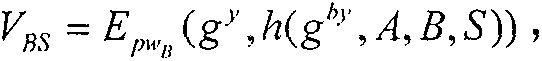Password-based three-party key exchange method
A key exchange and password technology, which is applied in the field of communication security, can solve problems such as undetectable dictionary attacks, impersonation attacks, and inability to resist man-in-the-middle attacks, and achieve perfect forward security and resist various attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
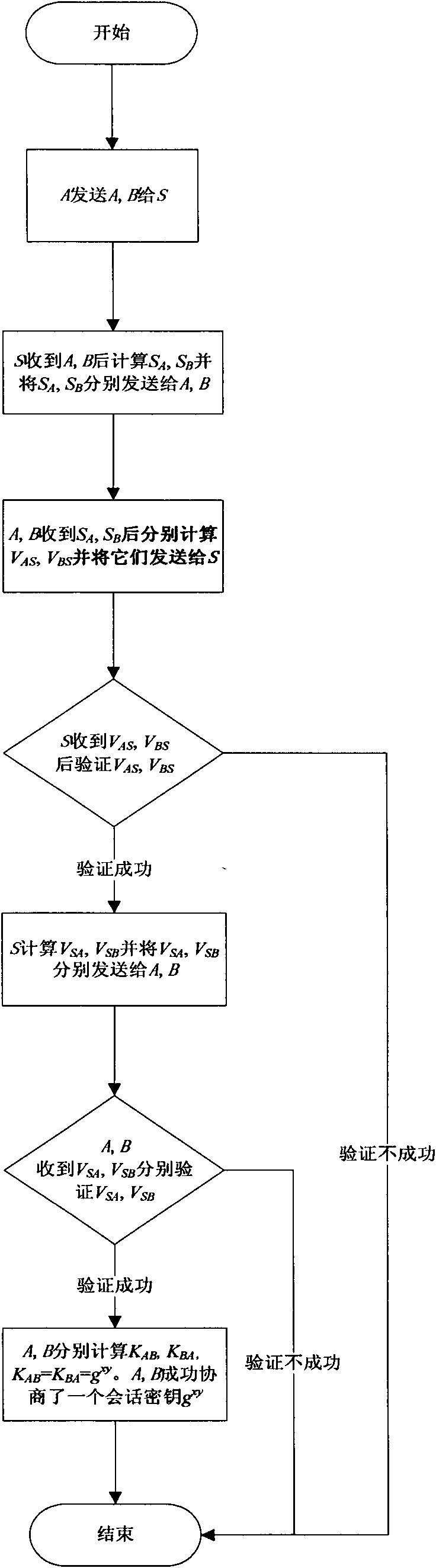
[0024] Below, in conjunction with accompanying drawing, the method of the present invention is described in detail, wherein adopt symbol:
[0025] A, B represent the two clients who need to negotiate keys in the agreement
[0026] S stands for trusted third-party server
[0027] pw A Indicates the password shared by A and S
[0028] pw B Indicates the password shared by B and S
[0029] Z p Represents the set of residual classes modulo p
[0030] a∈ R Z p * Indicates that a is randomly selected from the multiplicative group modulo p
[0031] (G, g, p) represents the finite cyclic group G, g is Z p Generator of , p is a large prime number
[0032] h() is a {0, 1} * → Z p-1 hash function
[0033] E. K (M), D K (M) respectively represent the symmetric encryption and symmetric decryption of M with the key K
[0034] For brevity, "mod p" is omitted from the protocol description
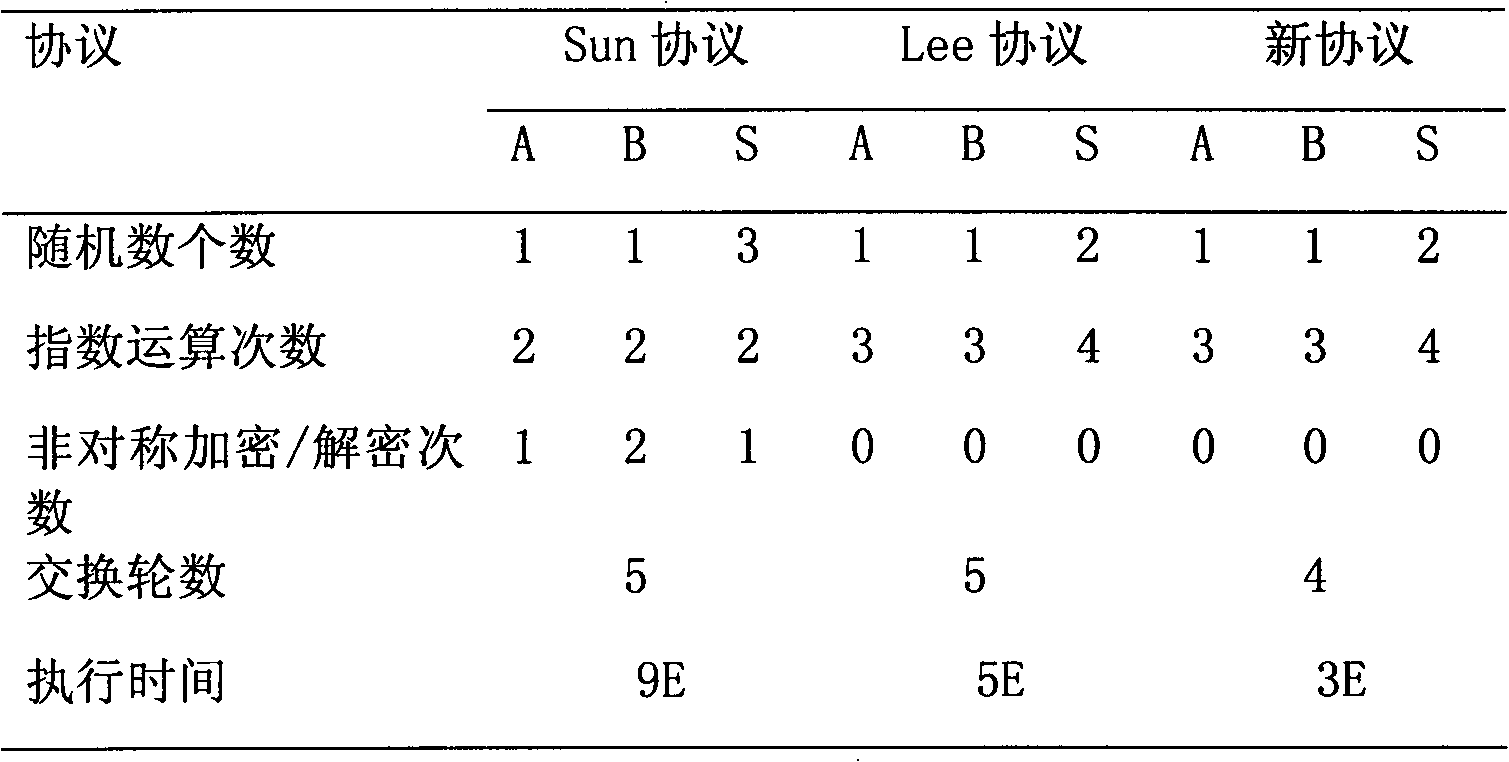
[0035] The password-based three-party key exchange method of the present invention is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com