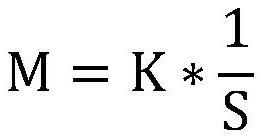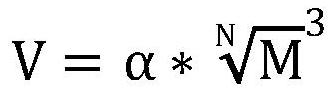Information security processing method based on big data
A technology of information security and processing methods, applied in data processing applications, instruments, character and pattern recognition, etc., can solve problems such as dry eyes, affecting the health of office personnel, oil loss, etc., and achieve the effect of avoiding dryness and pain
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
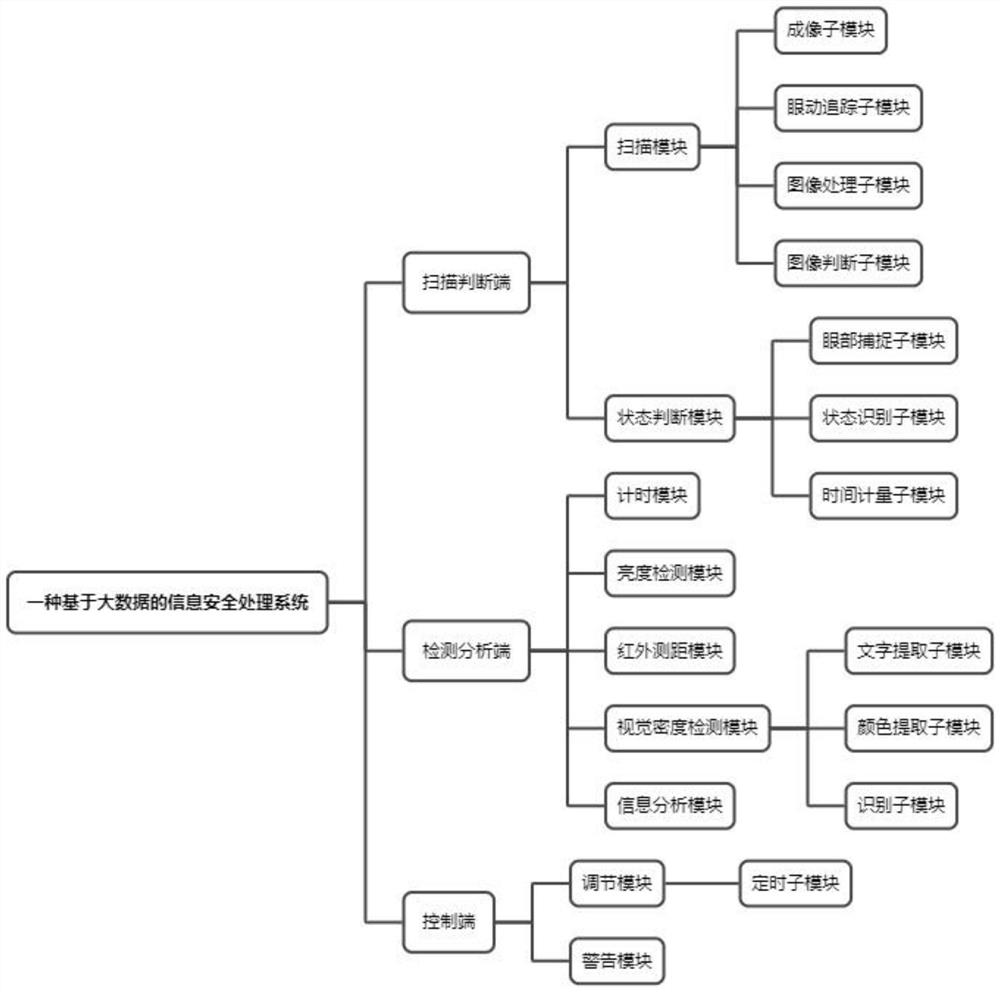
[0076] Example 1: The office staff is in a state of continuous energy and concentrated work. By tracking the eyes of the office staff, the range of the office staff's gaze is judged, and the size of the text extracted within the range is S=5. According to the formula K=2, M=0.4 can be obtained, and the extracted color feature value is N=3, according to the formula α=2, V=0.8 can be obtained, the current brightness of the computer screen is P=0.3, and the working time of the office staff is t=0.2h, according to the formula β=0.5, Q=66.7% can be obtained, and the timing sub-module controls the facial humidifier to be turned on for 5 minutes.
Embodiment 2
[0077] Embodiment 2: The office staff is in a state of continuous energy and concentrated work. By tracking the eyes of the office staff, the range of the office staff's gaze can be judged, and the size of the text extracted within the range is S=2. According to the formula K=2, M=1 can be obtained, and the extracted color feature value is N=6, according to the formula α=2, we can get V=2, the brightness of the current computer screen is P=0.6, and the working time of the office staff is t=2h, according to the formula β=0.5, Q=15.4% can be obtained, the timing sub-module controls the facial humidifier to be turned on for 20 minutes, and the warning module displays a rest warning on the computer.
Embodiment 3
[0078] Embodiment 3: The office staff is in a state of continuous energy and concentrated work. By tracking the eyes of the office staff, the range of the office staff's gaze is judged, and the size of the text extracted within the range is S=8. According to the formula K=2, M=0.25 can be obtained, and the extracted color feature value is N=3, according to the formula α=2, we can get V=0.5, the brightness of the current computer screen is P=0.4, and the working time of the office staff is t=0.2h, according to the formula β=0.5, Q=69.4% can be obtained, and the timer sub-module controls the facial humidifier to be turned on for 5 minutes.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com