Method for protecting digital content from unauthorized use by automatically and dynamically integrating a content-protection agent
a technology of content protection agent and content protection technology, applied in the protection of program/content, television system, instruments, etc., can solve the problems of difficult real-world “last mile” solution, difficult market penetration of such approaches, and inability to control source cod
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056]A description of example embodiments of the invention follows.
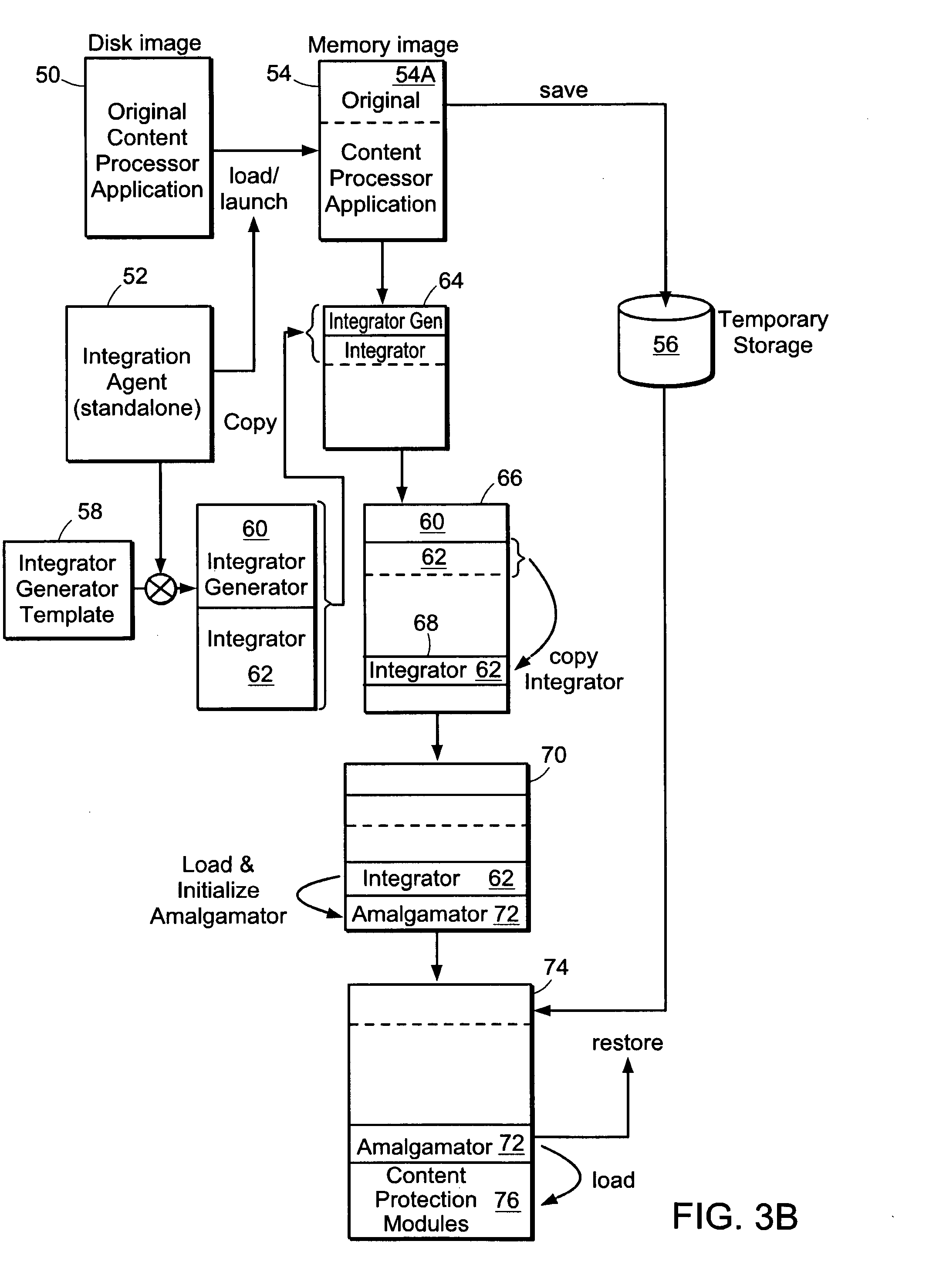
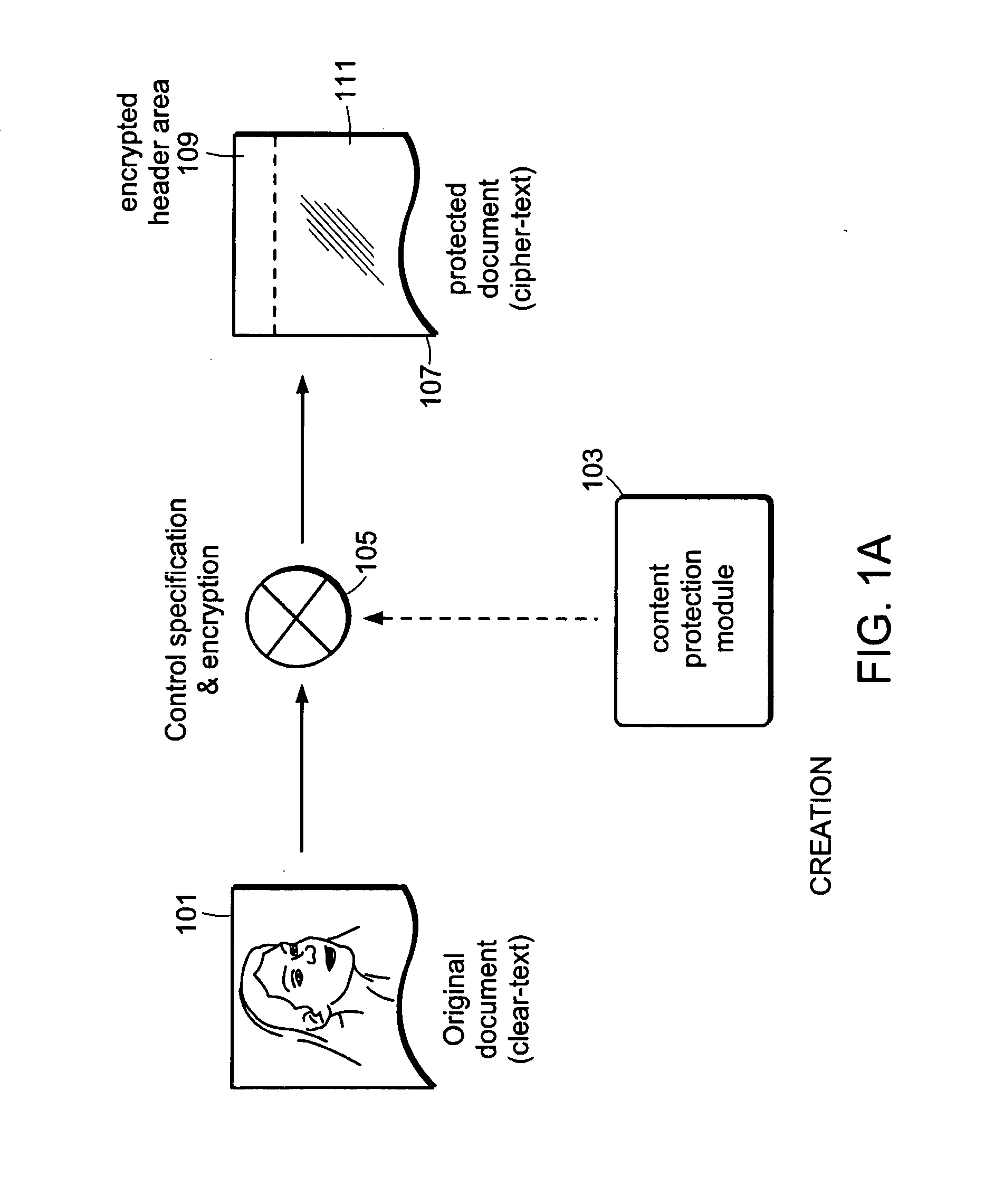
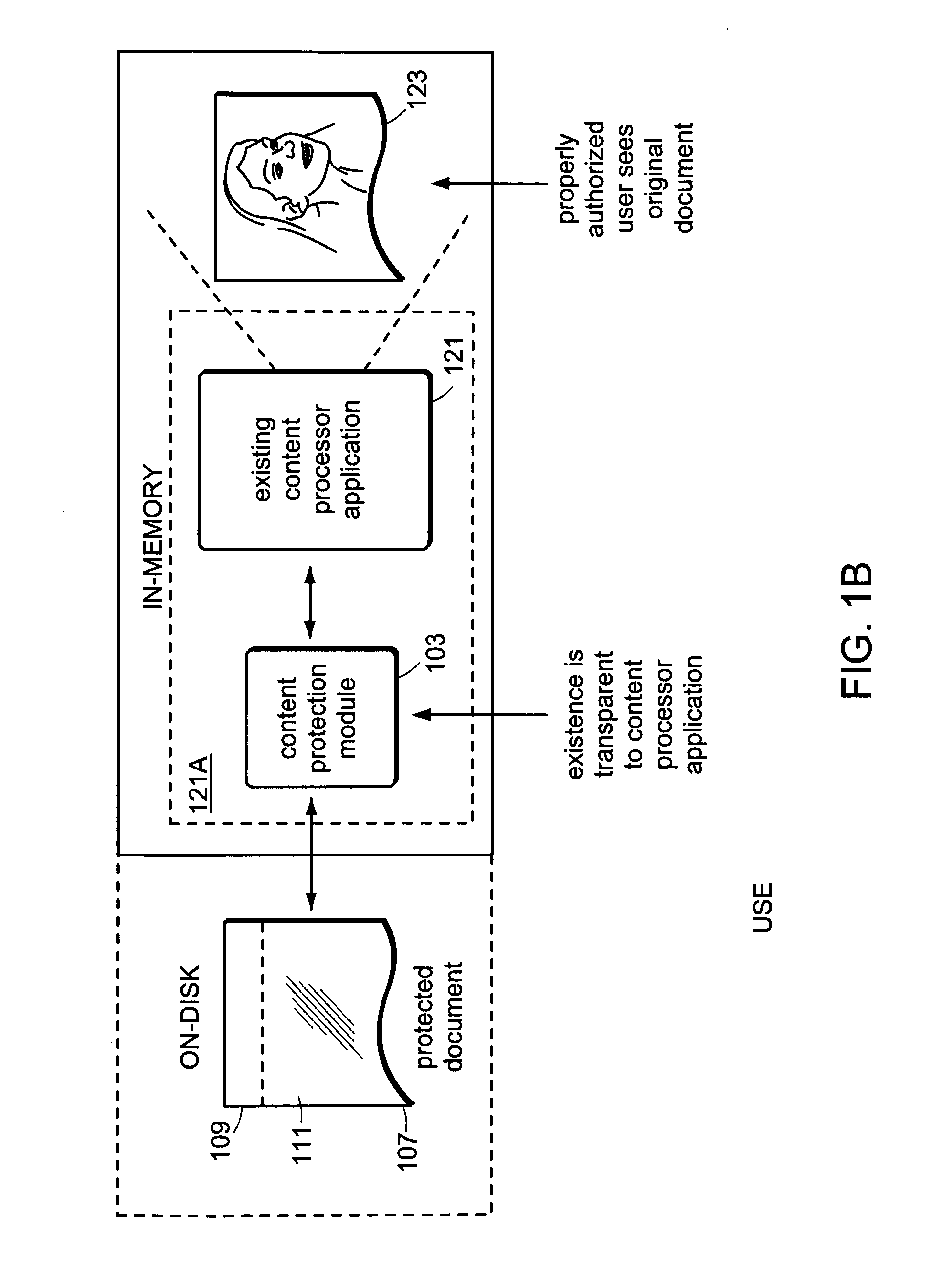
[0057]As used herein, a “content protection module” (or protection module, for short) is a software module which provides clear-text access to cipher-text content for only authorized users. Further, a “content processor application” (or content processor) is any software application that supports the viewing and / or editing of clear-text content files. Also, a “protected content” is an encrypted cipher-text file (possibly containing additional information required for authentication), which the content protection module knows how to decrypt and interpret.
[0058]The content protection module may also be implemented using a combination of software and hardware. In any case, the software component, possibly backed by hardware support, must include the “main” or “driver” portion because it is integrated into the software of the content processor application and gets control before the content processor application.
[0059]F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com