Two-party safety comparison method and system
A technology for safety and comparison of results, applied in the field of safety, can solve the problems affecting the application range of MPC and high network cost, and achieve the effect of reducing communication and calculation amount and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
[0030] Before describing the solution provided by the embodiment of the present specification, the inventive concept of the solution is explained as follows.
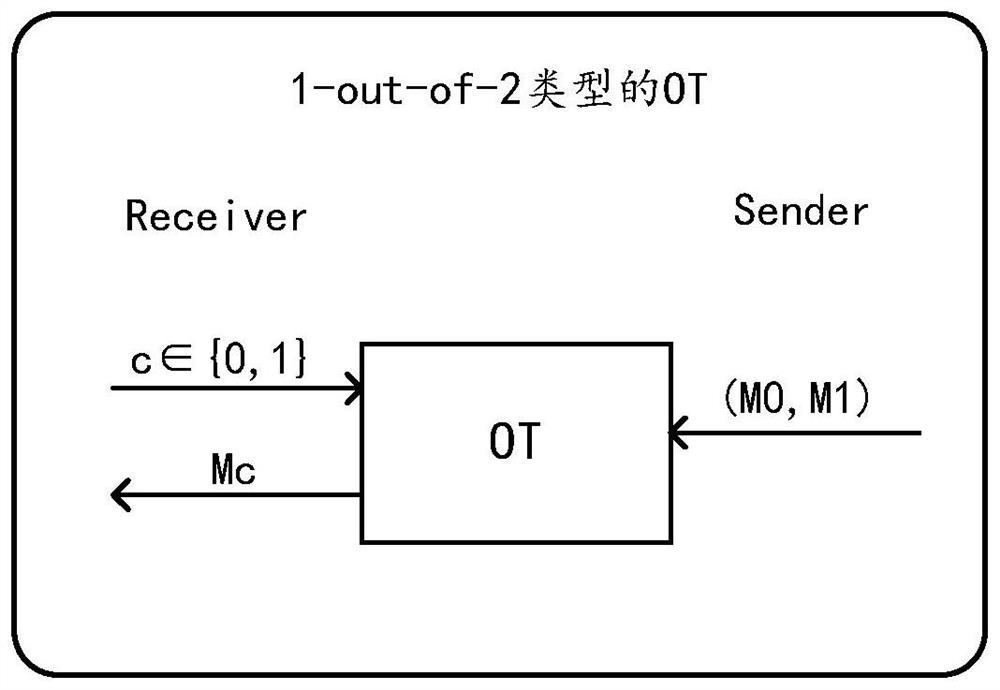
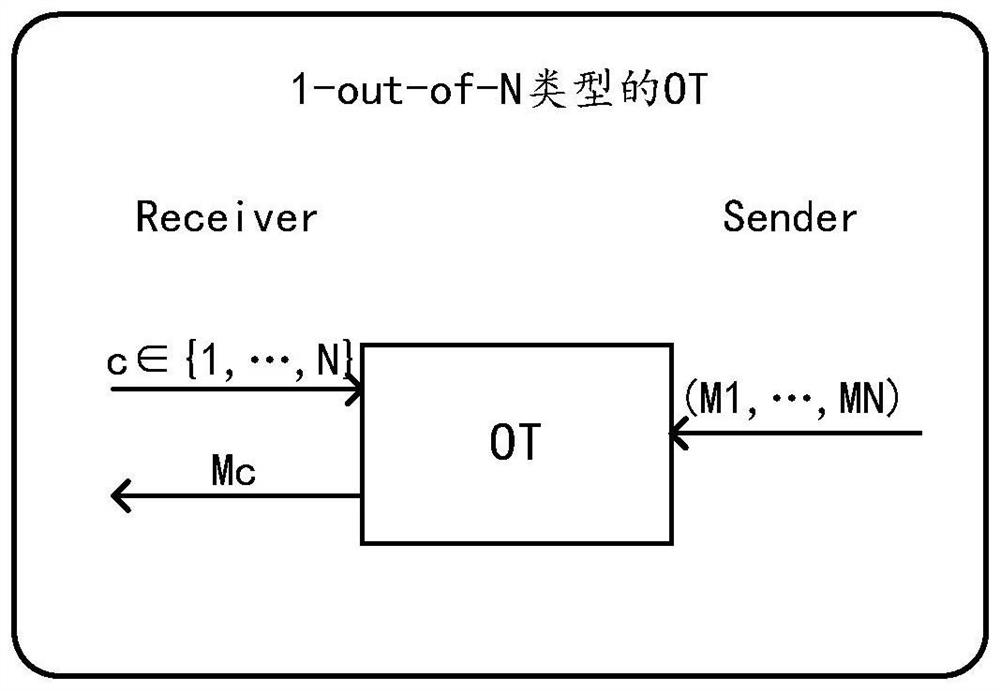
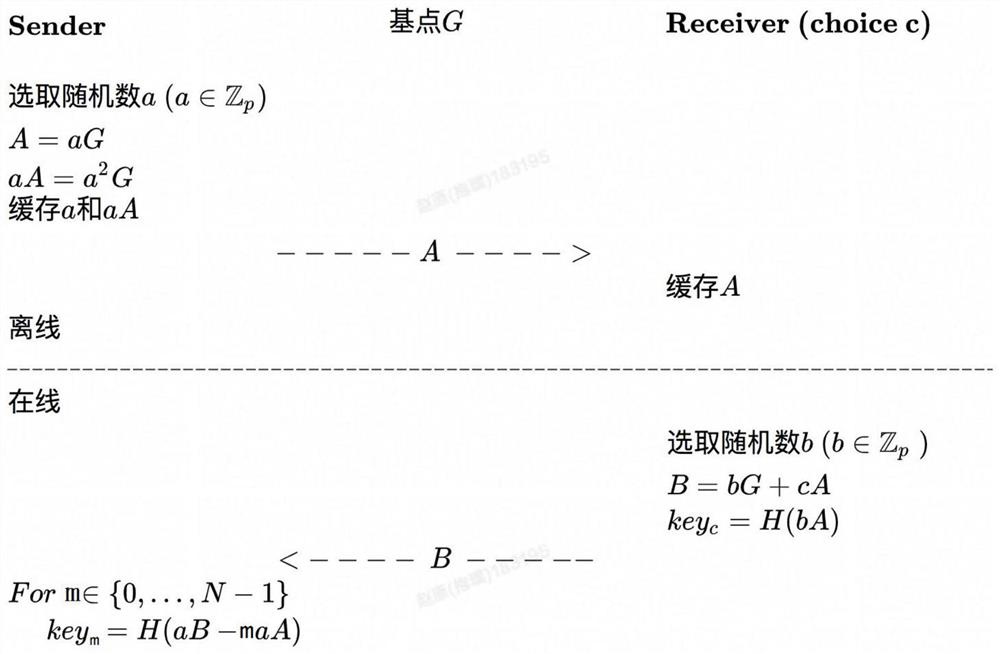
[0031] First of all, in order to further strengthen the privacy protection of the first party (also known as the data requester), the inventor of this application proposes that the first party simultaneously sends n identifiers to the second party, and the n identifiers include the target identifier and n-1 A confusing identification, so that the second party (also known as the data holder) cannot know the data requested by the first party for comparison. In addition, after the comparison is completed, the first party can only obtain the comparison result of the data corresponding to the target identifier, but cannot obtain the comparison result of the data corresponding to other identifiers.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com