Key management mechanism
A key management and key technology, applied in key distribution, can solve the problem of inability to solve the security of cryptographic device key management, the use of device keys cannot meet customer requirements, etc., to ensure safe use and ensure safe management. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
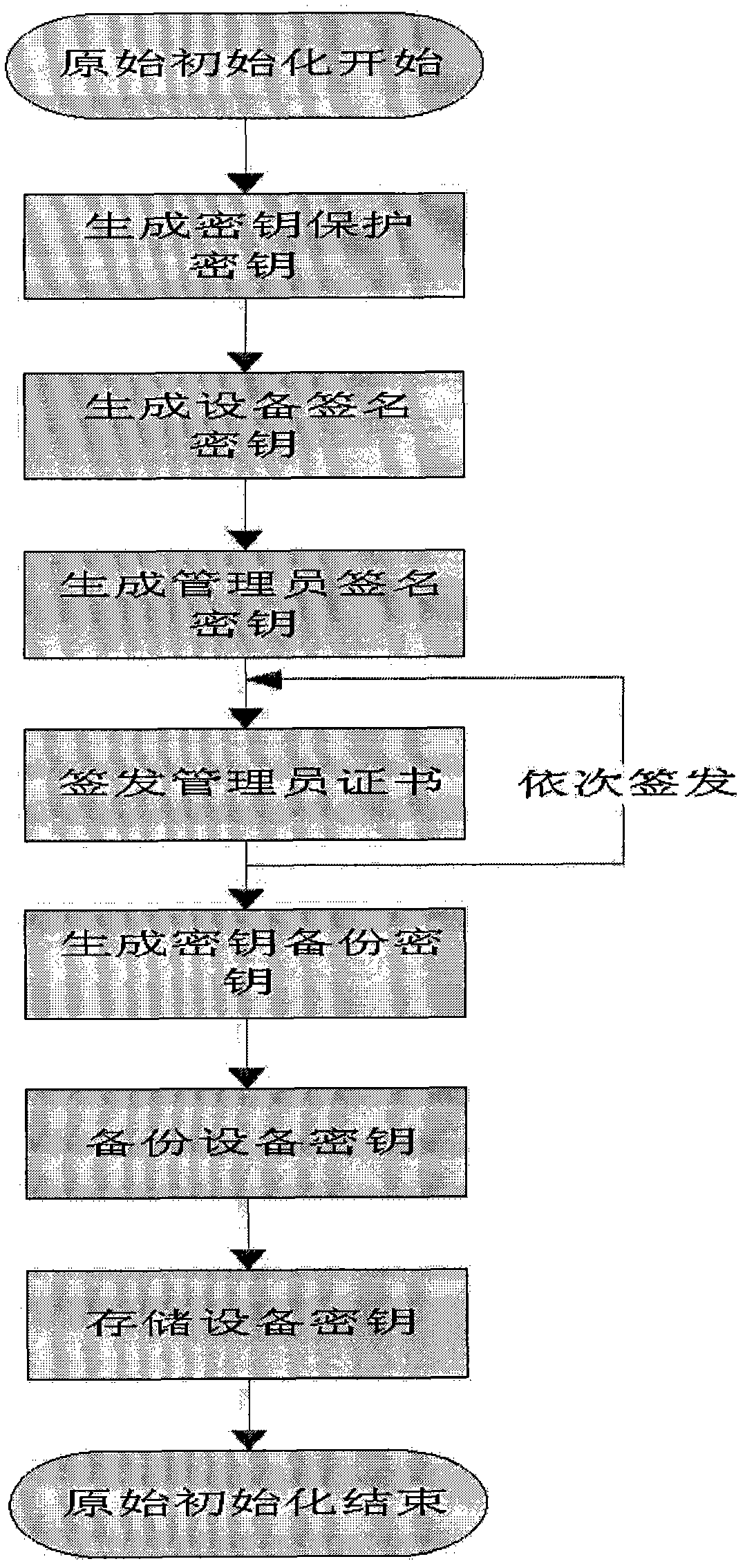
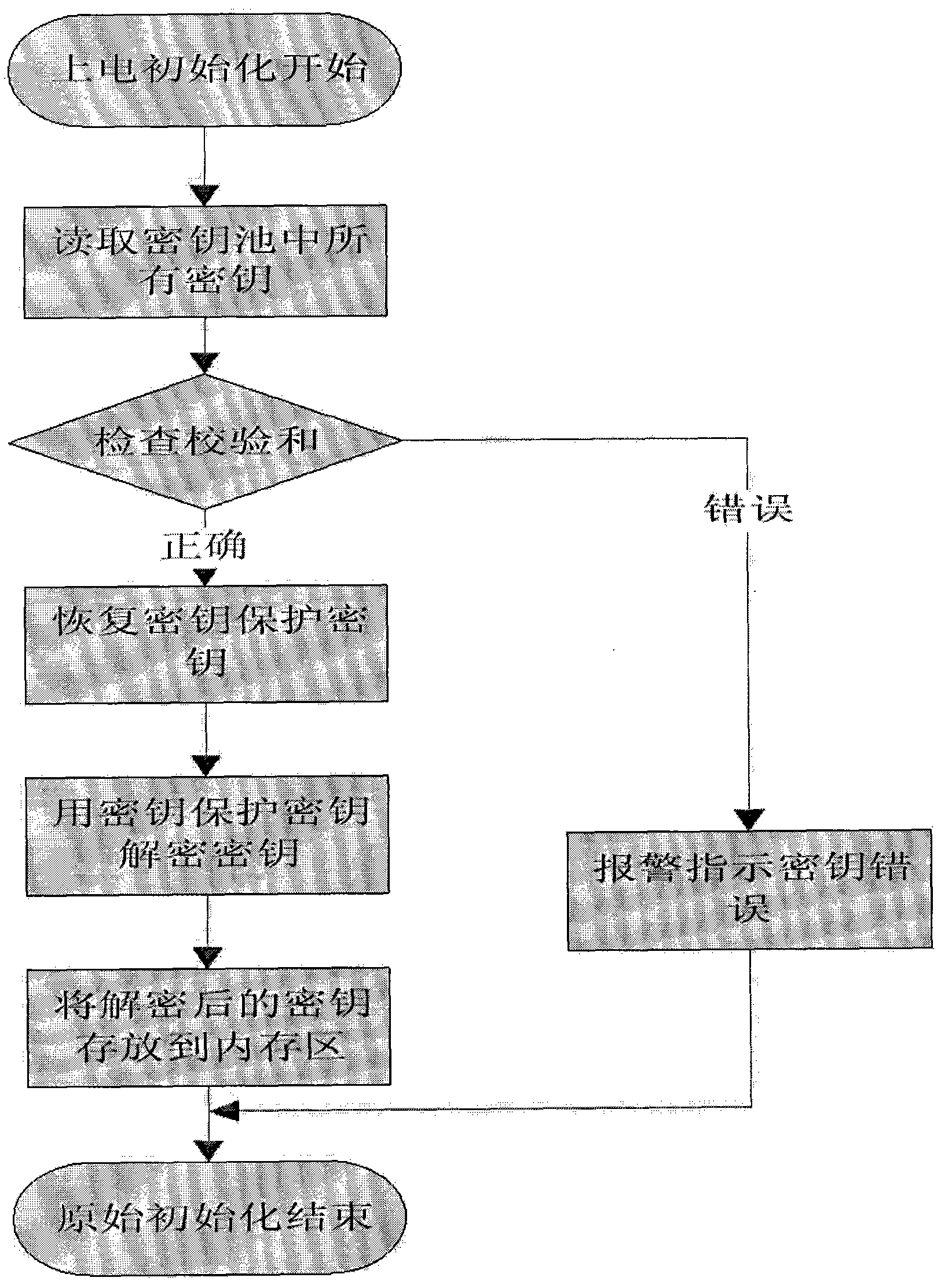
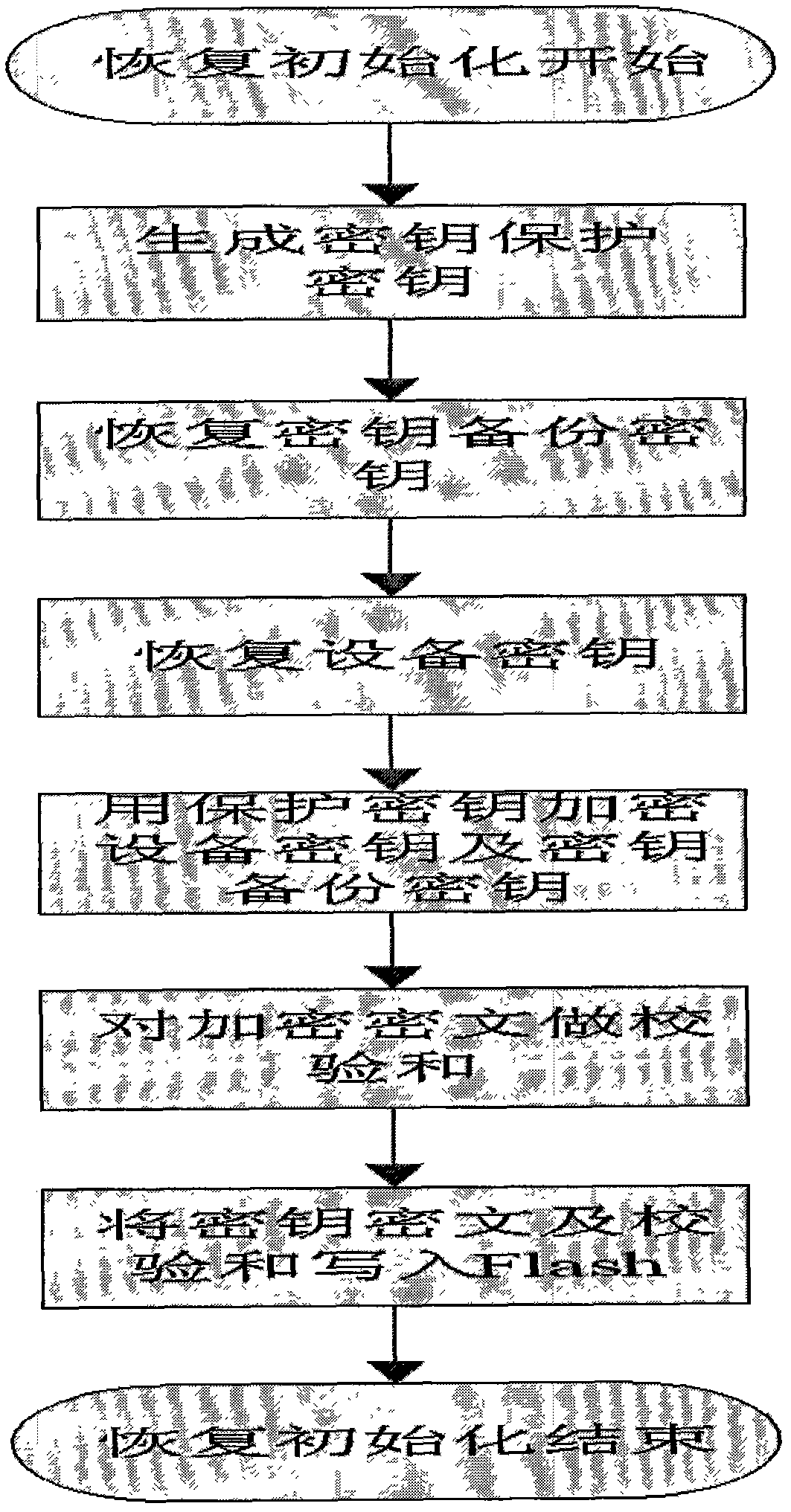
[0028] Key management mechanisms such as figure 1 a. figure 2 a and image 3 As shown in a, the steps are as follows:
[0029] Key management mechanism, the steps of the key management are as follows:
[0030] The first step: Initialize the cryptographic device in the initial state, that is, clear all keys in the key storage area of the cryptographic device, generate two 128-bit symmetric keys called component 1 and component 2, and convert component 1 to Stored in the key storage area of the cryptographic device, component 2 is temporarily stored in the memory;
[0031] The second step: regenerate the device signing key, that is, generate a pair of public and private keys as the signing key of the device and store it in the signing key storage area of the key, copy the device signing key to the device encryption key storage area, Put the cryptographic device in the ready state;
[0032] Step 3: Regenerate the administrator’s signature key, that is, generate a pair...
Embodiment 2
[0043] According to the figure below, some characteristics and changing steps of the key are described in detail to ensure the safe management of the key. Through various initializations of the key, the initialization method and process are explained to ensure the safe use of the key, so as to solve the problem of cryptographic equipment in key management. And the problem of achieving safety and reliability in use.
[0044] 1. Key generation and storage:
[0045] 1. Device key: the signature key pair is generated by the cryptographic device during the original initialization, and the cryptographic device is in the ready state after the key is generated. In this state, you can export its public key to apply for a certificate from a certificate authority at any time. The device encryption key pair is generated by an external key management center, and its private key is protected by a device signature public key as a digital envelope, which can be downloaded to the encryption d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com