Network access method and device, terminal equipment and network equipment
A network device and access network technology, applied in the field of communication, can solve the problem of tight use of network resources, and achieve the effect of avoiding resource waste
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
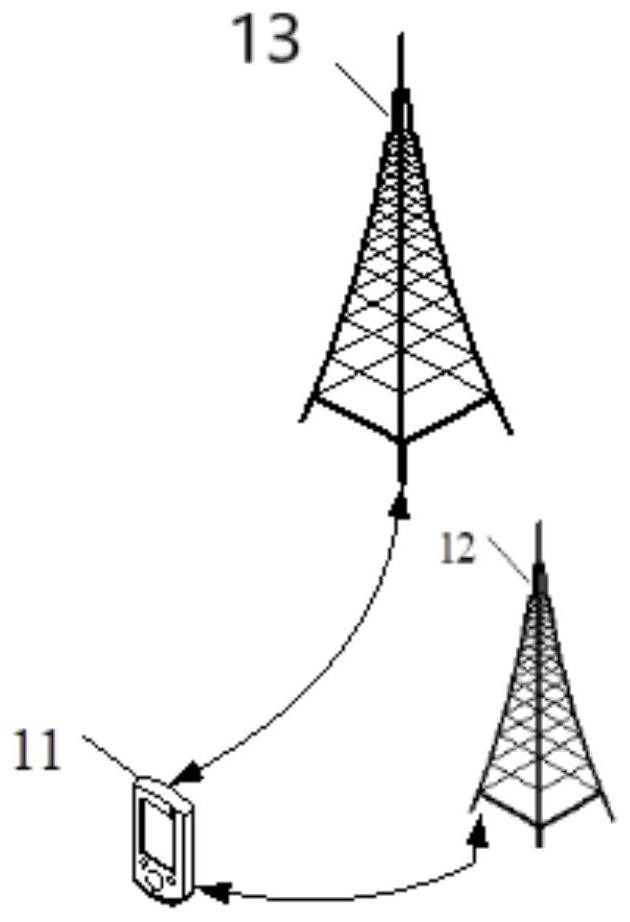
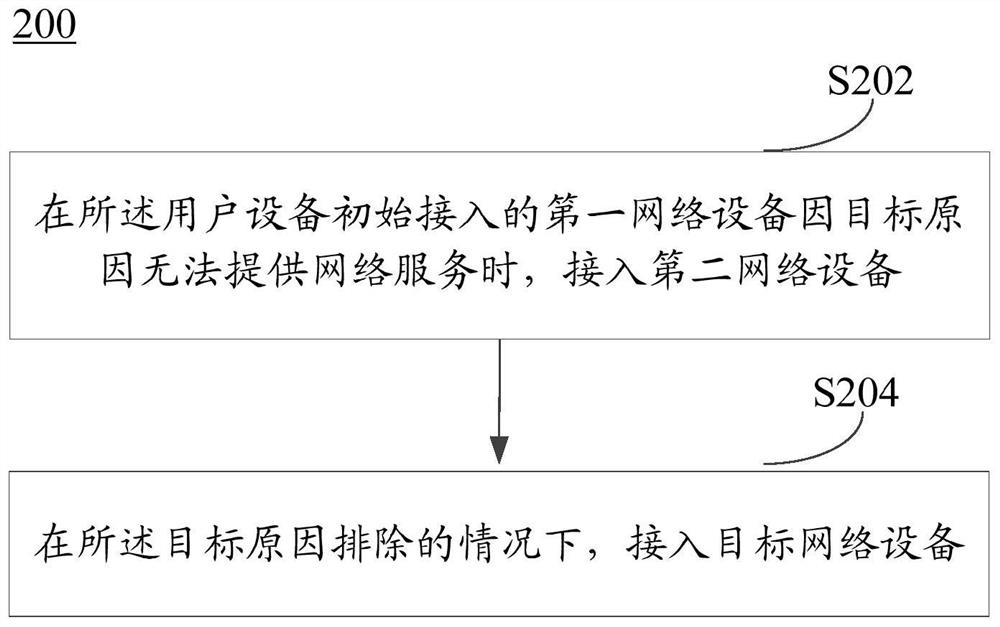
[0141] In step S402, a disaster occurs in the first network device initially accessed by the user equipment.
[0142] In step S403, the UE obtains the disaster area range from the first network, such as a tracking area (Tracking Area, TA) area, a TA list (list), or latitude and longitude. For example, the registration acceptance / rejection of the first network, the acceptance / rejection of a scheduling request (Scheduling Request, SR), the configuration update message, and the deregistration message may be obtained.
