Blockchain system and computer-implemented method for detecting an attack on a computer system or computer network
A computer system and computer network technology, applied in the field of blockchain systems, can solve problems such as destroying businesses, complex central analysis institutions, and unattractive economics, so as to solve the problems of single point of failure, easy maintenance and scalability , the effect of reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] exist figure 1 The embodiment of the computer-implemented method according to the invention for detecting an attack on a computer system or a computer network shown in has four steps S10 , S20 , S30 , S40 .
[0053] In step S10 , an analysis device for a computer system or computer network is inserted as a smart contract into a blockchain having a plurality of blocks linked to each other. In step S20, parameters are set for the analysis device. At least some of these parameters correspond to the behavior of the computer system or computer network and have log files of the computer system or computer network. In step S30, the analysis means are executed based on the parameters. In step S40, the analysis result is added to the block chain.
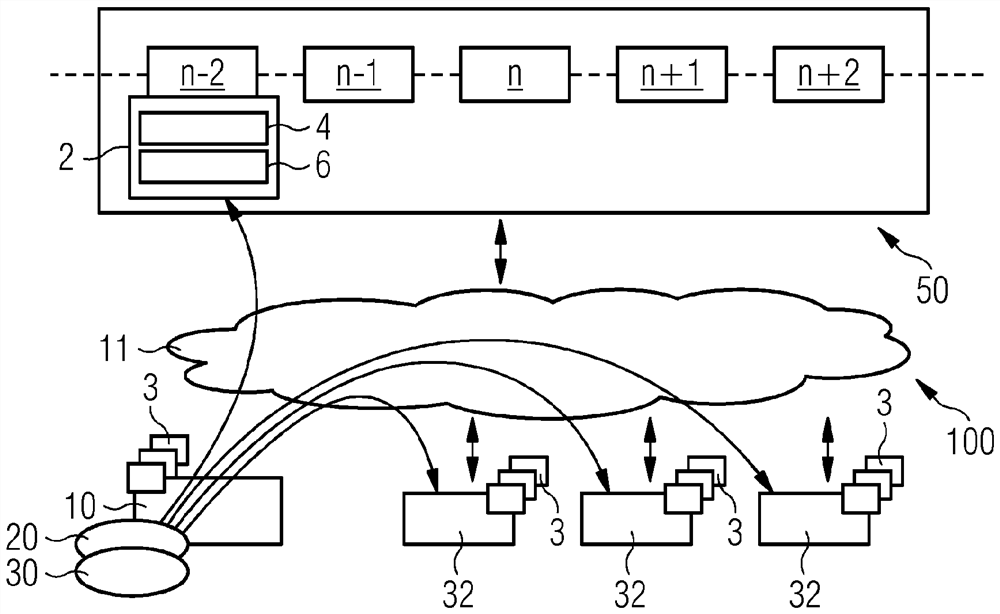
[0054] exist figure 2 The embodiment of a blockchain system 100 for identifying attacks on a computer system or computer network according to the invention shown in has a blockchain 50 with a plurality of blocks n-2 linked to eac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com