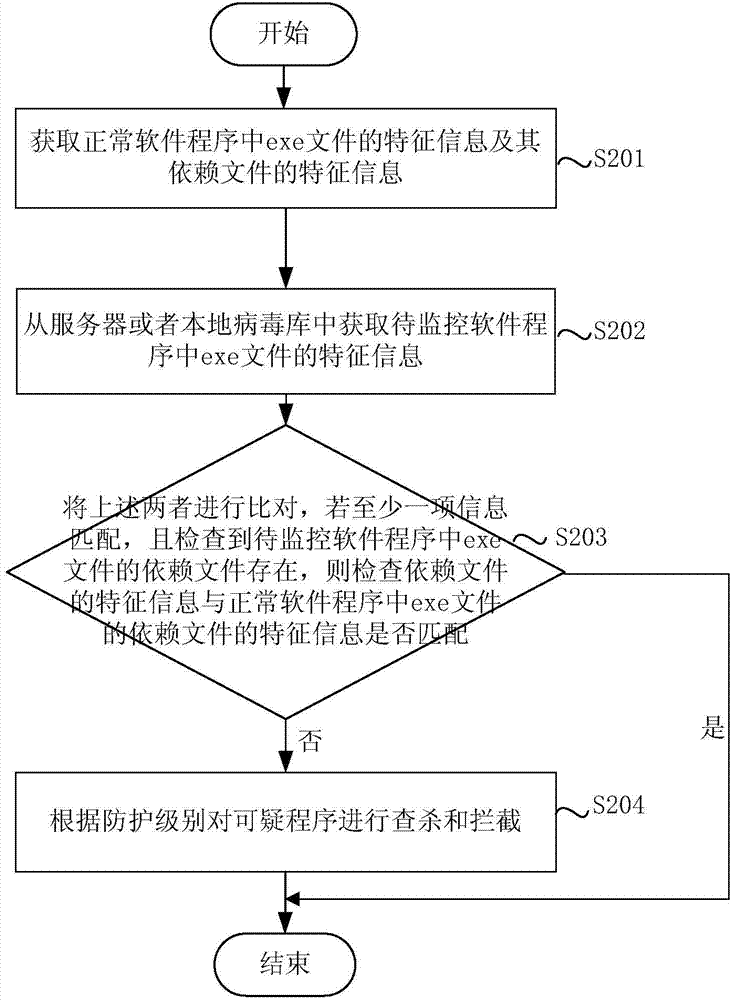
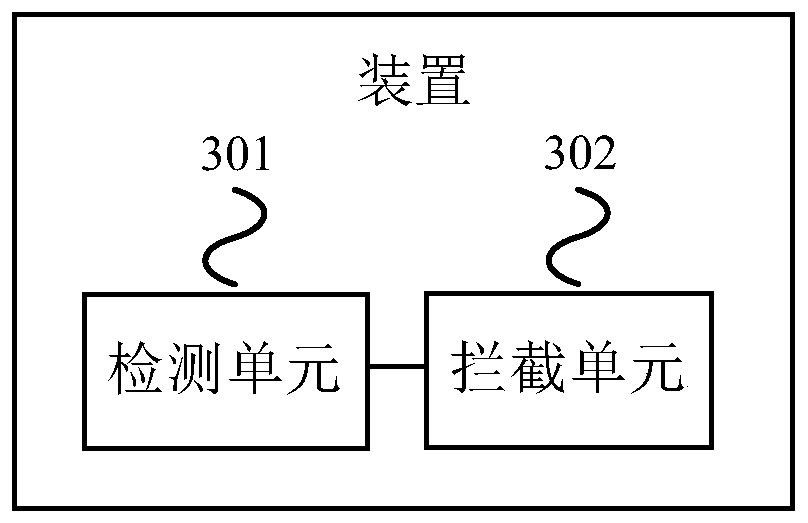
Method and device for monitoring executable program
InactiveCN104123489AKill in timeIntercept in timePlatform integrity maintainanceClient-sideUser information
The invention discloses a method and device for monitoring an executable program. The method includes the steps that the executable program to be monitored is determined; feature information of the executable program to be monitored and a file, installed on a client side, of the executable program to be monitored are acquired; according to the matching result of the file and the feature information, whether the executable program to be monitored is an incredible program or not is determined, and when the executable program to be monitored is the incredible program, the executable program to be monitored is intercepted. The feature information of the executable program to be monitored and the file, installed on the client side, of the executable program to be monitored are acquired, according to the matching result of the file and the feature information, it is determined that the executable program to be monitored is the incredible program, and then the executable program to be monitored is intercepted, dependence on malicious code features is removed, the incredible program can be searched for, killed and intercepted, and security of user information is effectively guaranteed.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
Risk prevention and control method and device and electronic device
ActiveCN108052824AImprove real-time performanceIntercept in timePlatform integrity maintainanceRisk preventionAnomalous behavior
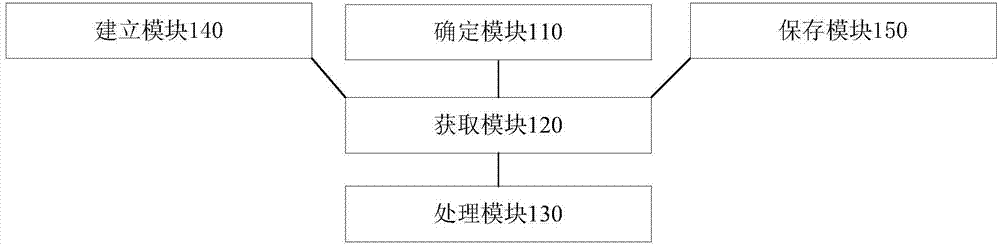
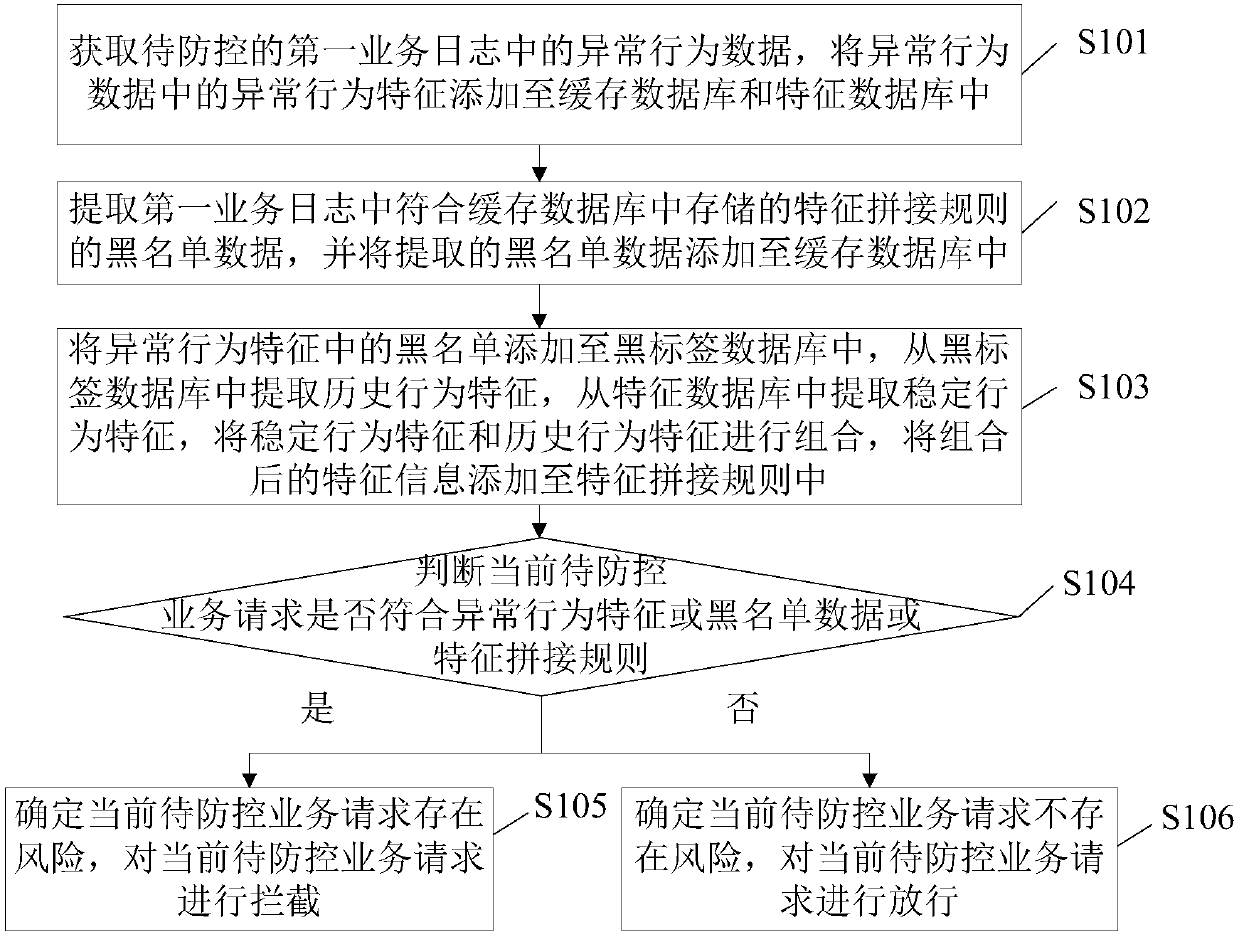
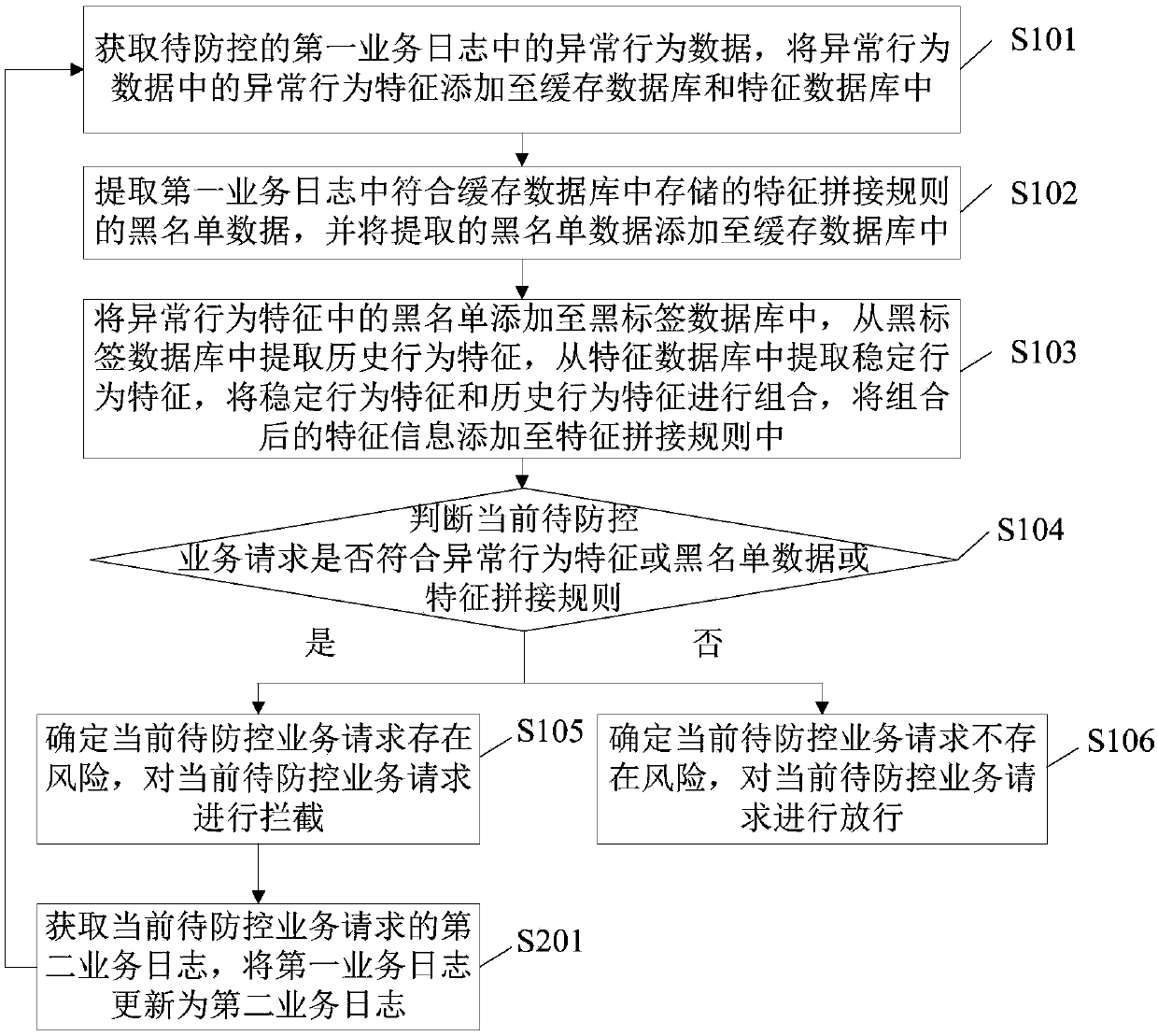
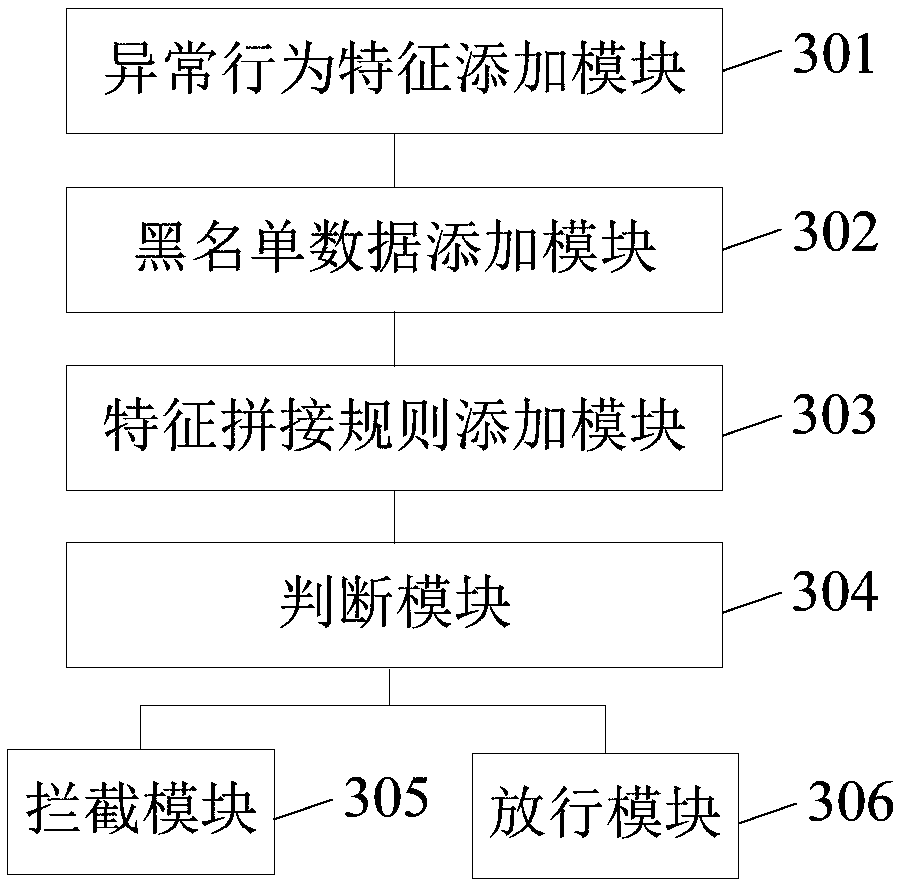
The embodiment of the invention provides a risk prevention and control method and device and an electronic device, and is applied to the technical field of information security. The method includes the steps of obtaining abnormal behavior data in a service log, adding abnormal behavior features in the abnormal behavior data to a cache database and a feature database, extracting blacklist data meeting a feature splicing rule in the service log, adding the extracted blacklist data to the cache database, adding black labels in the abnormal behavior features to a black label database, combining historical behavior features extracted from the black label database and stable behavior features extracted from the feature database, adding the combined feature information to the feature splicing rule, judging whether a current to-be-prevented / controlled service request meets the abnormal behavior features or the blacklist data or the feature spliced rule, if yes, determining that a risk exists in the current to-be-prevented / controlled service request, and intercepting the current to-be-prevented / controlled service request. The real-time property of risk detection can be improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
