Computer authorizing monitoring system with image identification function and its method
An image recognition and computer technology, applied in computing, instruments, electrical and digital data processing, etc., can solve the problems of high security risks, control of the operation authority of objects that cannot be protected, and the operation control right falling into the hands of others, so as to improve the safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
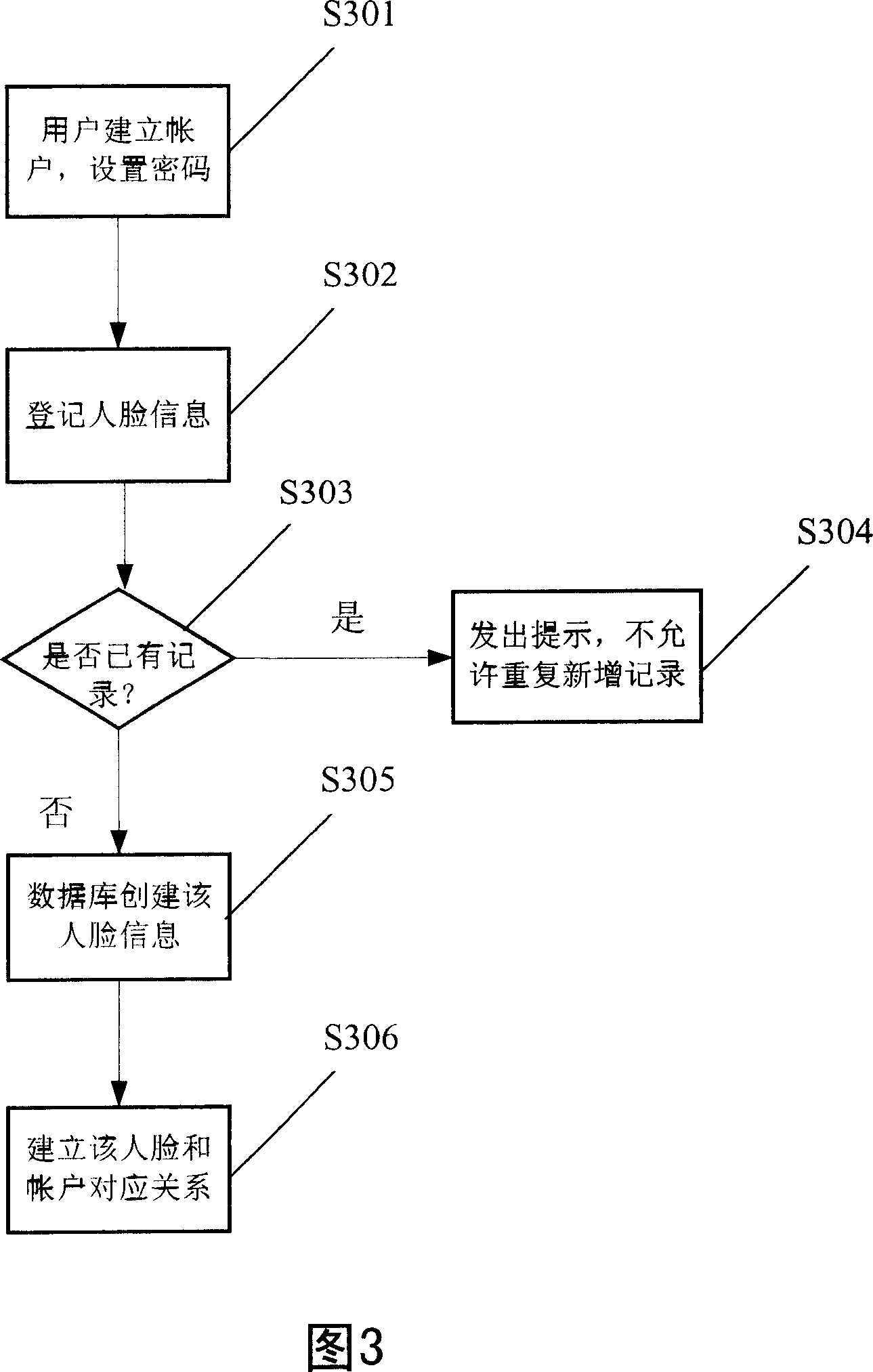
[0012] The invention provides an application scheme for real-time control of computer system operation authority by using face recognition. The present invention will be described in further detail below in conjunction with the accompanying drawings.
