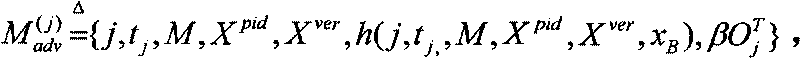Safe and effective method for dynamically updating wireless sensor network program
A wireless sensor and program update technology, applied in wireless communication, network topology, security devices, etc., can solve the problem of no wireless sensor network program dynamic update method, etc., to achieve the effect of resisting wormhole attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The relevant technical terms are as follows:
[0019] M program
[0020] x pid Identifier of program M
[0021] x VER Version of program M
[0022] h one-way hash function
[0023] XOR operation
[0024] A·B The dot product of matrix A and matrix B
[0025] A T Transpose of matrix A
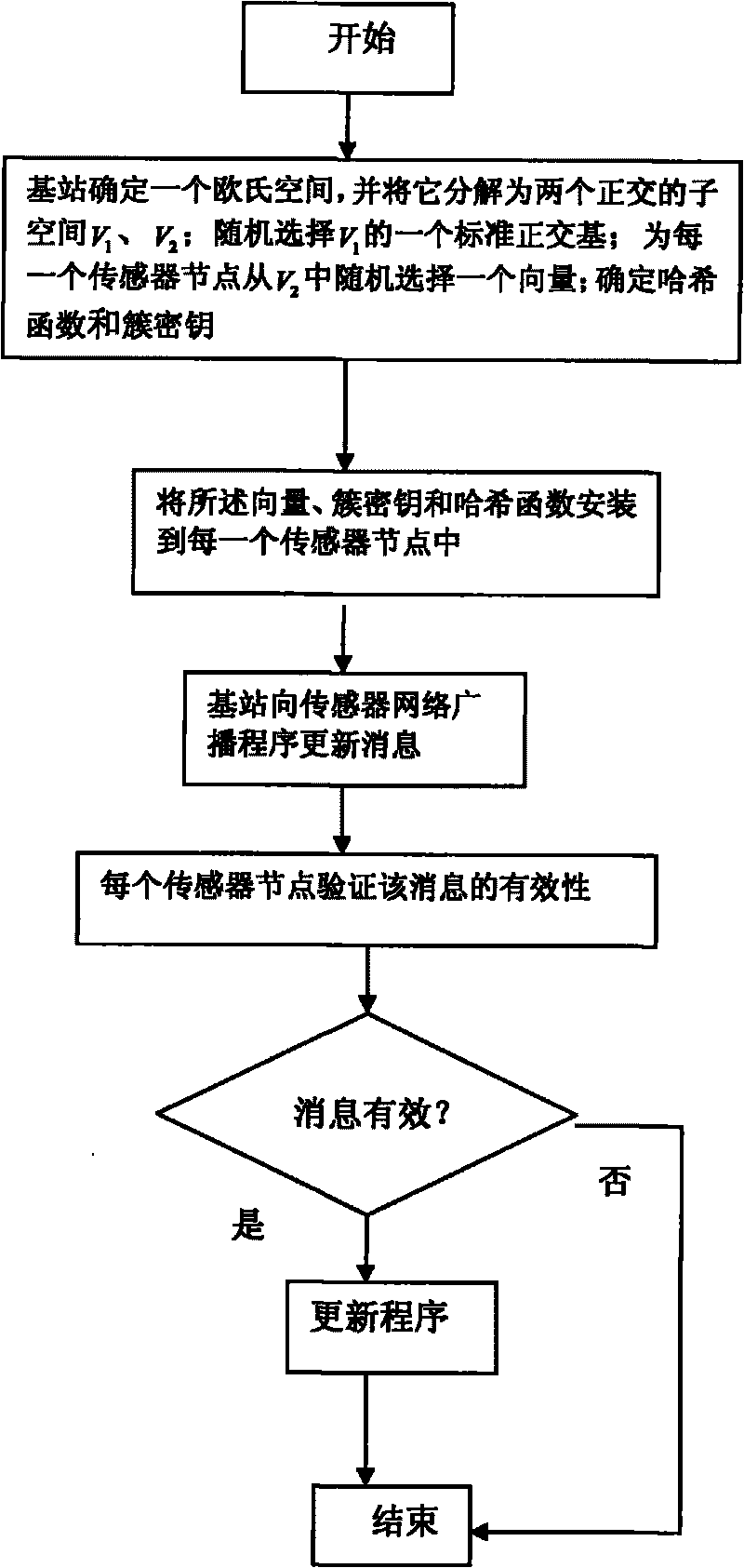
