IP voice hidden communication method based on stream encryption
A technology of covert communication and stream encryption, applied in the field of secure communication, can solve problems such as voice quality damage, and achieve the effect of good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described below in conjunction with the accompanying drawings.
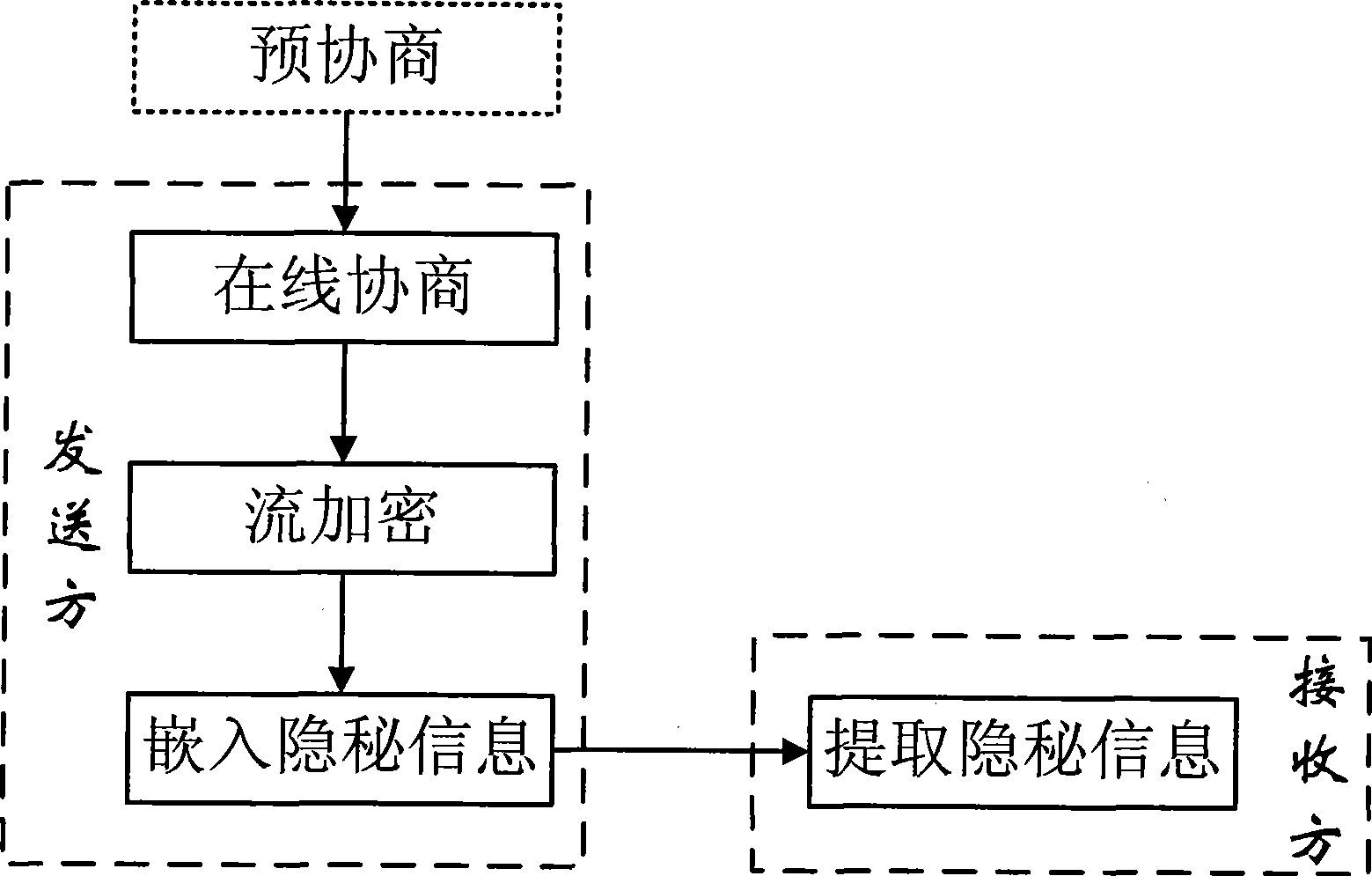
[0045] The processing flow of the present invention is as figure 1 Shown: including pre-agreement steps, online negotiation steps, stream encryption steps, embedding secret information steps and extracting secret information steps.