A kind of active defense method and device based on Linux system
ActiveCN104008337BIntercept in timeEffective active defensePlatform integrity maintainanceGNU/LinuxSystem call
The invention discloses an active defense method and device based on a Linux system, and belongs to the field of system security. The method includes the steps that system call of a Linux kernel is monitored through a Hook; when it is monitored that the system call provided with the Hook is called by a user mode course, whether the user mode course exists in a white list or not is judged; when the user mode course exists in the white list, the user mode course is allowed to call the system call; when the user mode course does not exist in the white list, the user mode course is forbidden from calling the system call, wherein the white list comprises one or more user mode courses allowing execution of the system call. Running programs of the Linux system can be effectively detected, running malicious programs of the Linux system, back door Trojan horse programs and the like can be intercepted in time, and the active defense method is an effective active defense method based on the Linux system.
Owner:GUANGZHOU HUADUO NETWORK TECH
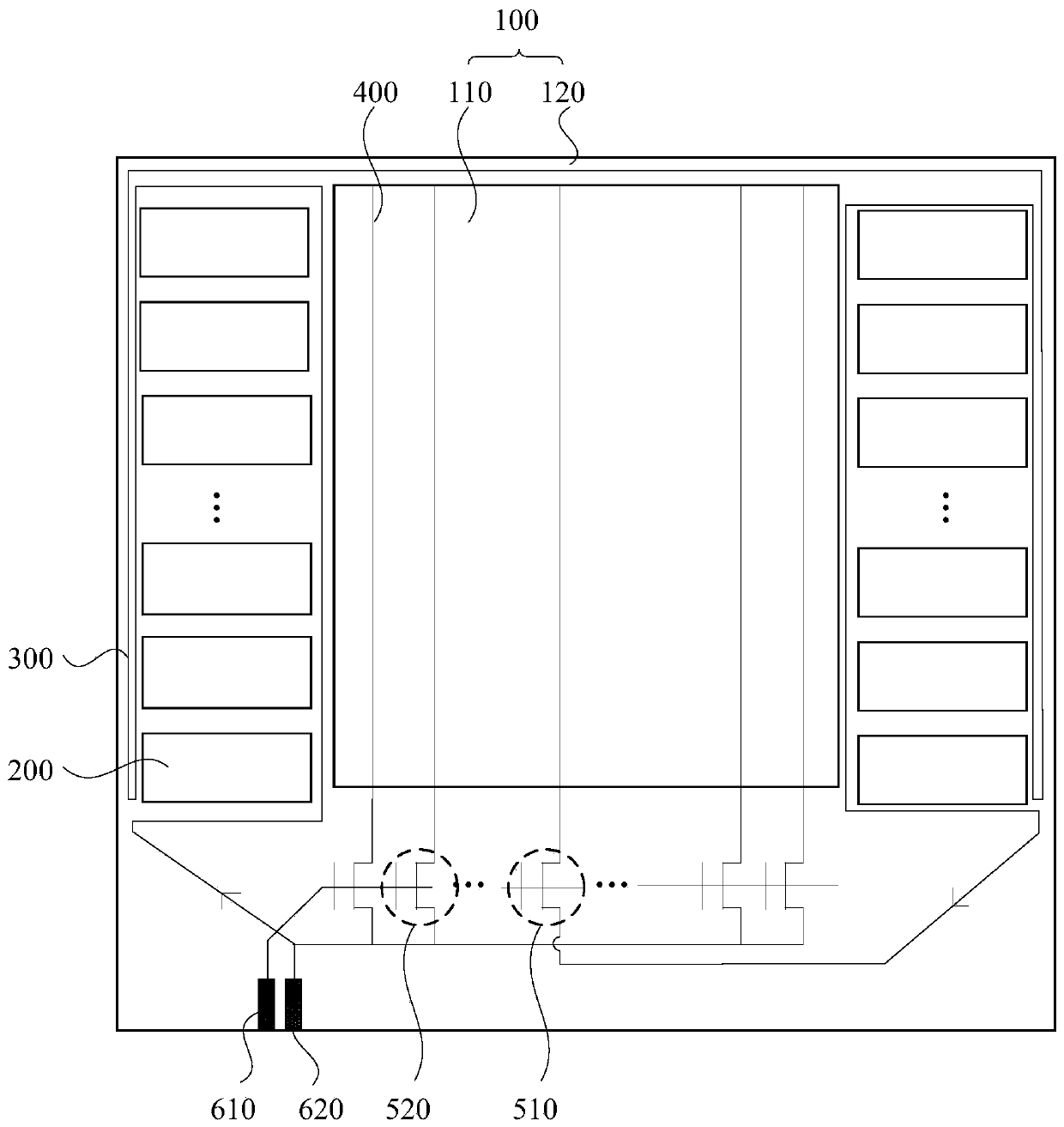
Display panel and display device
ActiveCN110827728AImprove yieldAvoid post-processingStatic indicating devicesHemt circuitsComputer hardware
The embodiment of the invention discloses a display panel and a display device. The display panel includes a substrate including a display area and a non-display area; a multi-stage gate drive circuitwhich is located in the non-display area of the substrate; a broken line detection line which is located in the non-display area of the substrate and surrounds the multi-stage gate drive circuit at one side of the display area. Compared with the prior art, and according to the embodiment of the invention, the detection of ESD disconnection is realized, the display panel with poor ESD disconnection can be timely intercepted, and the yield of the display panel is improved.
Owner:KUNSHAN GO VISIONOX OPTO ELECTRONICS CO LTD
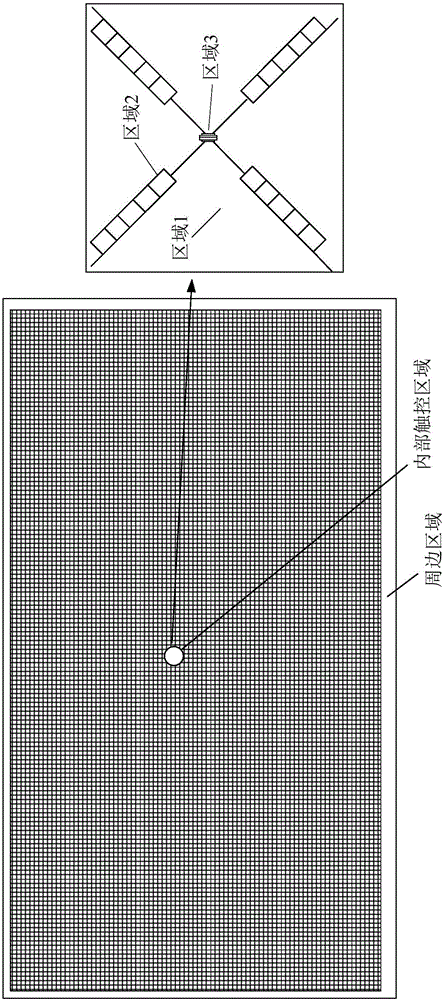
Touch substrate shadow elimination detection method and manufacturing method, touch substrate and touch device
ActiveCN106168868AIntercept in timeAvoid production lossInspection/indentification of circuitsNon-linear opticsOptical testHuman–computer interaction
The invention provides a touch substrate shadow elimination method, a touch substrate manufacturing method, a touch substrate and a touch device. The touch substrate shadow elimination detection method comprises the steps that optical test equipment is used for testing a difference of the optic reflectivity of test blocks which are located in an area located outside a touch area of the touch substrate and have different structures; the shadow eliminating effect of the touch substrate is determined according to the difference, wherein each test block in the test blocks with different structures comprises a structure which is the same as the corresponding structure in the different structures in the touch area.
