Group message interaction realization method and system
A group information and group message technology, applied in the network field, can solve the problems of data information loss, inability to authenticate and control, time-consuming and labor-intensive, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
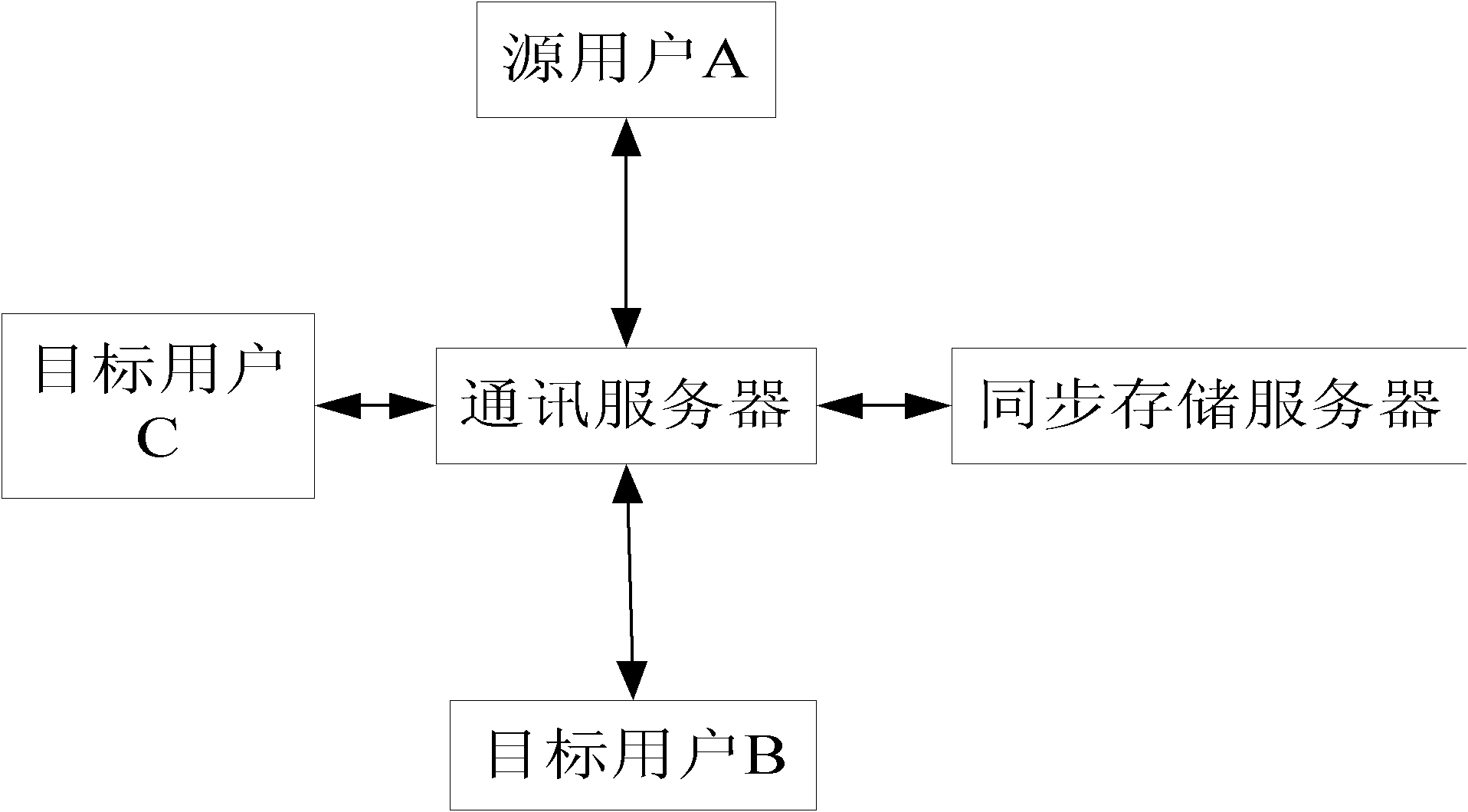
[0071] User A logs in to the webpage and obtains the ID of each group that the user joins;
[0072] The webpage loads the flash plug-in, the flash plug-in connects to the communication server, and the flash plug-in starts to monitor messages;
[0073] The Flash plug-in sends all group IDs and user accounts to the synchronous storage server through the communication server;
[0074] After the synchronous storage server receives the message, it searches out the member hash table corresponding to each group ID from the group hash table, and adds the user account to the member hash table corresponding to each group ID;
[0075] The source user sends a group message command to the communication server, and the communication server performs authentication after receiving the group message command sent by the source user: source user identity authentication, data command authority authentication (whether the source user has the authority to send group message commands) , authenticat...
Embodiment 2
[0080] User A logs in to the webpage and obtains the ID of each group that the user joins;
[0081] The webpage loads the flash plug-in, the flash plug-in connects to the communication server, and the flash plug-in starts to monitor messages;
[0082] The Flash plug-in sends all group IDs and user accounts to the communication server;
[0083] After the communication server receives the message, it searches out the member hash table corresponding to each group ID from the group hash table, and adds the user account to the member hash table corresponding to each group ID;
[0084] The source user sends a group message command to the communication server, and the communication server performs authentication after receiving the group message command sent by the source user: source user identity authentication, data command authority authentication (whether the source user has the authority to send group message commands) , authentication of the target authority of the source use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com