Rubbish voice information detecting method and device
A technology for voice information and detection methods, applied in the field of network information security, can solve the problems of no longer applicable black and white list mechanism, inability to filter content, lack of solutions to detect SPIT behavior, etc., and achieve the effect of refining detection granularity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
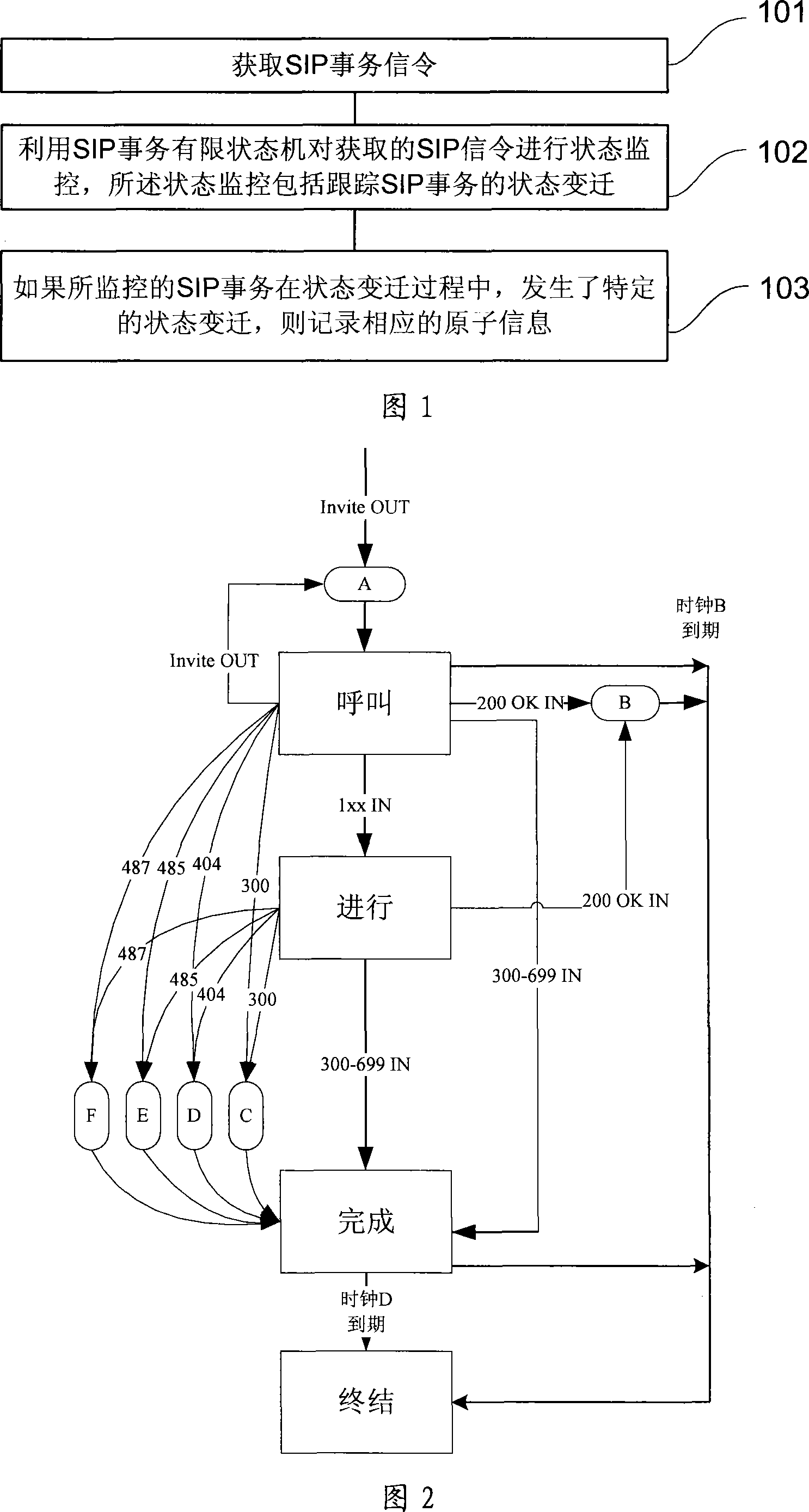
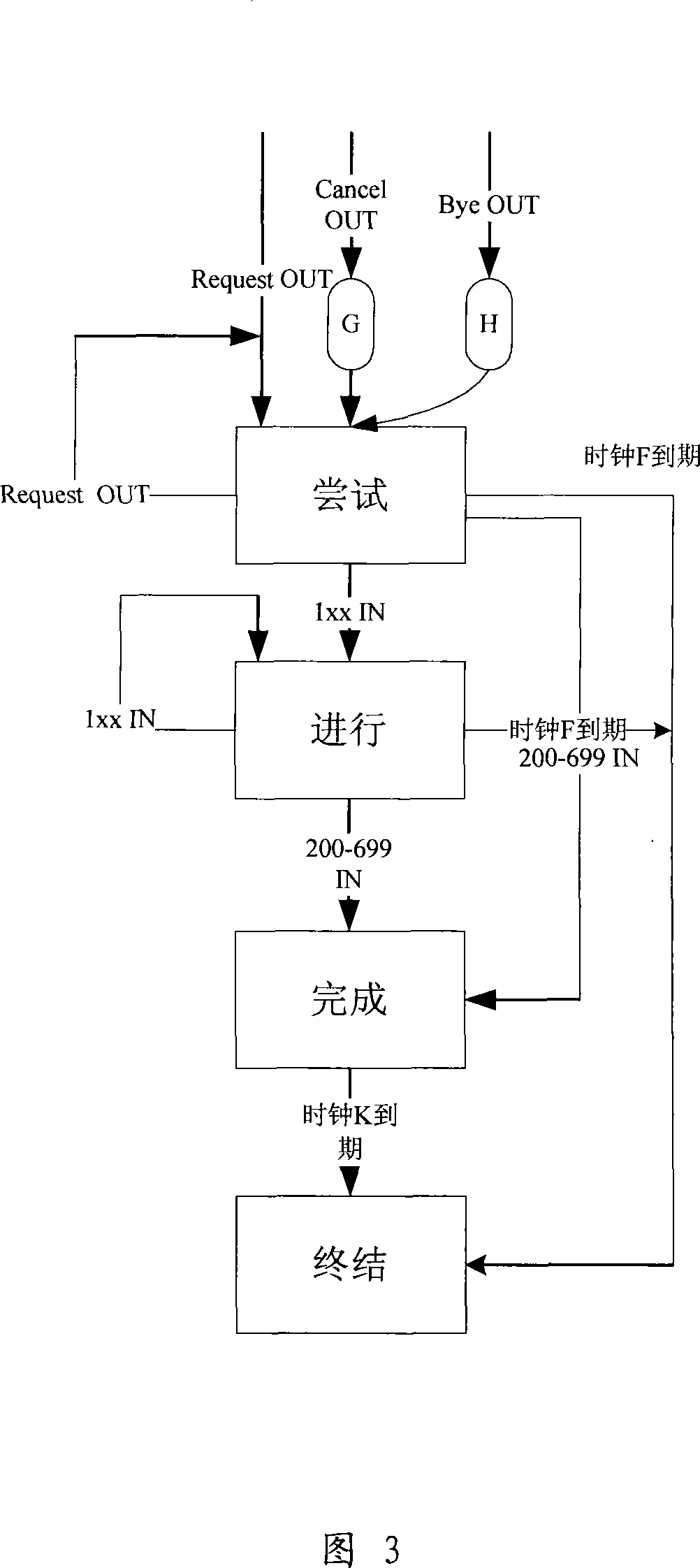
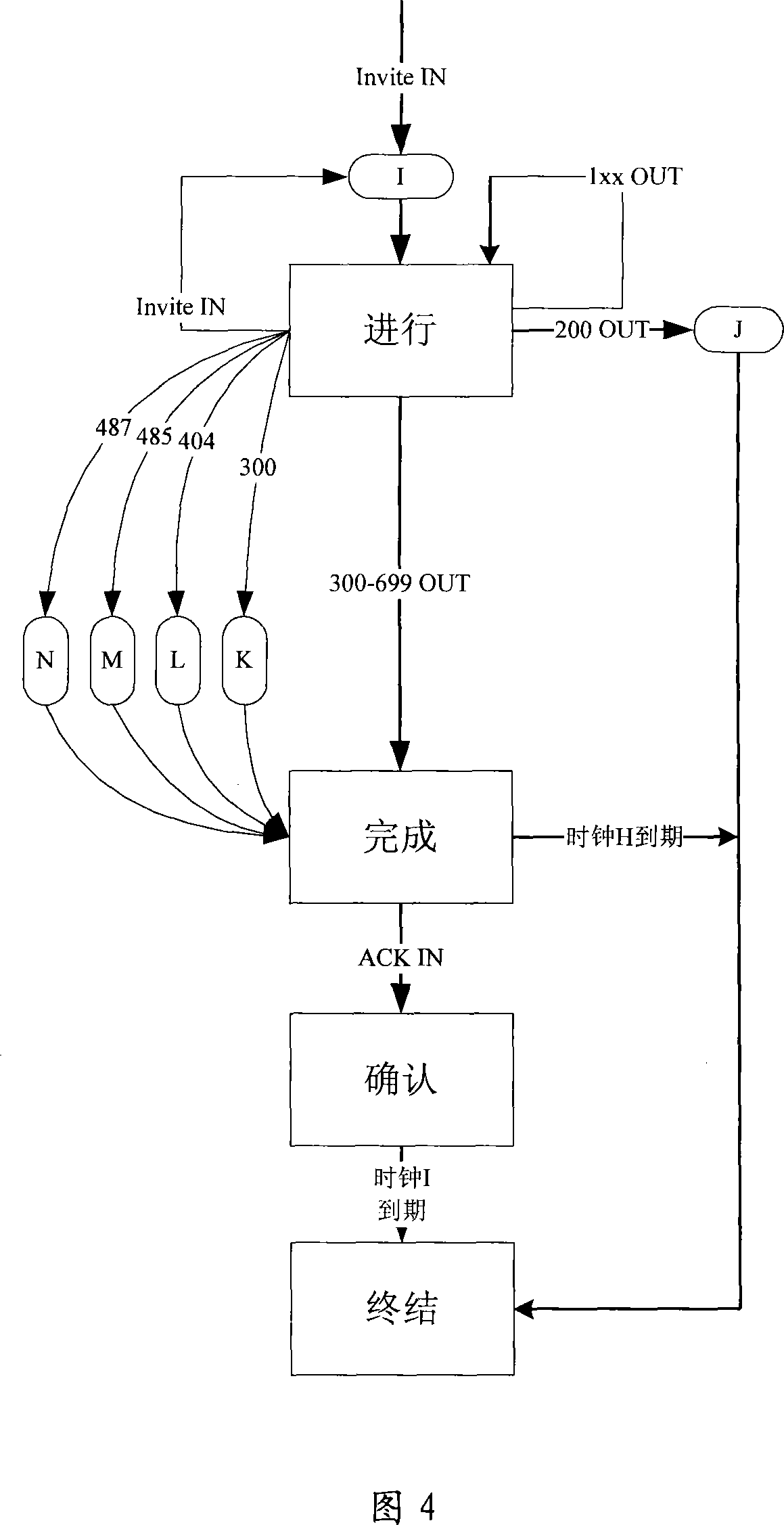
[0059] Referring to Fig. 1, it shows a kind of garbage voice information detection method embodiment 1 of the present invention, specifically may include:
[0060] Step 101, obtaining SIP transaction signaling;
[0061] Step 102, using the SIP transaction finite state machine to monitor the state of the acquired SIP signaling, the state monitoring includes tracking the state transition of the SIP transaction;
[0062] Step 103, if the monitored SIP transaction undergoes a specific state transition during the state transition process, record the corresponding atomic information; the atomic information is related to spam voice information.
