Method for processing a security setup control message in mobile communication system
A technology of mobile communication system and safety message, applied in the field of message processing of mobile communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Reference will now be made in detail to the preferred embodiments of the invention, examples of which are illustrated in the accompanying drawings. Wherever possible, the same reference numbers will be used throughout the drawings to refer to the same or like parts.
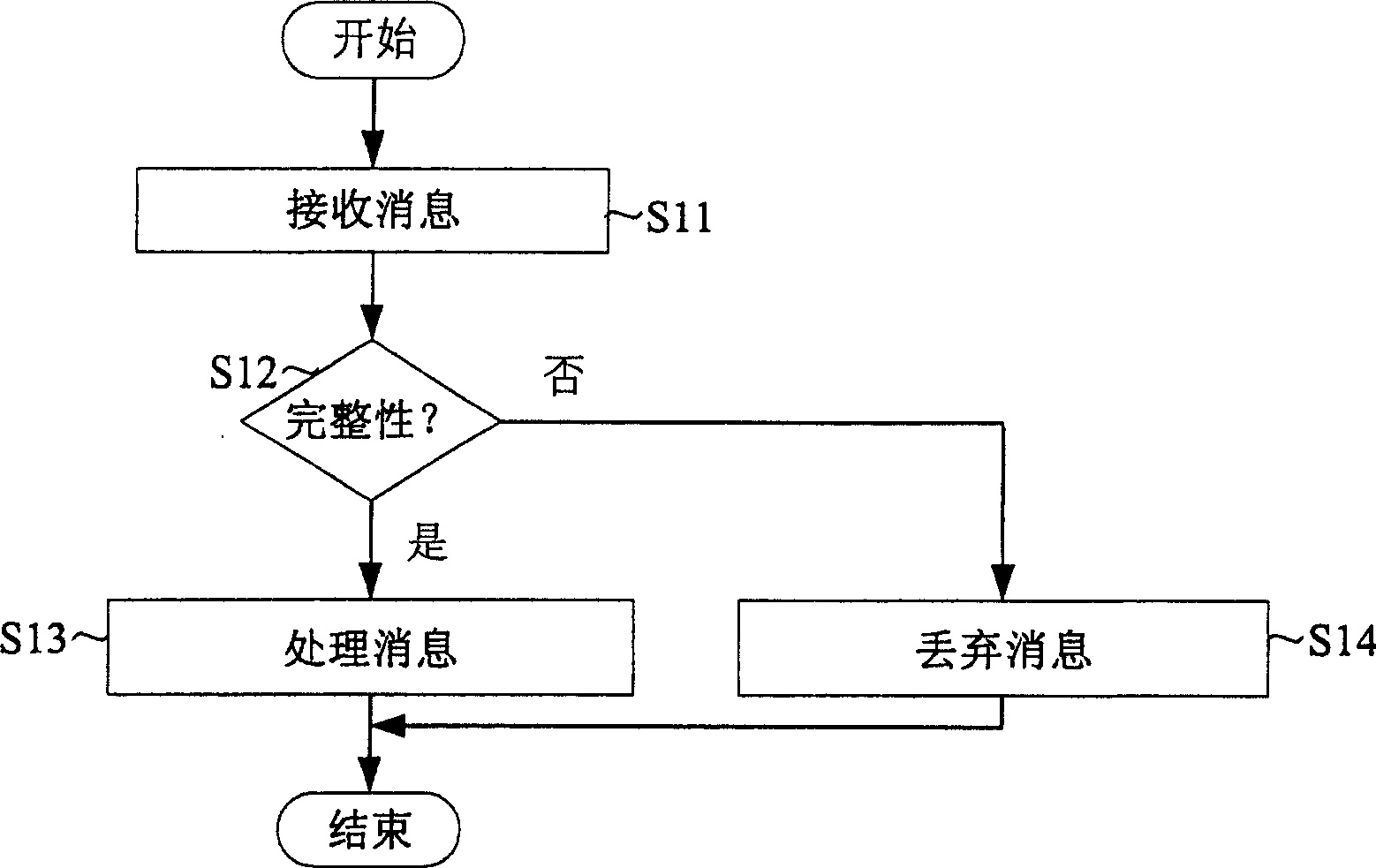
[0028] figure 1 is a flowchart illustrating a general message processing method.
