Method for realizing electronic mail credibility management on the basis of anti-fraud control logic unit
A technology for controlling logic and e-mail, applied in electrical components, digital transmission systems, transmission systems, etc., can solve problems such as spam flooding, interference with users' daily life and work, and economic losses.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
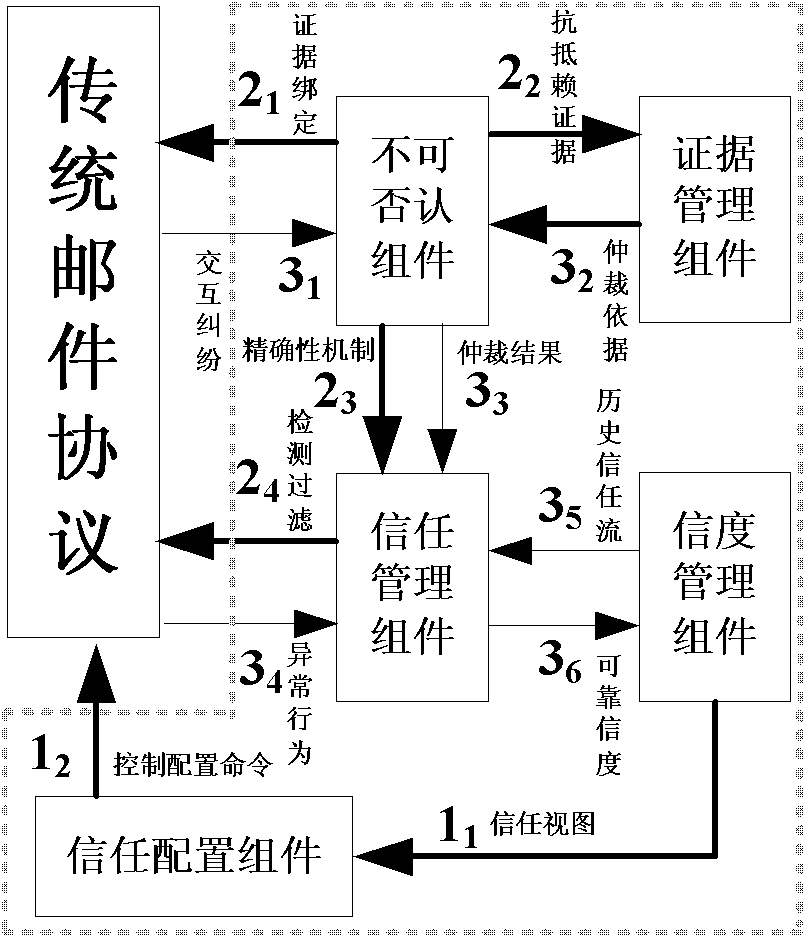
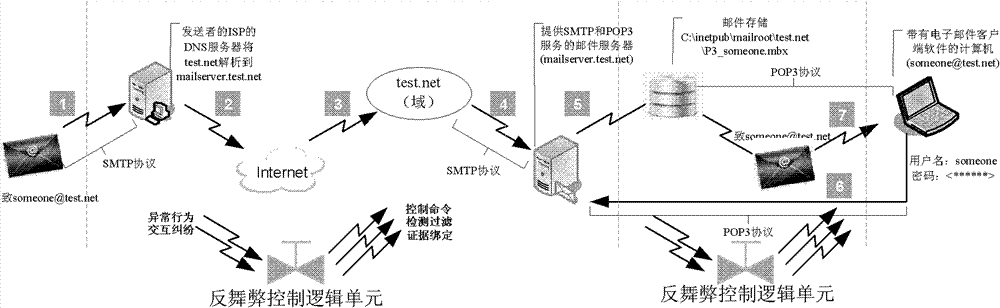
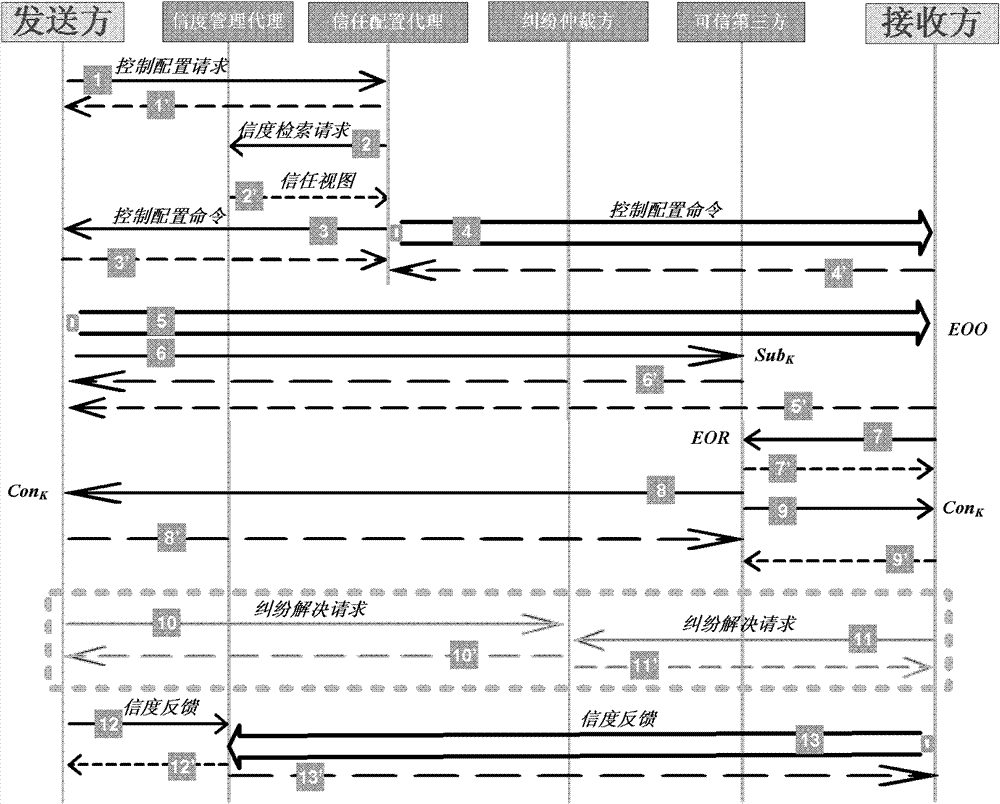
[0084] Embodiment 1: A method for implementing trusted email management such as figure 1 As shown, it does not overthrow any e-mail protocol structure widely used in the existing network system to rebuild a new type of e-mail protocol structure, but adds an anti-fraud control logic unit on this basis, which includes credibility management, trust Configuration, evidence management, non-repudiation and trust management are five components, among which the credibility management component provides the current credibility of the target entity to the trust configuration component in the form of trust view, and provides the target entity credibility to the trust management component in the form of historical trust flow Historical changes, and the reliability of the target entity that accepts the feedback from the trust management component; the trust configuration component implements trust decisions based on the trust view, and forms an email interaction control configuration comma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com