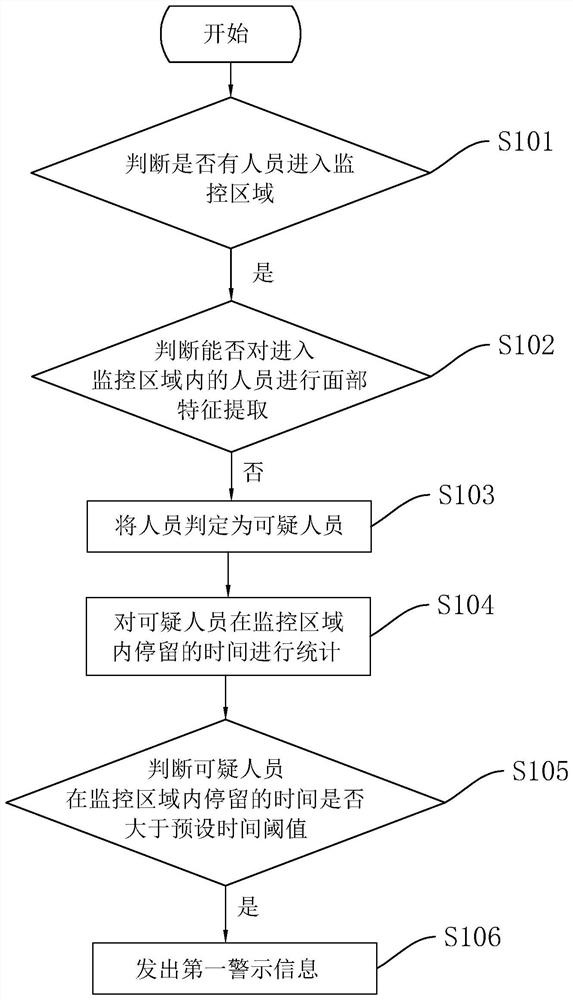
Security monitoring method
A technology for security monitoring and monitoring areas, which is applied in anti-theft alarms, mechanical vibration actuation of anti-theft alarms, instruments, etc. It can solve the problems that it is difficult for staff to take into account the places to be monitored, the effective judgment of monitoring pictures, and the loss of monitoring places.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
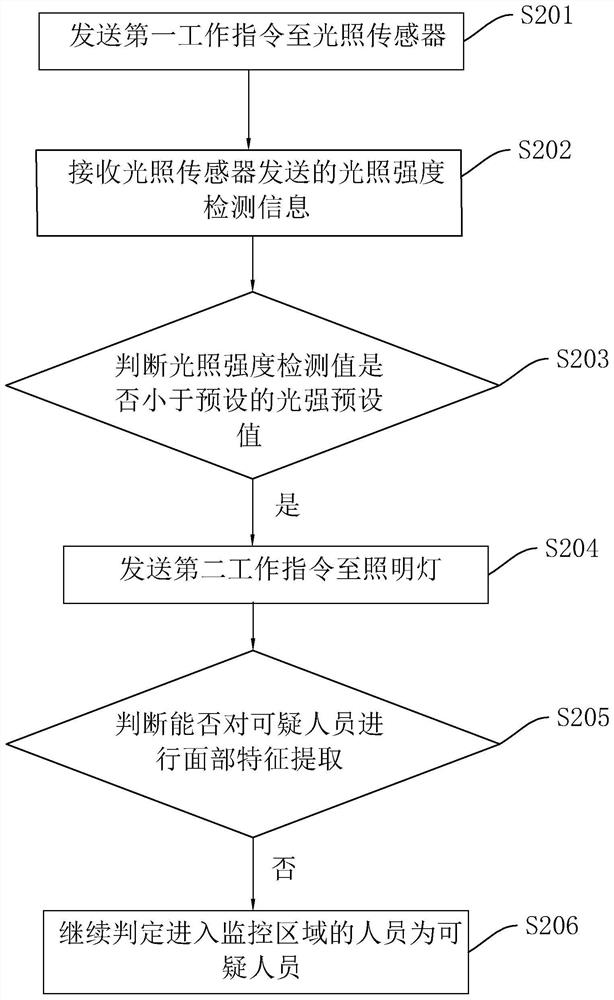
[0076] As another implementation manner of the security monitoring method, after sending the second work order to the lighting lamp, it further includes:
[0077] select and save several images containing suspicious persons; and,
[0078] Send pictures containing suspicious people.
[0079] Specifically, after the server sends the second work instruction to the lighting lamp, the lighting lamp works. At this time, the monitoring area can photograph suspicious persons more clearly than before the lighting lamp works. After the server obtains the video sent by the monitor, it first intercepts the surveillance video, and then judges whether the video frame picture contains suspicious persons through the pedestrian detection algorithm. ) containing a picture of the suspicious person, send the picture containing the suspicious person. Pictures containing suspicious persons can be sent to the smart terminal of the security personnel, or to the monitoring system at the security per...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com