Visual security mechanism for a device with a front-facing camera
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
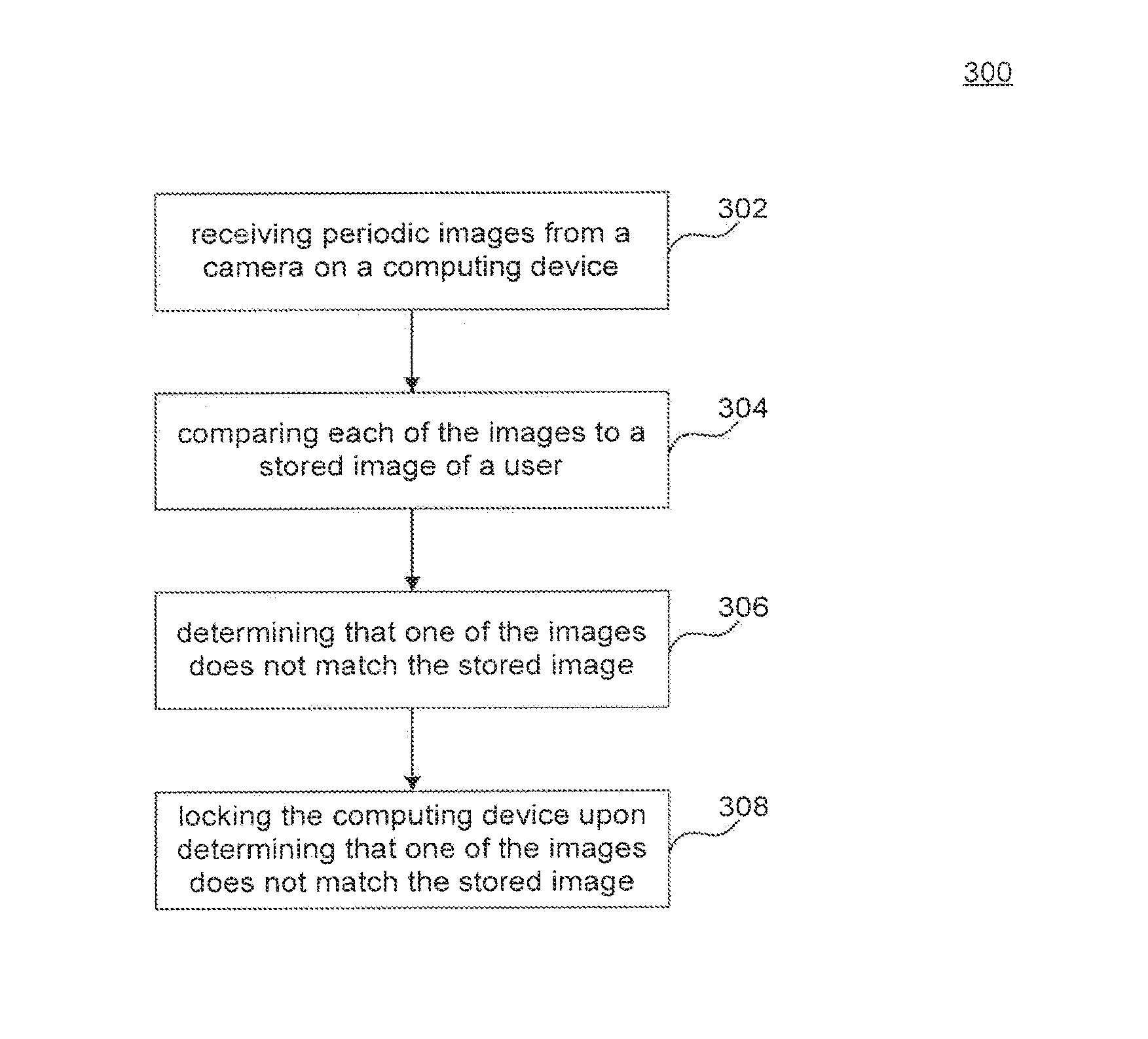
[0010]Cameras used with computing devices can be used in helping lock a computing device when persons that are not authorized users are seen using the computing device. Images of authorized users can be stored and compared against images of persons using the computing device, and depending on who is using a device, the device can be locked.