Owner:HEFEI XINSHENG OPTOELECTRONICS TECH CO LTD +1
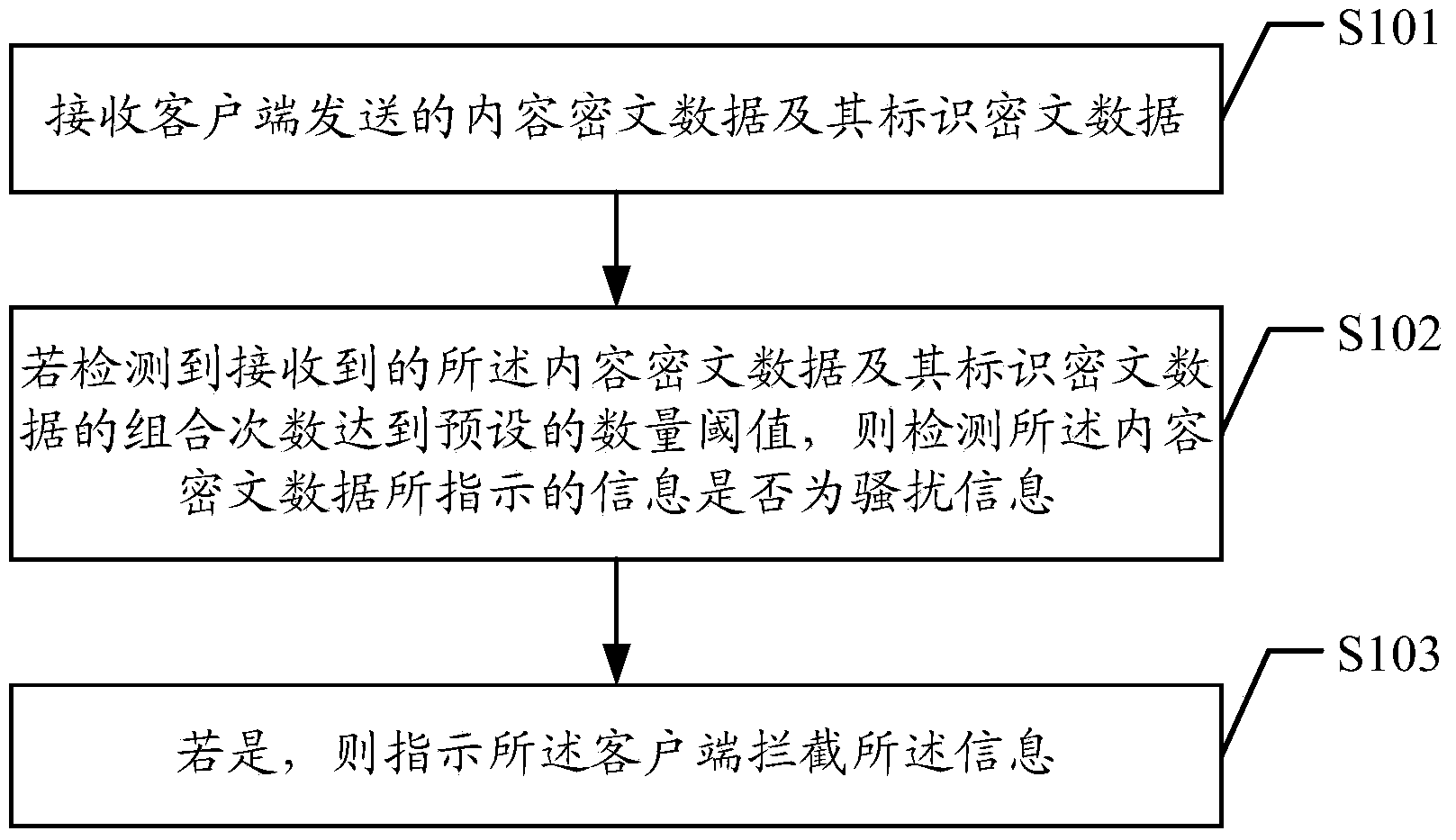
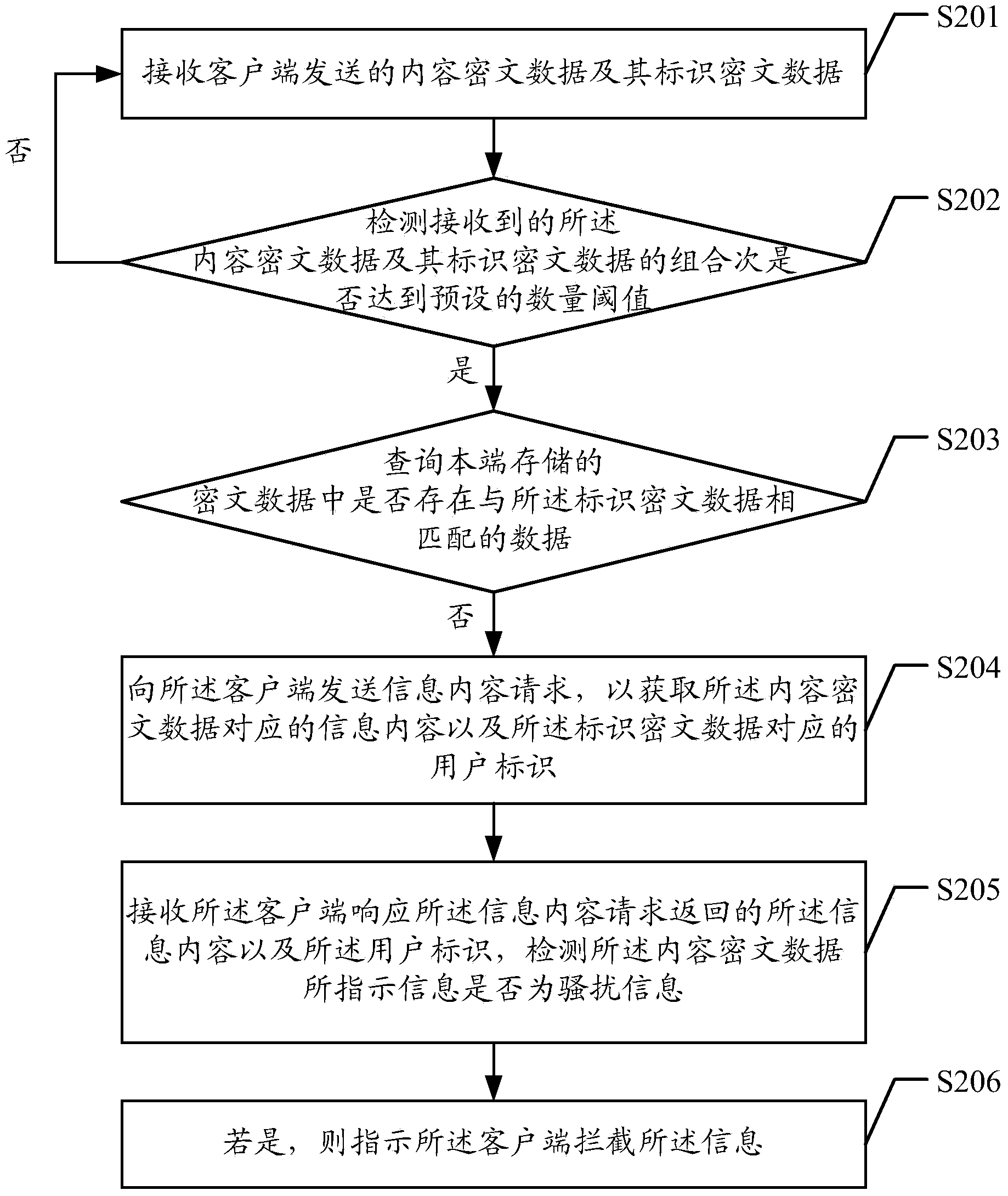
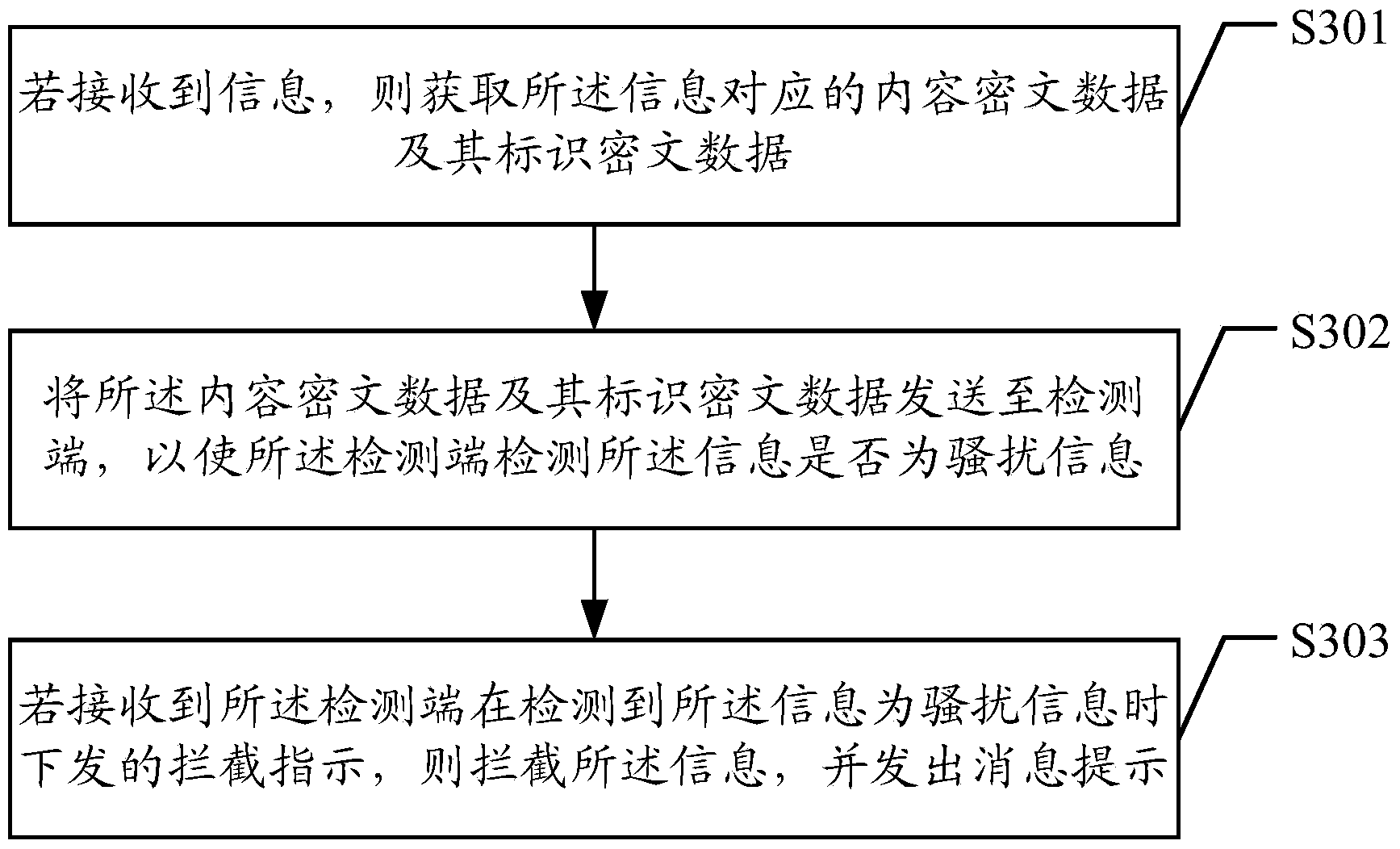
Information interception method, device and system
The embodiment of the invention discloses an information interception method. The information interception method includes receiving content ciphertext data and identification ciphertext data sent by a client; detecting whether information indicated by the content ciphertext data is harassing information or not if the combination number of the received content ciphertext data and the identification ciphertext data is detected to reach a preset threshold value; if so, indicating the client to intercept the information. The embodiment of the invention also discloses a detecting terminal, a client and an information interception system. The information interception method, the detecting end, the client and the information interception system can effectively and timely intercept spam messages of mass texting and are simple in the method.
