Software self-protection method
A software and protected technology, applied in the field of all-round software self-protection, can solve problems such as difficult to protect safe software damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
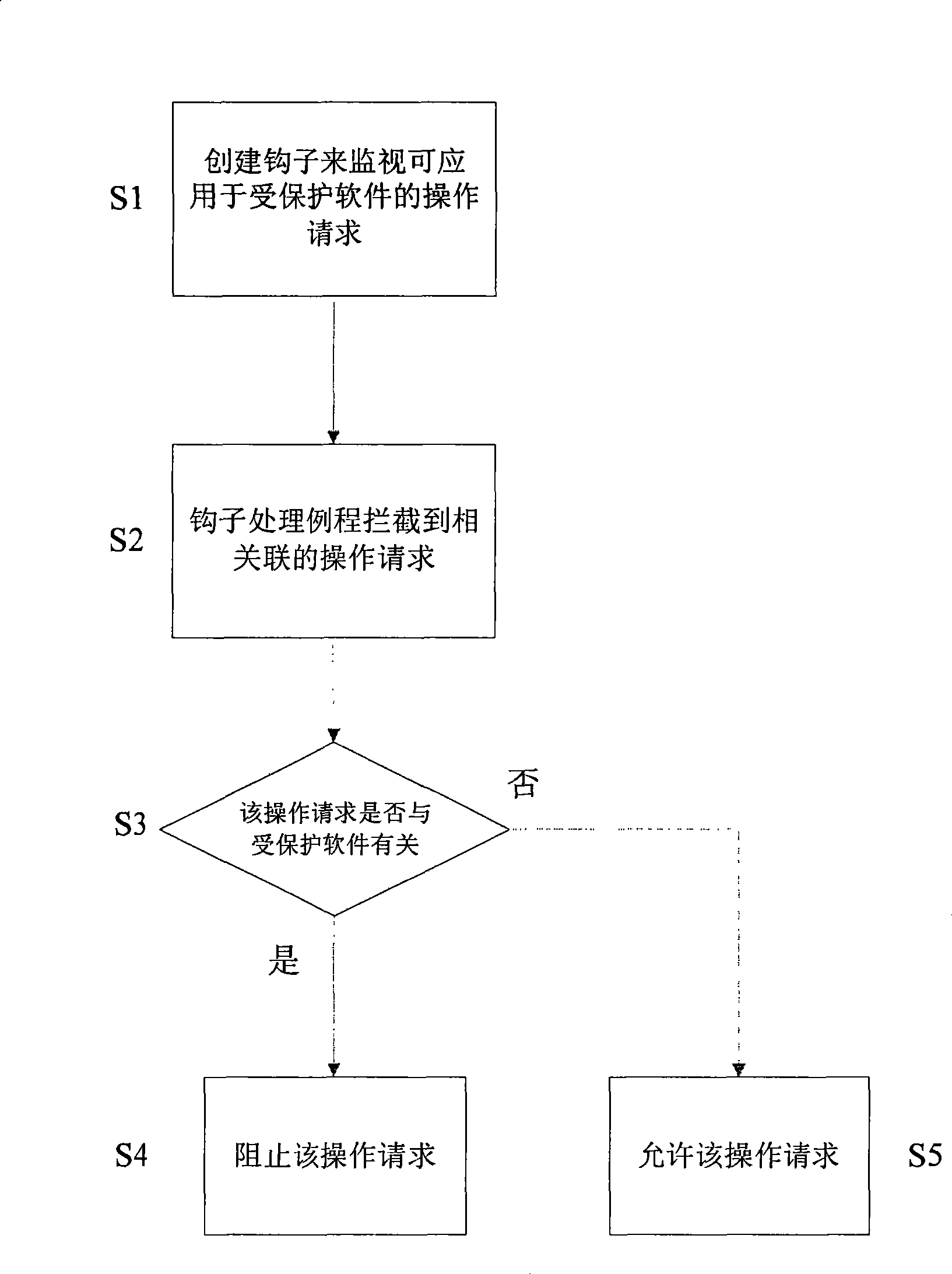
[0011] Combine below figure 1 A specific embodiment of realizing software protection according to the comprehensive software self-protection strategy of the present invention is described.
[0012] figure 1 A flow chart of protecting software by monitoring operation requests applicable to the protected software is exemplarily shown. In step S1, a hook processing routine hooked to a certain operation request is created to intercept the associated operation request. The operation request can be implemented, for example, by calling an API, so that the corresponding hook processing routine is monitored by hooking this API. For the set of operation requests to be monitored in the present invention, an associated hook processing routine can be created for each operation request for monitoring. In step S2, when the operation request is intercepted, for example, when the hook processing routine intercepts that the associated API is called, before processing the operation request, f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com