Signature apparatus, verifying apparatus, proving apparatus, encrypting apparatus, and decrypting apparatus
a verification apparatus and verification method technology, applied in the field of verification apparatus, can solve the problems of ineffective efficiency decryption method and insufficient proof of crypto scheme safety, and achieve the effect of reducing the amount of calculation and high safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first exemplary embodiment
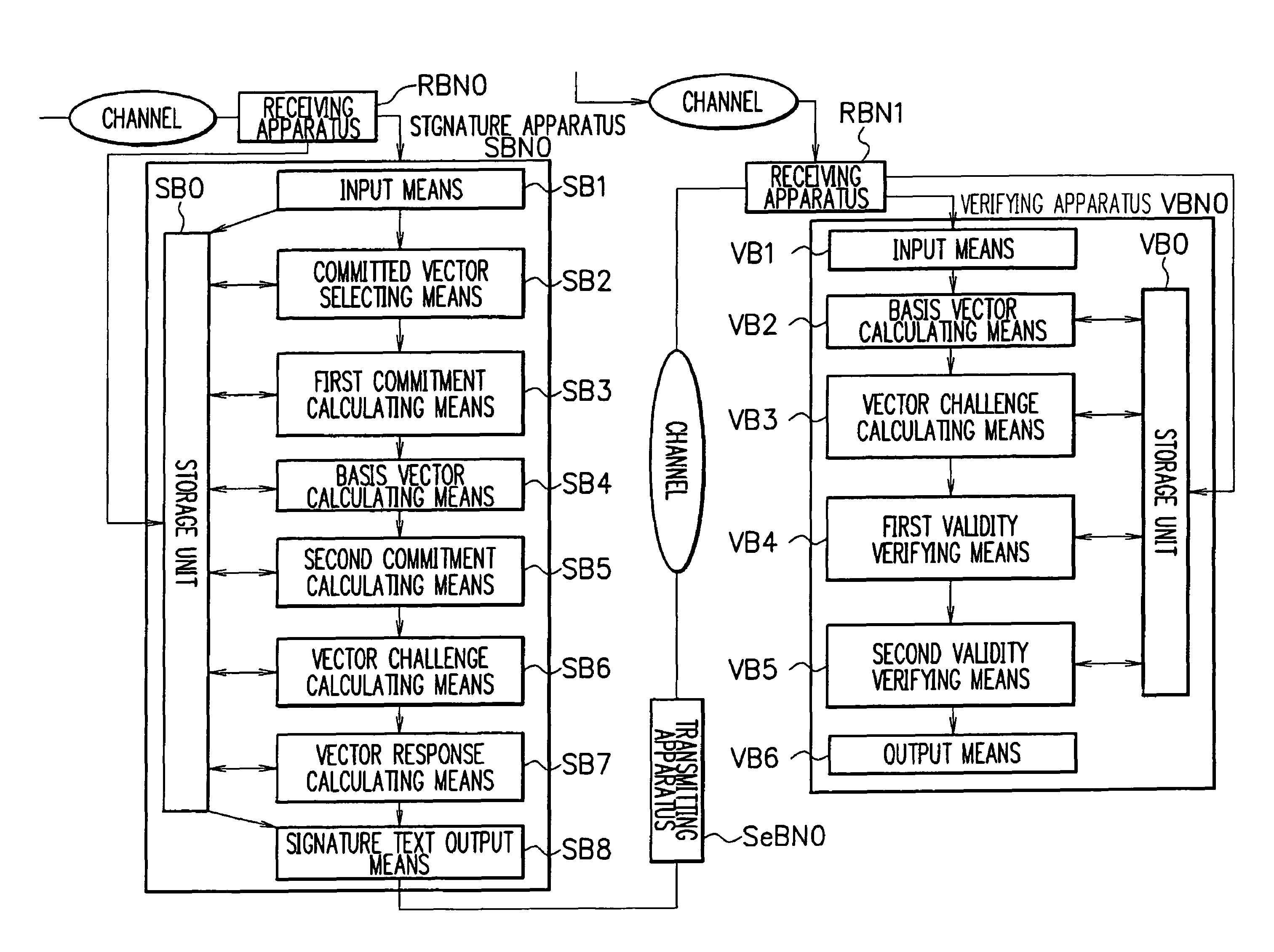
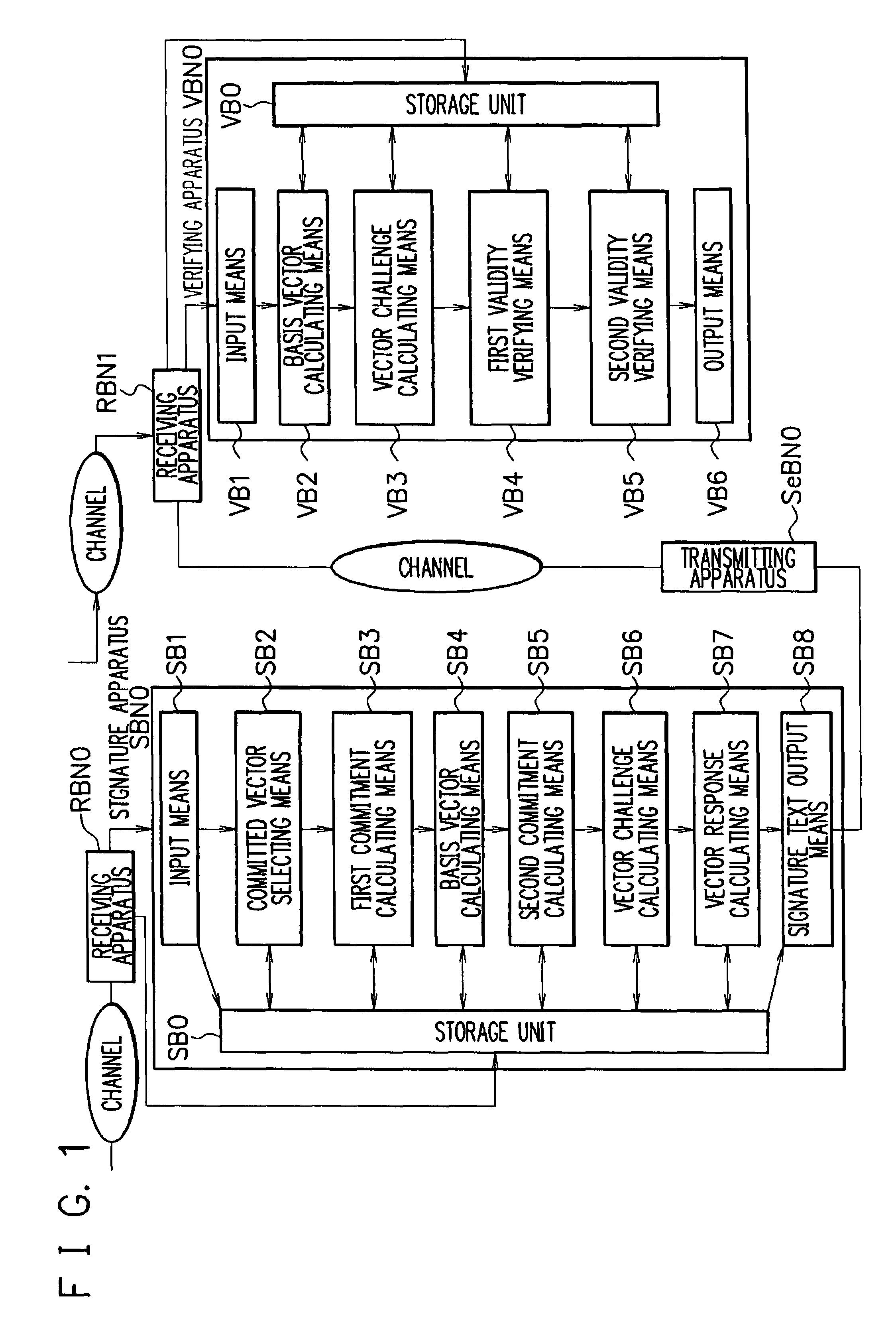
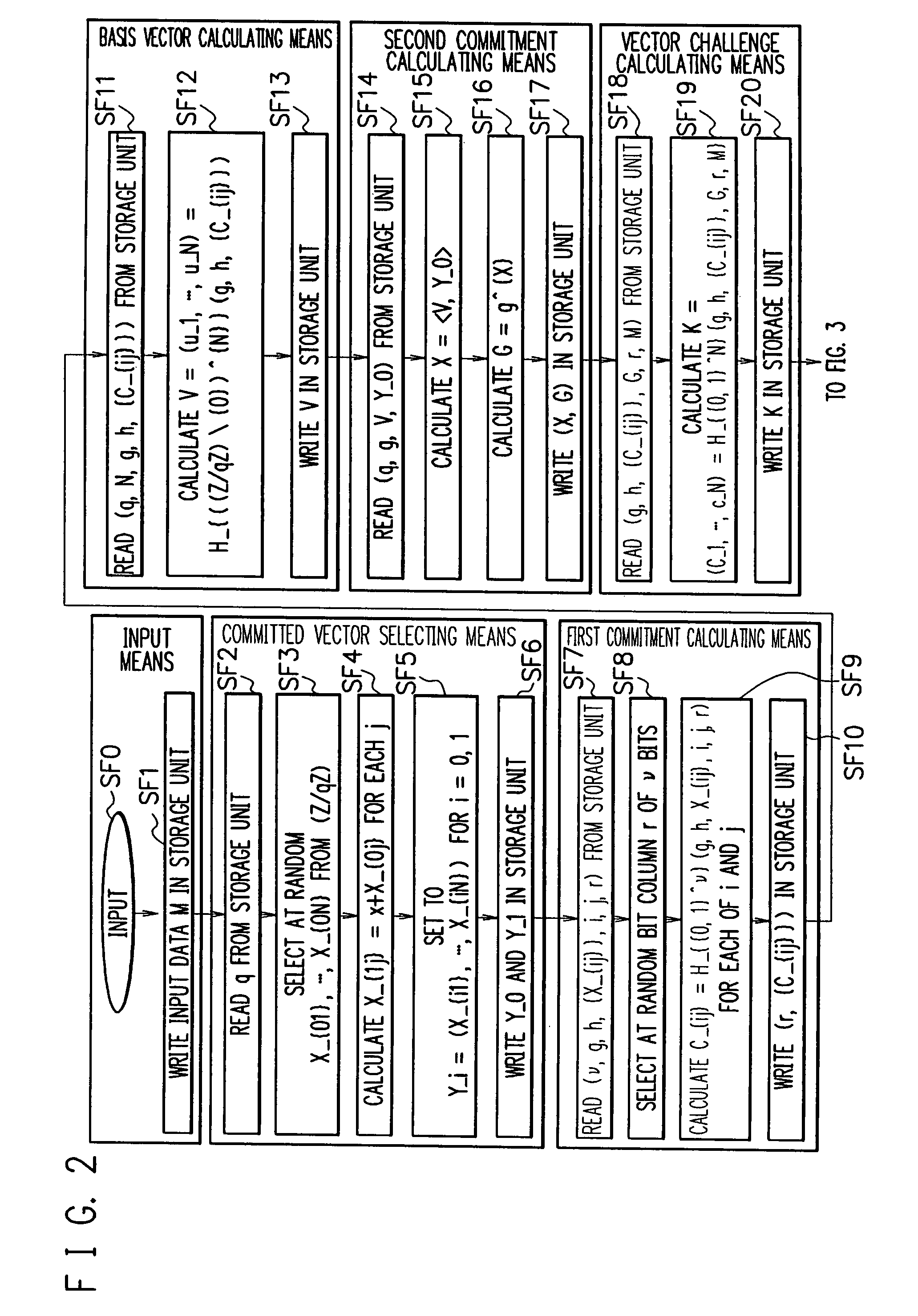
[0069]FIG. 1 is a block diagram illustrating configurations of a signature apparatus SBN0 and a verifying apparatus VBN0 according to a first exemplary embodiment. The signature apparatus SBN0 receives data by using a receiving apparatus RBN0 and transmits data through a transmitting apparatus SeBN0. The verifying apparatus VBN0 receives data by using a receiving apparatus RBN1. For example, LAN or Internet can be used as a channel used for data communication, but the present invention is not limited thereto.
[0070]Now, symbols used in the embodiment are described.
