Systems and methods for protecting private information in a mobile environment
a mobile environment and private information technology, applied in the field of protecting nonpublic information, can solve the problems of conventional systems that do not work well in mobile environments, and inability to protect private information in a mobile environmen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
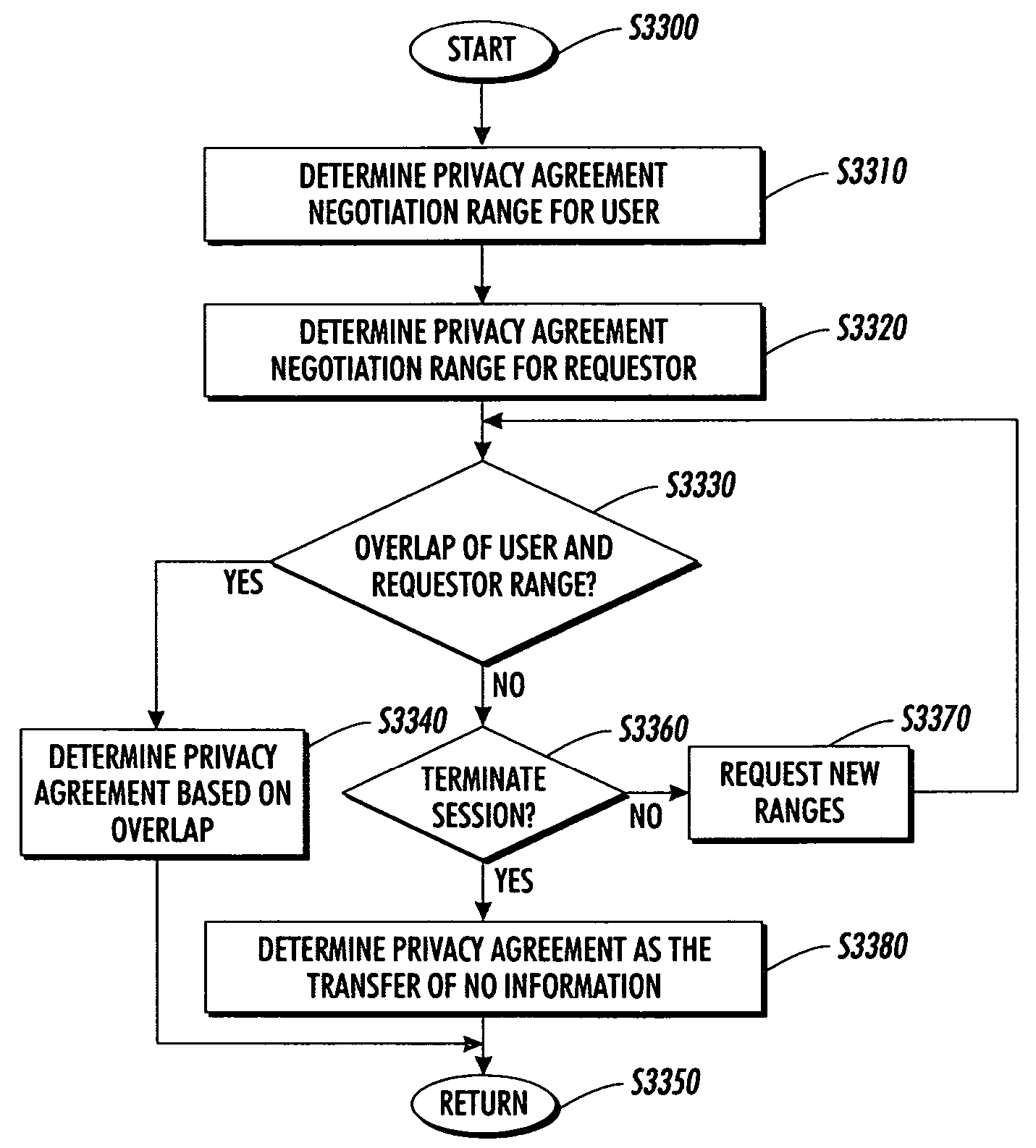
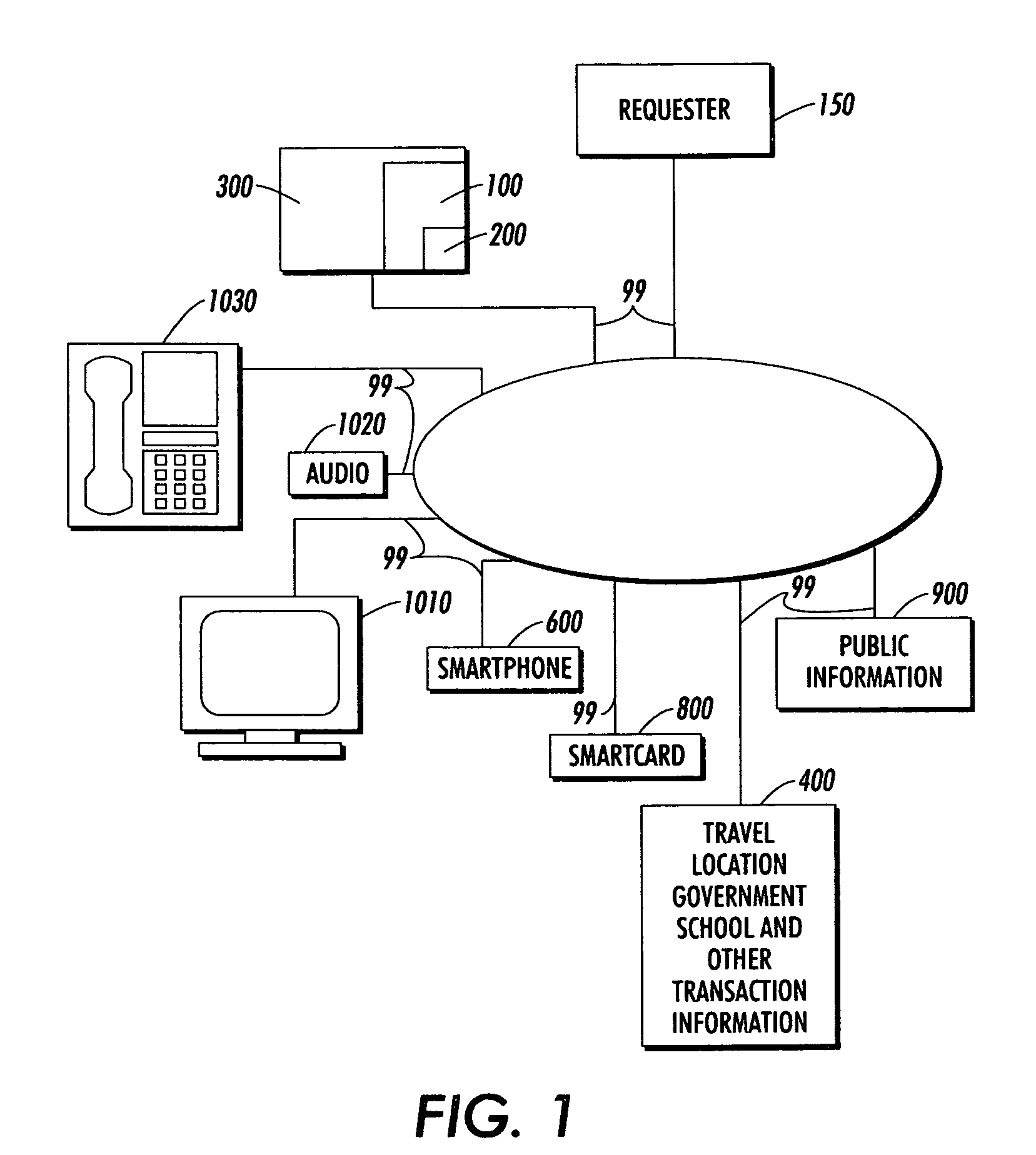
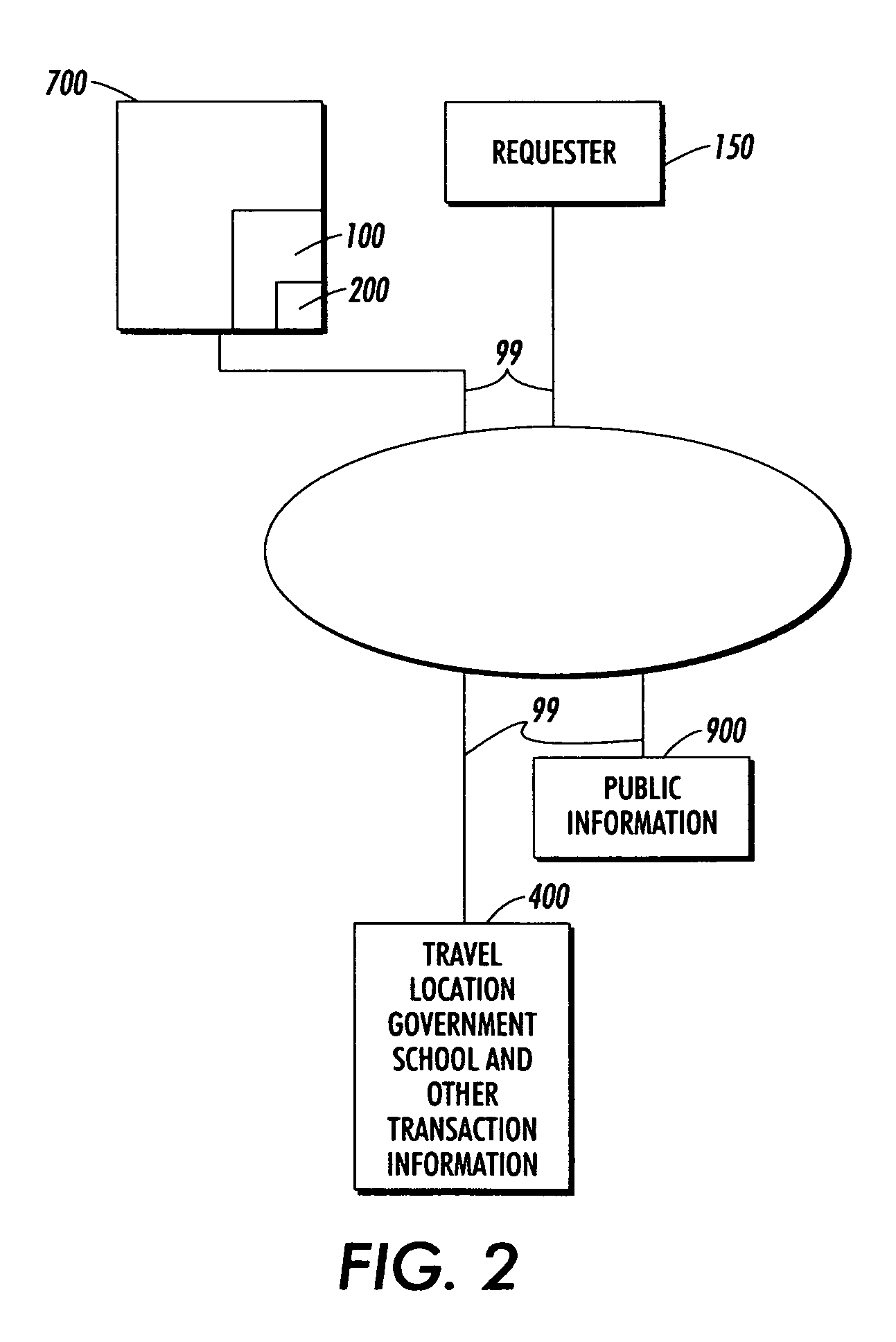
[0025]FIG. 1 shows an overview of a first exemplary system for protecting non-public information 100 according to this invention. The system for protecting non-public information 100 is embedded within a home gateway 300 and connected to data source 400; a smartphone 600; a smartcard 800; a video viewing device 1010; an audio device 1020; a telecommunications device 1030 and public information source 900 over communication links 99. A requestor 150 submits a request for non-public information. The requestor 150 is a public or non-public entity such as an individual, an organization and / or a system seeking access to the non-public information secured by the system for protecting non-public information 100. The exemplary data source 400 may include, but is not limited to, travel, location, government, school, health, financial, sales and / or any known or later developed type of non-public information about a user. In various embodiments according to this invention, the non-public infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com