[0029] refer to figure 1 , UE (User Equipment) first receives a general message (S11) and performs an integrity check on it (S12). Depending on the result of the integrity check, the message is processed normally or discarded. That is, if the message passes the integrity check, it is processed normally (S13). If the message does not pass the integrity check, it will be discarded due to security issues (S14).
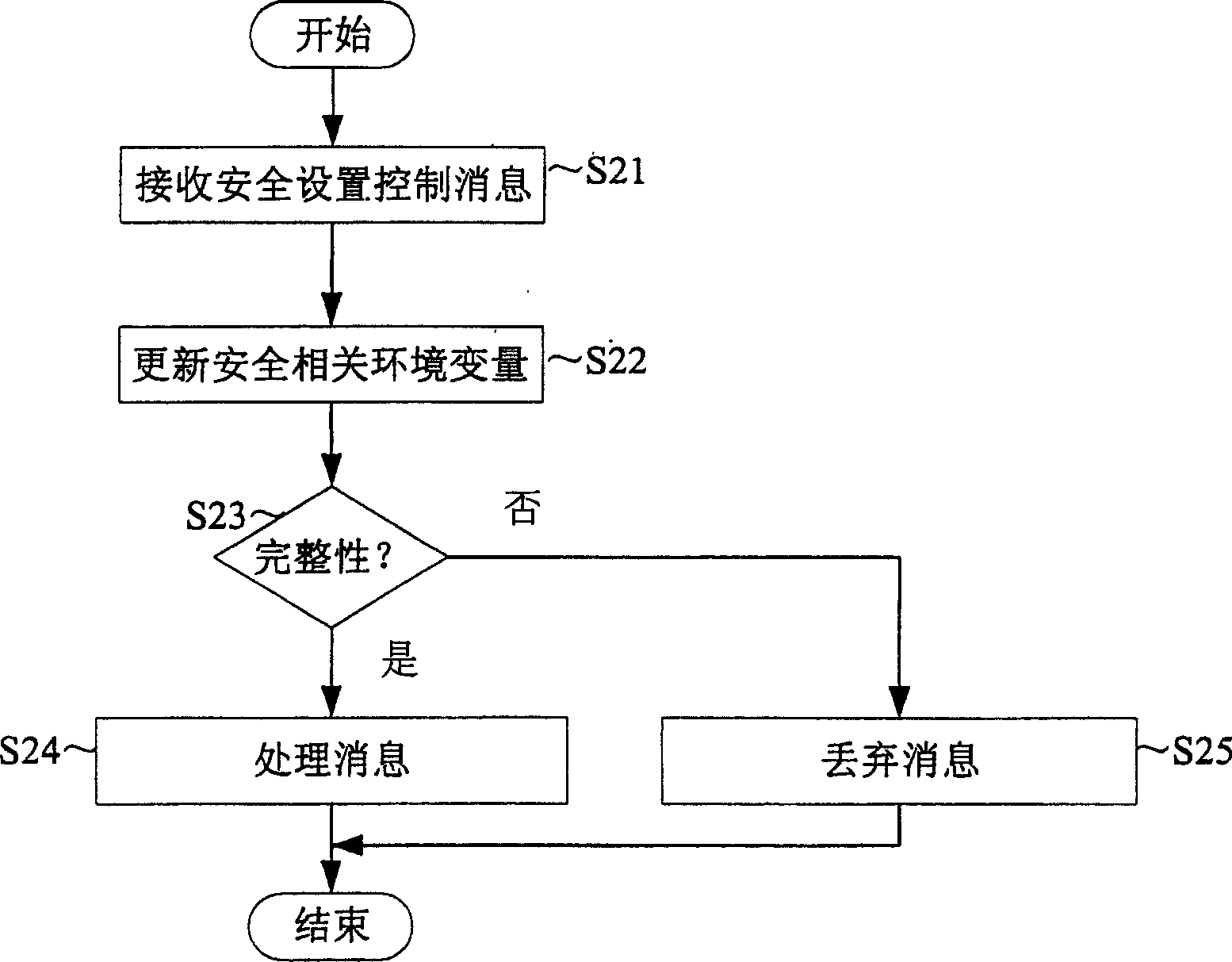
[0030] figure 2 is a flowchart illustrating a method of processing a security setting control message according to the first embodiment of the present invention.
