Login verification method based on zero knowledge proof
A zero-knowledge proof, login verification technology, applied in user identity/authority verification, digital transmission systems, secure communication devices, etc., can solve the problem of low security of account login verification, and achieve the effect of improving account security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
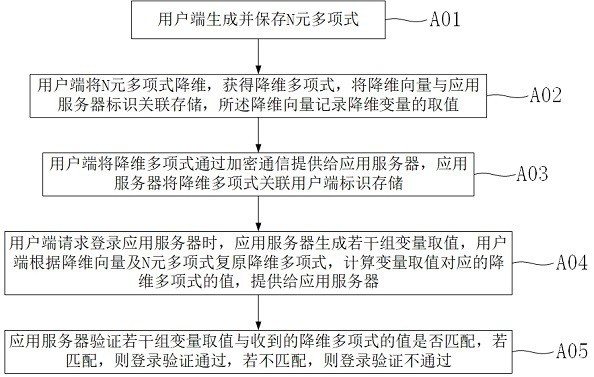
[0019] A login verification method based on zero-knowledge proof, please refer to the attached figure 1 , including the following steps: step A01) the user end generates and saves the N-ary polynomial; step A02) the user end reduces the dimension of the N-ary polynomial to obtain the dimensionality reduction polynomial, stores the dimensionality reduction vector in association with the application server ID, records the dimensionality reduction vector The value of the dimension variable; Step A03) The client provides the dimensionality reduction polynomial to the application server through encrypted communication, and the application server stores the dimensionality reduction polynomial in association with the client ID; Step A04) When the client requests to log in to the application server, the application server generates a number of The value of the group variable, the client restores the dimensionality reduction polynomial according to the dimensionality reduction vector an...
Embodiment 2
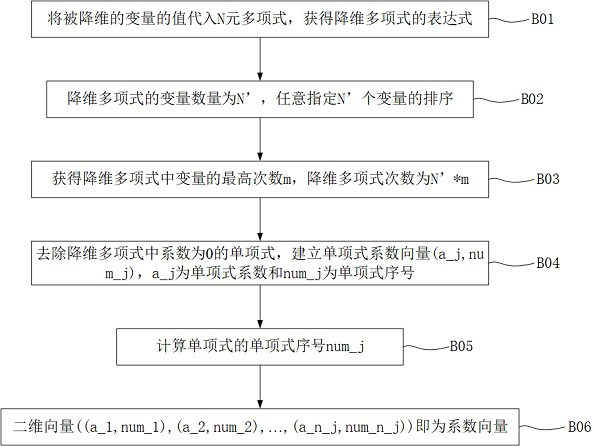
[0026] A login verification method based on zero-knowledge proof, including: the client generates and saves an N-ary polynomial, f(x,y,z,s)=3*x^3*y*z^2*s^3+5 *x^2*y^2*z^3*s+13*x*y^3*z^2*s^2, which is a 4-element polynomial, and the monomial with the highest degree is 3*x^3*y* z^2*s^3, the degree of polynomial is 9 degrees.
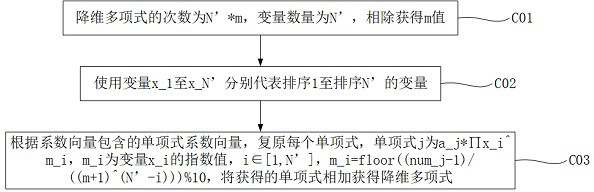
[0027] The client reduces the dimensionality of the N-ary polynomial to obtain the dimensionality reduction polynomial, associates and stores the dimensionality reduction vector with the application server ID, and the dimensionality reduction vector records the value of the dimensionality reduction variable. Specifying s=2, substitute f(x,y,z,s). Obtain the dimensionality reduction polynomial f(x,y,z)=24*x^3*y*z^2+10*x^2*y^2*z^3+52*x*y^3*z^2 . The dimensionality reduction vector is (0,0,0,3), and the corresponding value of x, y, and z in the dimensionality reduction vector is 0, which means that the values of variables x, y, and z are not limited, and...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap