Techniques for preventing collusion using simultaneous key release
A user, cryptographic key technology, applied to key distribution, can solve problems such as hindering the fair distribution of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In the following description, various embodiments will be described. For the purposes of explanation, specific configurations and details are set forth to provide a thorough understanding of the embodiments. However, those skilled in the art will appreciate that embodiments may be practiced without specific details. Moreover, well-known features may be omitted or simplified to avoid obscuring the description.
[0021] The description of some terms prior to the details of some embodiments of the present invention can be conducive to various embodiments.
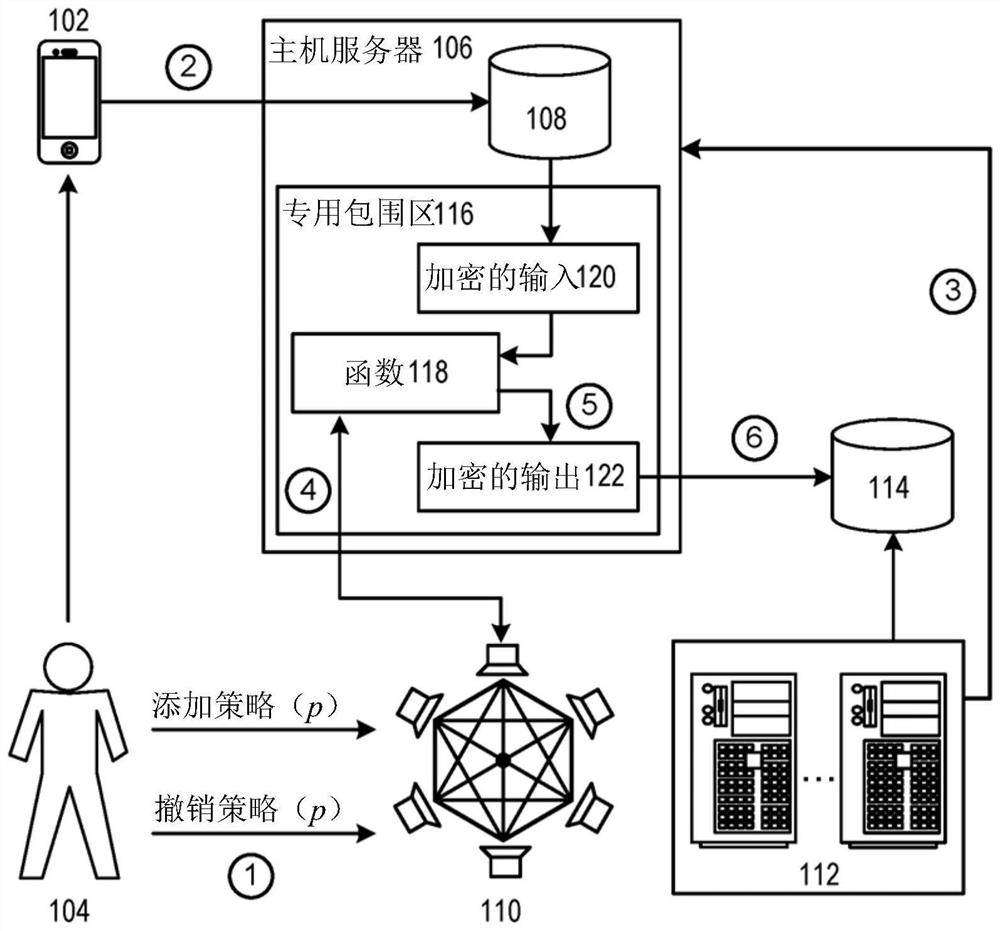
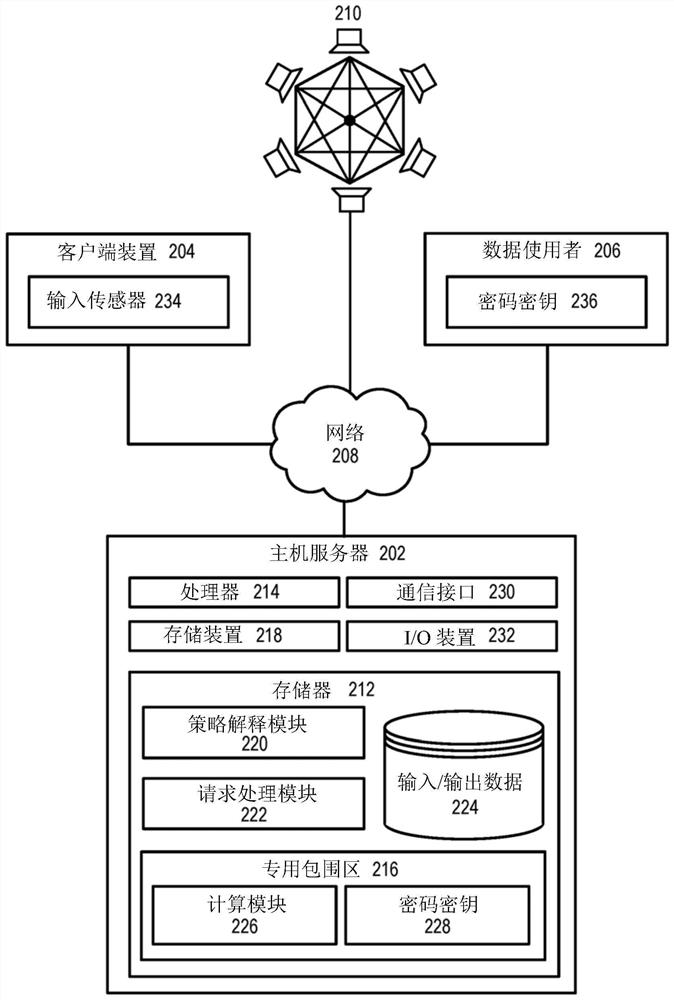
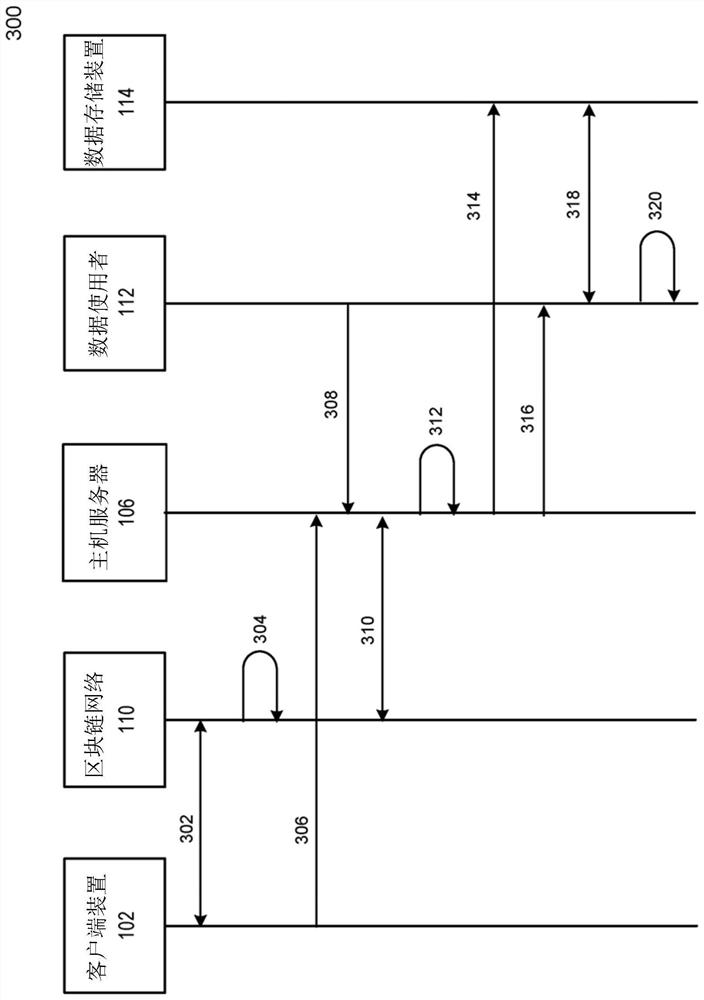
[0022] The "block chain" can include a distributed database. The block chain can be used to maintain a list of records called blocks. The block chain can be used to maintain a record of affairs or events between the parties in a difficult manner. Each block in the block chain can include a number of records, and a hash of the previous block in the block chain. If the record in the previous block changes, the hash in any of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com