Method for mobile terminal authentication
A mobile terminal, identity authentication technology, applied in the field of identity authentication, can solve problems such as user loss and user password leakage, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
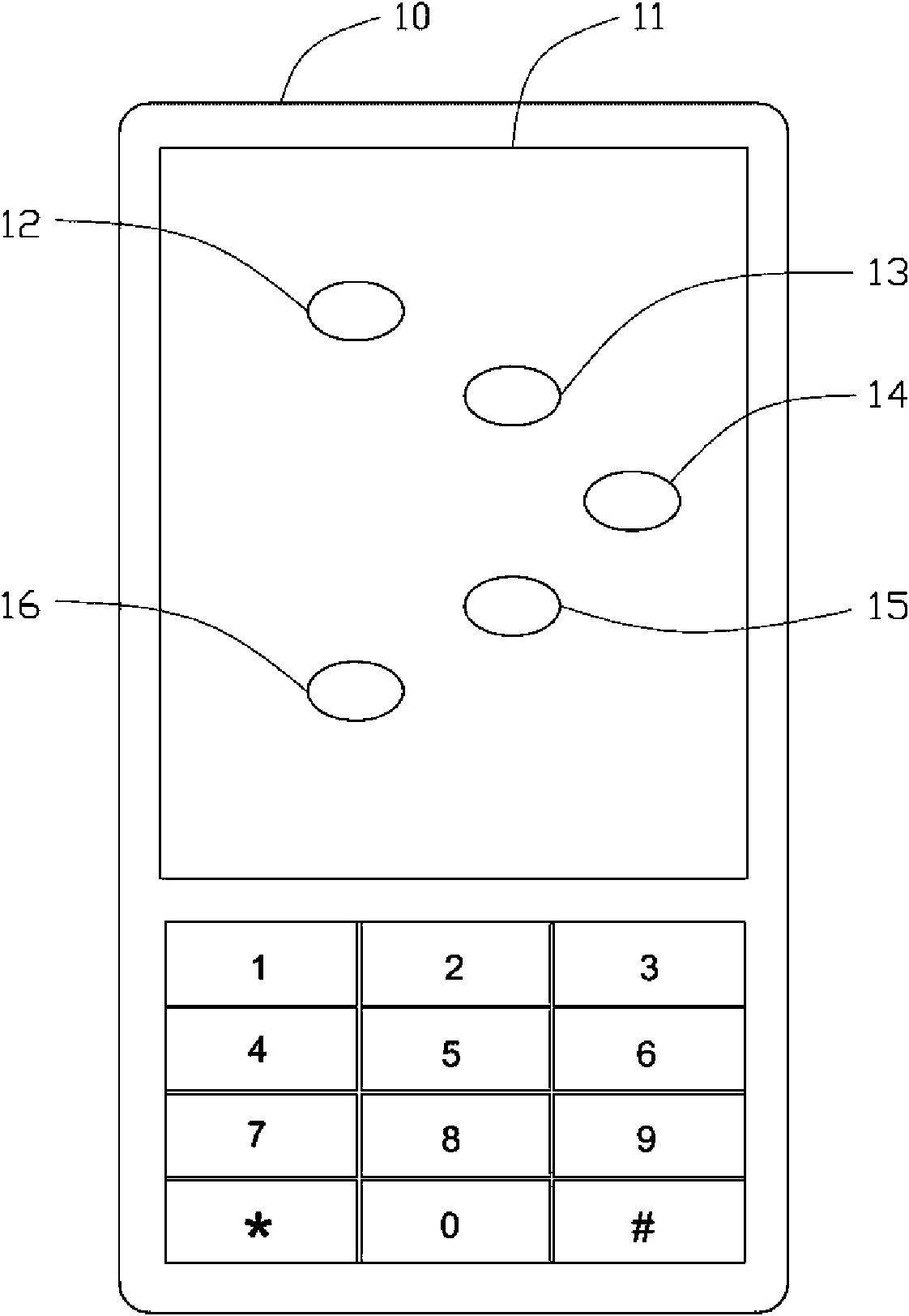
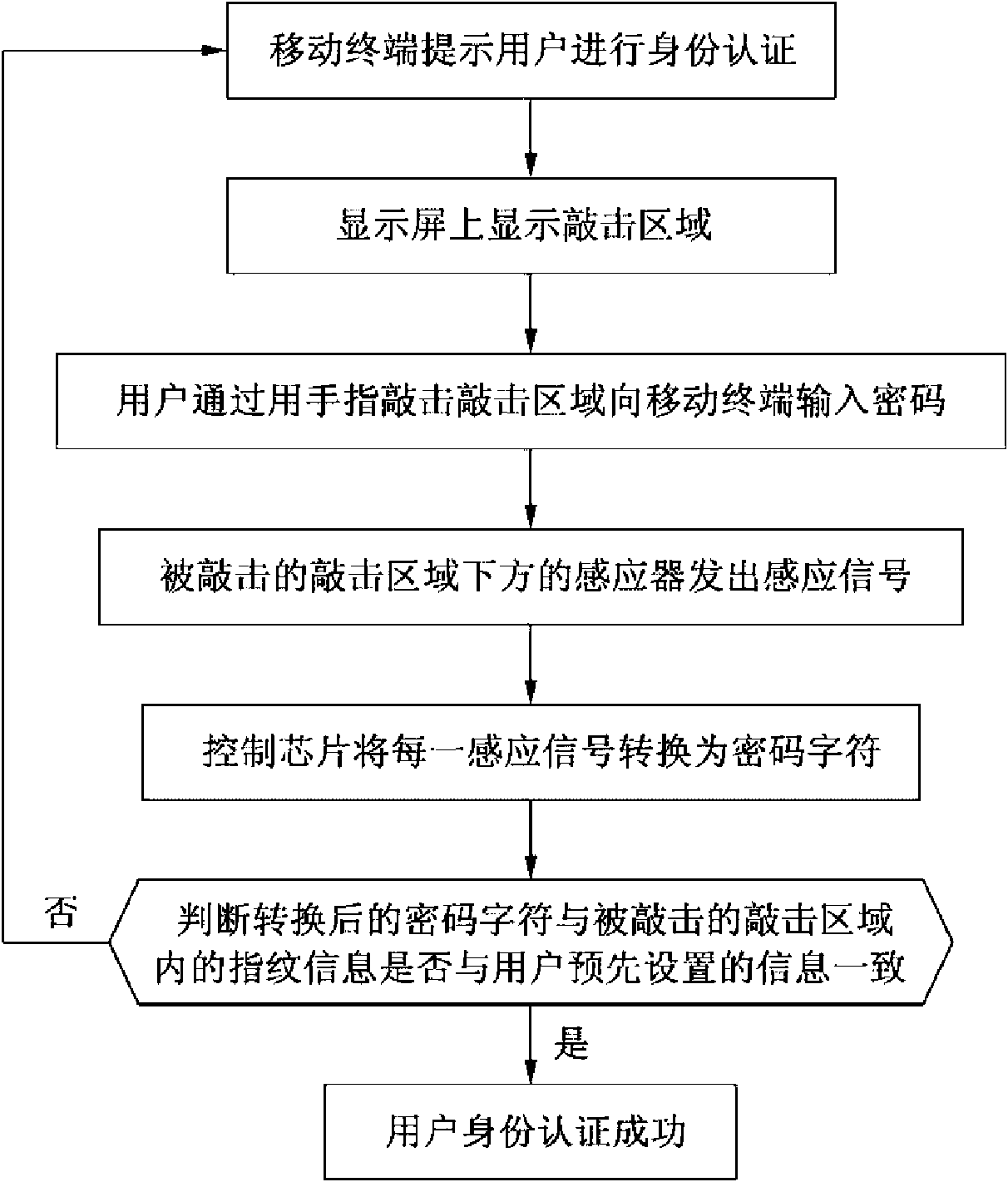
[0009] see figure 1 , figure 1 A schematic diagram of a mobile phone 10 for realizing the mobile terminal identity authentication method of the present invention, the mobile phone 10 has a display screen 11, and the display screen 11 can display five oval fingerprint-shaped knocking areas 12, 13, 14, 15, 16 , and the five tapping areas 12, 13, 14, 15, 16 are arranged in an arc according to the shape of the finger arrangement, and a sensor that can sense the user's fingers tapping on the tapping area is arranged directly below each tapping area A control chip is also installed in the mobile phone 10, and the control chip can set the tapping area and the different characters of the user password such as numbers or letters in sequence, and receive the information sent by the sensor under each tapped tapping area. Signals are sensed and converted into corresponding characters such as numbers or letters.
[0010] Assuming that the identity authentication password set by the user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com