Method for judging identity based on keyboard-mouse crossed certification
A technology of cross-certification and judgment method, applied in the fields of digital data certification, instruments, electronic digital data processing, etc., can solve problems such as misjudgment of legal user identity, improve fault tolerance, reduce uncertainty, widen security and applicability sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described in detail below with reference to the accompanying drawings and examples of implementations.
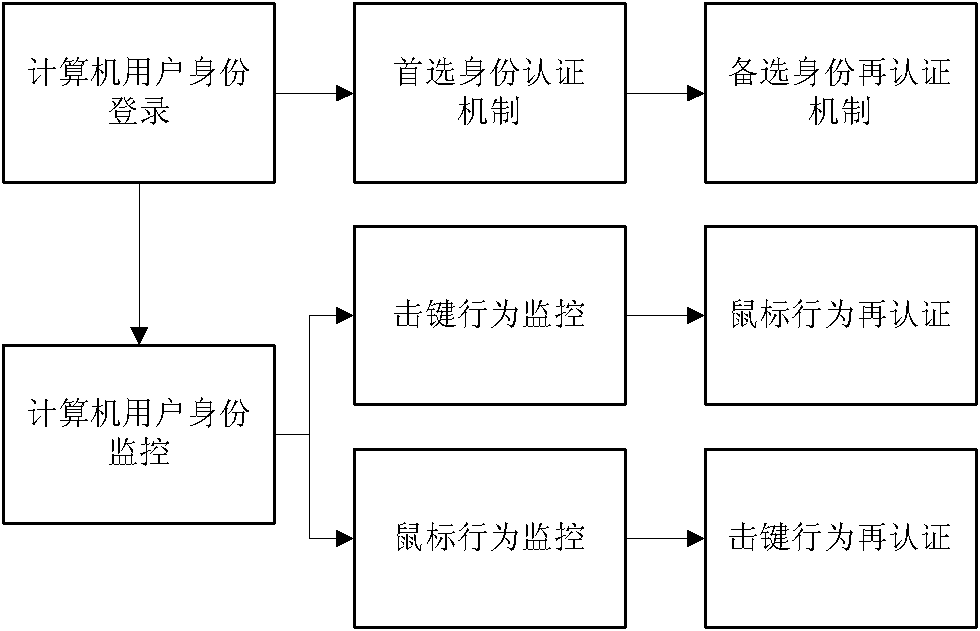
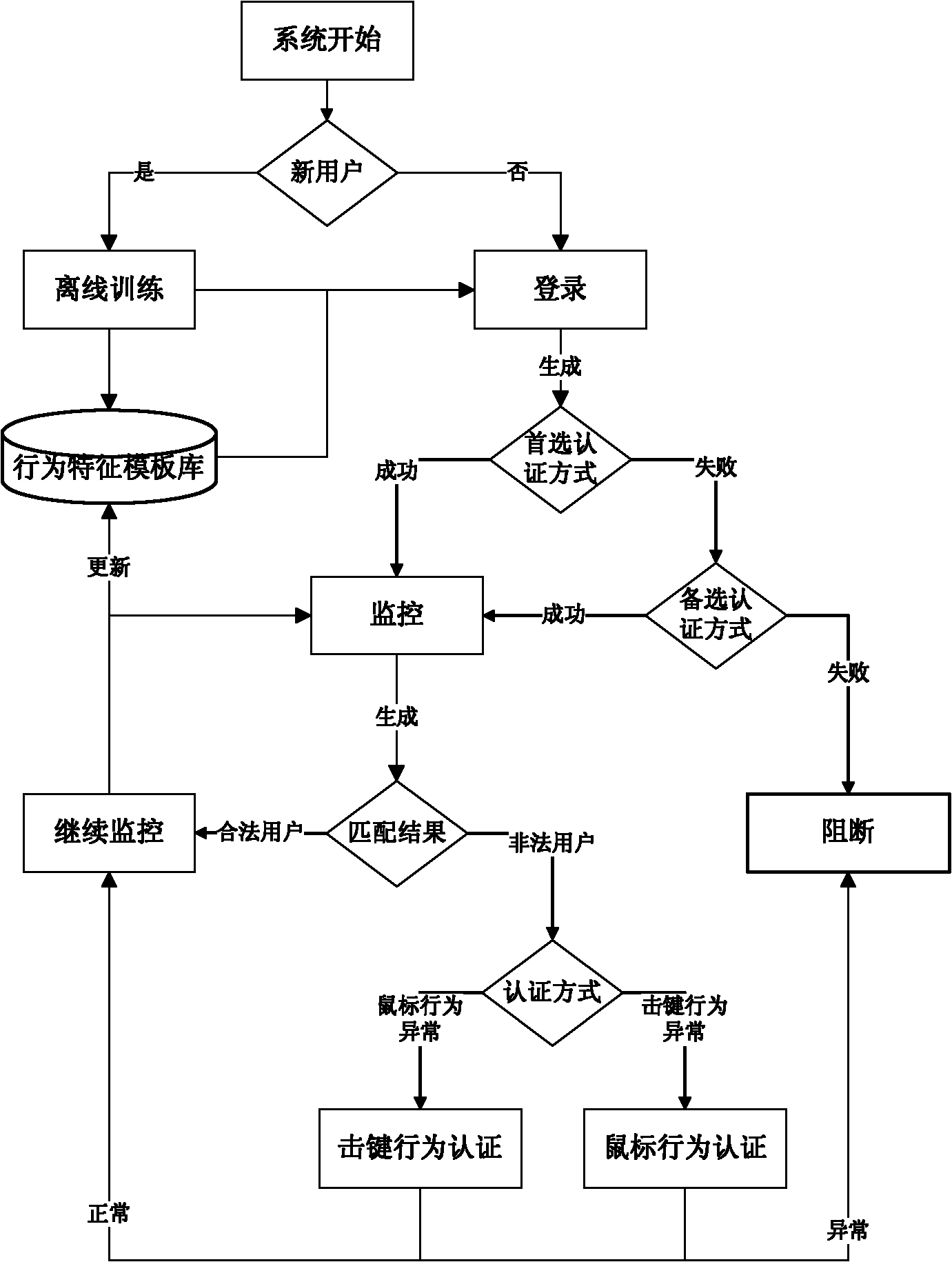
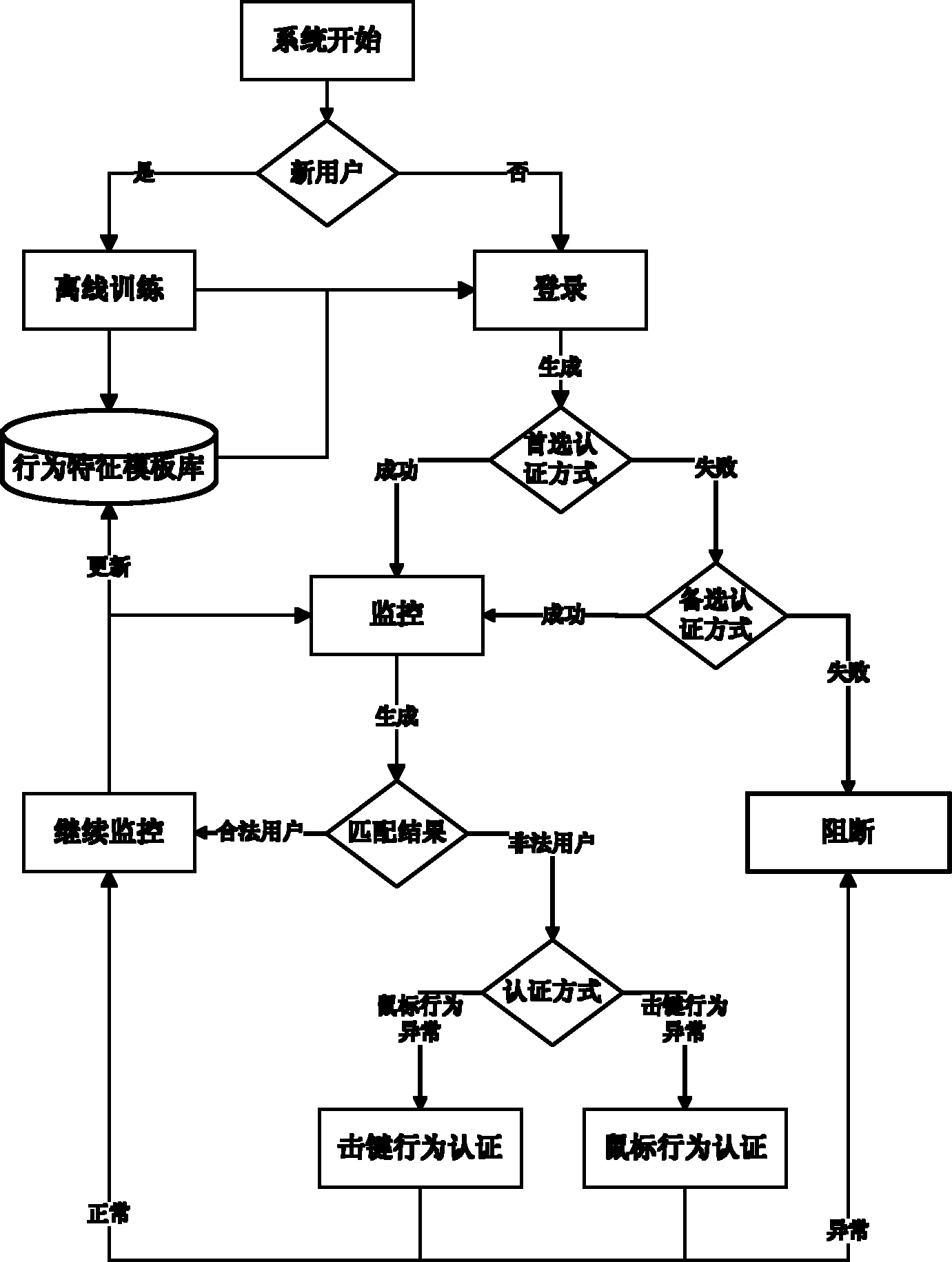
[0023] system structure
[0024] see figure 1 , the present invention monitors the user identity based on the computer operation behavior (keystroke and mouse behavior), and combines the keystroke behavior authentication with the mouse behavior authentication by using the cross-certification method. In the process of identity login for computer users, keystroke behavior authentication or mouse behavior authentication is randomly selected as the preferred mechanism or alternative mechanism for identity authentication. When the preferred identity authentication mechanism is successfully authenticated, the user passes identity authentication; When the mechanism authentication fails, the alternative authentication mechanism is used to re-authenticate the user's identity. If the authentication succeeds, the user passes the identity a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com