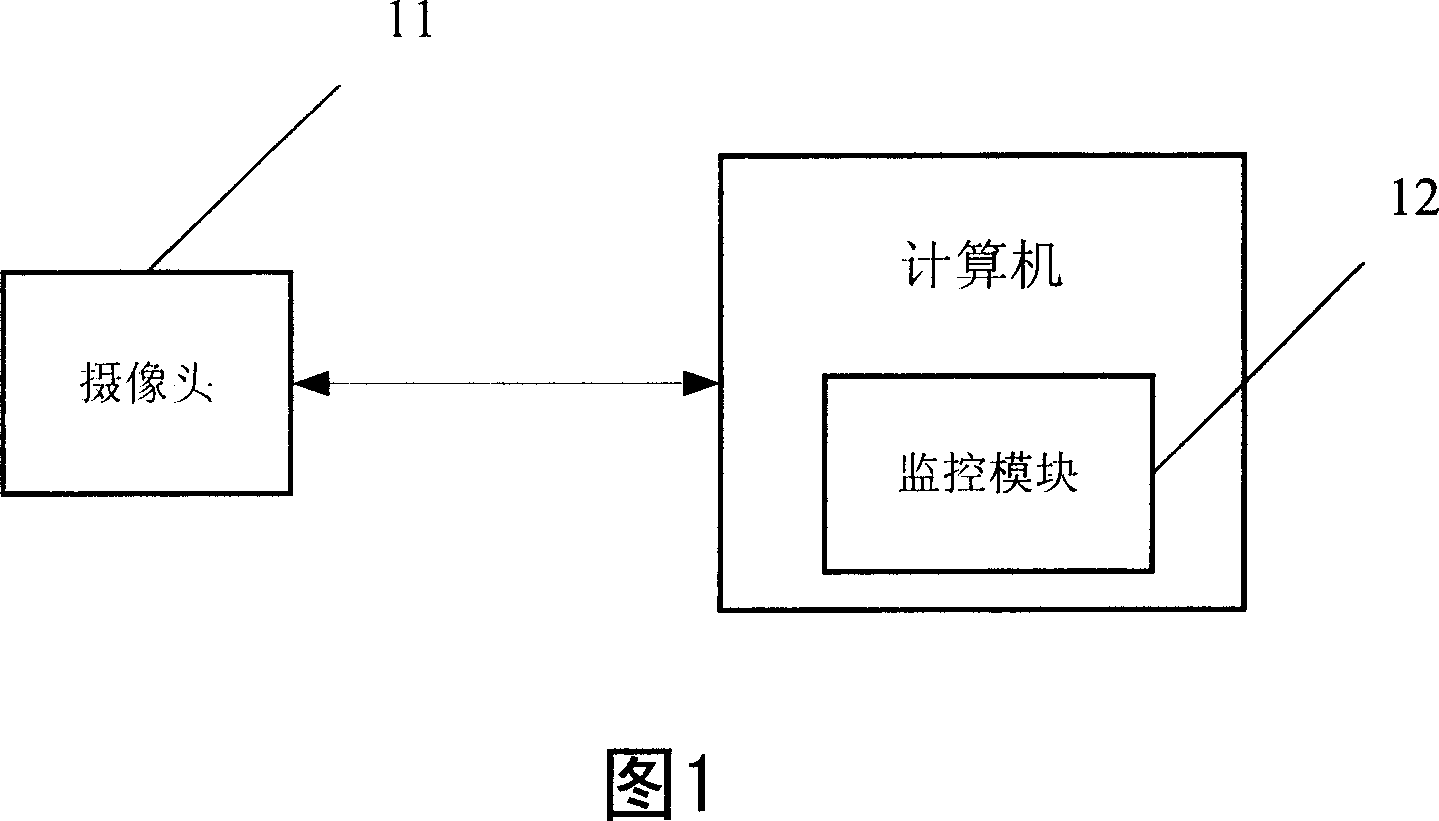
[0013] As shown in FIG. 1 , the monitoring system according to the present invention includes a camera 11 and a monitoring module 12 located in a computer. Camera 11 is used for taking the face image of the user who uses the computer. The monitoring module 12 judges whether the user has the authority to operate the computer according to the face image captured by the camera 11 . The camera 11 can also be built into a computer.
