Attack path restoration method, device, equipment and storage medium
A technology of attack path and storage medium, which is applied in the direction of secure communication devices, digital transmission systems, instruments, etc., and can solve the problem that the application effect of prior knowledge is not universal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
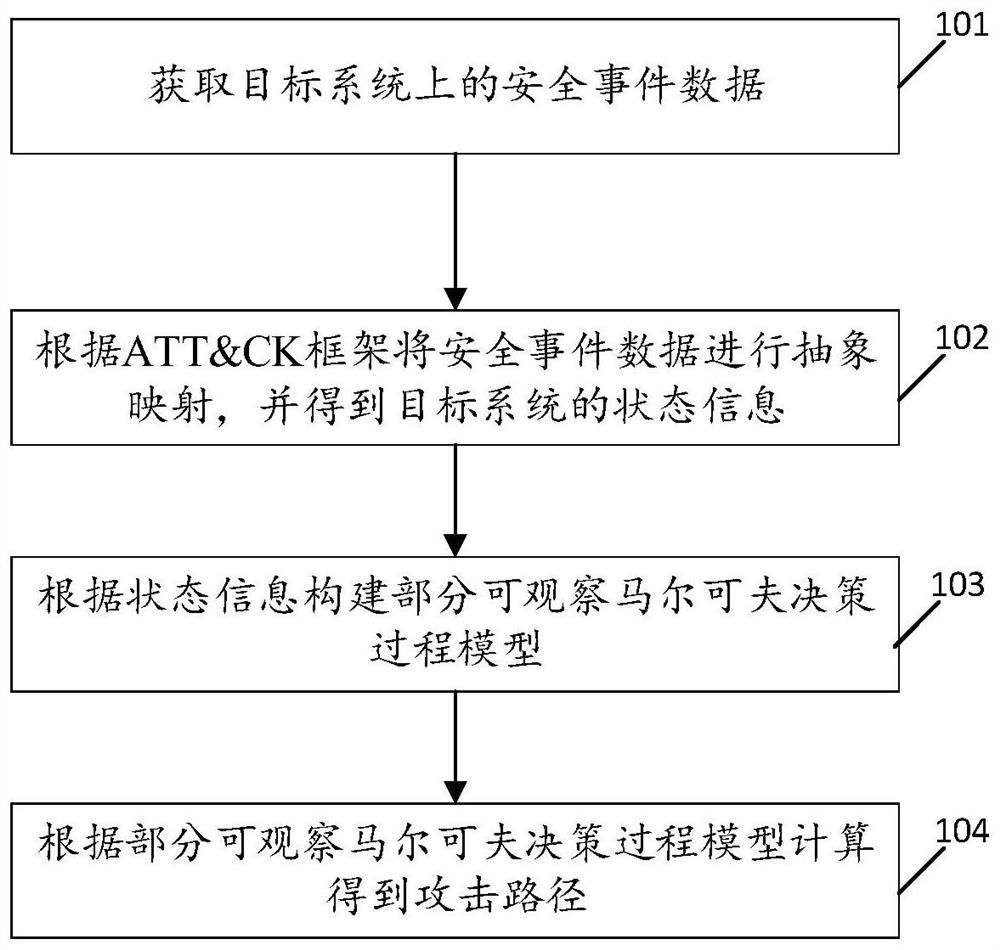
[0044] see figure 1 , figure 1 It is a schematic flowchart of an attack path restoration method disclosed in the embodiment of the present application. Such as figure 1 As shown, the method of the embodiment of the present application includes steps:
[0045] 101. Obtain security event data on the target system;
[0046] 102. Abstractly map the security event data according to the ATT&CK framework, and obtain the status information of the target system;
[0047] 103. Construct a partially observable Markov decision process model based on state information;
[0048] 104. The attack path is calculated according to the partially observable Markov decision process model.
[0049] In the embodiment of the present application, the state information of the target system can be obtained by abstractly mapping the security event data according to the ATT&CK model, wherein the state information of the target system includes the state information of multiple stages of the target system...