Owner:KENIU NETWORK TECH BEIJING
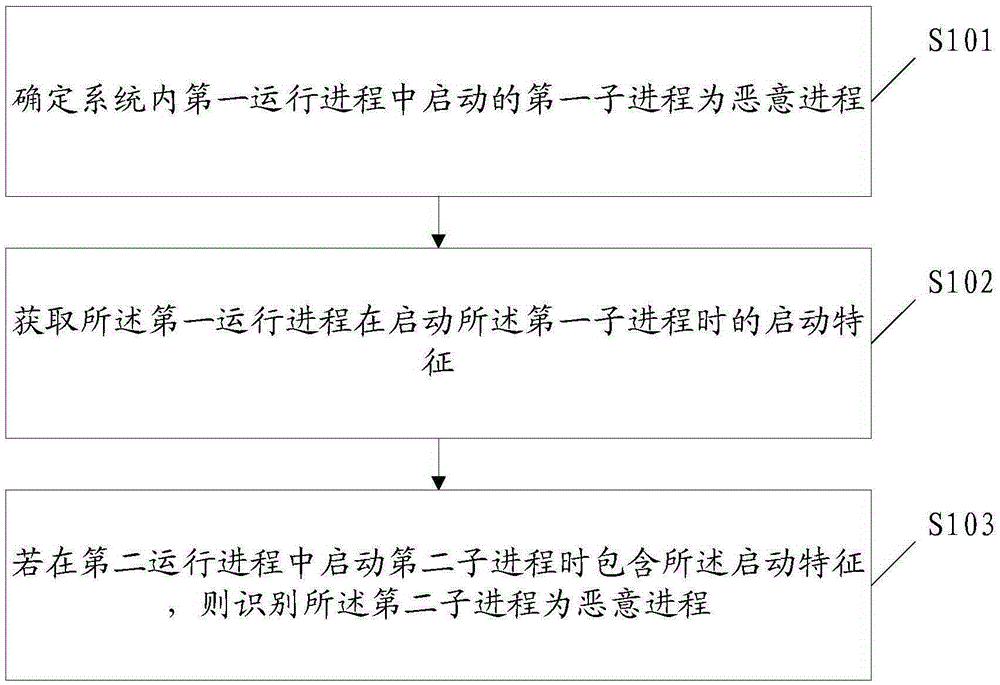
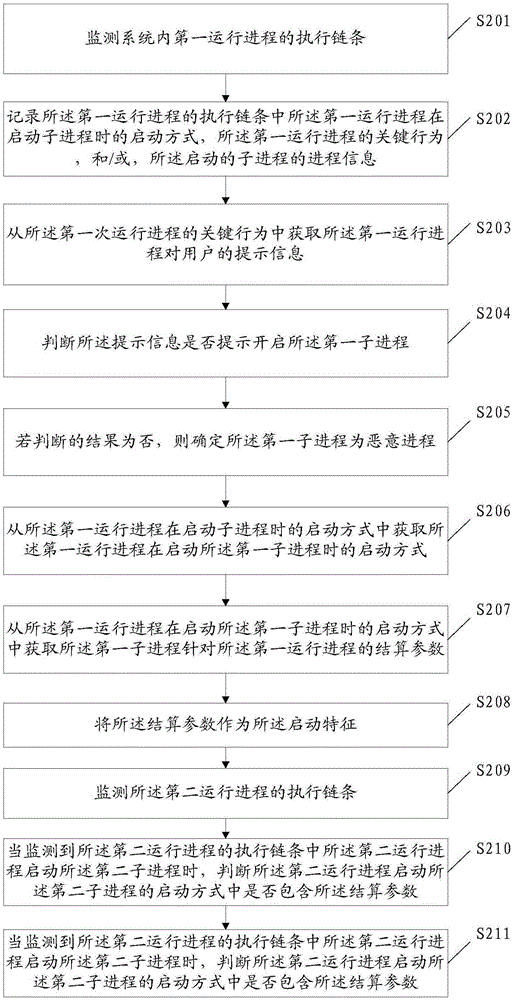
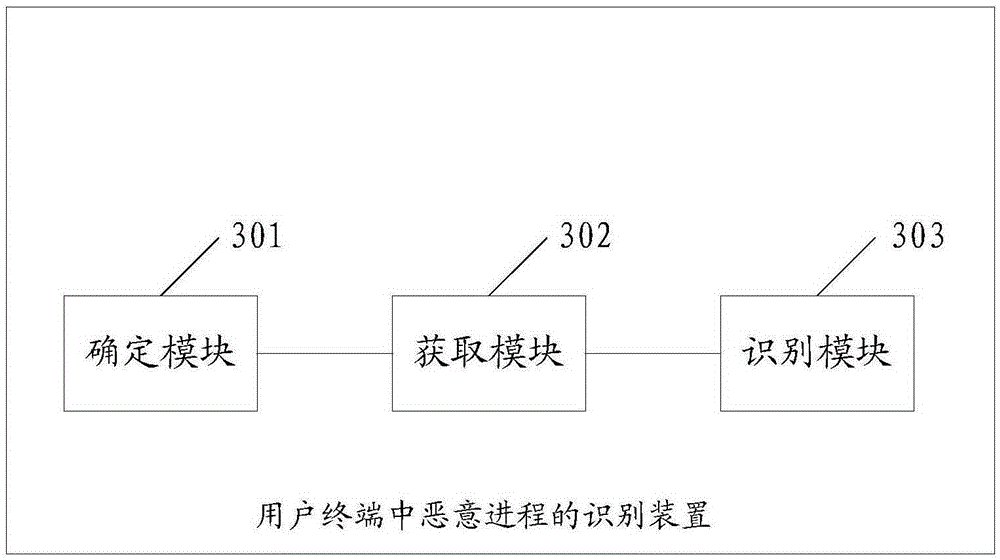
Identifying method and apparatus for malicious process in user terminal and user terminal
ActiveCN105303111ATimely identificationIntercept in timePlatform integrity maintainanceSoftware engineering
Embodiments of the invention disclose an identifying method and apparatus for a malicious process in a user terminal and the user terminal. The method comprises: determining that a first sub-process started in a first running process in a system is the malicious process; obtaining starting features of the first running process when starting the first sub-process; and if a second running process contains the starting features when starting a second sub-process, identifying the second sub-process as the malicious process. With the adoption of the embodiments of the invention, the malicious process can be identified before a malicious sample is acquired, and the malicious process can be identified in time, so that the malicious process can be intercepted in time, and the interception efficiency is improved.
Owner:ZHUHAI BAOQU TECH CO LTD
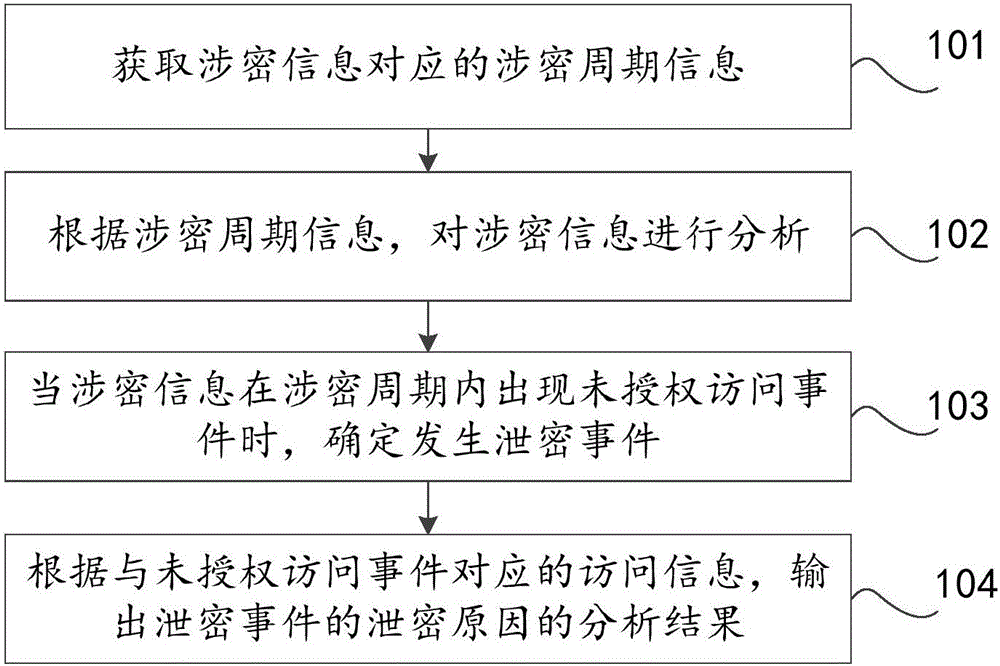
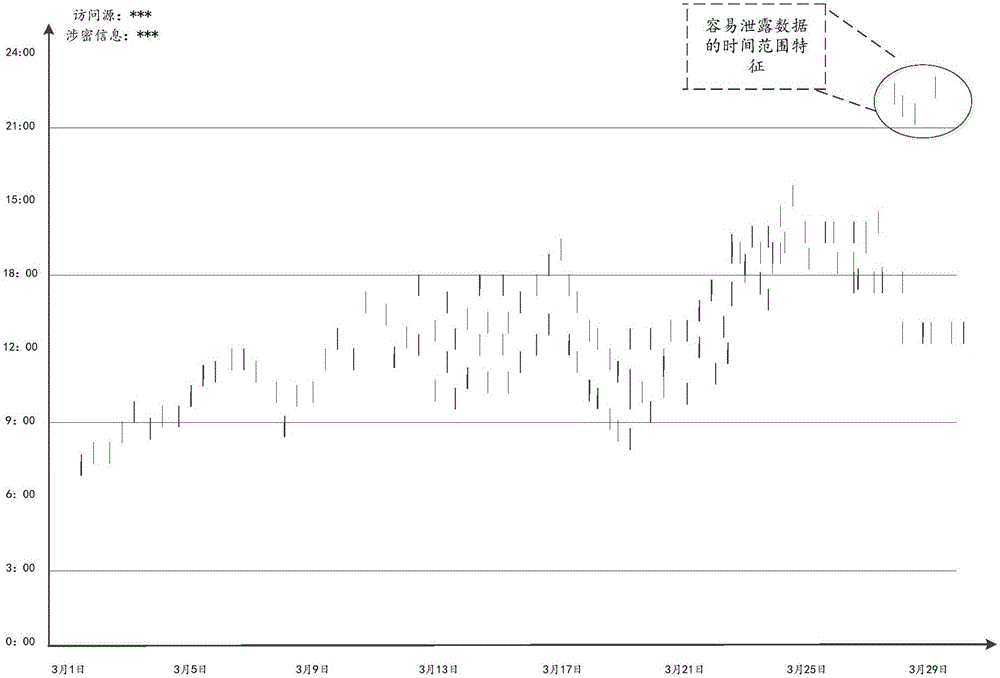
Secret-related information analysis method and apparatus
ActiveCN106650432AAutomate analysisImprove the efficiency of querying the reasons for leakageDigital data protectionPlatform integrity maintainanceInformation analysisAnalysis method
The invention discloses a secret-related information analysis method and apparatus, which relates to the technical field of information and can improve efficiency of querying a secret leakage reason. The method comprises the steps of obtaining secret-related cycle information corresponding to secret-related information; analyzing the secret-related information according to the secret-related cycle information; when an unauthorized access event occurs for the secret-related information in a secret-related cycle, determining that a secret leakage event occurs; and outputting an analysis result of the secret leakage reason of the secret leakage event according to access information corresponding to the unauthorized access event. The method and the apparatus are suitable for secret-related information analysis.
Owner:BEIJING QIHOO TECH CO LTD +1
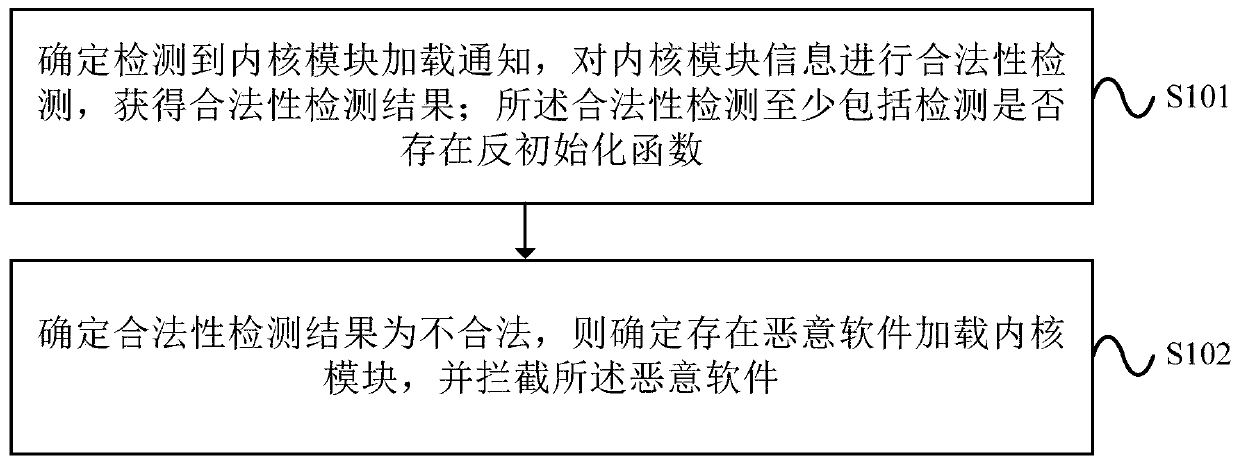
Malicious software interception method and device based on kernel module
ActiveCN111259392AAvoid detectionAvoid repairsPlatform integrity maintainanceHigh level techniquesInitMalware
The embodiment of the invention provides a malicious software interception method and device based on a kernel module, and the method comprises the steps: determining that a kernel module loading notification is detected, carrying out the legality detection of kernel module information, and obtaining a legality detection result; wherein the legitimacy detection at least comprises detecting whetheran anti-initialization function exists; and if it is determined that the legality detection result is illegal, determining that malicious software loads the kernel module, and intercepting the malicious software. The device executes the method. According to the method and the device provided by the embodiment of the invention, malicious software can be intercepted in time, so that after-event detection and repair carried out after the kernel module is loaded by the malicious software are avoided.
