Verification method between electronic lock and electronic key
An electronic key and verification method technology, applied in the field of verification between electronic locks and electronic keys, can solve problems such as illegal opening of electronic locks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
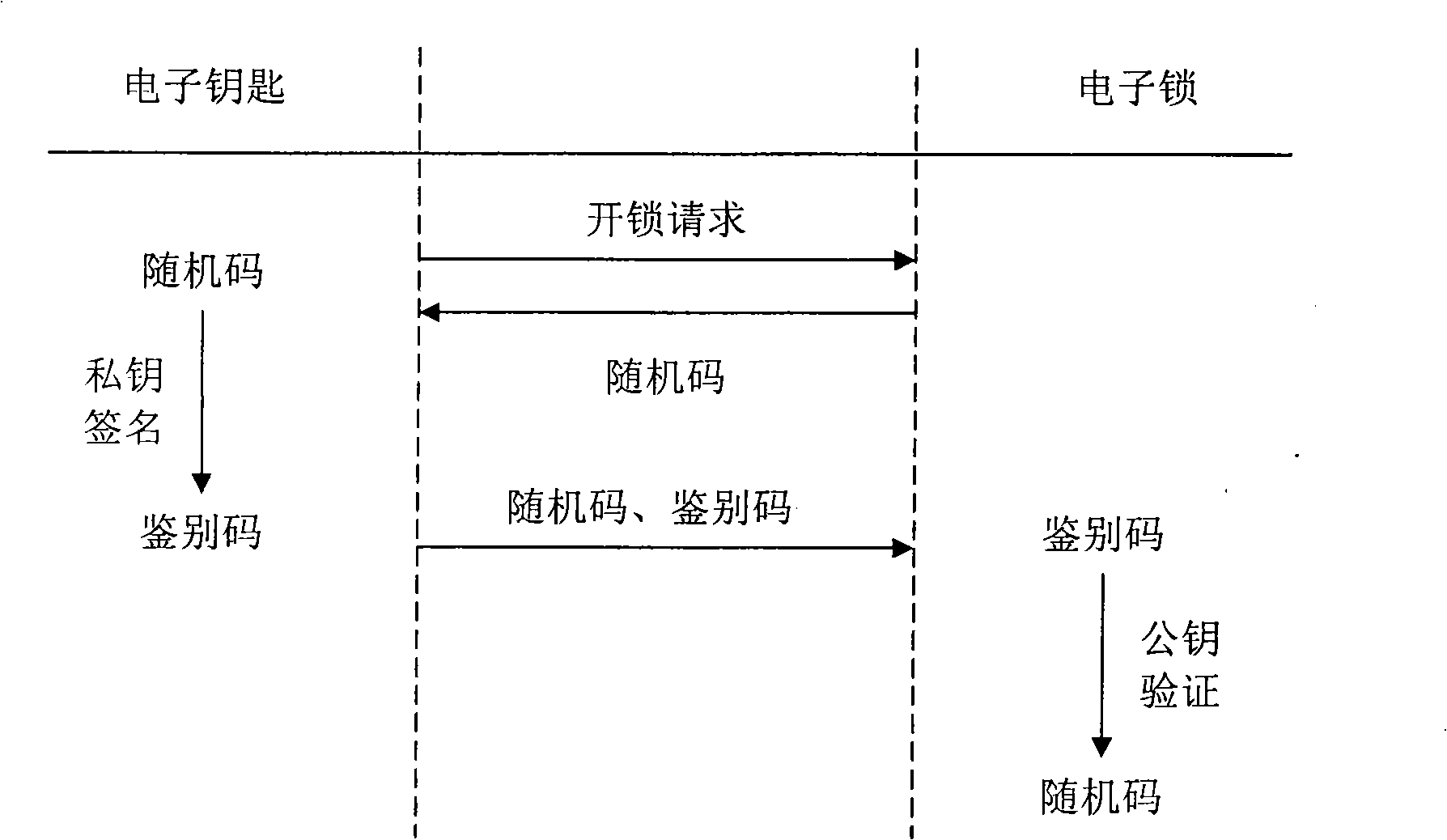
[0012] Electronic locks and keys for access control systems such as figure 1 , when the user approaches the electronic lock, the electronic lock senses the unlock request from the electronic key carried by the user, and generates a random code and sends it to the electronic key;
[0013] The electronic key signs the random code with the private key to generate an authentication code (which can be sent to the electronic lock together with the above random code);
[0014] The electronic lock verifies the authentication code with the public key, and if the generated verification result is consistent with the random code, unlocking is allowed, otherwise, unlocking is refused.
[0015] The public key can be pre-stored in the electronic lock; it can also be pre-stored in the electronic key, and the electronic key sends the public key to the electronic lock during verification.
