Identity identifying method
An identity authentication and identity technology, applied in the field of authentication, identity authentication methods and systems, can solve the problem of single authentication information, achieve the effect of increasing active participation, diversifying methods, increasing user experience and interactivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
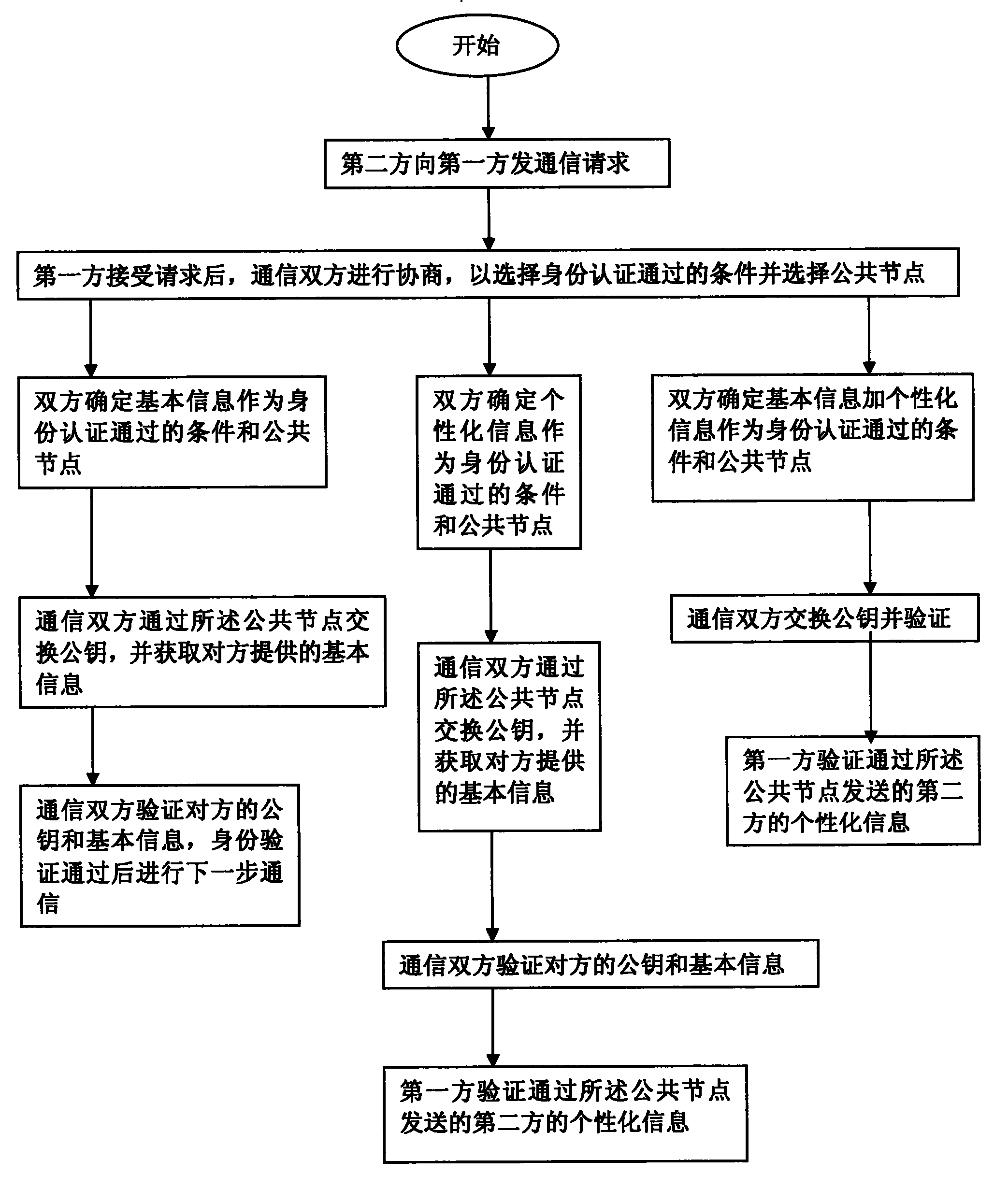
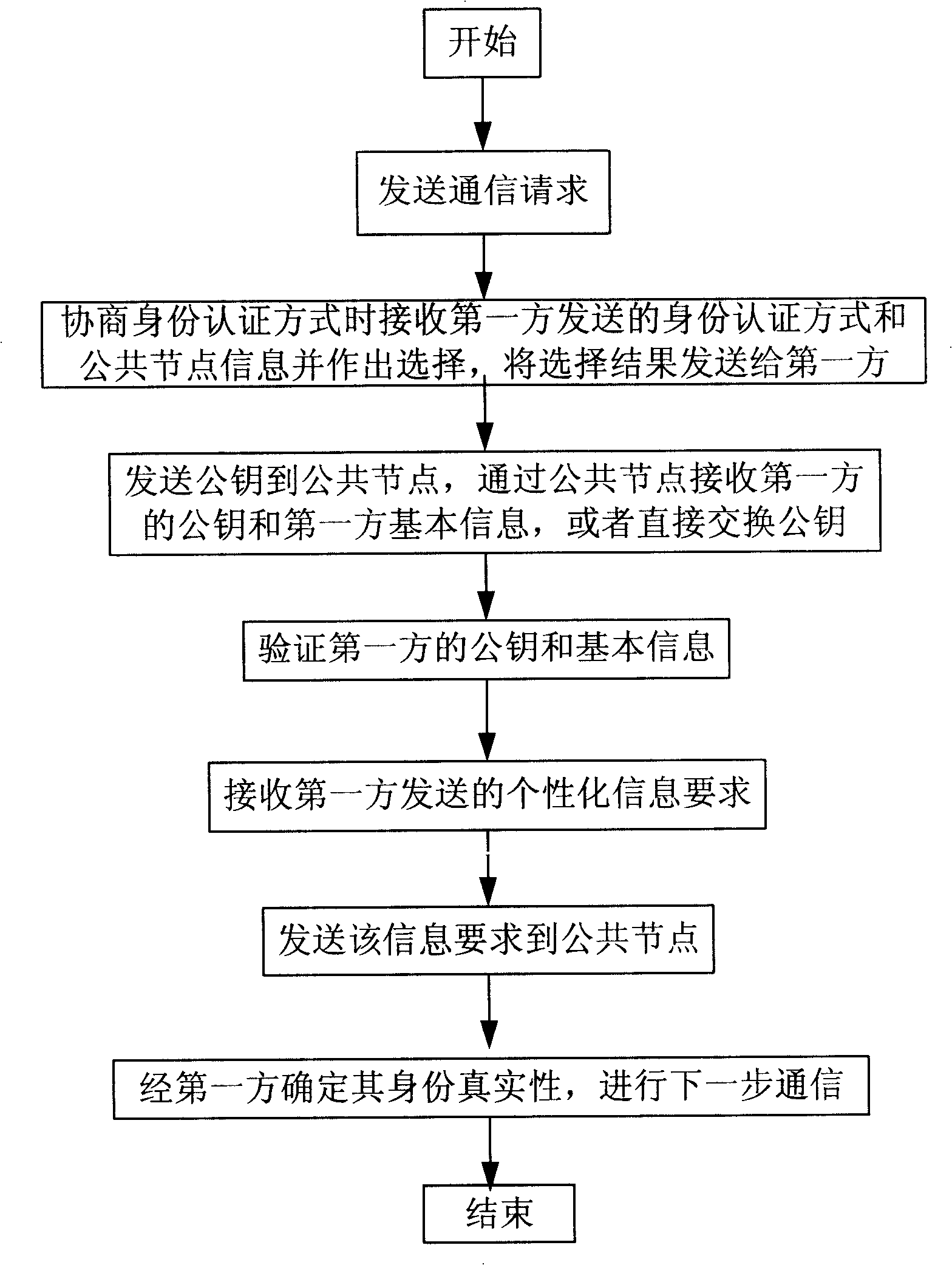
[0081] In network communication, after the second-party node sends a communication request, the first-party node needs to verify the authenticity of the identity of the second-party node before accepting the communication request for communication. The existing technology generally adopts a method based on public key The identity authentication method based on the public key mainly relies on a special third-party certification authorization center to issue an identity certificate for the customer to confirm the identity information of the other party. In the existing technology, both parties need to go to the certification center to obtain the digital certificate of the other party. Use the root certificate of the certification center to verify the digital signature of the digital certificate to determine whether the digital certificate is trustworthy, and then use the public key in the digital certificate to encrypt and communicate with the other party, so that the identity of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com