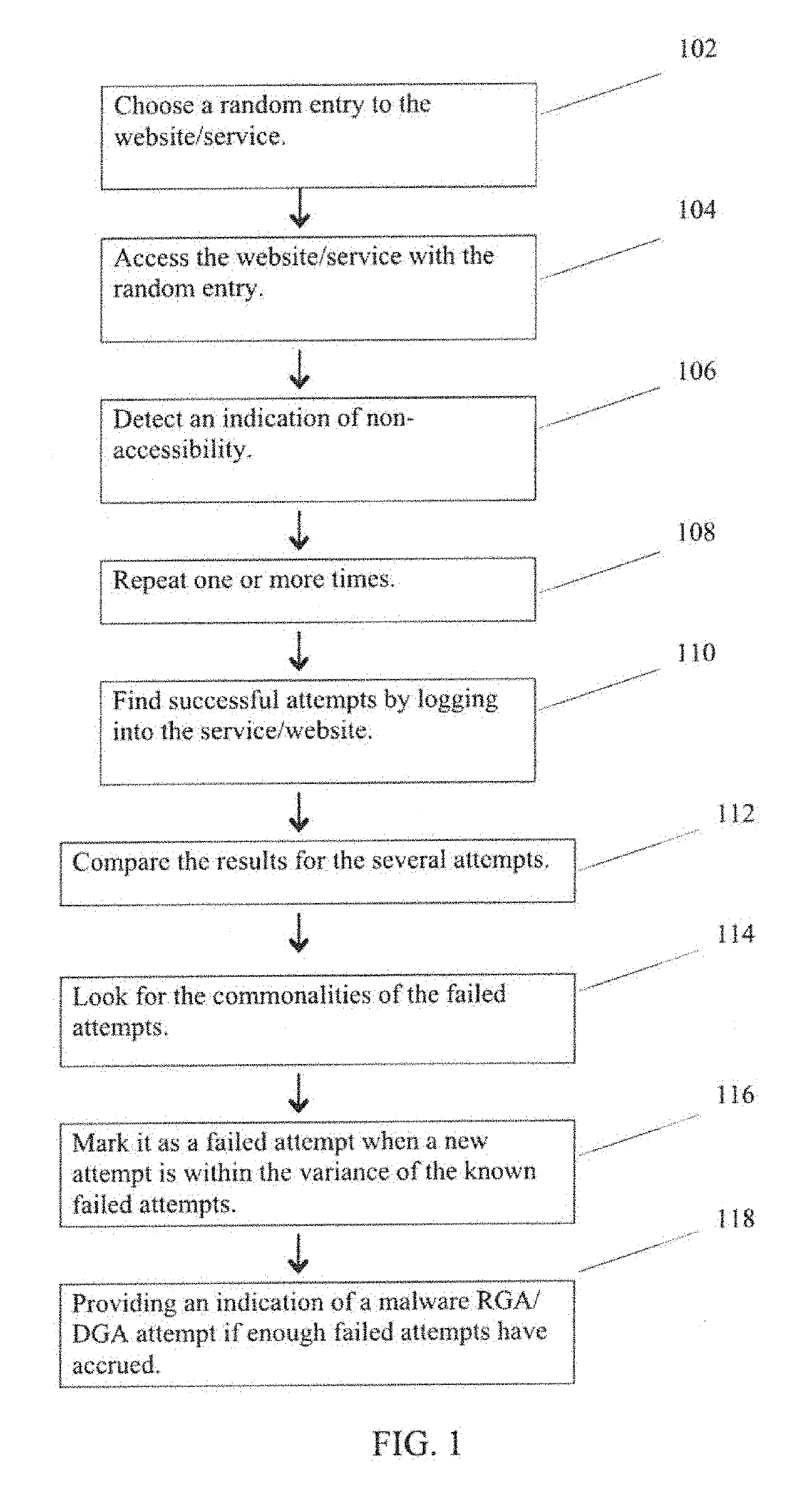
Prevention of rendezvous generation algorithm (RGA) and domain generation algorithm (DGA) malware over existing internet services
a technology of domain generation algorithm and malware, applied in the field of computer security, can solve the problems of malware operator redundancy, malware will likely need several attempts to find a current, and network-based solutions will often fail for encrypted communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
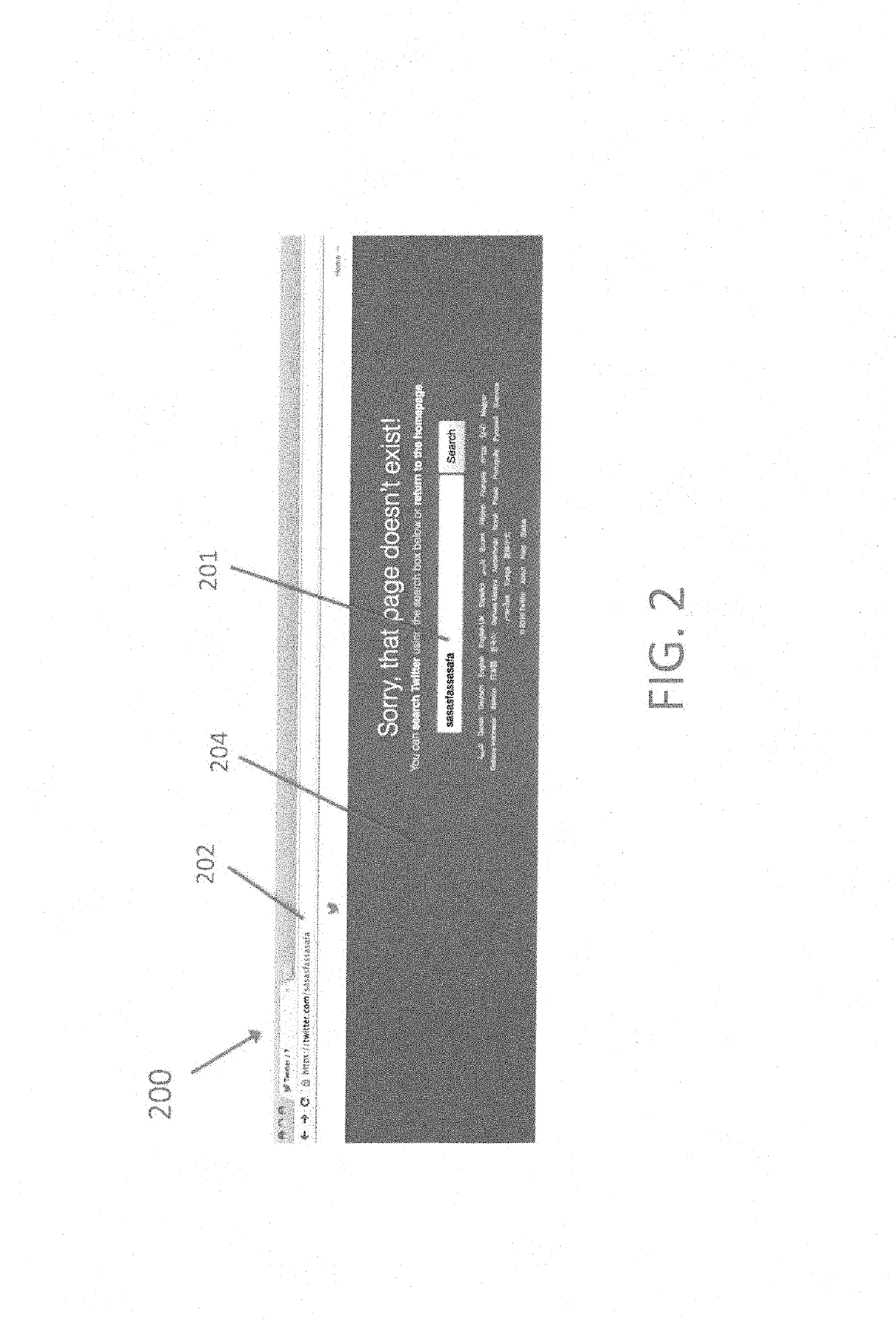
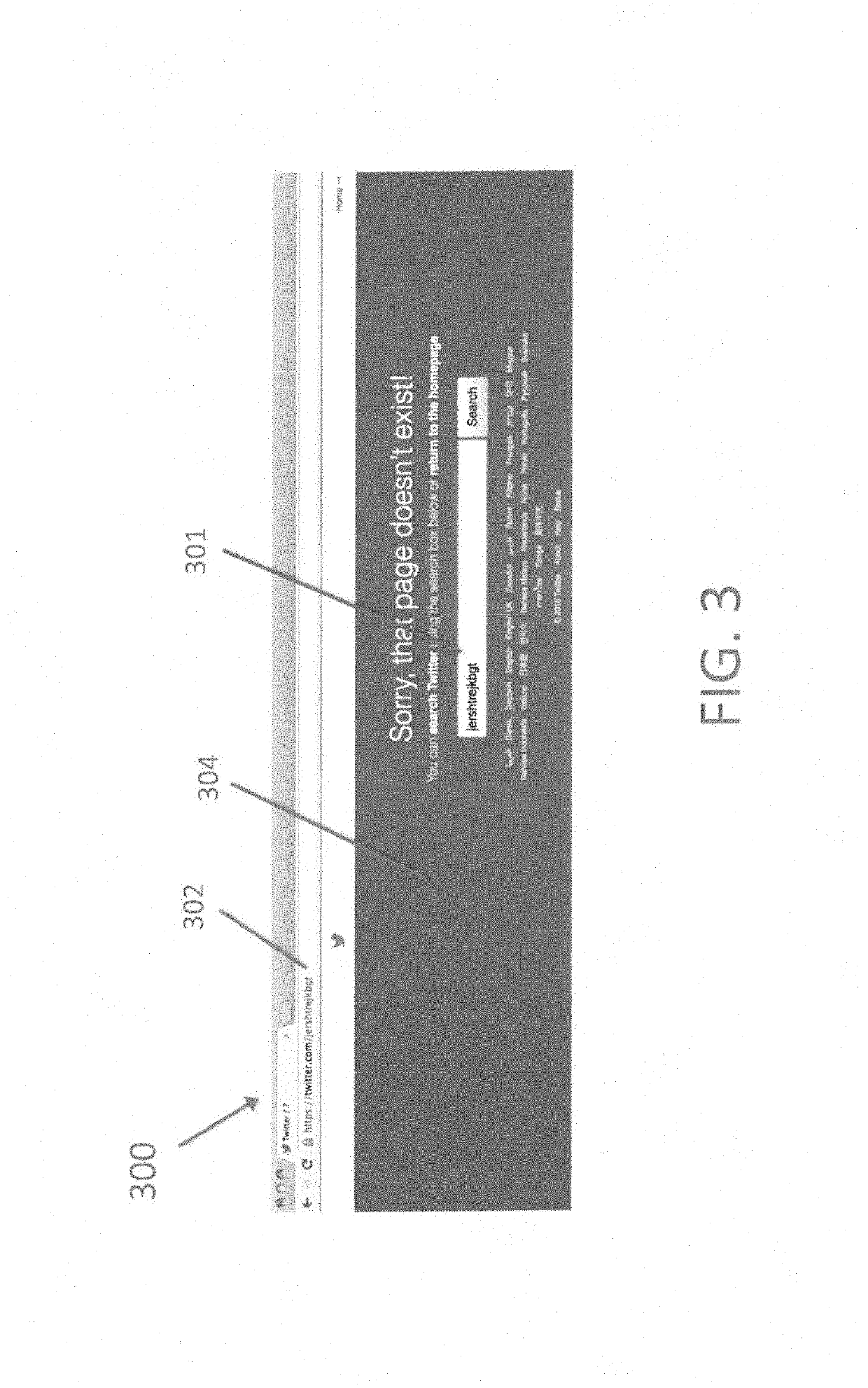
[0046]FIG. 2 illustrates the Twitter web service application for a random nonexistent username. Choosing a random Twitter name login sasasfassasafa 201 goes to the url https: / / twitter.com / sasasfassasafa 202. Twitter provides a webpage 204. FIG. 3 illustrates the Twitter web service application for