Assess method and system for completion of call to busy subscriber service based on identity identification
A technology for identification and service access, applied in transmission systems, subscriber special services, communication supplementary services, etc., can solve problems affecting normal users' normal calls, adverse call fairness, etc., to eliminate priority call access rights, reflect fairness effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
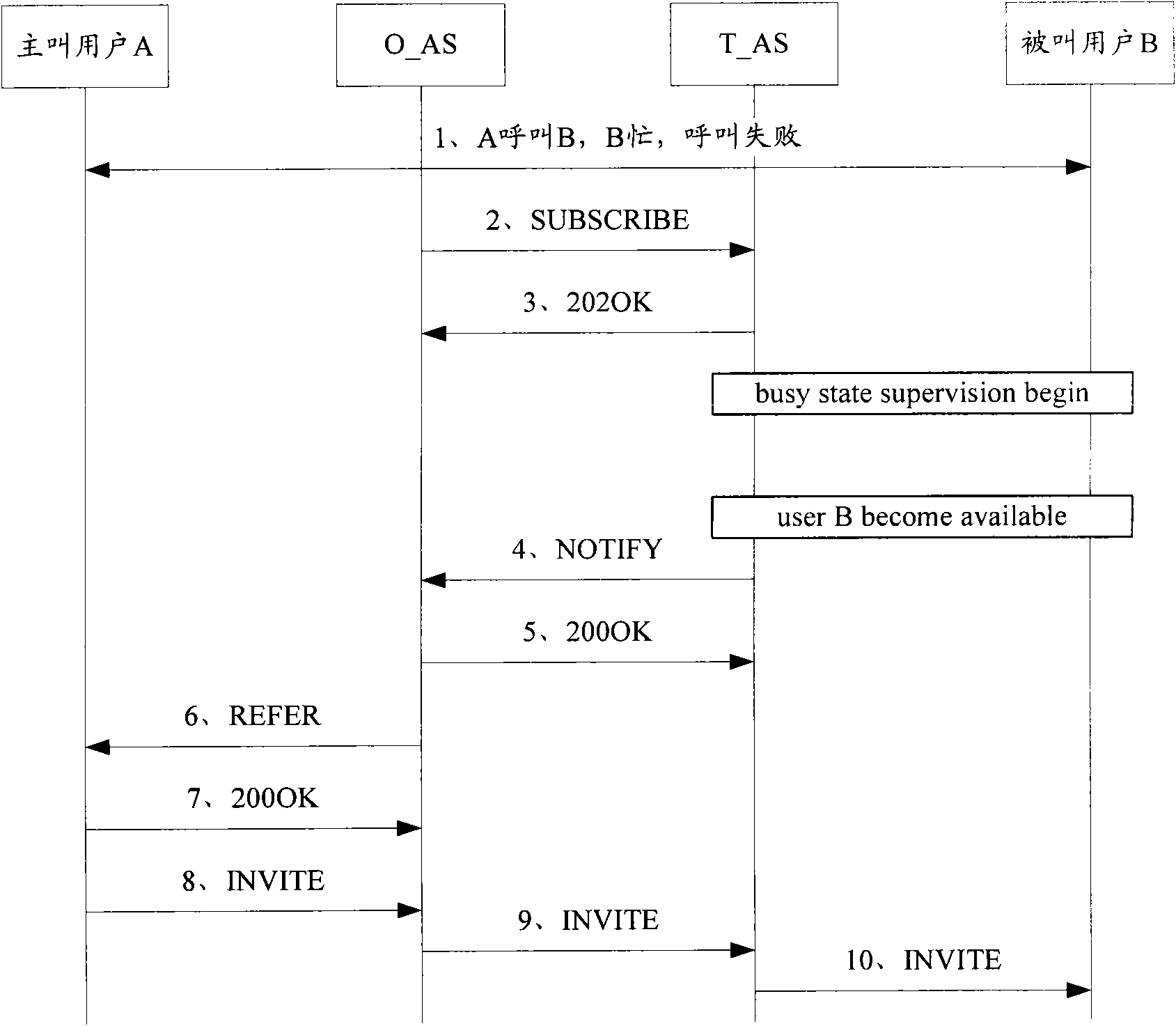
