Network attack path prediction method
A network attack and prediction method technology, applied in the field of network security, can solve the problems that the attack cannot be detected, it is difficult for network security personnel to prevent the work in advance, and the attack path cannot be achieved, so as to reduce the cost of manpower maintenance and protect against intrusion and the effect of stealing and protecting against network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
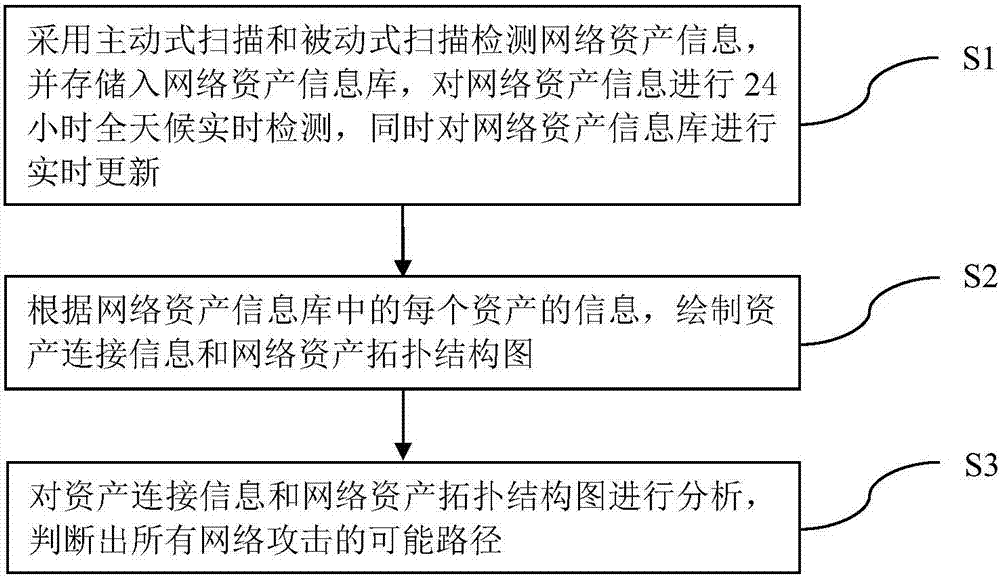
[0017] In order to make the technical means, creative features, goals and effects of the present invention easy to understand, the following embodiments will specifically illustrate the network attack path prediction method of the present invention in conjunction with the accompanying drawings.
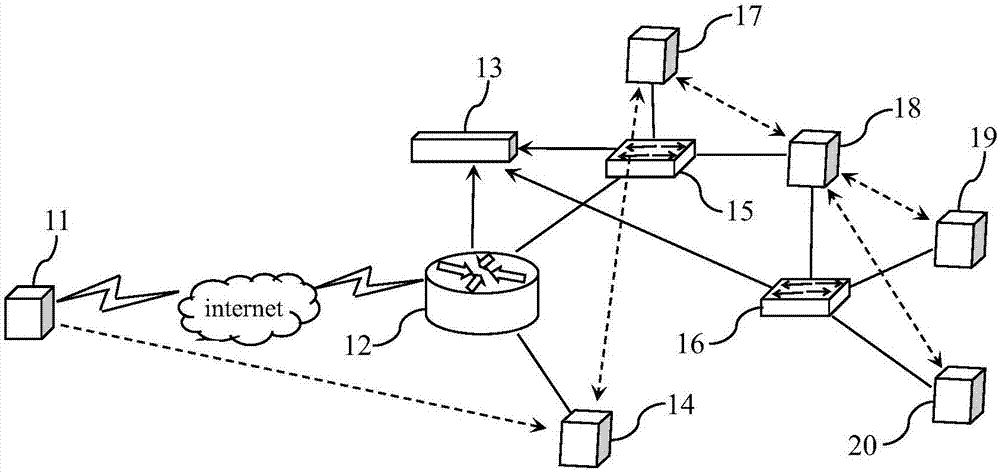
[0018] Such as figure 1 As shown, the network attack path prediction method of the present invention includes the following steps:
[0019] Step S1, using active scanning and passive scanning to capture IP data packets to discover network assets, and store them in the network asset information database, perform 24-hour real-time detection of network asset information, and update the network asset information database in real time.
[0020] In this embodiment, before the network asset information is stored, the IP data packet is split to extract data fields related to the asset information. Network assets include IP, port, protocol information, application service information, system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com