another random nonexistent username. Choosing another random Twitter name login jershtrejkbgt 301 goes to the url https: / / twitter.com / jershtrejkbgt 302 and finds a similar webpage 304. Note that the two pages look very similar and have similar wording (the earth movers distance is just the difference of the two random Twitter name login strings). However, if one goes to a valid Twitter page (https: / / twitter.com / cybereason) (FIG. 4) there is something very different.
[0047]Note that the difference between Cybereason's Twitter page 400 and the random pages (FIGS. 2 and 3) (using e.g., the Earth movers distance) is very large. Thus, one can detect the instance in which a valid result is return...
example 2
[0049]FIG. 5 illustrates the Gmail web service application 500 after choosing a random nonexistent email 501 to log into Gmail email. FIG. 6 illustrates the Gmail web service application 600 after choosing a valid email 601 to log into Gmail email.
[0050]As can be seen in FIG. 6 a valid account 600 has different properties than an invalid account 500 (text saying “Sign in with a different account”604 rather than text saying “Create account”504, the appearance of the email which was attempted to be used 601 under the valid username 606, a sign in box 602 as opposed to a next box 502, a lack of the red text 506 saying that the email is incorrect, the appearance of a graphic with the first letter of the user's name 608 rather than a default person-outline 508, text saying “Need help?”610 rather than “Find my account”510, the appearance of a password box 612 rather than a red alert surrounding the invalid email 512, etc.).
[0051]The difference between invalid attempts (note that the only ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com