Method for generating a cipher-based message authentication code
A message authentication code and message technology, applied in the field of generating password-based message authentication code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] already discussed in the background figure 1 and 2 .
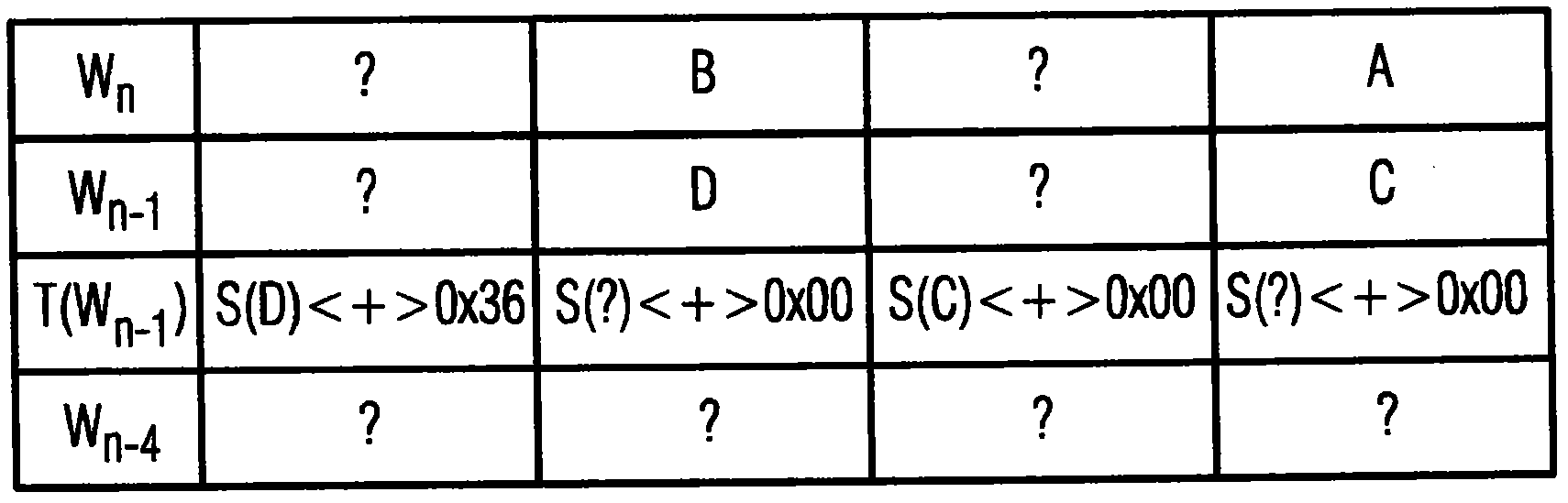
[0041] Figure 3-5 A potential differential power attack on a CMAC that has been computed according to the method of the present invention is shown.
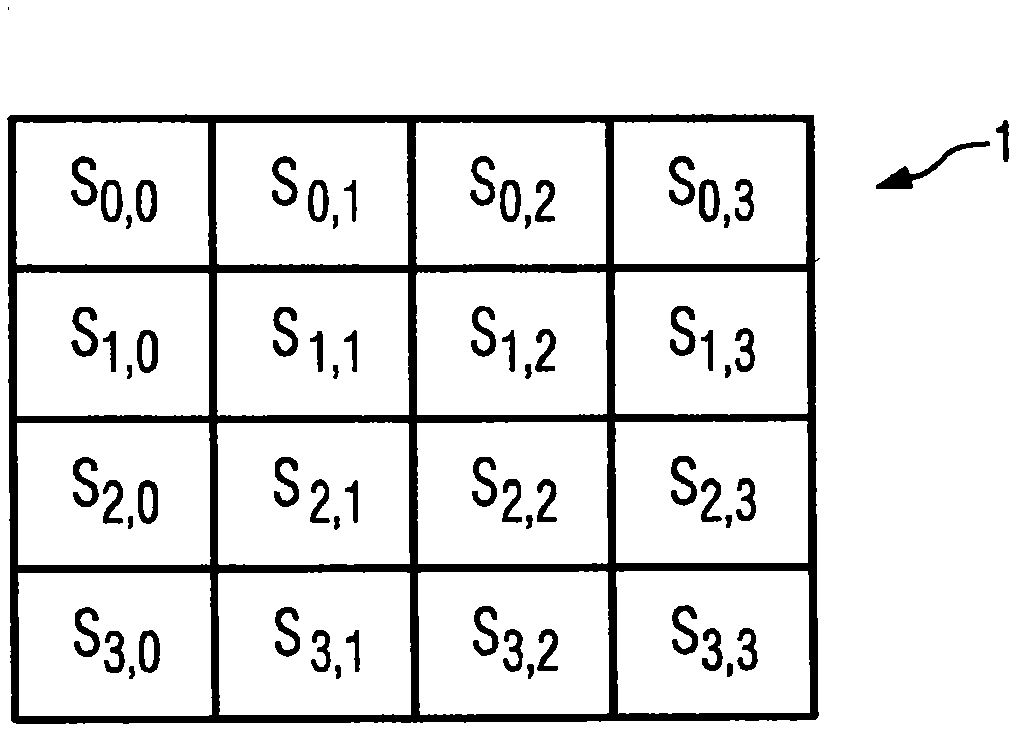
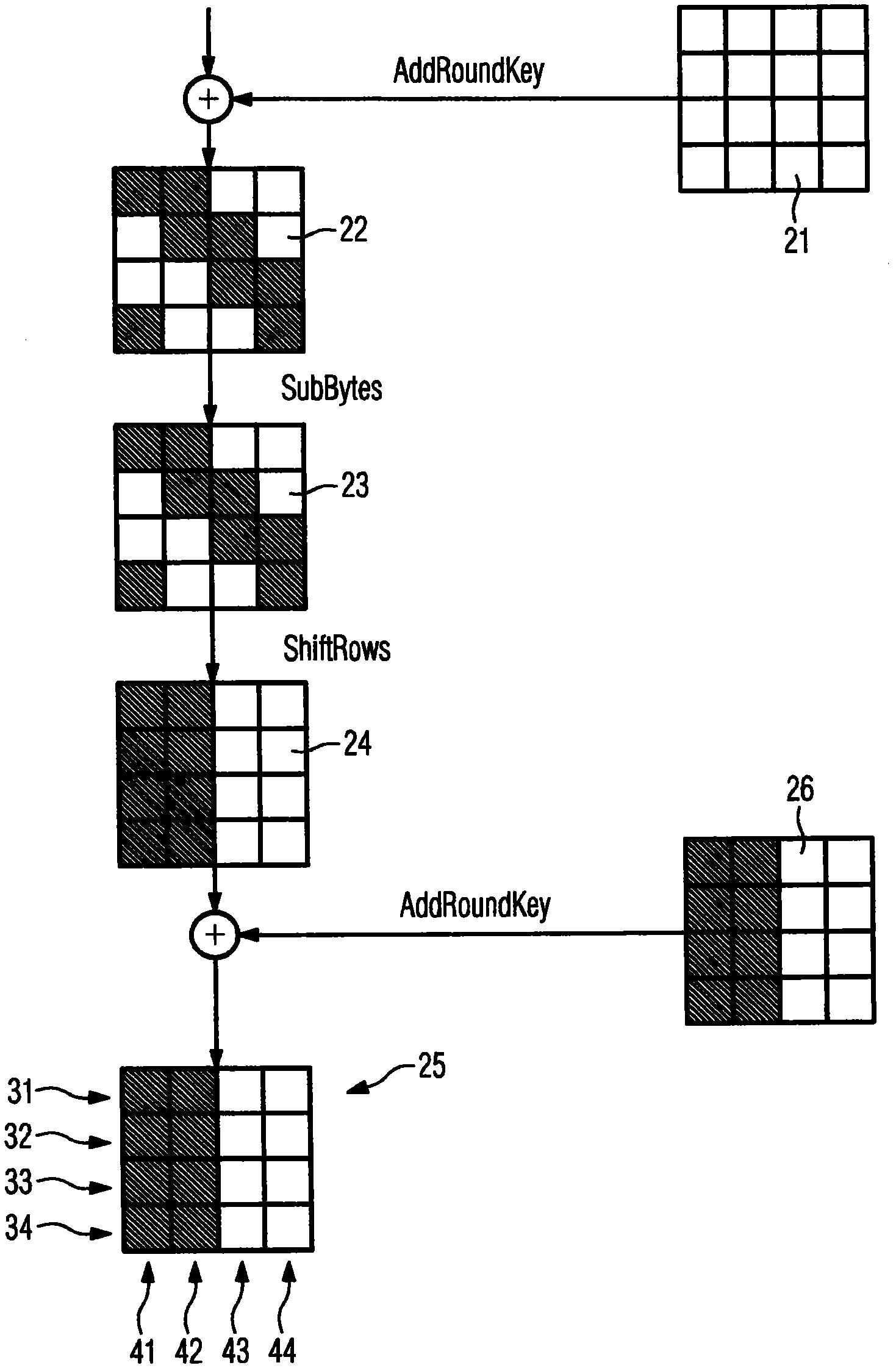
[0042] For the example embodiment, the state array 25 used to compute the CMAC is obtained as described in the Background. The state array 25 consists of four rows 31-34 and four columns 41-44. Additionally, the messages on which the state array 25 is based are as figure 1 The single-block message represented by state array 1 is shown.
[0043] For the example embodiment, the CMAC is computed by reserving the bytes 29, 30 of two of the four rows 31-34 of the state array 25. Bytes from the remaining lines are discarded. For the example shown, keep Figure 3-5 Bytes 29, 30 of lines 32 and 34 shown shaded in , and the remaining bytes of lines 31, 33 are discarded. Therefore, the even-numbered bytes of the state array 25 are reserved for computing the CMAC of thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com