Embodiment 2
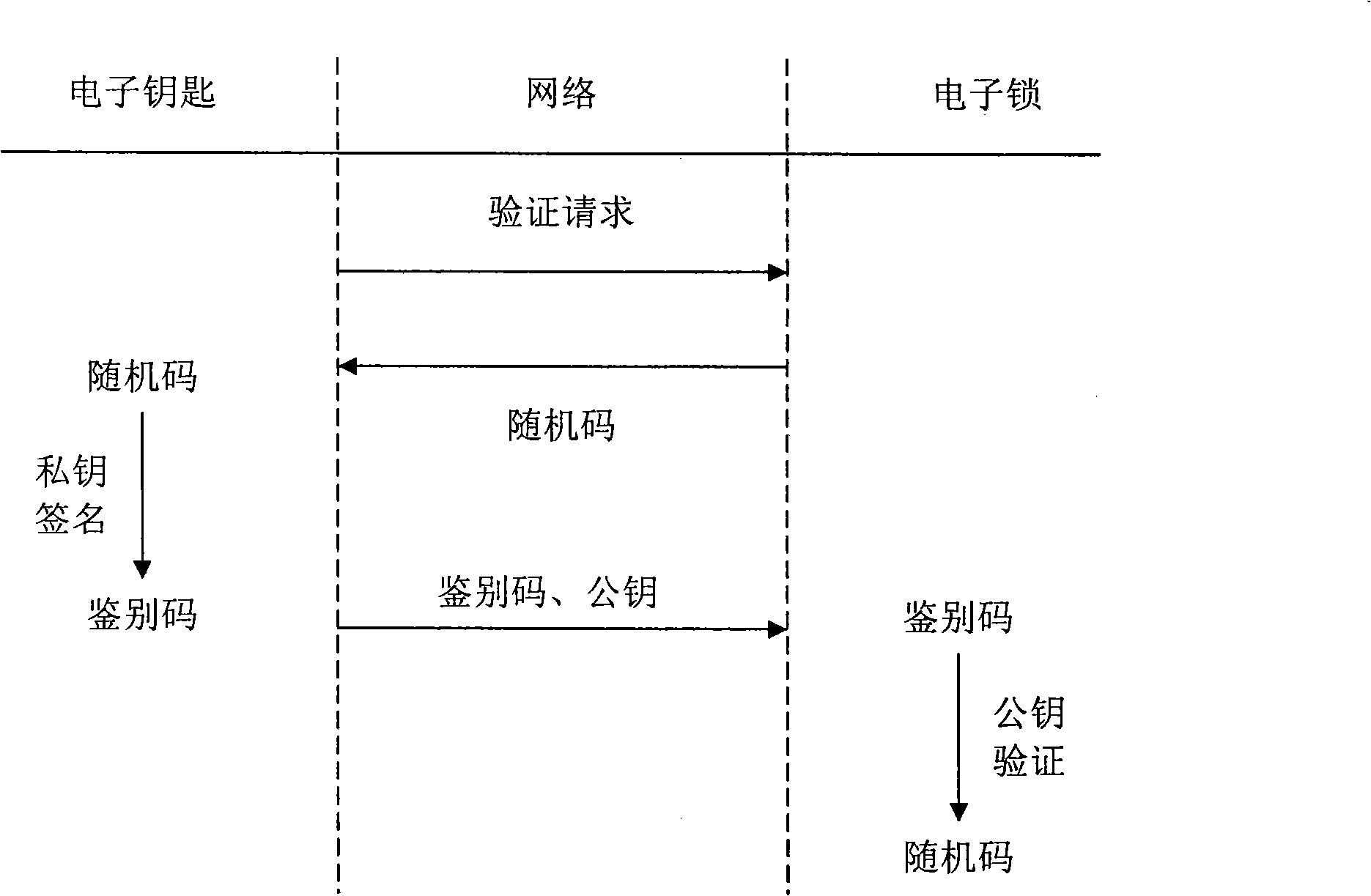
[0017] Electronic locks and keys with remote authentication such as figure 2 . When authenticating:
[0018] The electronic key sends a remote verification request to the electronic lock through the network;
[0019] After receiving the verification request, the electronic lock generates a random code and sends it to the electronic key;
[0020] The electronic key signs the random code with the private key to generate an authentication code (which can be sent to the electronic lock together with the above random code);
[0021] The electronic lock verifies the authentication code with the public key, and if the generated verification result is consistent with the random code, unlocking is allowed, otherwise, unlocking is refused.
[0022] The public key can be pre-stored in the electronic lock; it can also be pre-stored in the electronic key, and the electronic key sends the public key to the electronic lock during verification.
[0023] The embodiments of the present inv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com