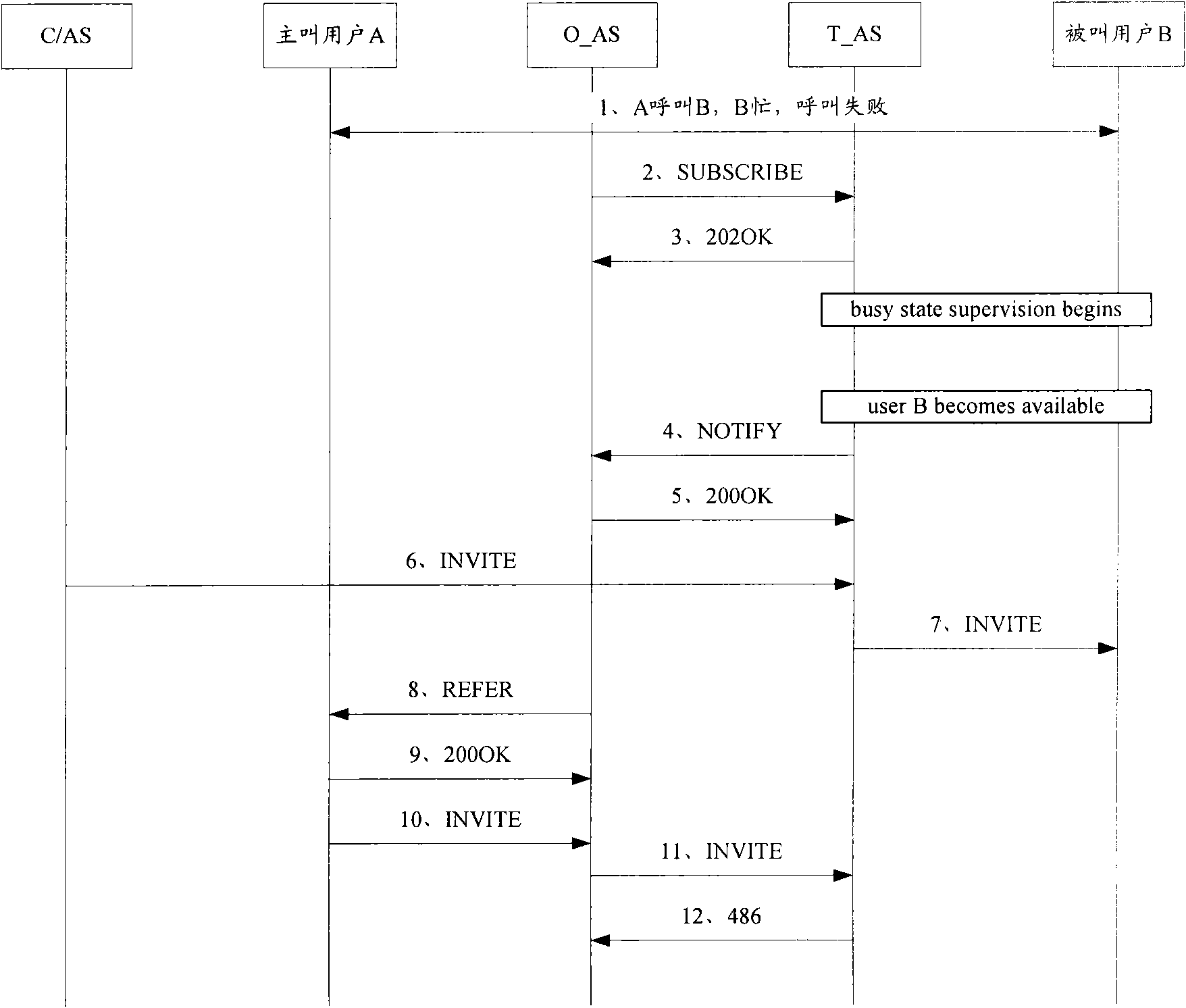
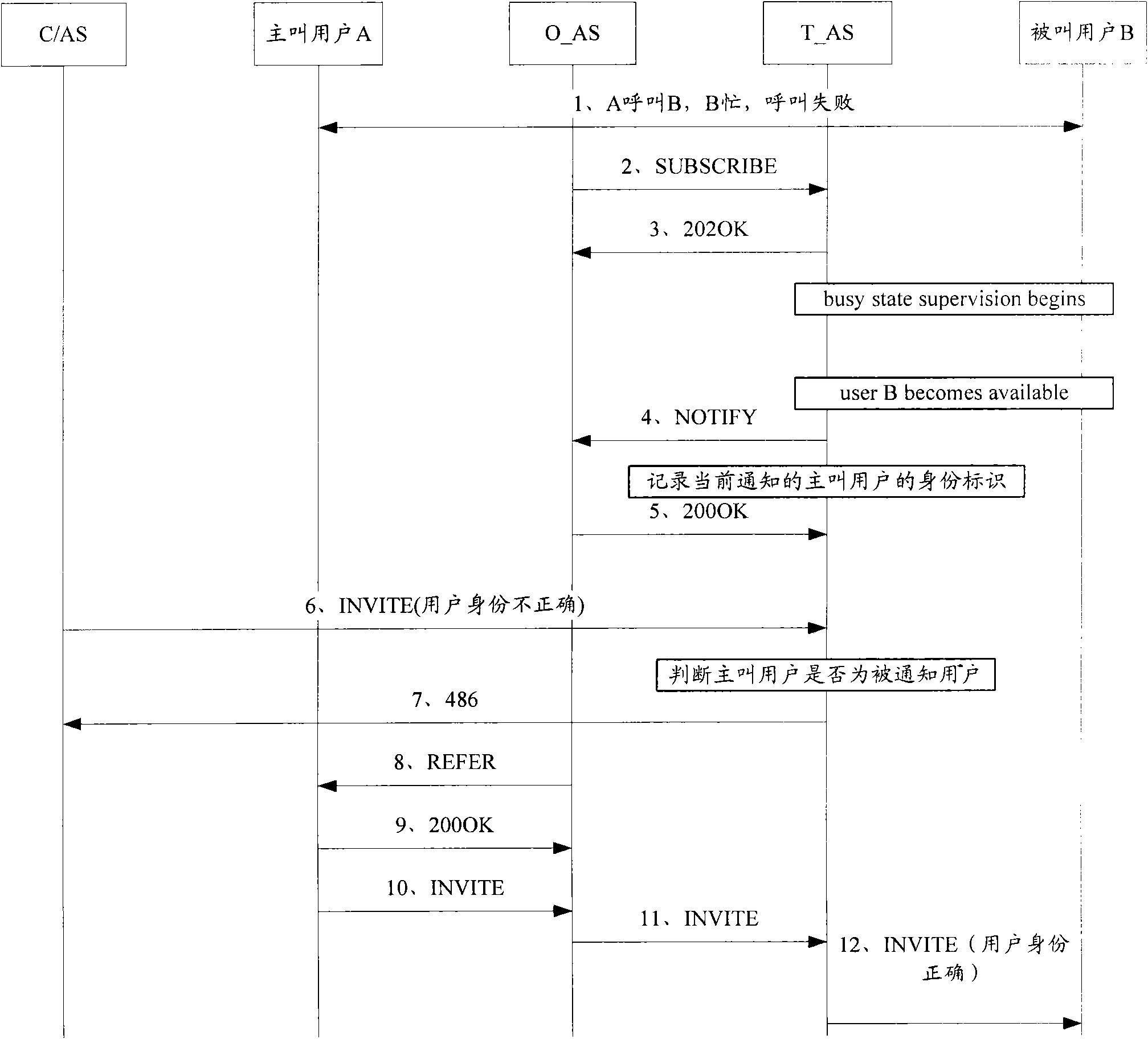
[0075] The basic idea of the present invention is: set the identity verification mechanism to the calling user in the application server of the called side, verify the user identity carried in the call request of the call back initiated by the calling user, and the calling user who passes the identity verification Only when the incoming call is allowed, otherwise, the calling user will be denied the incoming call. The invention fully guarantees the call access sequence of the calling user to the called user, embodies the fairness of call access, and eliminates the preferential call access right of malicious users.
[0076] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail by citing the following embodiments and referring to the accompanying drawings.
[0077] image 3 It is a flow chart of Embodiment 1 of the method for accessing the busy callback service based on identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com