Risk prevention and control method, device and equipment based on privacy protection
A privacy protection and risk control technology, applied in the computer field, can solve the problems of inability to meet the decision-making needs of risk prevention and control in complex scenarios, and the inability of the sender or receiver to perceive, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
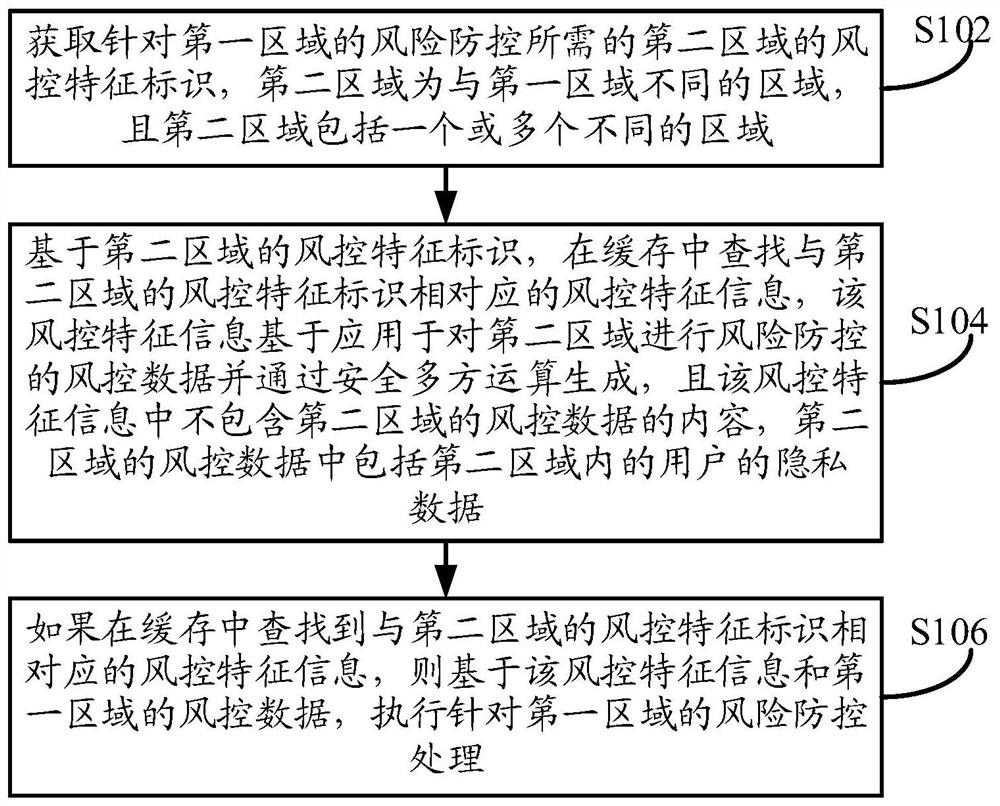
[0028] Such as figure 1 As shown, the embodiment of this specification provides a risk prevention and control method based on privacy protection. The execution subject of the method can be a terminal device or a server, wherein the terminal device can be a computer device such as a laptop or a desktop computer, or it can be such as For mobile terminal devices such as mobile phones or tablets, the server can be an independent server or a server cluster composed of multiple servers. The server can be used for a certain business (such as transaction business, financial business or instant messaging Business, etc.) background server. The terminal device or the server may be a terminal device or a server applied in the first area. In this embodiment, the execution subject is taken as an example for detailed description. For the case that the execution subject is a terminal device, processing may be based on the following content, which will not be repeated here. The method specif...