[0071]Symbol A denotes a cyclic group of which order is q. The number of bits of the order q is κ. Symbol g denotes a base point of the cyclic group A. It is assumed that, although the order q of the cyclic group A is publicized, the discrete logarithm problem associated with the cyclic group A is hard to falsify.
[0072]Symbol Z denotes a ring of all integers. Symbol N denotes a set of all natural numbers. An i-th component ...
second exemplary embodiment
[0105]FIG. 1 is a block diagram illustrating configurations of a signature apparatus SBN0 and a verifying apparatus VBN0 according to a second exemplary embodiment. The signature apparatus SBN0 receives data by using a receiving apparatus RBN0 and transmits data through a transmitting apparatus SeBN0. The verifying apparatus VBN0 receives data by using a receiving apparatus RBN1. For example, LAN or Internet can be used for transmission / reception of data, but the present invention is not limited thereto.
[0106]Now, symbols used in the embodiment are described.
[0107]Symbol A denotes a cyclic group of which order is q. The number of bits of the order q is κ. Symbol g denotes a base point of the cyclic group A. In addition, it is assumed that, although the order q of the cyclic group A is publicized, the discrete logarithm problem associated with the cyclic group A is hard to falsify.
[0108]Symbol Z denotes a ring of all integers. Symbol N denotes a set of all natural numbers. An i-th co...
third exemplary embodiment
[0138]FIG. 8 is a block diagram illustrating configurations of a signature apparatus SB30 and a verifying apparatus VBN30 according to a third exemplary embodiment. The signature apparatus SB30 receives data by using a receiving apparatus RBN30 and transmits data through a transmitting apparatus SeBN30. The verifying apparatus VBN30 receives data by using a receiving apparatus RBN31. For example, LAN or Internet can be used for transmission / reception of data, but the present invention is not limited thereto.
[0139]Now, symbols used in the embodiment are described.
[0140]Symbol A denotes a cyclic group of which order is q. The number of bits of the order q is κ. Symbol g denotes a base point of the cyclic group A. It is assumed that, although the order q of the cyclic group A is publicized, the discrete logarithm problem associated with the cyclic group A is hard to falsify.
[0141]Symbol Z denotes a ring of all integers. Symbol N denotes a set of all natural numbers. An i-th component o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com