Method and system for implementing network authentication
A network authentication and network technology, applied in the field of authentication, can solve the problems of easy loss, additional carrying of smart cards, poor convenience, etc., and achieve the effect of preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
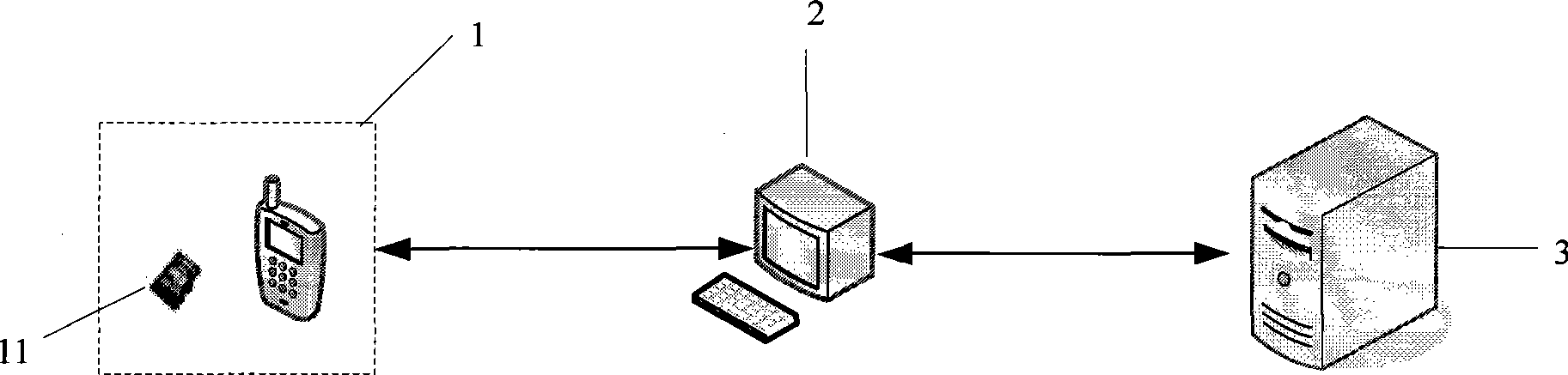
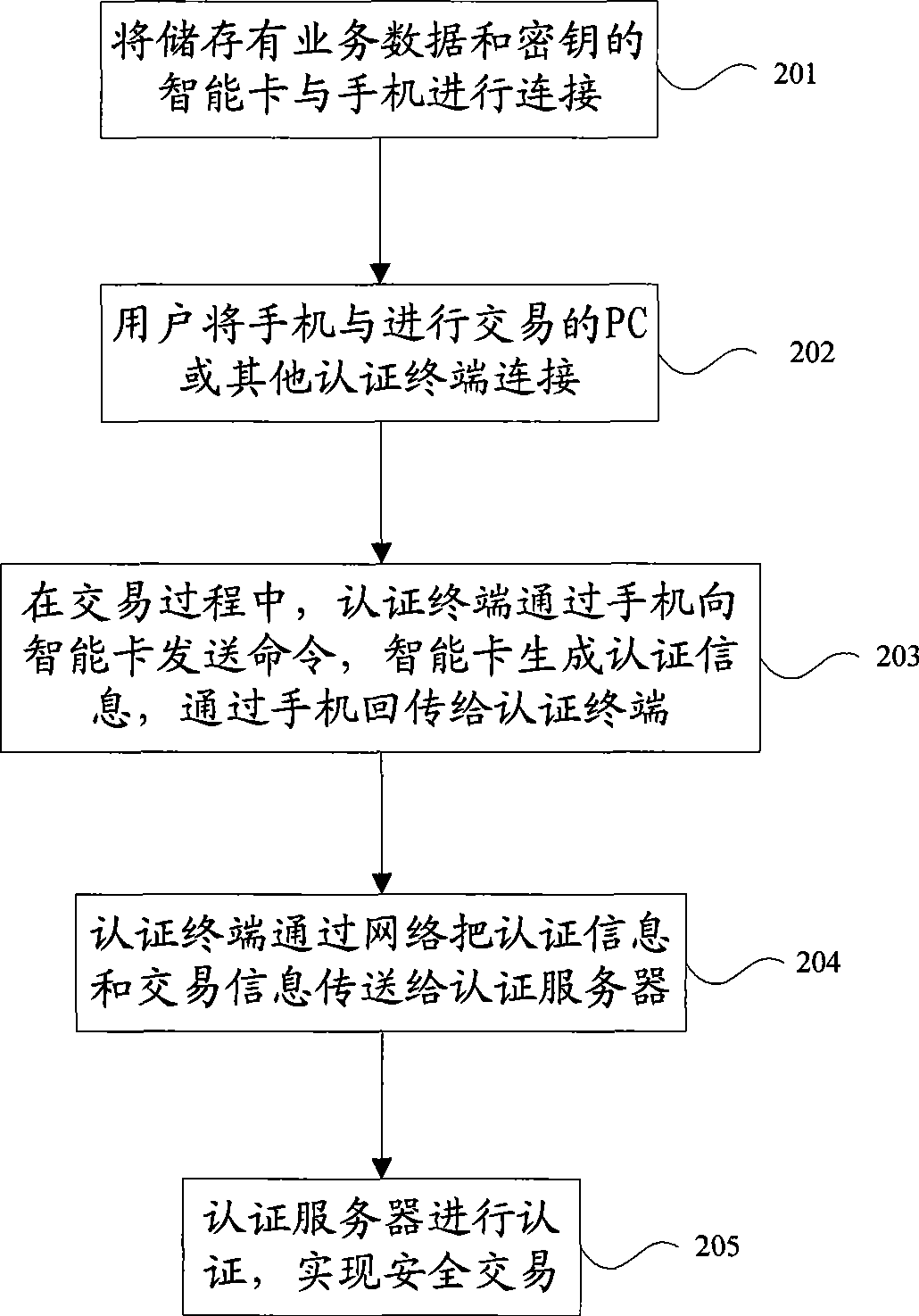
[0016] The embodiment of the present invention adopts smart card technology, uses the mobile terminal, which is widely used nowadays, as the carrier of the smart card, and uses the mobile phone to replace the traditional smart password key as the authentication medium to realize safe and convenient network authentication. The present invention changes the disadvantages of the existing users who must carry an additional smart password key for network authentication. At the same time, the mobile phone keyboard can be used to input data and display it on the display screen, effectively preventing man-in-the-middle attacks in the authentication process, and improving authentication security. With a more reliable guarantee.
[0017] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0018] figure 1 It is a system structure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com