Embodiment 2
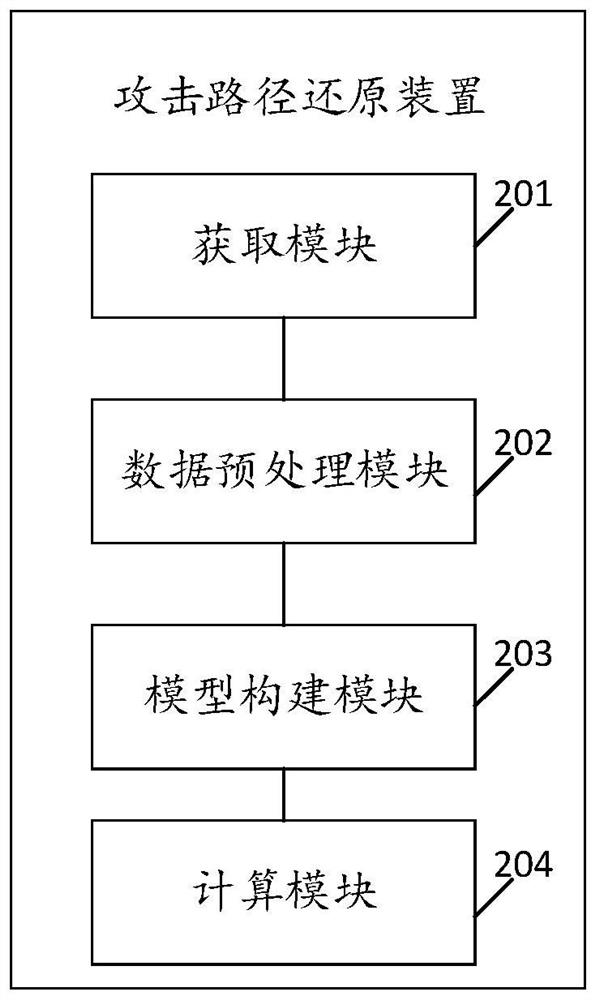
[0087] see figure 2 , figure 2 It is a schematic structural diagram of an attack path restoration device disclosed in the embodiment of the present application. Such as figure 2 As shown, the attack path restoration device in the embodiment of the present application includes:
[0088] An acquisition module 201, configured to acquire security event data on the target system;
[0089] A data preprocessing module 202, configured to abstractly map the security event data according to the ATT&CK framework, and obtain status information of the target system;
[0090] A model construction module 203, configured to construct a partially observable Markov decision process model according to state information;
[0091] The calculation module 204 is configured to calculate an attack path according to a partially observable Markov decision process model.
[0092] Compared with the prior art, the device of the embodiment of the present application can start from the actual securit...
Embodiment 3
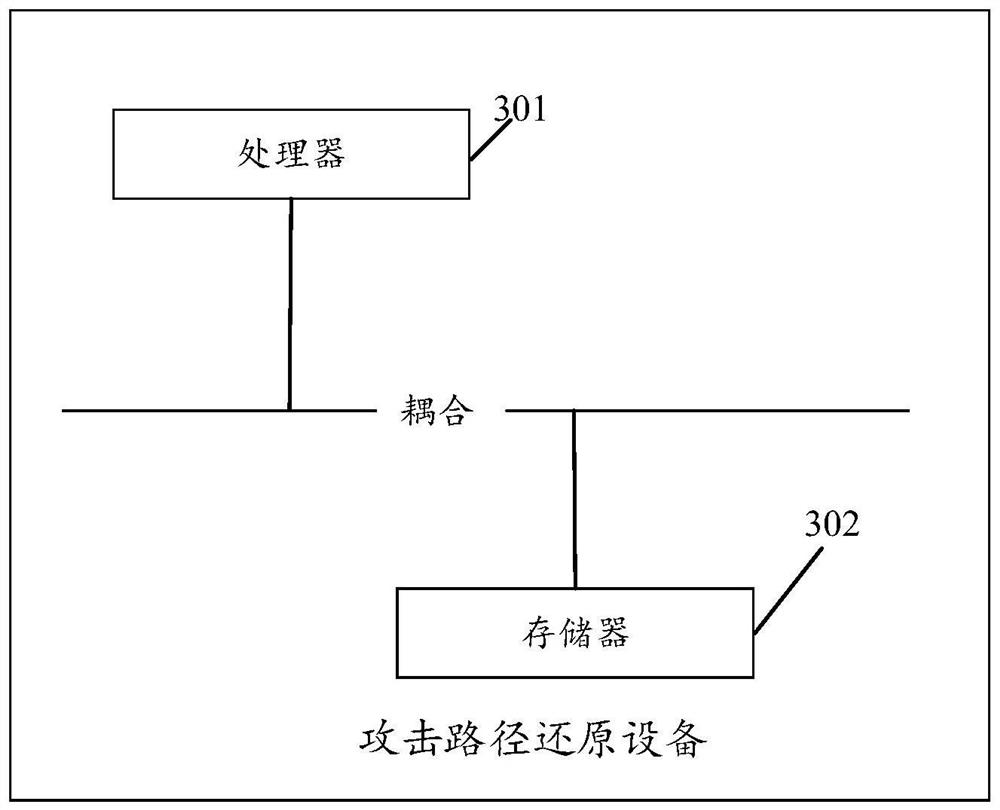
[0128] see image 3 , image 3 It is a schematic structural diagram of an attack path restoration device disclosed in the embodiment of the present application. Such as image 3 As shown, the attack path restoration device in the embodiment of the present application includes:
[0129] Processor 301;
[0130] The memory 302 is configured to store machine-readable instructions, and when the instructions are executed by the processor, execute the method for restoring an attack path according to Embodiment 1 of the present application.
[0131] Compared with the existing technology, the device in the embodiment of the present application can start from the actual security alarm event data, use the ATT&CK framework to abstract the state of the system and the attack execution action to form a partially observable Markov decision process model, so as to Under the assumption that the attacker has a clear intention but the attack process is complex, the attack process is modeled i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com