Decryption-key distribution method and authentication apparatus
a decryption key and distribution method technology, applied in the field of decryption key distribution methods and authentication apparatuses, can solve the problems of the inability to obtain the decryption key, and the length of time required therefor, so as to increase the number of sessions, the effect of safe distribution of the decryption key and not increasing the amount of communication dedicated
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
Hardware Configuration and Data Format
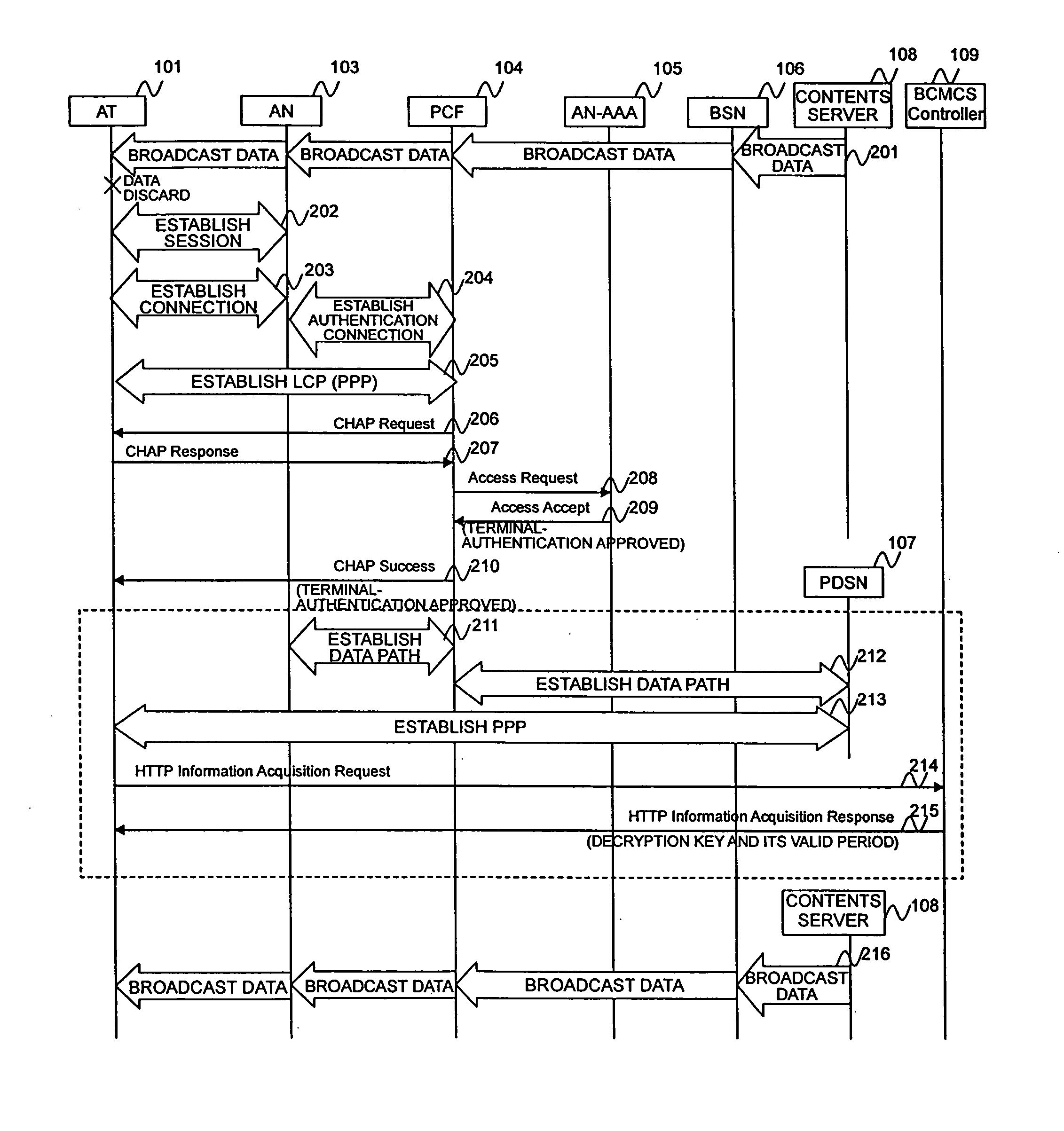
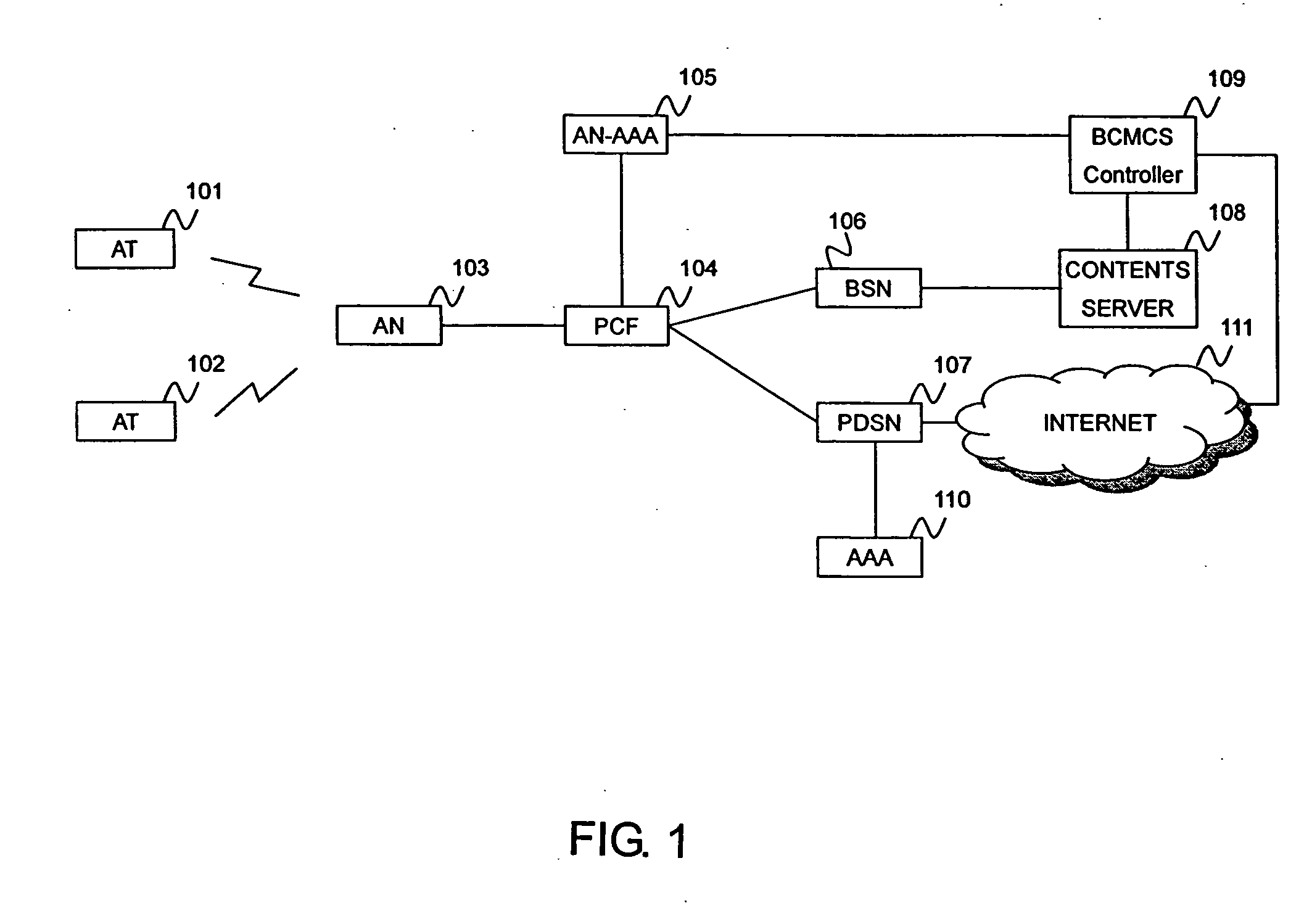
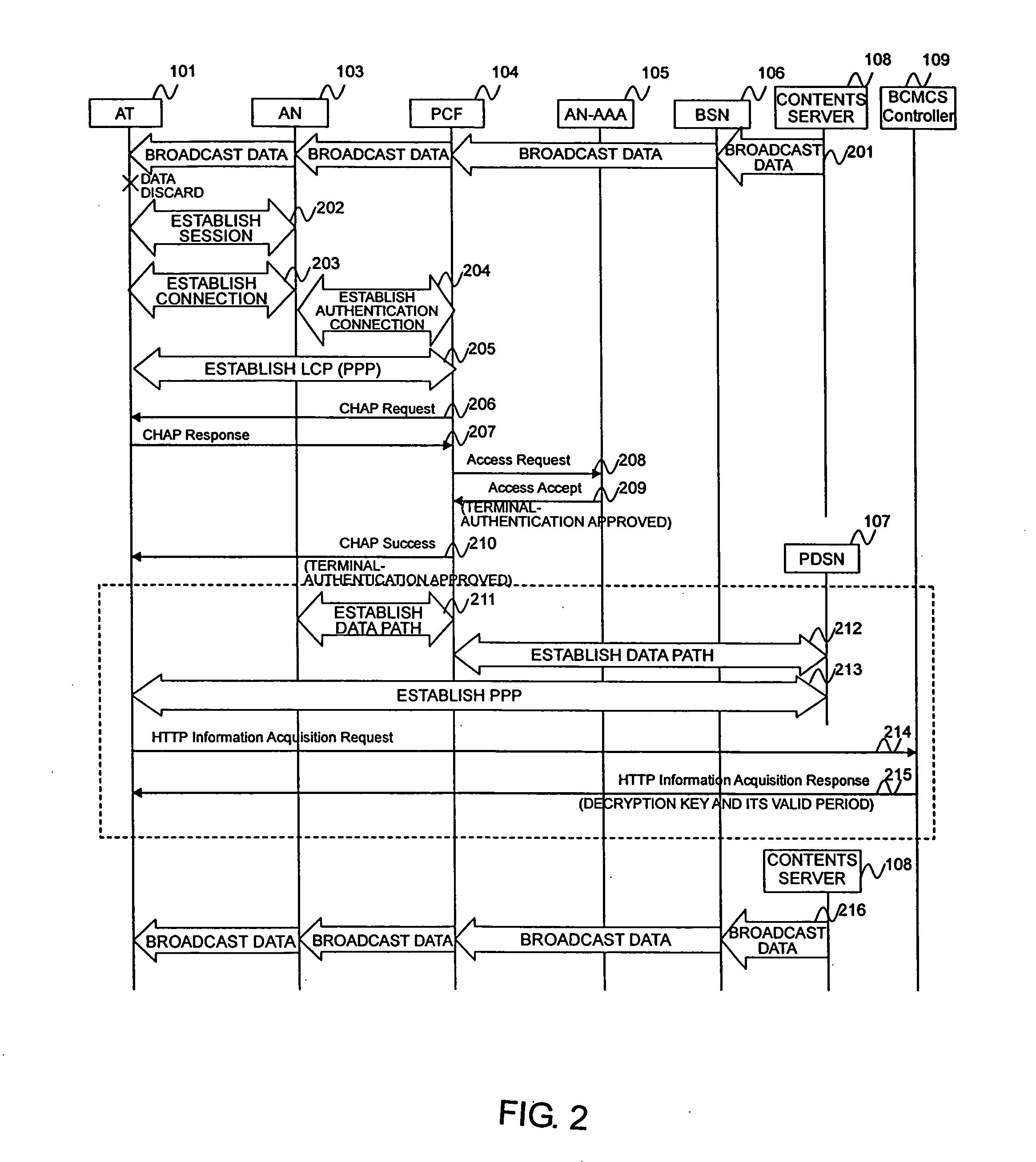
[0058]FIG. 1 is a view showing the structure of a 1×EV-DO network system according to an embodiment of the present invention.
[0059] The 1×EV-DO network system shown in FIG. 1 is used as an example in the following description. The present invention can also be applied to systems having a mobile-terminal authentication function and a broadcast channel through which encrypted data can be transmitted.
[0060] The network system includes, for example, a base station (access node: AN) 103, a packet control unit (packet control function: PCF) 104, an authentication unit (access network for authentication, authorization and accounting: AN-AAA) 105, a BCMCS service unit (broadcast serving node: BSN) 106, a packet-data service unit (packet-data serving node: PDSN) 107, a contents server 108, a BCMCS controller 109, and an authentication, authorization, and accounting unit (AAA) 110. To distribute a decryption key used for decrypting broadcast data to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com