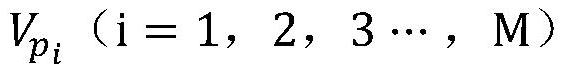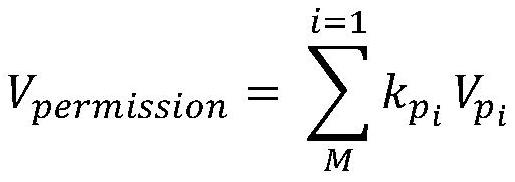Machine learning malicious software detection method based on privilege features and taint features
A malware and machine learning technology, applied in the field of information security, can solve problems such as leaking permissions, reducing the performance and occupation of mobile phones, and achieving the effect of reducing volume and improving classification results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Embodiments of the invention are described in detail below, examples of which are illustrated in the accompanying drawings. The embodiments described below by referring to the figures are exemplary only for explaining the present invention and should not be construed as limiting the present invention.
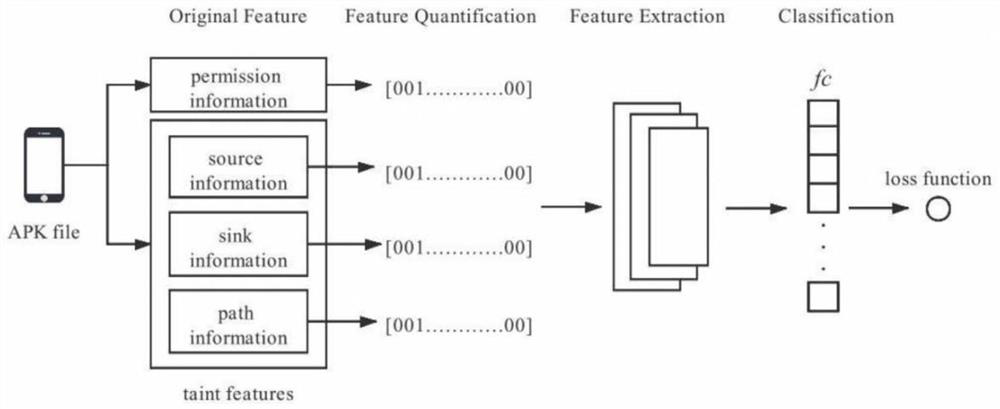
[0044] Such as figure 1 As shown, the present invention provides a kind of machine learning malware detection method based on privilege feature and taint feature, specifically comprises the following steps:
[0045] Step 1, decompress the APK file and obtain the AndroidMainfest.xml file;
[0046] Step 2, decompile the AndroidMainfest.xml file, and extract permission information from it;
[0047] Step 3, use FlowDroid to extract sink features, source features and path features;
[0048] Step 4, calculate the frequency of occurrence of each permission, and obtain the characteristic value table of a single permission;
[0049] First extract M kinds of permissions with the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com