Owner:BEIJING QIANXIN TECH +1
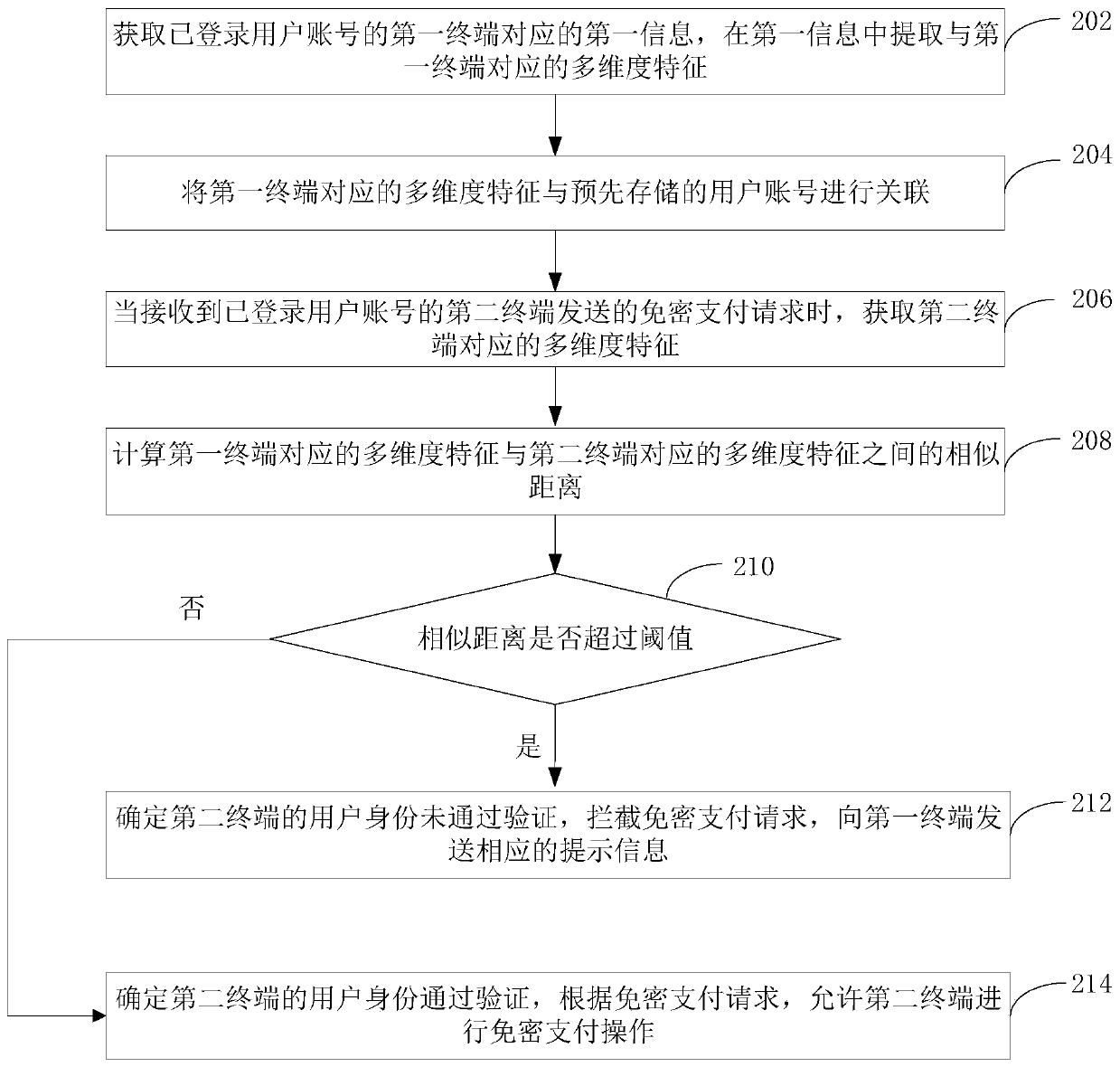
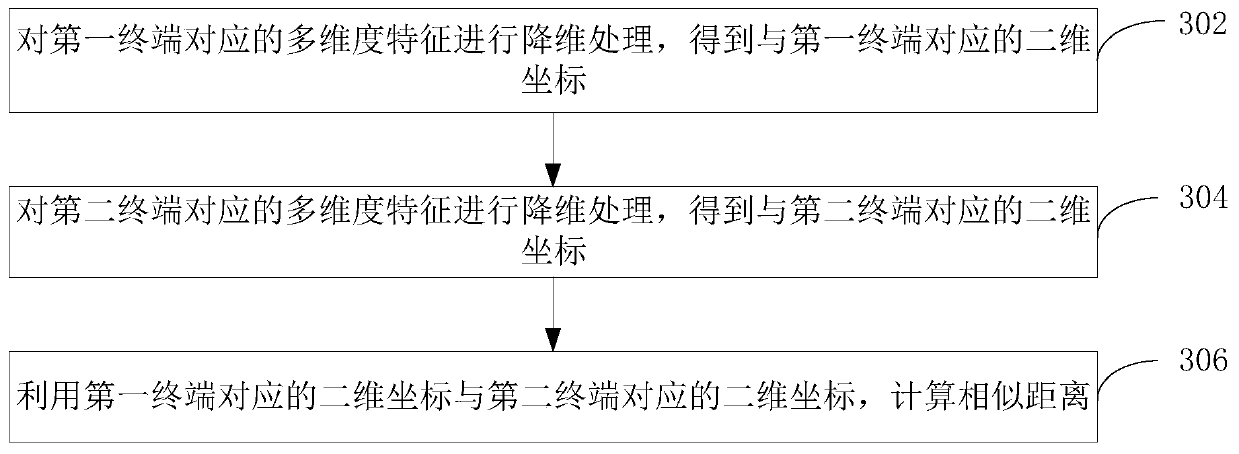
User identity authentication method and device, computer equipment and storage medium
The invention relates to a user identity authentication method and device, computer equipment and a storage medium in the field of information security. The method comprises the steps of acquiring first information corresponding to a first terminal of a logged-in user account, and extracting multi-dimensional features corresponding to the first terminal from the first information; associating themulti-dimensional feature corresponding to the first terminal with the user account; when a password-free payment request sent by a second terminal logging in the user account is received, obtaining multi-dimensional features corresponding to the second terminal; calculating a similar distance between the multi-dimensional feature corresponding to the first terminal and the multi-dimensional feature corresponding to the second terminal; and if the similarity distance exceeds a threshold value, determining that the user identity of the second terminal does not pass the verification, intercepting the password-free payment request, and sending corresponding prompt information to the first terminal. By adopting the method, the security of the password-free payment function can be effectively improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
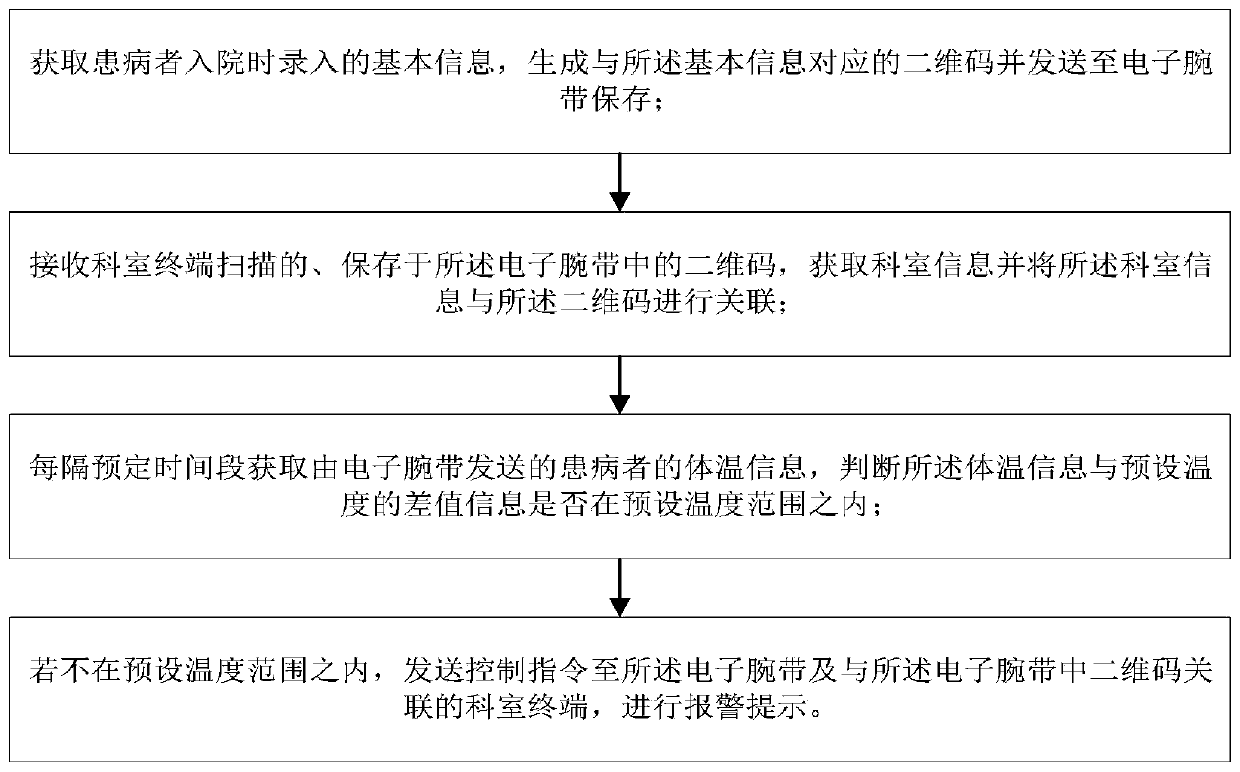
Real-time monitoring system for patient
InactiveCN110179442AEasy to track statusRealize real-time monitoringSensorsMeasuring/recording heart/pulse rateMonitoring systemComputer terminal
The embodiment of the invention discloses a real-time monitoring method for a patient in hospitals. The real-time monitoring method comprises the steps of obtaining basic information which is input when the patient is hospitalized, generating a two dimensional code corresponding to the basic formation, and sending the two dimensional code to an electronic wristlet for preservation; receiving the two dimensional code which is scanned by a terminal of the department and stored in the electronic wristlet, obtaining the information of the department, and enabling the information of the departmentto be related with the two dimensional code; obtaining the body temperature information of the patient send by the electronic wristlet at scheduled time intervals, and judging whether difference valueinformation between the body temperature information and preset temperature is in the preset temperature range or not; and if the difference value information is not in the preset temperature range,sending control instructions to the electronic wristlet and the terminal of the department, associated with the two dimensional code in the electronic wristlet, and performing warning promotion. The real-time monitoring method can realize real-time monitoring of the body state and the active state of the patient, the monitoring effect of the patient is increased, and the monitoring efficacy of medical personnel is improved.
