Safe positioning method of wireless sensor network
A wireless sensor and network security technology, applied in security devices, network topology, wireless communication, etc., can solve problems such as increased hardware cost, implementation complexity, large impact, collusion attacks, etc., to extend the network life cycle and save energy Overhead, the effect of resisting collusion attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the accompanying drawings.
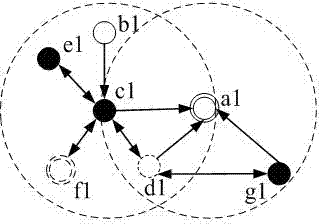
[0050] like figure 1 As shown, malicious nodes include intrusion nodes and compromised nodes. In the figure, the double-headed arrows represent the interaction between malicious nodes, and the one-way arrows represent the transmission of information. The intrusion node c1 can compromise the legitimate nodes d1 and f1 within its communication range, making them compromised nodes with the same malicious behavior, that is, randomly tampering with sent or forwarded data packets, or further compromising other legitimate nodes. If the compromised anchor node d1, the intrusion node c1 and the intrusion node g1 send wrong positioning information respectively, or the intrusion node c1 tampers with the positioning information from the legitimate node b1, then the sensor node a1 will not be able to complete accurate positioning. It can be seen that the collusion attack will seri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com