System and method for clustering host inventories
a host inventory and clustering technology, applied in the field of computer network administration and support, can solve the problems of incongruity between the executable software inventories, the differences between executable software inventories can arise in even the most tightly controlled network environment, and the impact of organization's incongruity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example embodiments
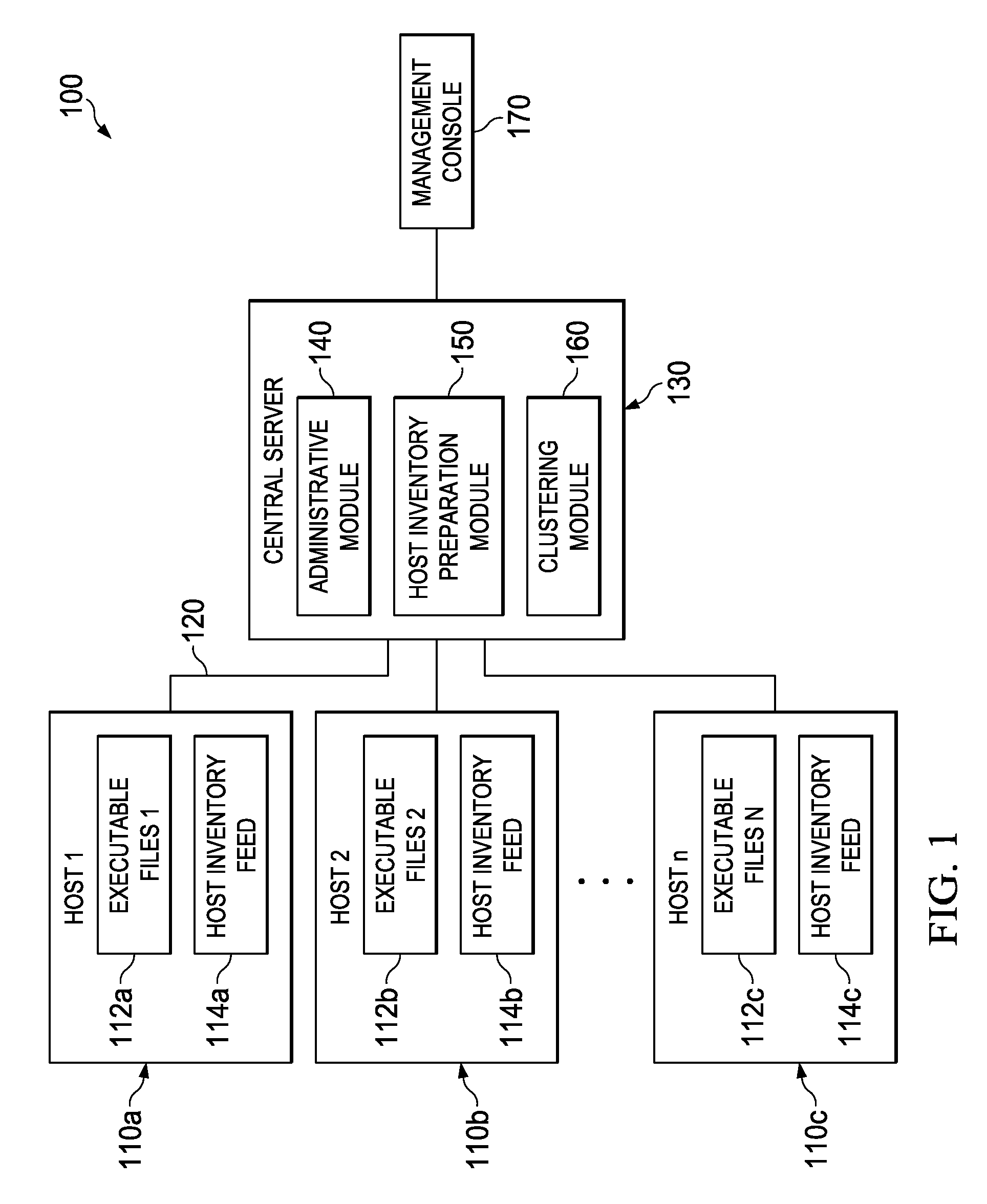
[0017]FIG. 1 is a pictorial representation of a computer network environment 100 in which embodiments of a system for clustering host inventories may be implemented in accordance with the present disclosure. Computer network environment 100 illustrates a network of computers including a plurality of hosts 110a, 110b, and 110c (referred to collectively herein as hosts 110), which may each have, respectively, a set of executable files 112a, 112b, and 112c (referred to collectively herein as sets of executable files 112) and a host inventory feed 114a, 114b, and 114c (referred to collectively herein as host inventory feeds 114). Hosts 110 may be operably connected to a central server 130 through communication link 120. Central server 130 may include an administrative module 140, a host inventory preparation module 150, and a clustering module 160. A management console 170 can also be suitably connected to central server 130 to provide an interface for users such as Information Technolo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com