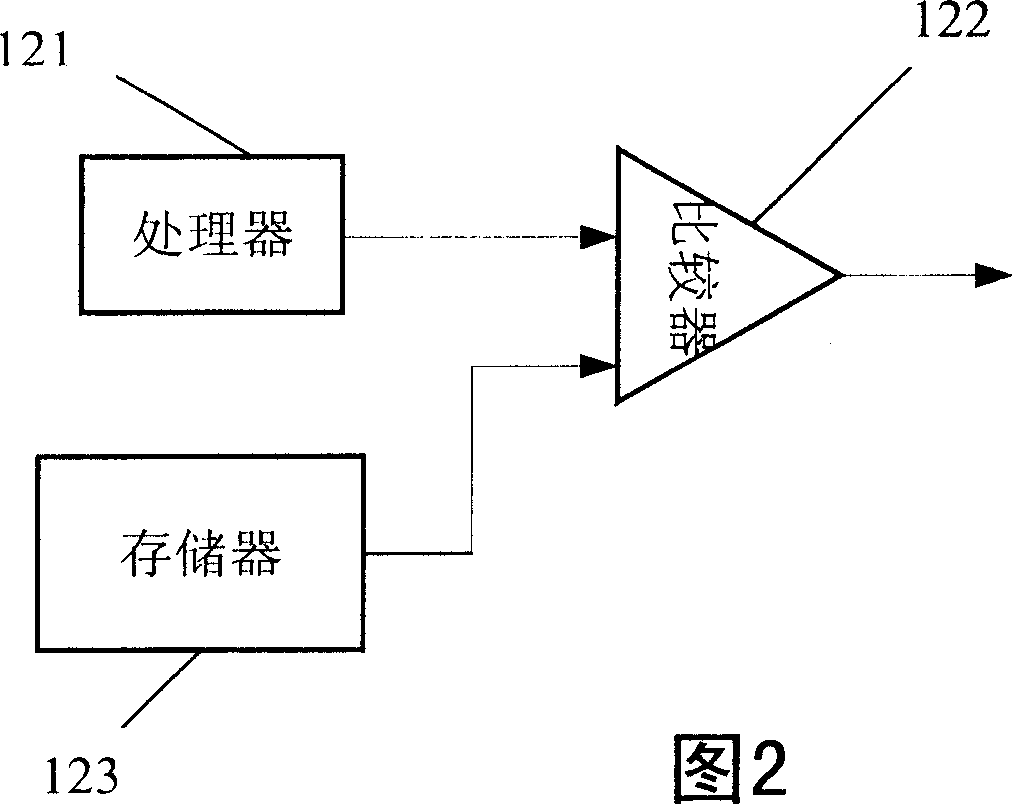
[0014] As shown in FIG. 2 , the monitoring module 12 includes three parts: a processor 121 , a comparator 122 and a memory 123 . The face image templates of one or more users are stored in the memory 123, and the users are users who have the authority to use the computer. The rights to use a computer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com