Implementation method for reducing amount of calculation for managing cipher key of MANET network
A network key and calculation technology, which is applied in the field of network security protection, can solve the problems of the overall performance of the system, the system cannot run normally, and the weak processing ability of the MANET network terminal, so as to reduce the calculation amount and improve the usability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
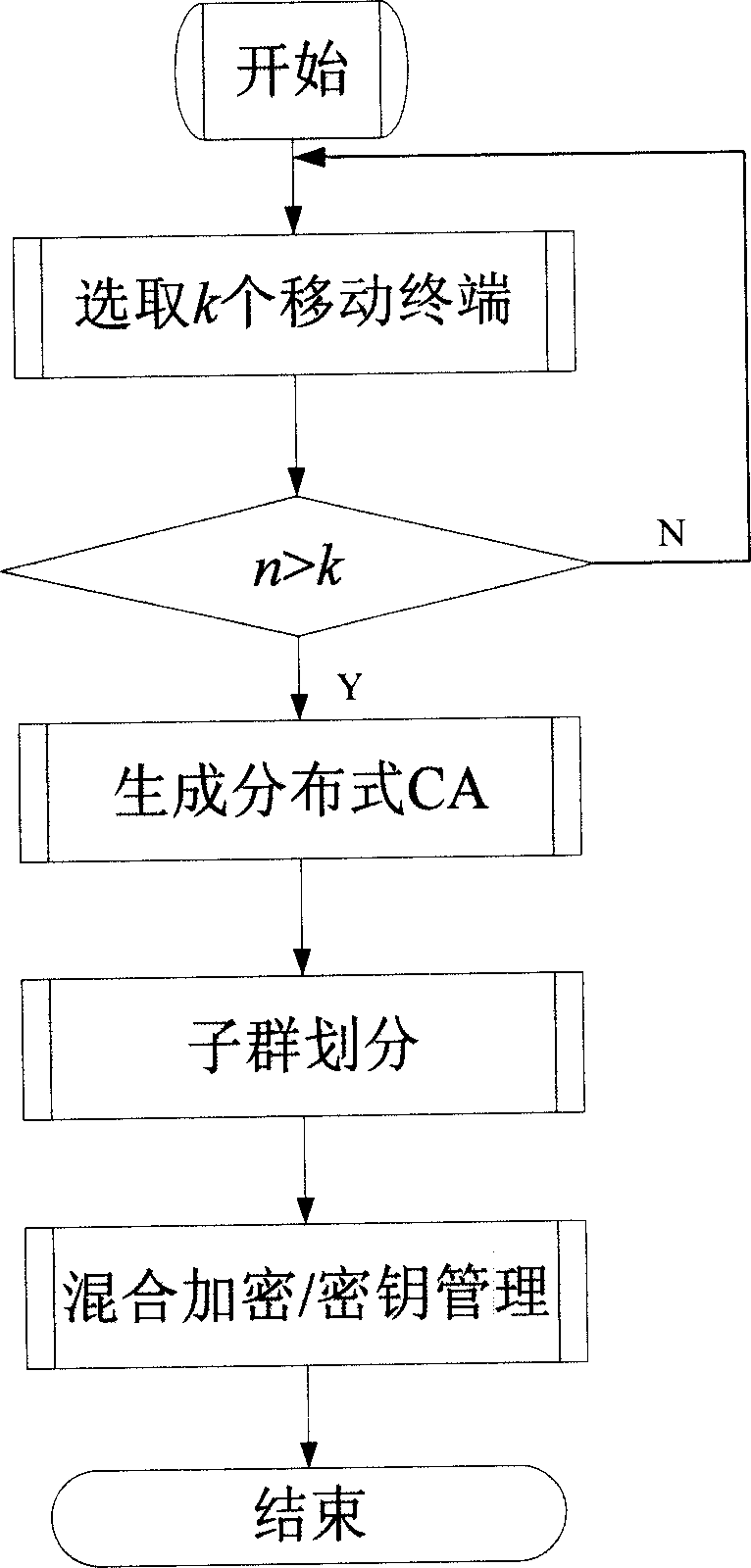
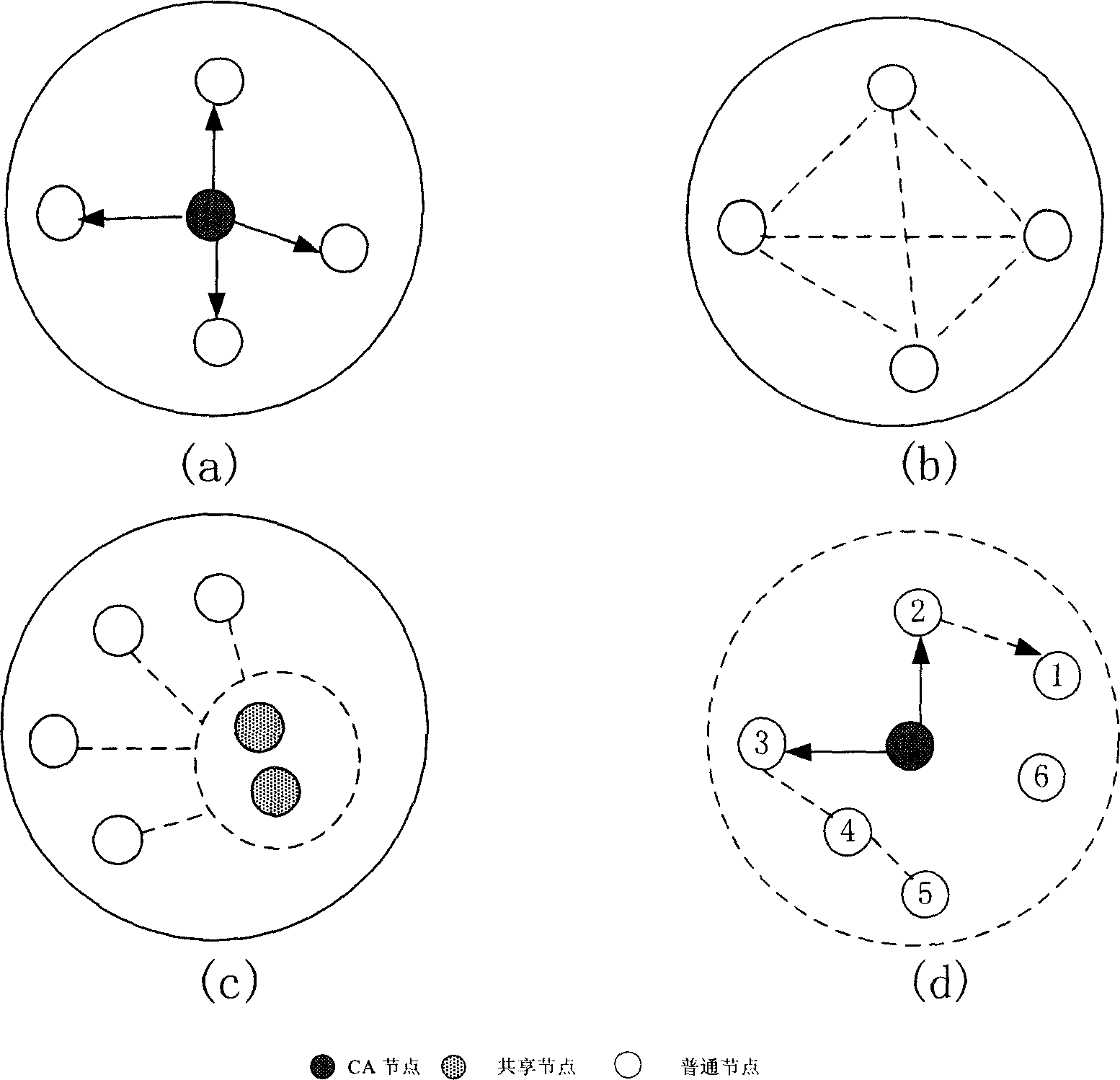