Owner:伍媛媛
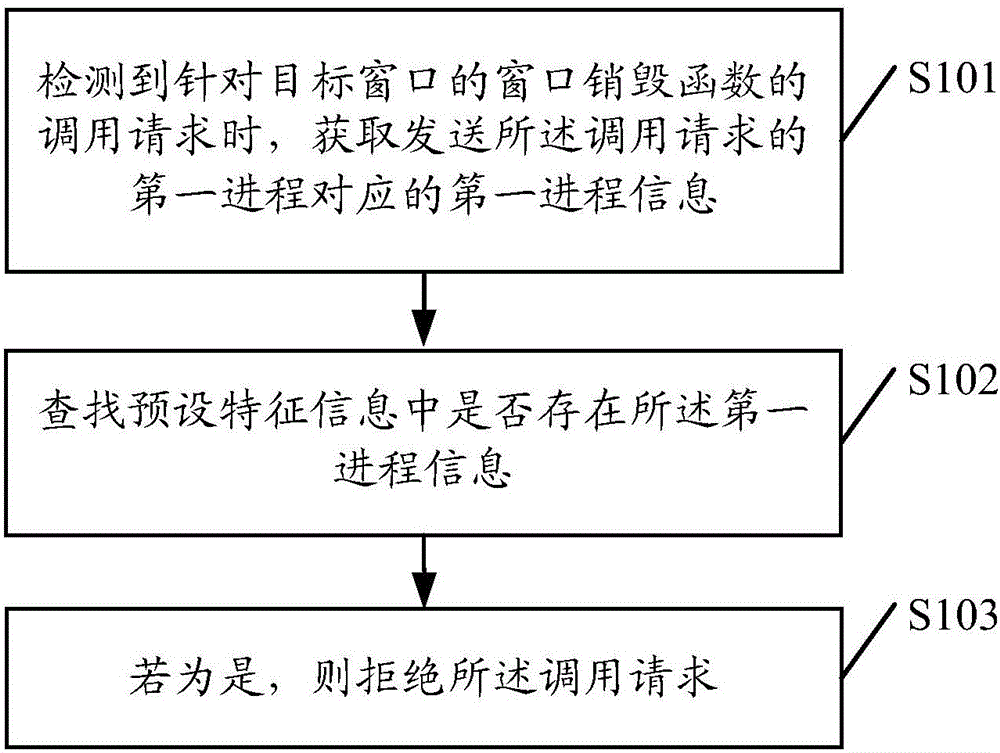
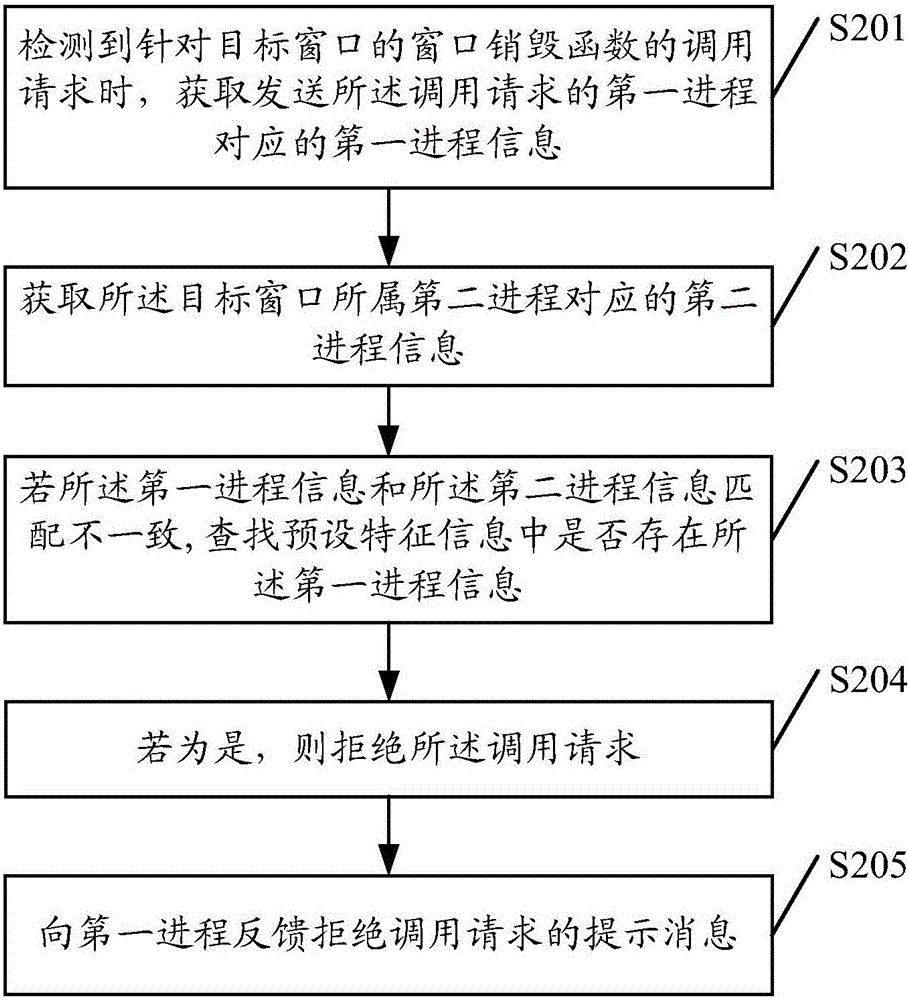
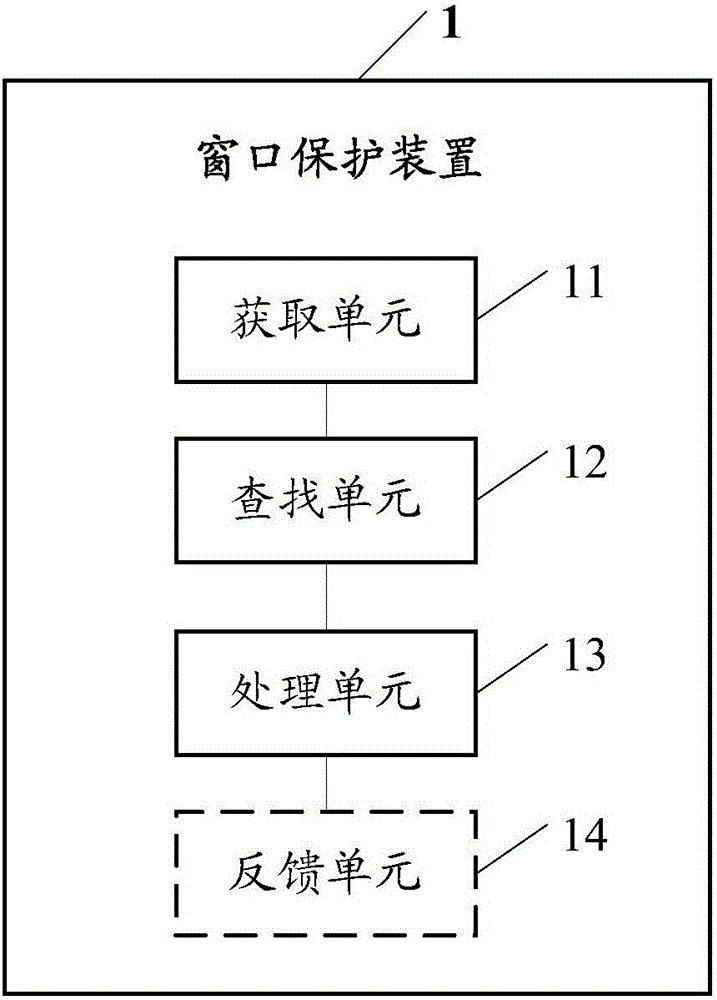
Window protection method and apparatus, and terminal
InactiveCN106022119AAchieve protectionIntercept in timePlatform integrity maintainanceMalwareProcess information
Embodiments of the present invention provide a window protection method and apparatus, and a terminal. The method comprises the following steps of when detecting a call request of a window destructor function for a target window, obtaining first process information corresponding to a first process transmitting the call request, the window destructor function being a system kernel function; searching whether the first process information exists in preset characteristic information; and if so, rejecting the call request. By adoption of the window protection method and apparatus, the problem that the window is closed due to the fact that the window destructor function of the system kernel is called by malicious software can be solved.
Owner:ZHUHAI BAOQU TECH CO LTD
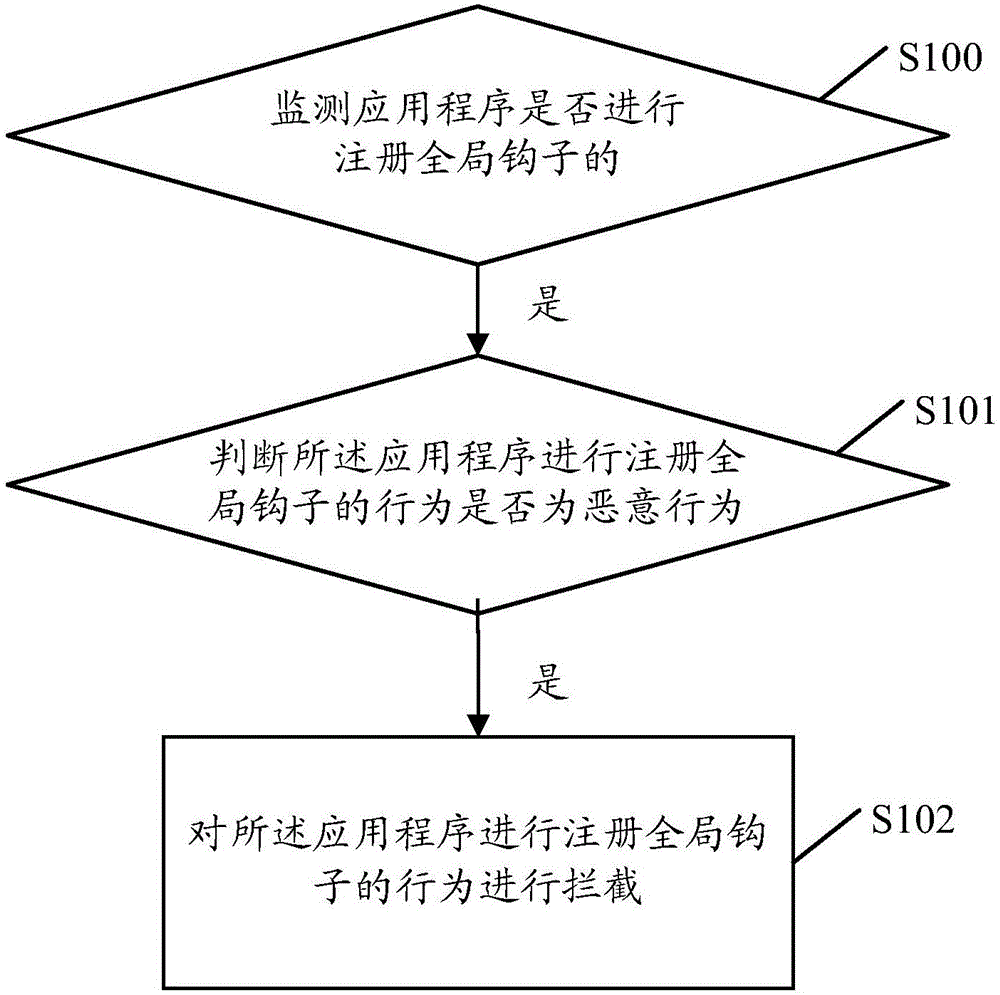
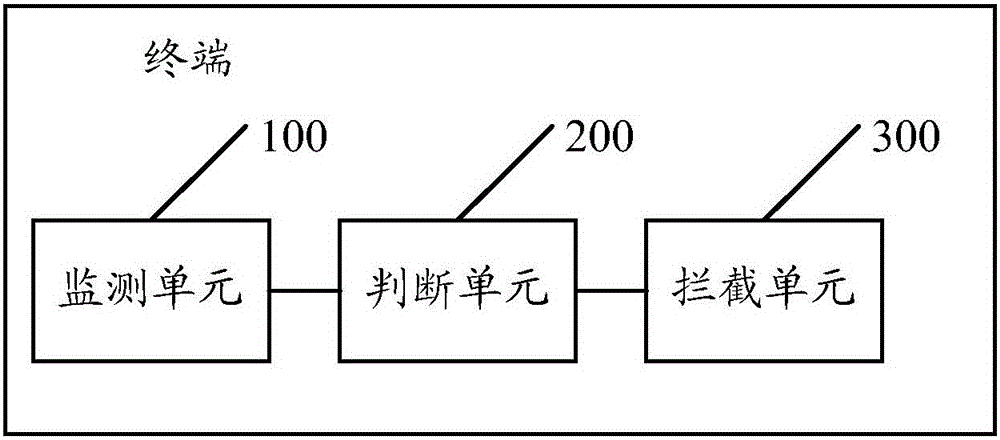
Method for intercepting application program behavior, and terminal
ActiveCN106127032AImprove securityIntercept in timePlatform integrity maintainanceComputer securityApplication software
An embodiment of the invention discloses a method for intercepting application program behaviors. The method comprises: monitoring whether an application program registers a global hook; when the application program registers the global hook is monitored, determining whether the behavior of registering the global hook by the application program is a malicious behavior; when the behavior of registering the global hook by the application program is determined to be a malicious behavior, intercepting the behavior of the application program registering the global hook. An embodiment of the invention also discloses a terminal. Using the method can prevent a malicious program from registering hook, and prevent damages on a terminal system, so as to improve security of the terminal.
