A comprehensive malicious code detection system and method in a power production system
A malicious code detection and power production technology, applied in the field of comprehensive malicious code detection system, can solve the problems of incomplete and missing messages, and achieve the effect of ensuring correctness and smoothness, improving performance, and ensuring delivery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0105] The present invention will be further described below with reference to the accompanying drawings and embodiments.
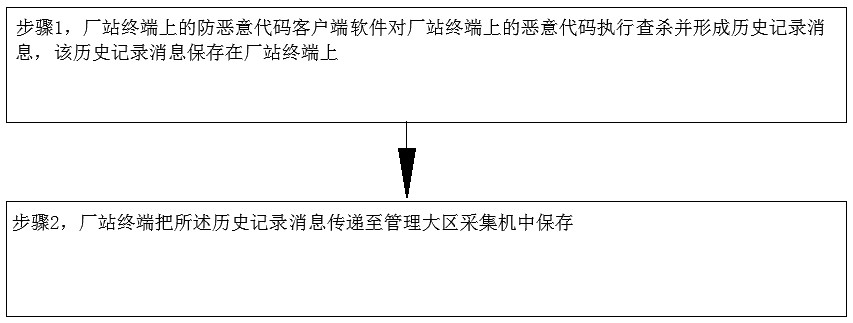
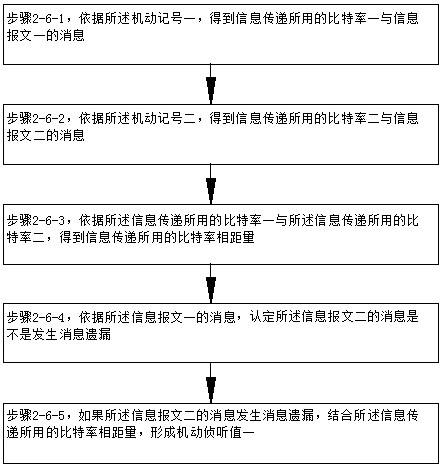
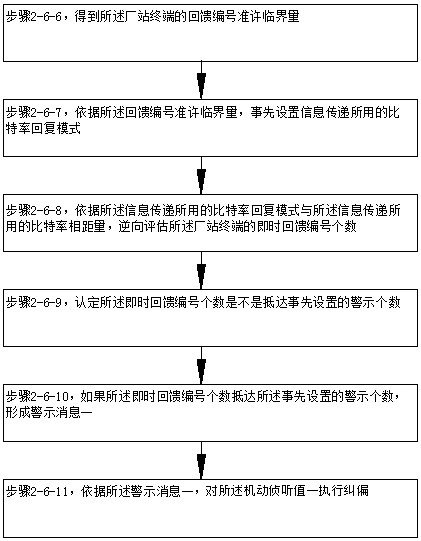
[0106] like Figure 1-Figure 8 As shown, the comprehensive malicious code detection system inside the power production system includes:
[0107] An anti-malicious code client software is set on the factory station terminal in the factory station, and the anti-malicious code client software is used to detect and kill the malicious code on the factory station terminal and form a historical record message; the anti-malicious code client software can be 360 Guard or Jinshan Guard, the factory terminal can be a PC or a server, and the history record message can include the name and size of the malicious code on the factory terminal to be checked and killed, as well as the time when the malicious code was checked and killed. Malicious codes include computer viruses (referred to as viruses), Trojan horses (referred to as Trojan horses), and computer worms (refe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com