[0063] After the atomic information related to the spam voice information is recorded, it can be used for further data processing, and corresponding preventive measures can also be executed according to the detected atomic information. There are many preventive measures, such as forwarding, alarming or blocking, etc. This part is not the fo...
Embodiment 2
[0103] Referring to FIG. 6 , a second embodiment of a method for detecting spam voice information is shown, which may include:
[0104] Step 601, acquire SIP transaction signaling;
[0105] Step 602, using the SIP transaction finite state machine to monitor the state of the acquired SIP signaling, the state monitoring includes tracking the state transition of the SIP transaction;
[0106] Step 603, if the monitored SIP transaction has a specific state transition during the state transition process, then record the corresponding atomic information; the atomic information is related to spam voice information;
[0107] Step 604: Statistically analyze the detected atomic information according to a preset statistical model, and generate an alarm for confirmed spam voice information.
[0108] After the statistical results and alarm information are obtained, they can be used for further data processing, and corresponding preventive measures can also be executed according to the stat...
Embodiment 3
[0141] Referring to FIG. 7 , it shows Embodiment 3 of a method for detecting spam voice information, which may include:
[0142] Step 701, acquire SIP transaction signaling;
[0143] Step 702, using the SIP transaction finite state machine to monitor the state of the acquired SIP signaling, the state monitoring includes tracking the state transition of the SIP transaction;
[0144] Step 703, if the monitored SIP transaction has a specific state transition during the state transition process, then record the corresponding atomic information; the atomic information is related to spam voice information;
[0145] Step 704, perform statistical analysis on the detected atomic information according to the preset statistical model, and generate an alarm for the confirmed spam voice information;
[0146] Step 705, perform normalization processing on the detected atomic information and alarms obtained through statistical analysis, and obtain corresponding meta-alarms;
[0147] Step 70...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com