Owner:ZHUHAI BAOQU TECH CO LTD
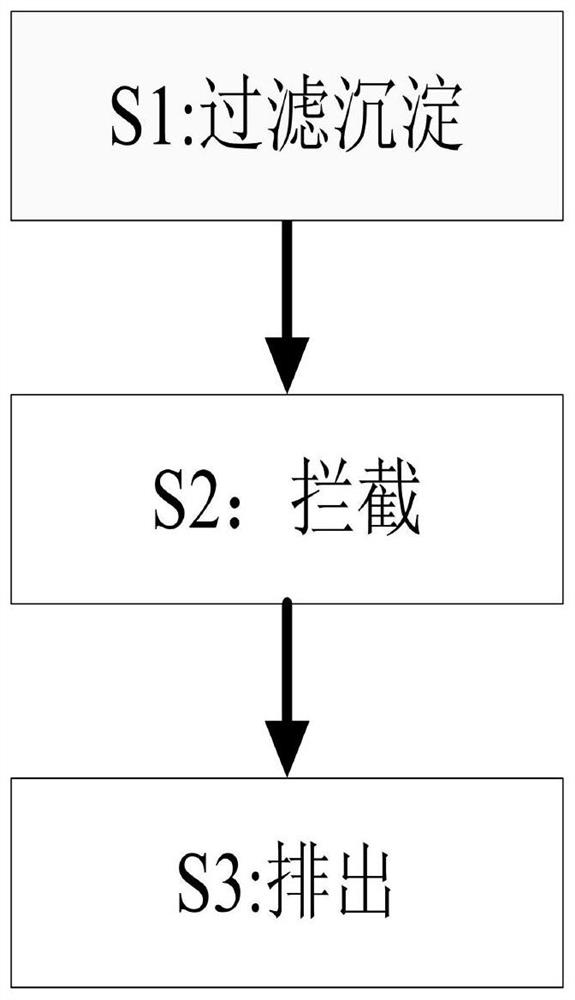
Metal chemical polishing waste liquid renewable resource utilization treatment process
ActiveCN111888835AEasy dischargeImprove work efficiencyFiltration circuitsEnvironmental engineeringRenewable resource
The invention provides a metal chemical polishing waste liquid renewable resource utilization treatment process. Operation is completed through cooperation of an outer frame, a cover body, a filteringunit, a sedimentation unit, a discharging opening and a sealing block. The problems that after waste residues are precipitated at the bottom, when waste liquid is discharged, part of precipitates canbe discharged along with the surging waste liquid, a small amount of waste residues still exist in the discharged polishing waste liquid, a small amount of waste residues are still difficult to separate from the waste liquid even if the waste residues are precipitated and discharged multiple times, and the overall working efficiency is reduced due to multiple times of precipitation can be solved.
Owner:佛山市铂朗环境科技有限公司
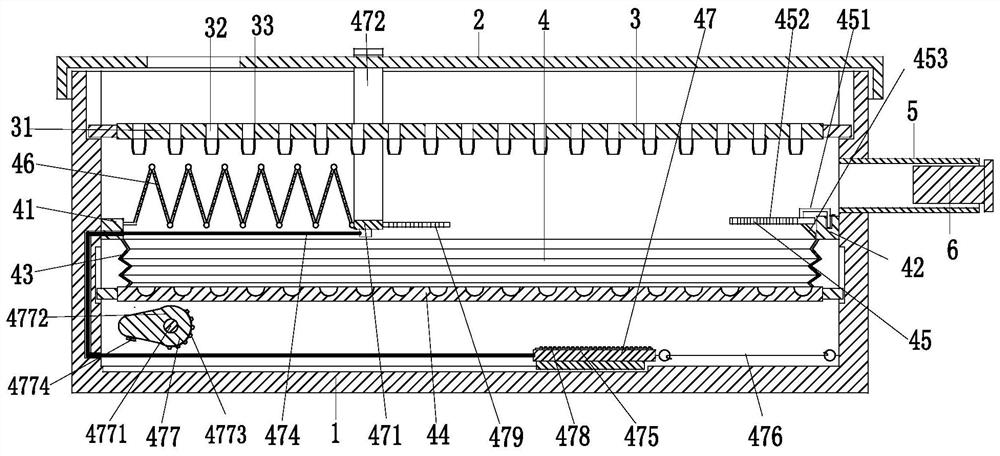
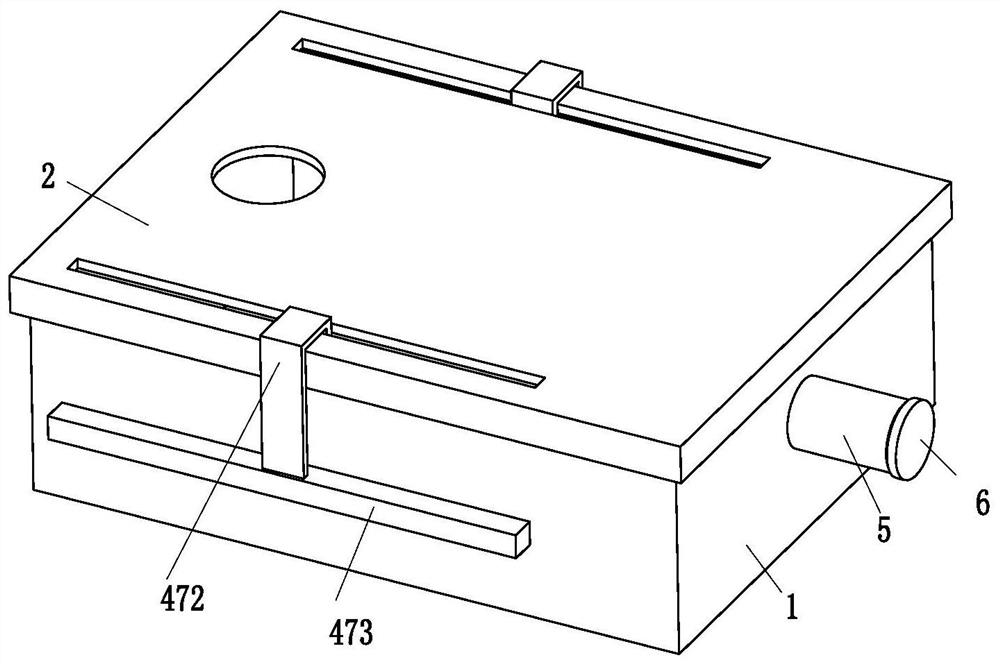
Battery cell dispensing quality detection method
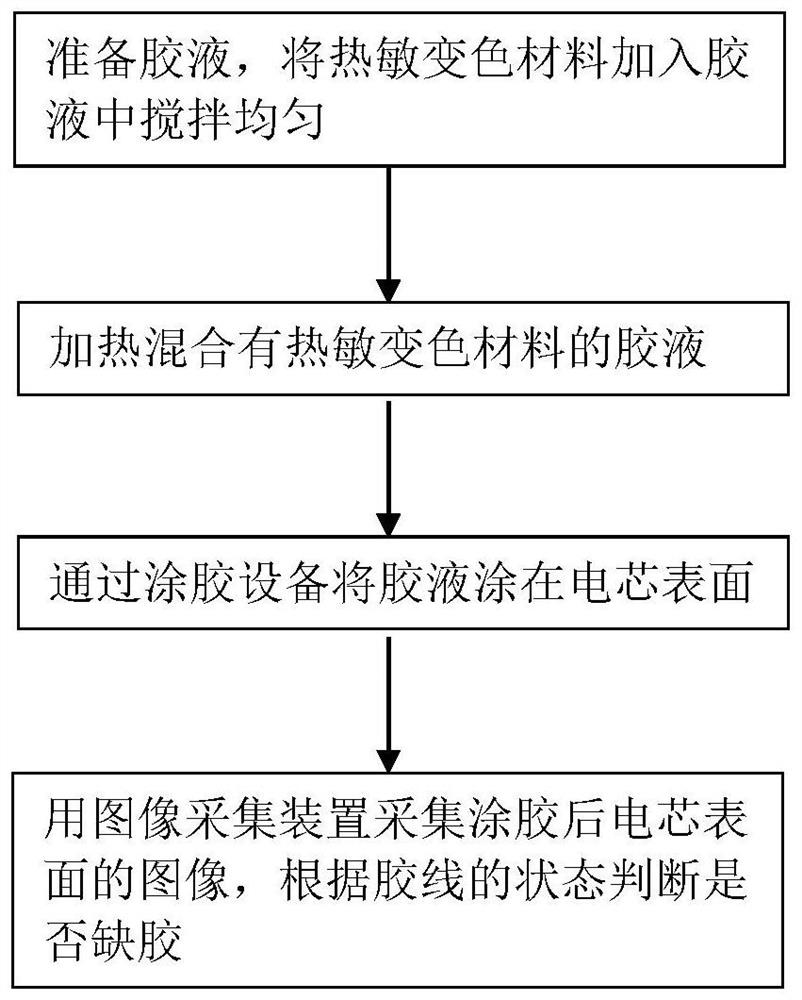
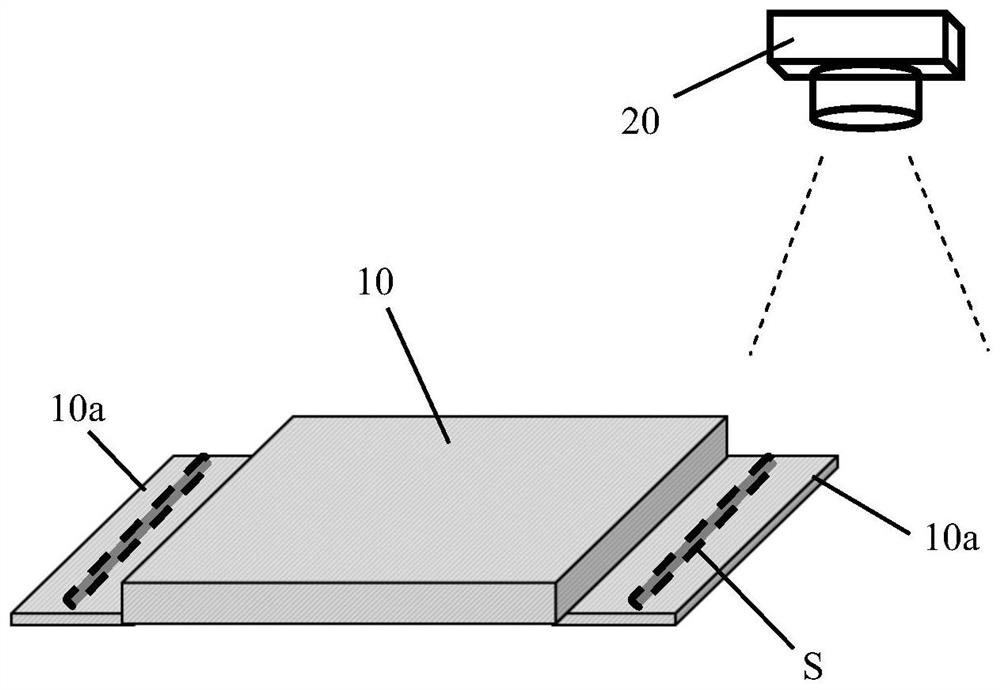
PendingCN114324198AReduce the risk of ultra-wideIntercept in timeColor/spectral properties measurementsImage InspectionEngineering
A battery cell dispensing quality detection method comprises the following steps: preparing a glue solution, adding a reversible thermo-sensitive color-changing material into the glue solution, and uniformly stirring the reversible thermo-sensitive color-changing material and the glue solution; heating the glue solution to enable the glue solution to be in a fluid state; coating a gluing position on the surface of the battery cell with the glue solution mixed with the reversible thermosensitive color-changing material; an image of the surface of the glued battery cell is collected through an image collecting device, and whether the glue line is lack of glue or not is checked. According to the method, the reversible thermosensitive color-changing material is added into the glue solution, and the glue line formed by the glue solution can change color at different temperatures, so that the glue line has a color obviously different from that of an aluminum-plastic film during detection, the state of the glue line can be conveniently detected, the glue line does not develop color at normal temperature, and the appearance of a battery is not influenced. The detection method disclosed by the invention does not need to add new detection equipment or change a battery cell preparation process, and is simple and easy to use.