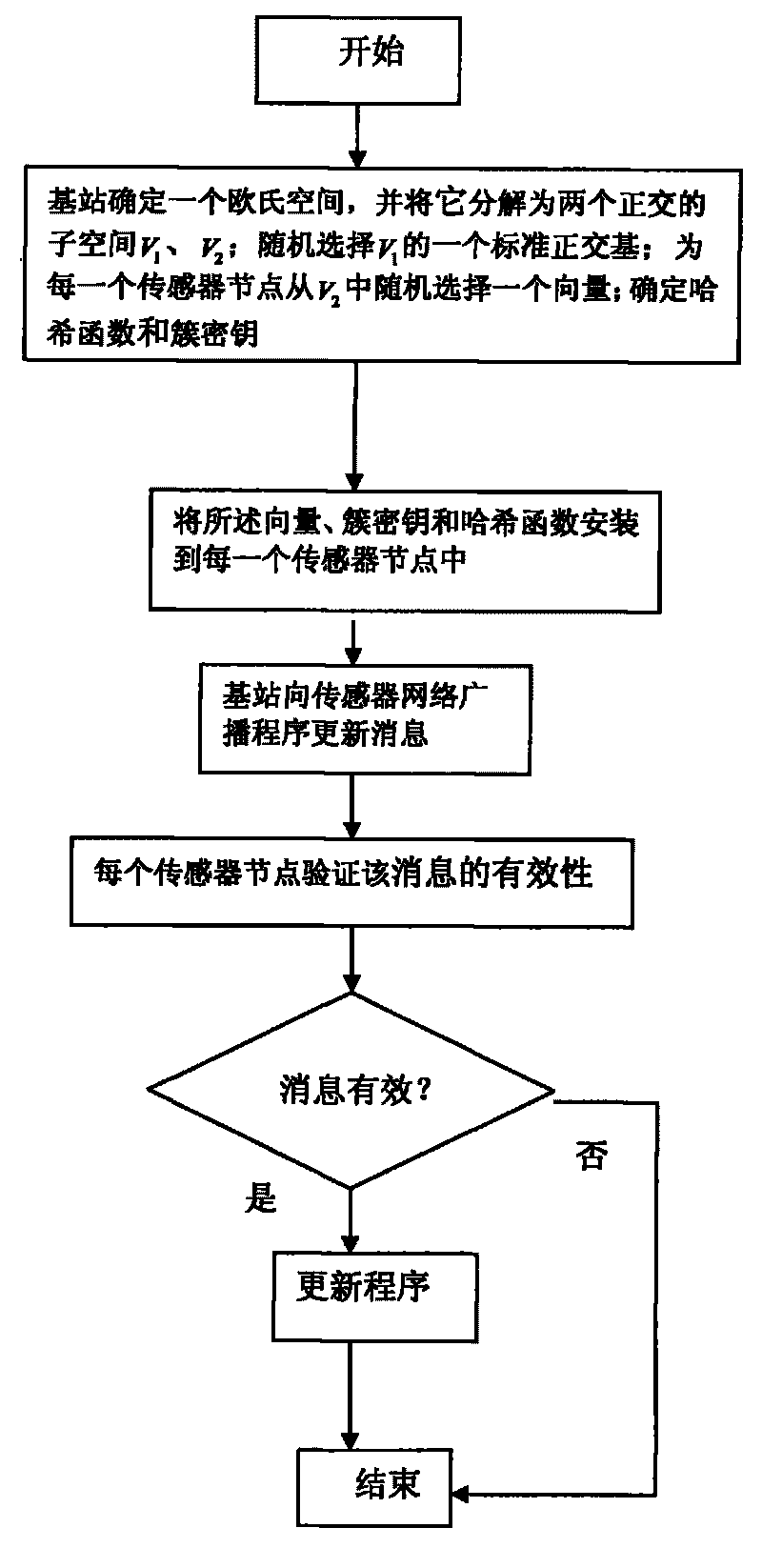
[0026] A. Before the deployment of sensor nodes, the base station selects an n-dimensional Euclidean space V, and decomposes V into two orthogonal first subspaces V 1 and the second subspace V 2 , where V 1 is k-dimensional, V 2 is n-k dimension. The base station then randomly selects V 1 An orthonormal basis {Q 1 , Q 2 ,...,Q k}; and choose a vector C for each sensor node i i , i=1, 2K, k, where C i is of V 2 Elements. The base station determines a hash function, and then selects the same m-bit random number x for all sensor nodes B As a cluster key, m should be large enough, for example 256, that is to say x B is a random number with high information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com