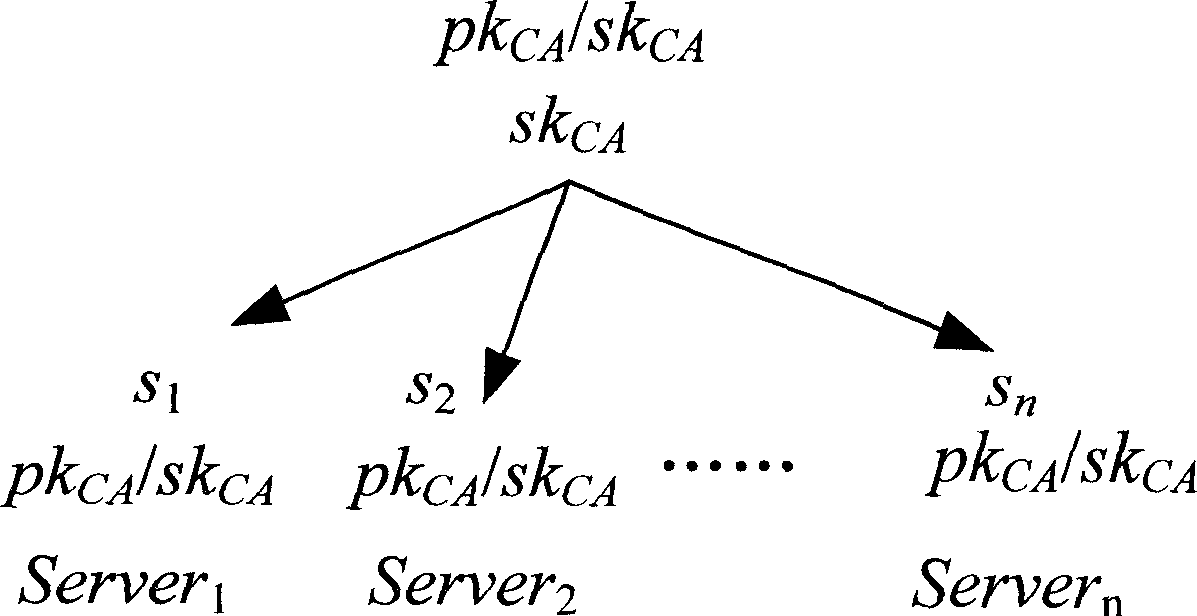
[0099] (i) Initialization
[0100] P i Run the probabilistic polynomial time algorithm G(i, 1 l ), the input value is the security parameter l, and the output value is the key SK i ={p i ,q i} and PK i =n i , P i broadcast n i . After initialization, each terminal is able to i know other terminals n i information, recorded as:
[0101] N j = Π j = 1 n j ≠ i n j .
[0102] (ii) Key agreement
[0103] P i pick bit k i and a random integer x i ∈ Z n i * .
[0104] if k i = 0,p i calculate X i = ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap