Service authorization method and communication device
一种服务授权、通信装置的技术,应用在通信领域,能够解决第一服务器访问第二服务器未获服务授权等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
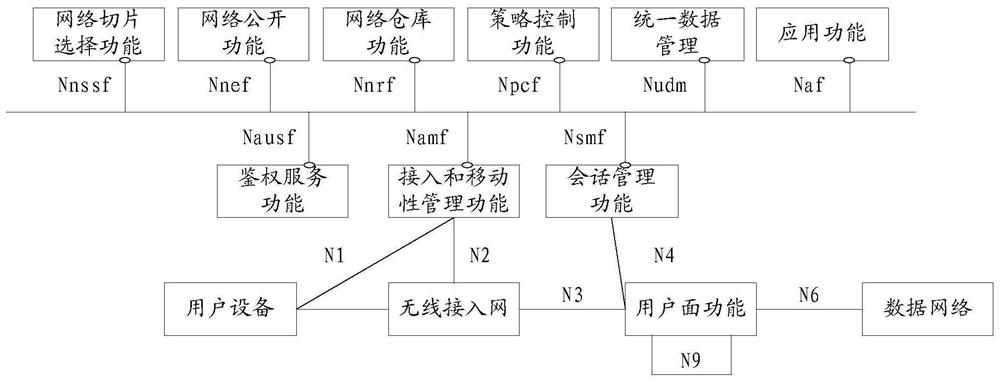
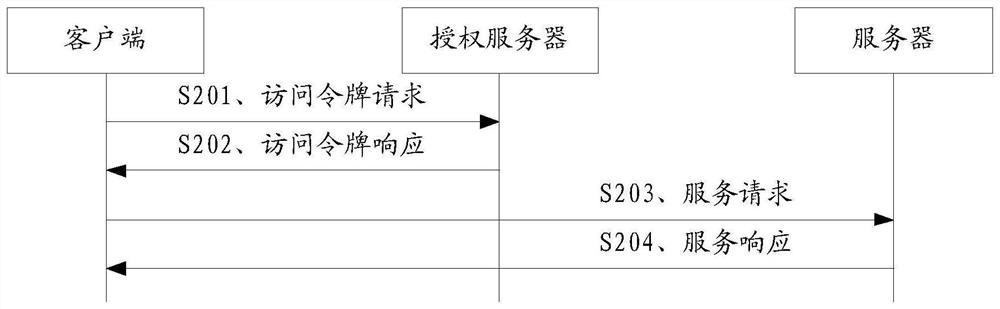
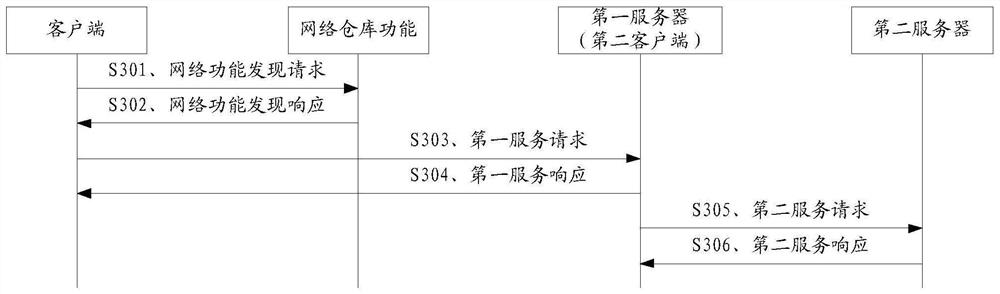
[0146] Embodiment 1, the above access token request message may also carry the network function type of the client and / or the network function type of the first server, the network function type of the second server and a list of expected service names, so that the authorization server can The function type and / or the network function type of the first server, the network function type of the second server and the expected service name list, determine the second server that authorizes the client and / or the first server to access the network function type, and generate access token. The access token also includes a list of network function types and desired service names of the second server.
Embodiment approach 2
[0147] Embodiment 2, the above access token request message may also carry the instance identifier of the second server and a list of expected service names. For example, the desired server's service name list may include one or more second server's service names. So that the authorization server determines the second server corresponding to the instance identifier of the second server authorized to access the client and / or the first server according to the instance identifier of the second server and the expected service name list. Therefore, optionally, the above-mentioned access token may also include an instance identifier and a list of service names of the second server.
[0148]Optionally, in the above two implementation manners, the access token may further include an instance identifier of the authorization server, which is used to indicate the identity information of the authorizer of the access token.
[0149] Optionally, in the above two implementation manners, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com