Owner:重庆冠宇电池有限公司
Quantitative fertilizing machine
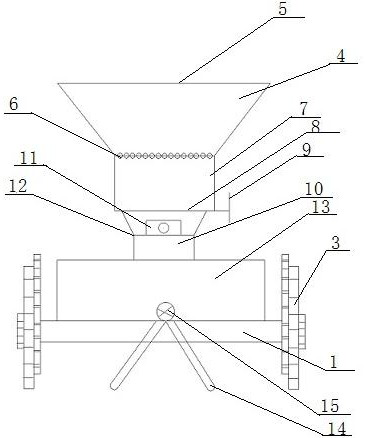
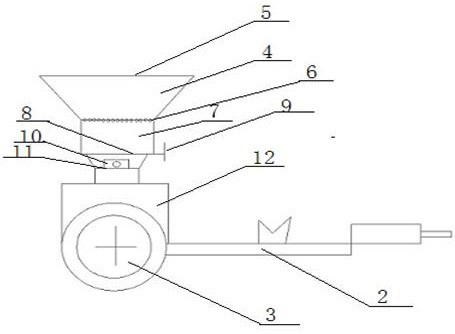
InactiveCN112400436AApply fertilizer evenlyIntercept in timeFertiliser distributersAgricultural scienceAgricultural engineering
The invention belongs to the field of agricultural fertilizing instruments, and particularly relates to a quantitative fertilizing machine. The quantitative fertilizing machine comprises a fertilizingdevice and a supporting device, wherein the fertilizing device comprises a fertilizer box, a fertilizer box cover, a filter sieve, a filter material box, a striker plate, a discharging pipe, a storage box and a fertilizing pipe; the fertilizer box cover is arranged at the top of the fertilizer box and matched with the fertilizer box, the filter sieve is arranged at the bottom of the fertilizer box, the filter material box is arranged below the filter sieve, the striker plate is arranged at the bottom of the filter material box, the discharging pipe is arranged below the filter material box, afertilizer batcher is arranged on the outer wall of the discharging pipe, and the other end of the discharging pipe is connected with the storage box; and the fertilizing pipe is arranged at the bottom of the storage box, and a switch for controlling a discharge port is arranged at the outer side of the storage box. The filter sieve can ensure uniform texture of the applied fertilizer; the striker plate and an intercepting plate can intercept excessive fertilizer in time; the fertilizer batcher can ensure scientific fertilization; the storage box can ensure the continuity of the fertilizationprocess; and the fertilizing pipe can ensure fertilization in different directions.
Owner:曲靖市马龙区品康农业科技有限公司
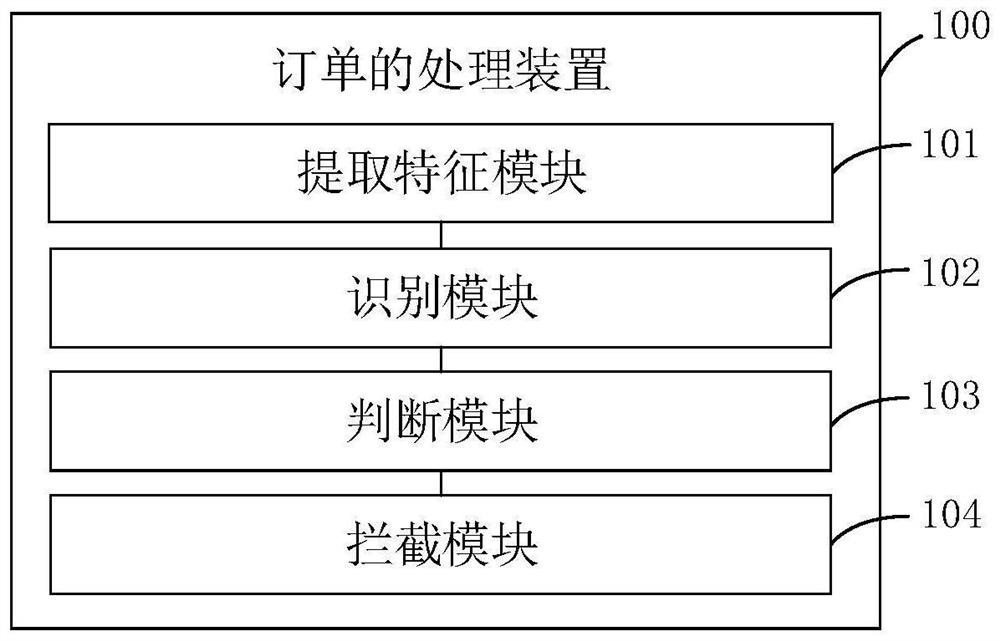
Order processing method and device, equipment and storage medium
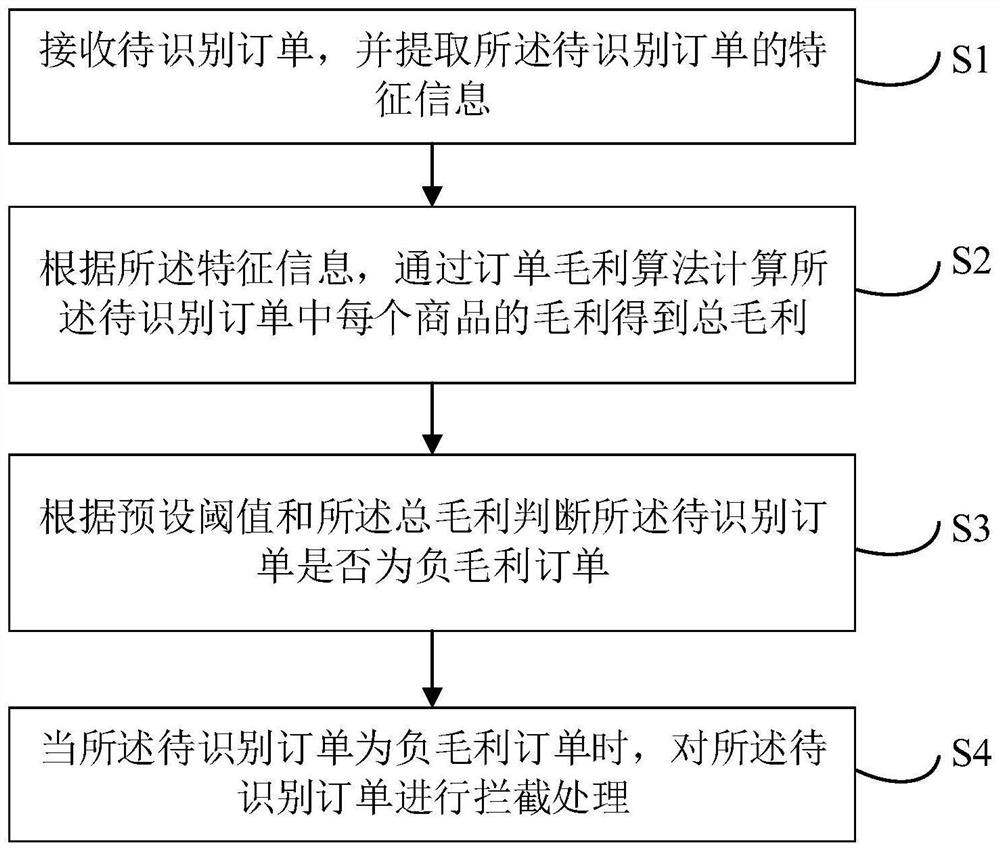
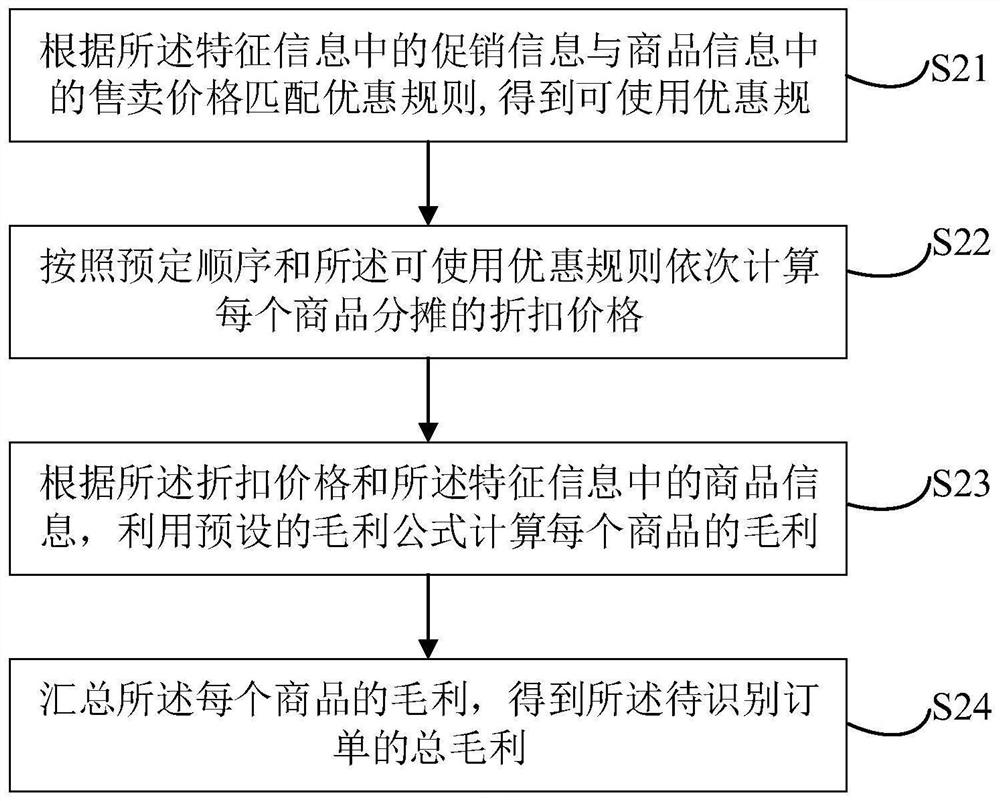
PendingCN114596125AExpand the scope ofImprove efficiencyBuying/selling/leasing transactionsMarketingBlockchainOrder processing
The invention relates to a big data technology, and discloses an order processing method comprising the following steps: receiving a to-be-identified order, and extracting feature information of the to-be-identified order; according to the feature information, calculating gross profit of each commodity in the to-be-identified order through an order gross profit algorithm to obtain total gross profit; judging whether the to-be-identified order is a negative gross profit order or not according to a preset threshold value and the total gross profit; and when the to-be-identified order is the negative gross profit order, intercepting the to-be-identified order. In addition, the invention also relates to a block chain technology, and the to-be-identified order can be stored in a node of a block chain. The invention further provides an order processing device, electronic equipment and a storage medium. According to the invention, the problem that negative gross profit orders cannot be timely and effectively identified and intercepted can be solved.
Owner:KANG JIAN INFORMATION TECH (SHENZHEN) CO LTD
Production process intelligent control system and method
ActiveCN103197640BExtend your lifeImprove integrityTotal factory controlProgramme total factory controlUser inputIntelligent management
The invention provides an intelligent management and control system of a manufacturing technique. The intelligent management and control system comprises one or a plurality of working procedure computers corresponding to each manufacturing working procedure, the working procedure computers are connected with a server through a router to form a local area network; client ends of a working procedure data base are installed on the working procedure computers, entering interfaces corresponding to working procedures are provided, and each entering interface at least comprises an input box of product ID numbers; a user inputs production information corresponding to the working procedures after the working procedures are finished, and then the working procedure computers send the production information corresponding to the working procedures to the server through the local area network; and data bases of each working procedure are installed on the server, and data bases of each working procedure are mutually connected. The server receives the production information which corresponds to the working procedures and is sent from each working procedure computer, checks and tests validity of contents in the production information, feeds back mistake contents in the production information to the corresponding working procedure computers, gives an alarm and prompts. The intelligent management and control system is used for managing and controlling a manufacturing process.
Owner:江苏润达光伏无锡有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com