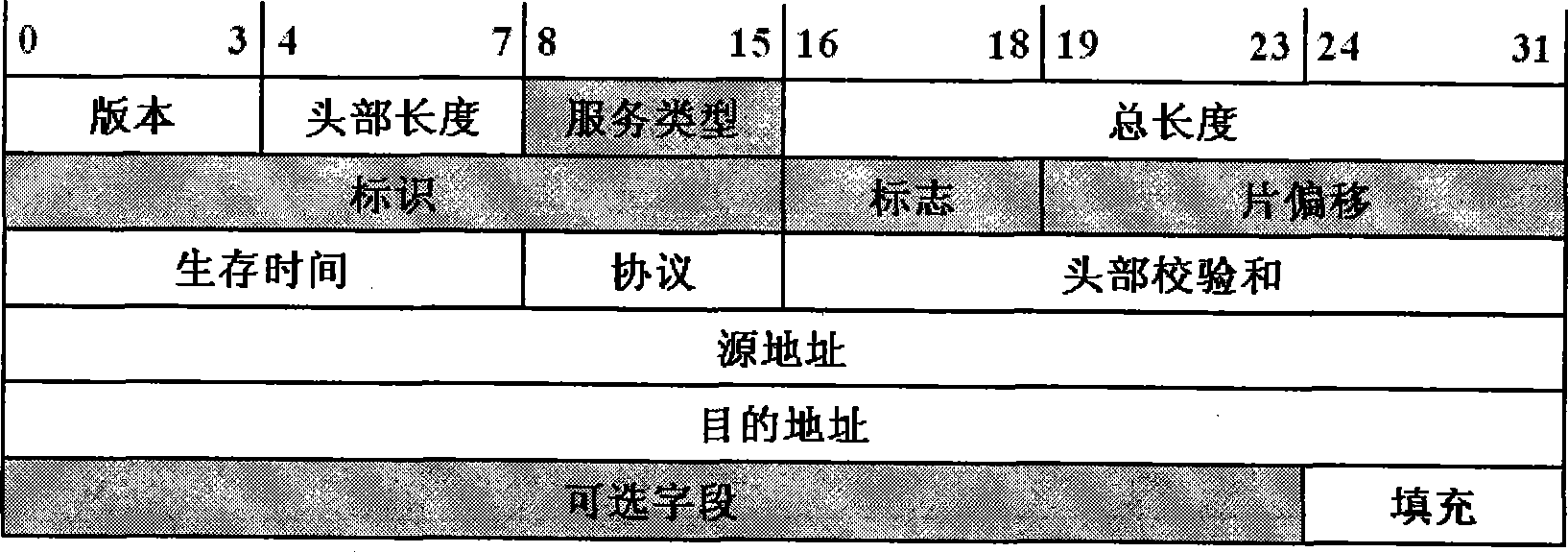
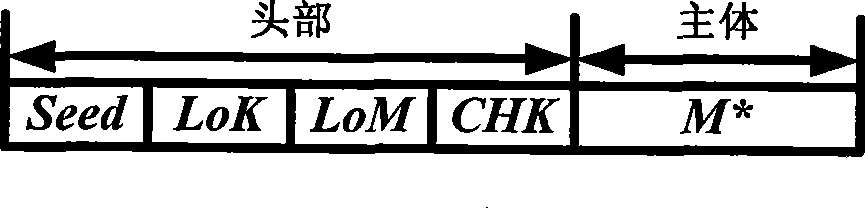
[0046] In the pre-agreement step, the two parties in the communication pre-agreed: (1) Embedding a synchronization bit sequence in the header of the first Internet protocol data packet in communication. The reasons are as follows: VoIP is built on IP technology, and all voice frames are encapsulated in Internet Protocol data packets for transmission. However, there are many unused bits in the header of the Internet protocol data packet, such as figure 2 As shown in the shaded field, there are a total of 64 bits in total. Therefore, the synchronous bit sequence (Beginning of Message, BoM) can be "hidden" in the header of the Internet pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com