Operation method of hash table
An operation method and hash table technology, applied in the field of hash table operation, can solve problems such as affecting search performance, inapplicability of master-slave multi-core processor system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
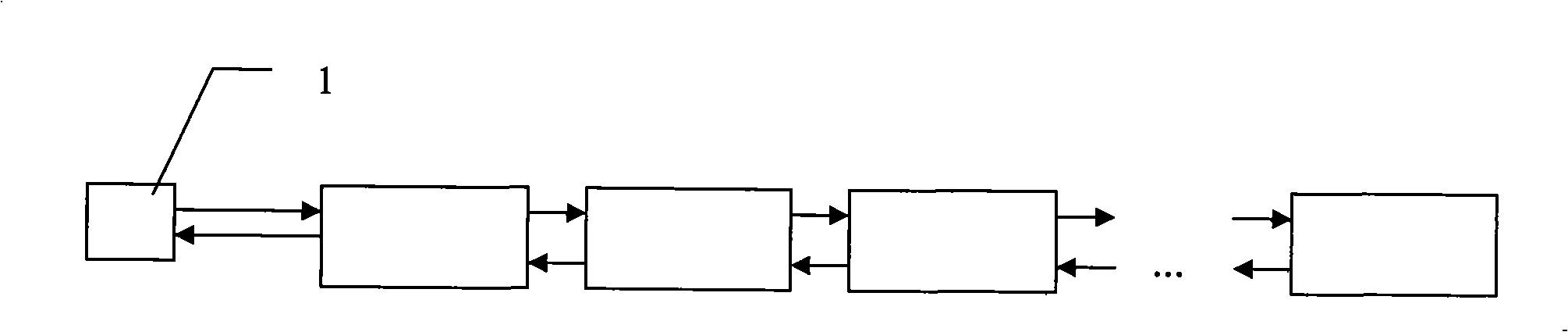
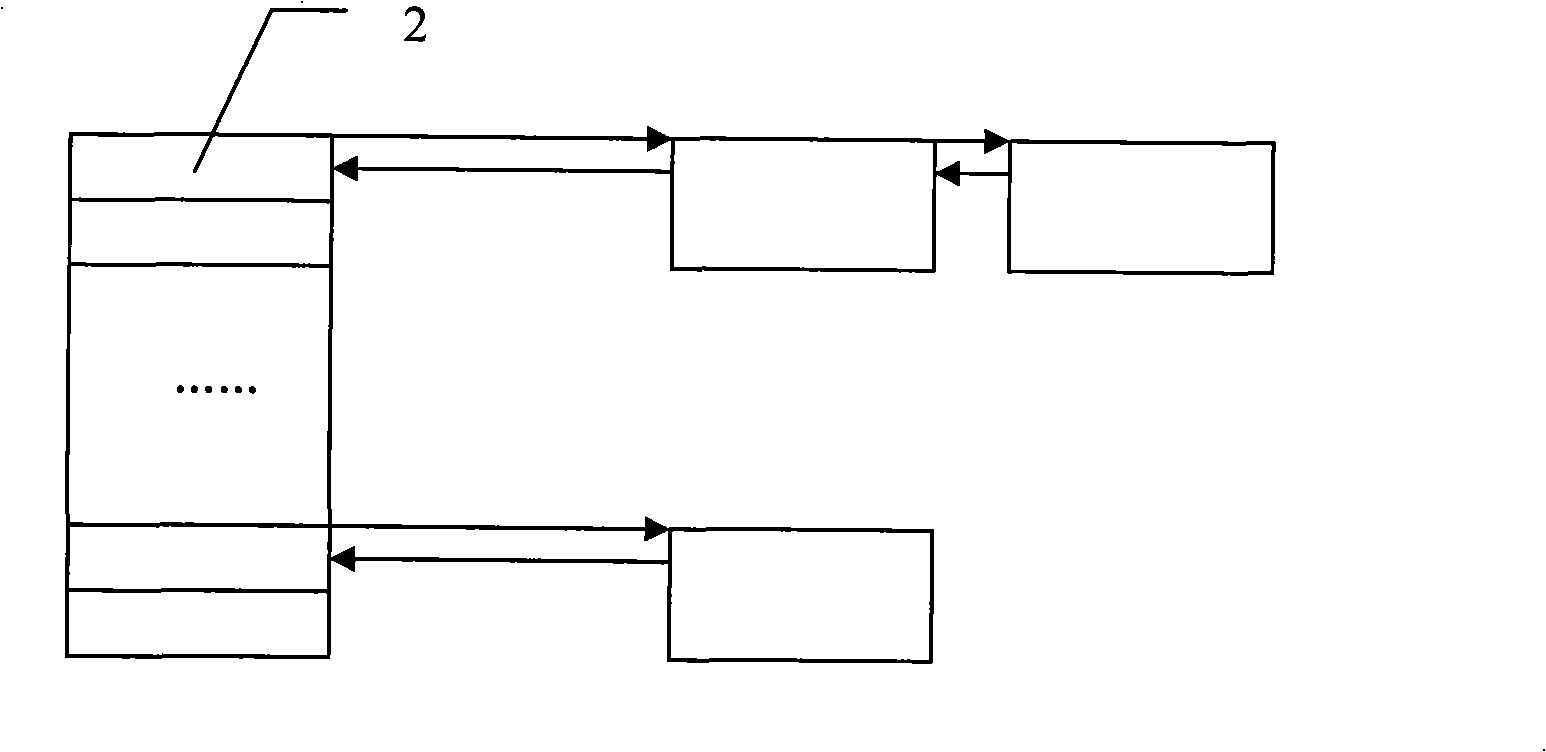
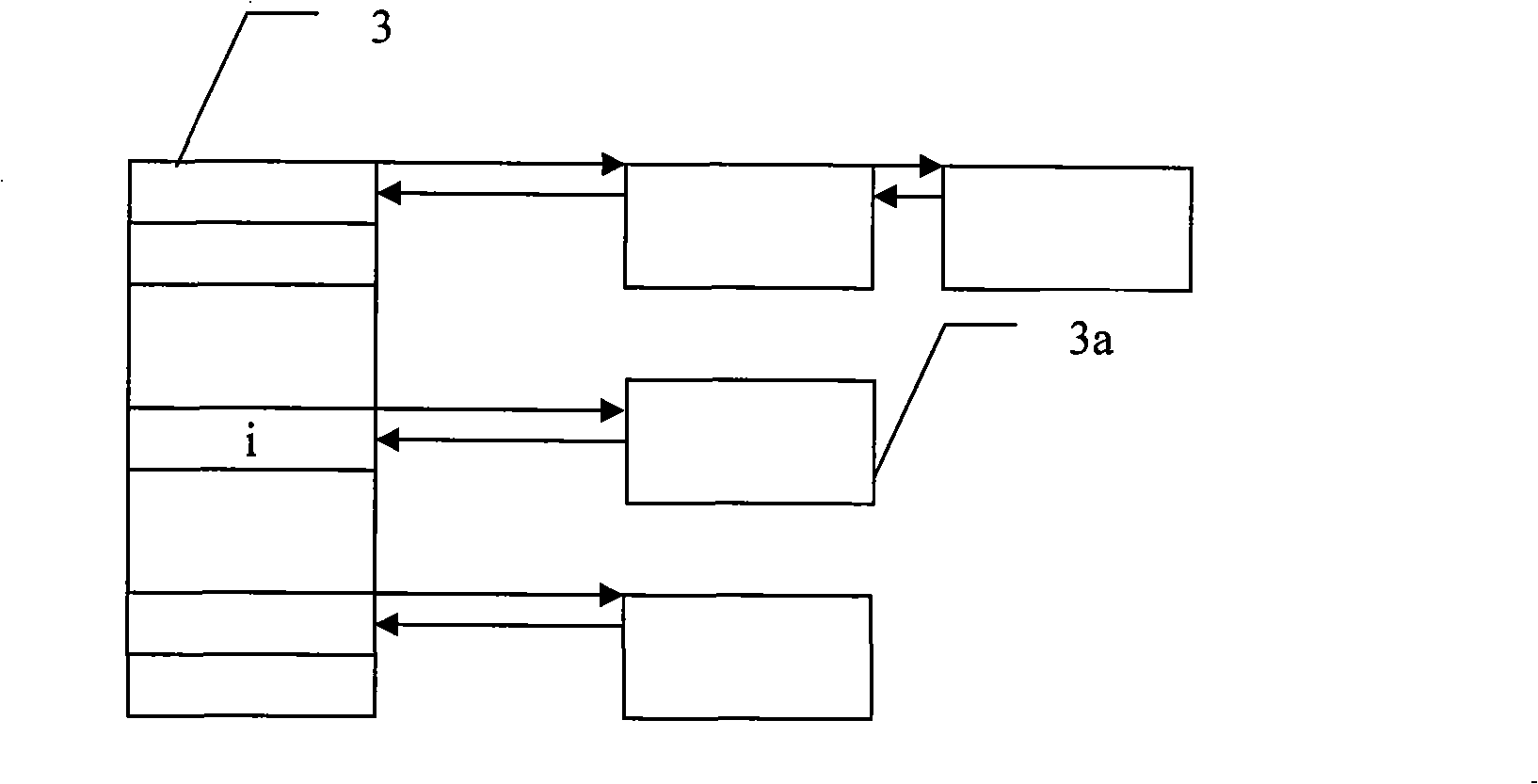
[0018] Embodiment 1: This embodiment is implemented in a master-slave multi-core processor system with one master core and one slave core. figure 1 , figure 2 , image 3 It is a schematic diagram of the Hash table and memory node linked list of two cores in this embodiment. figure 1 , figure 2 , image 3 Indicates that during initialization, operations are performed on the main core to create and initialize the first Hash table 2 and the second Hash table 3, wherein the first Hash table 2 is the Hash used by the main core for data management, and the second Hash table 3 It is the Hash table used by the slave core for data management, and then the main core allocates the required memory for the nodes corresponding to the total number of entries in the two Hash tables, and links these memory nodes through the memory node linked list 1. In order to limit the use of memory, it is generally necessary to limit the number of entries in the total Hash table, so it is reasonable ...
Embodiment 2
[0022] Embodiment 2: This embodiment is implemented in a master-slave multi-core processor system with one master core and multiple slave cores. Create a Hash table on the main core for each core including the main core and the slave core, and allocate the required memory for the nodes corresponding to the total number of entries in the Hash table of each core, and allocate these memory nodes Linked through the memory node linked list.
[0023] When a lookup operation is performed on the Hash table, the lookup operation of the Hash table of the master core is performed on the master core, and the lookup operation of the Hash tables of each slave core is performed on each corresponding slave core.
[0024] Insertion, deletion, and update operations on each slave core are as in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com