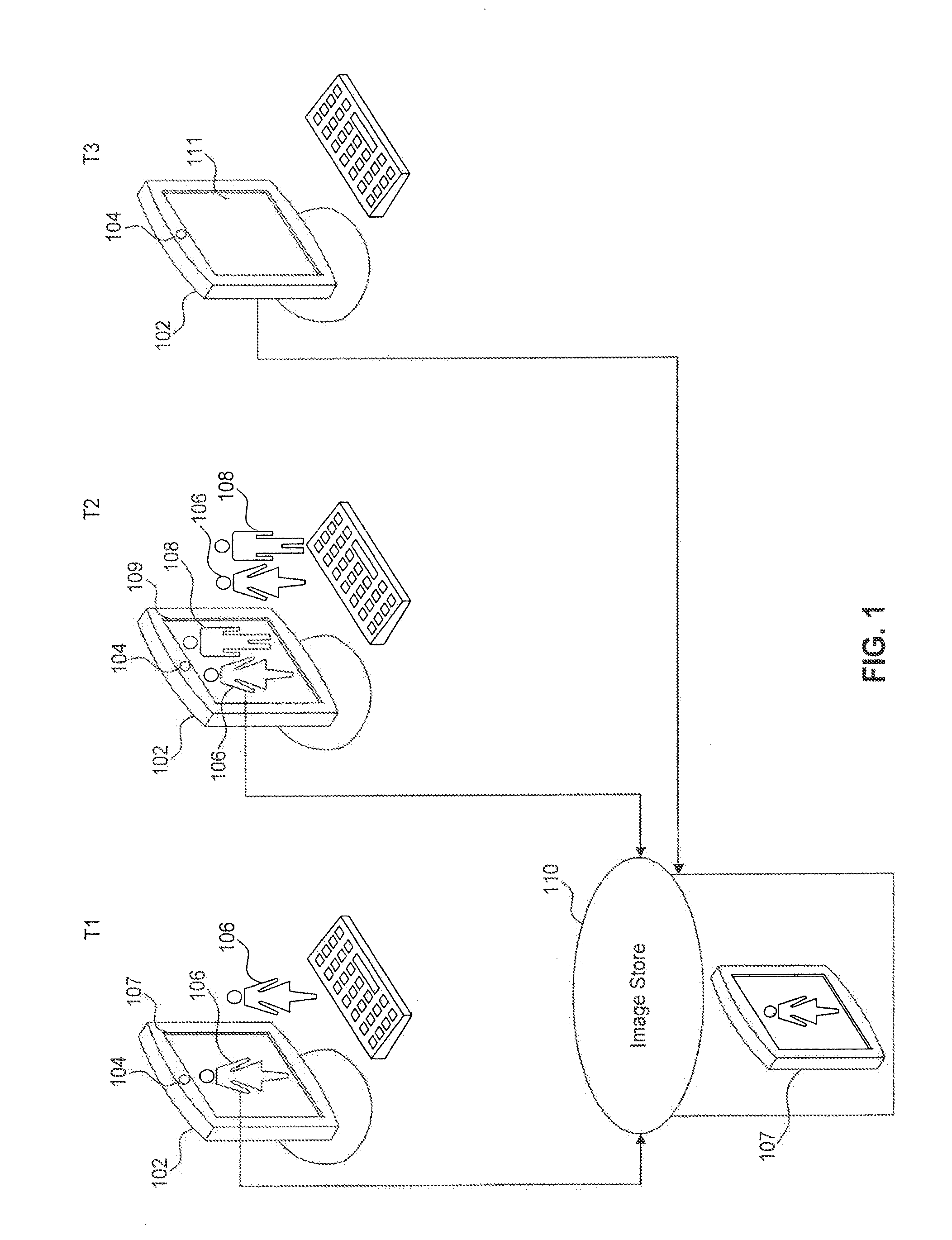
[0011]FIG. 1 displays a computing device 102 at three different time periods T1, T2, and T3. Computing device 102 may be, for example and without limitation, a device such as a desktop computer, laptop computer, mobile device, tablet computer, set top box.