Embodiment 2
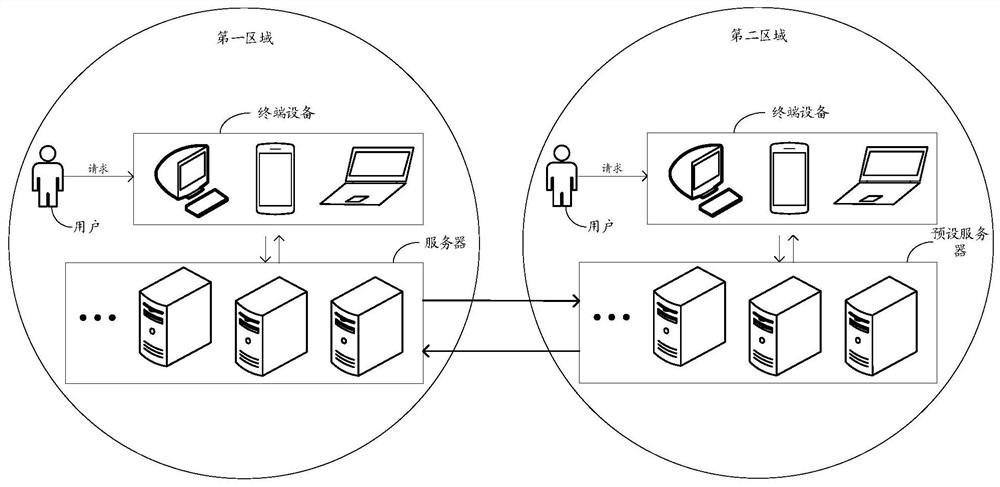
[0045] Such as image 3 As shown, the embodiment of this specification provides a risk prevention and control method based on privacy protection. The execution subject of the method can be a terminal device or a server, wherein the terminal device can be a computer device such as a laptop or a desktop computer, or it can be such as For mobile terminal devices such as mobile phones or tablets, the server can be an independent server or a server cluster composed of multiple servers. The server can be used for a certain business (such as transaction business, financial business or instant messaging Business, etc.) background server. The terminal device or the server may be a terminal device or a server applied in the first area. In this embodiment, the execution subject is taken as an example for detailed description. For the case that the execution subject is a terminal device, processing may be based on the following content, which will not be repeated here. The method specif...
Embodiment 3
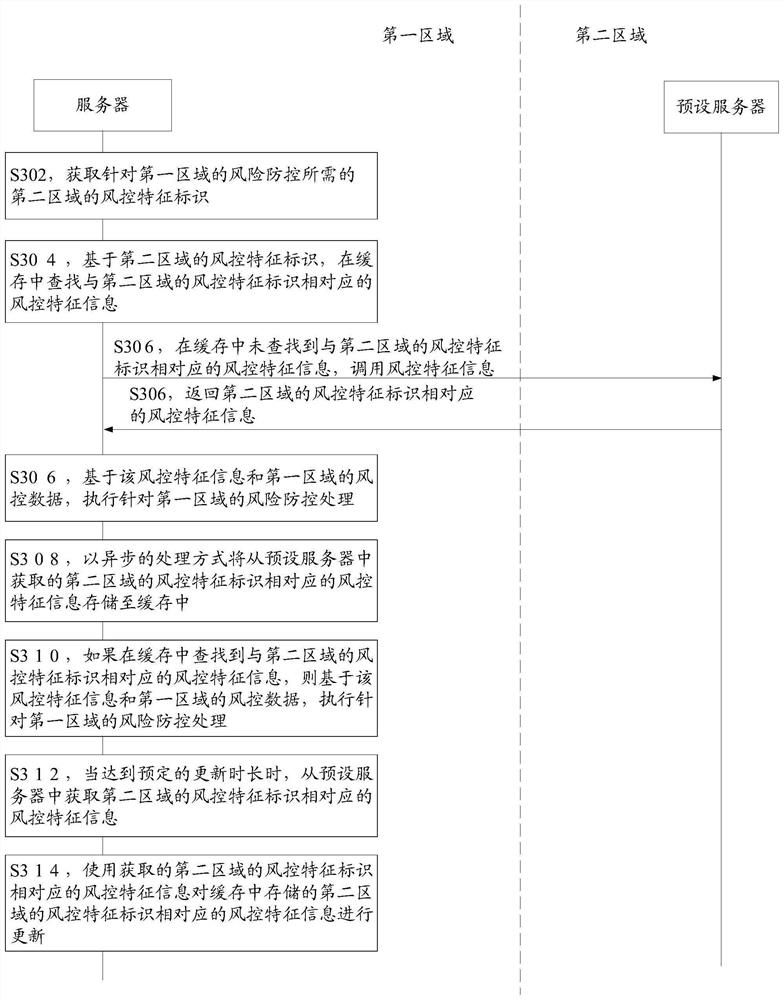
[0066] Such as Figure 4 As shown, the embodiment of this specification provides a risk prevention and control method based on privacy protection. The execution subject of the method can be a terminal device or a server, wherein the terminal device can be a computer device such as a laptop or a desktop computer, or it can be such as For mobile terminal devices such as mobile phones or tablets, the server can be an independent server or a server cluster composed of multiple servers. The server can be used for a certain business (such as transaction business, financial business or instant messaging Business, etc.) background server. The terminal device or the server may be a terminal device or a server applied in the first area. In this embodiment, the execution subject is taken as an example for detailed description. For the case that the execution subject is a terminal device, processing may be based on the following content, which will not be repeated here. The method speci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com