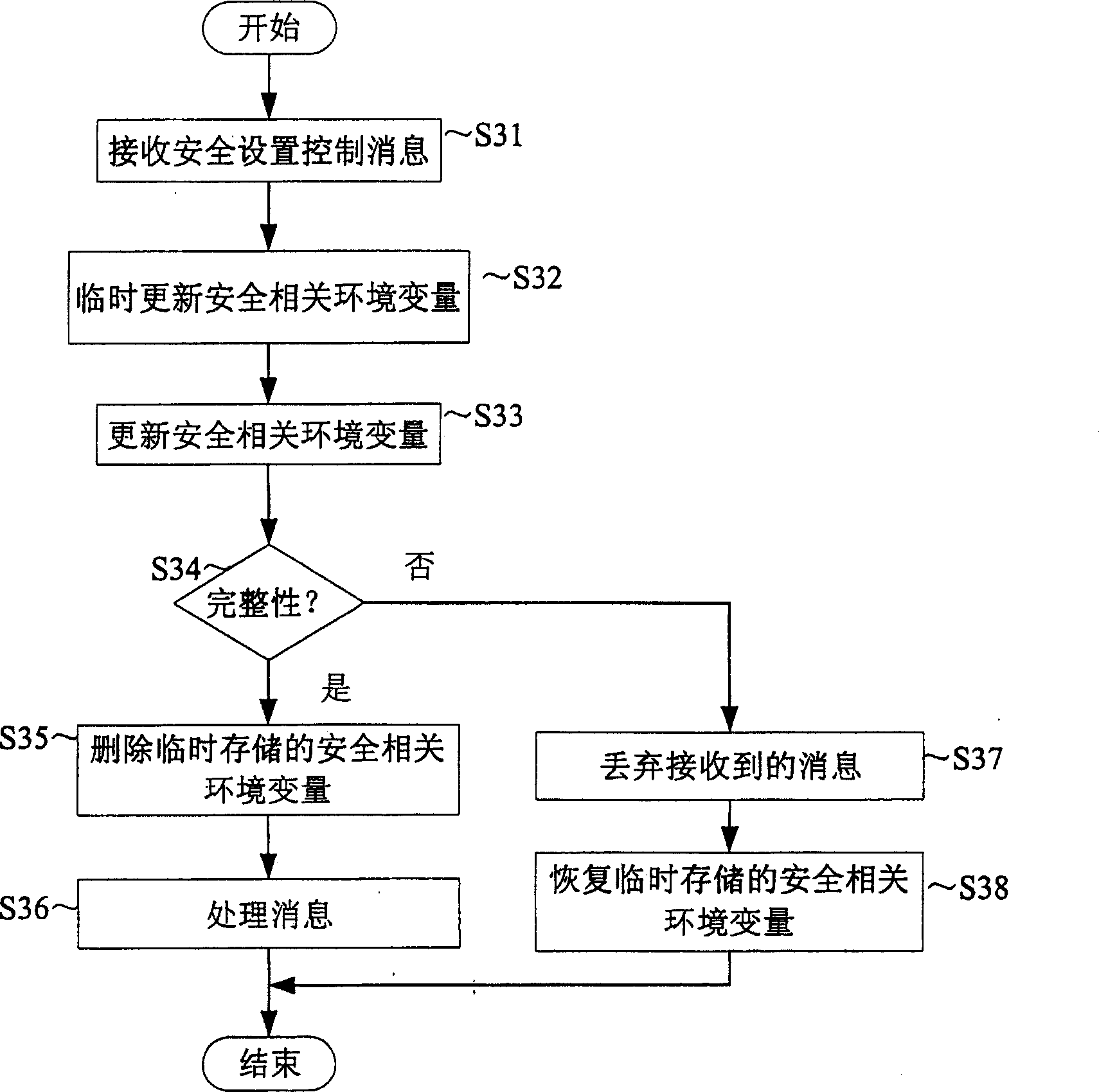
[0031] refer to figure 2 , UE (User Equipmen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com