[0143] In an implementation manner, when the UE obtains the scope of the disaster area from the first network, it may not be in the disaster area. For example, in an area of the first network where no disaster has occurred, the UE receives a notification from the first network that a disaster has occurred in a certain area. , the UE can access the second network when entering the disaster area.
[0144] In another implementation manner, when the UE obtains the s...
example 2
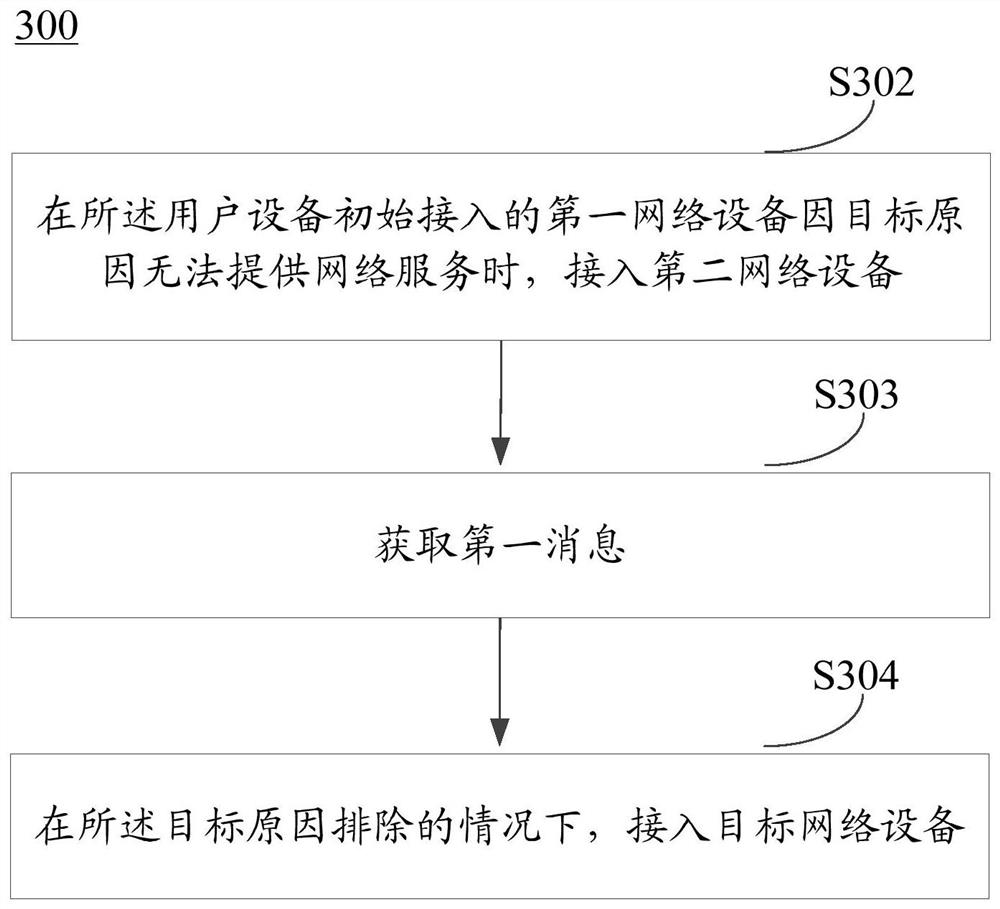
[0149] In step S402, a disaster occurs in the first network device initially accessed by the user equipment. The UE leaves the disaster network, that is, the first network, and accesses the second network.
[0150] In step S403, the UE obtains the disaster area range, such as TA area, TA list, or latitude and longitude, from the second network. For example, it can be obtained through registration acceptance / rejection of the second network, SR acceptance / rejection, configuration update message, and deregistration message.
[0151] In an implementation manner, when the UE obtains the scope of the disaster area from the second network, it may not be in the disaster area. A disaster occurs in one area, and the UE may not access the first network when entering the disaster area.
[0152] In another implementation manner, when the UE obtains the scope of the disaster area from the first network, it may be in the disaster area, for example, when a disaster occurs in the first netwo...
example 3
[0155] In step S402, a disaster occurs in the first network device initially accessed by the user equipment.
[0156] In step S403, the UE obtains the disaster area range from the third network. The third device learns the information that the disaster occurs to the first network device, and the third device is not the first network device in which the disaster occurred, nor the second network device registered by the UE. The third device can be, for example, a Bluetooth device, satellite or broadcast television, etc., and can notify the UE of the disaster area of the first network device, such as the latitude and longitude, the first TA LIST, CELL LIST of network equipment.
[0157] Alternatively, the third device may inform the UE that the UE has entered the disaster area. For example, when the UE moves to an area and finds that the cell of the first network device can be found, and / or the cell is not in the disaster celllist, it determines in step S404 that it has left ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com