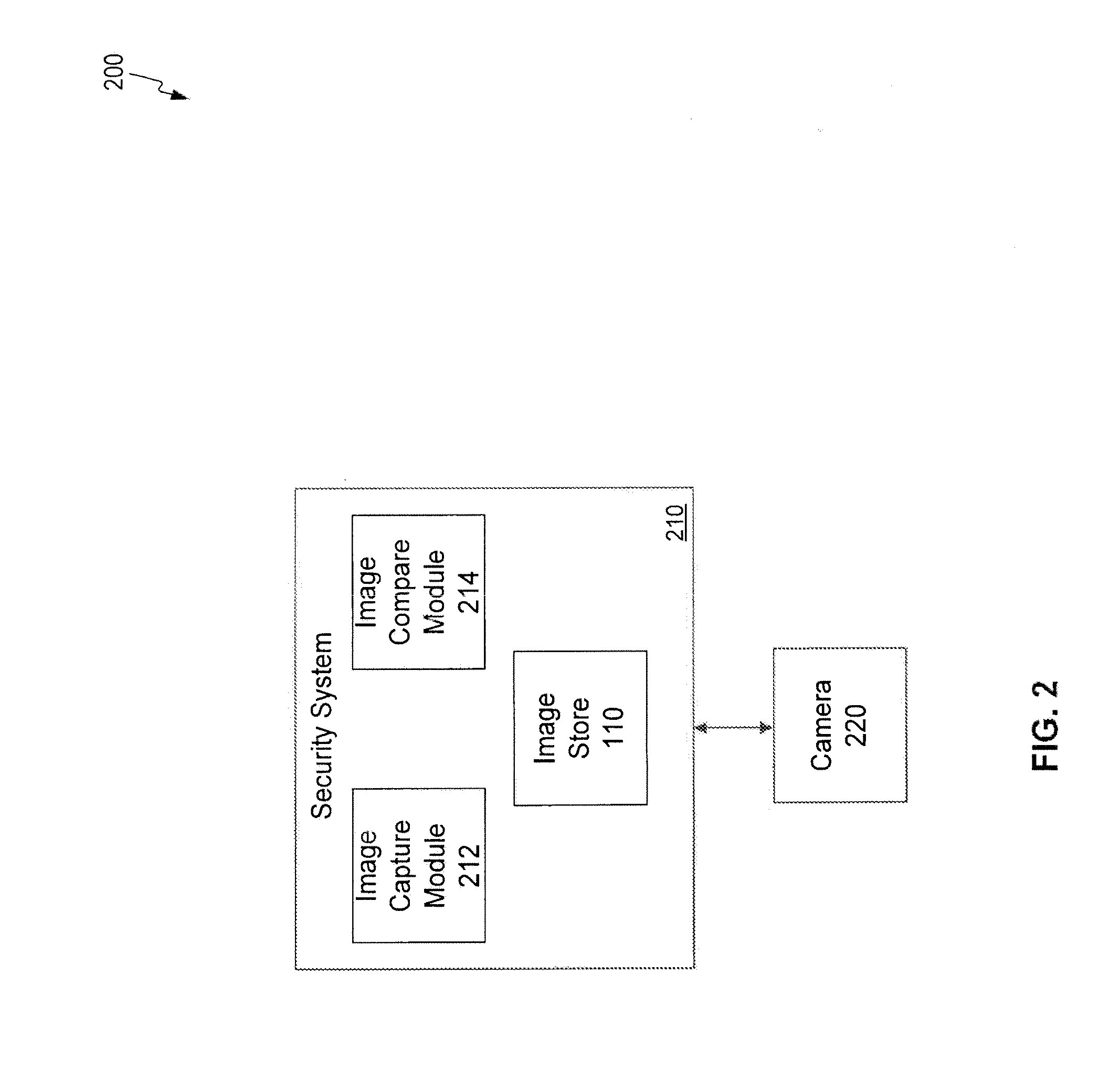
[0012]A user 106 at time T1 is using computing device 102. User 106 may be the owner of computing device 102. In one implementation, a camera 104 of the computing device 102 can be used to take an image 107 of the user 106 and the image 107 can be stored in a database 110 that is remotely connected to computing device 102, or can be part of the computing device 102. In another implementation, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com