Secure clustering routing management method for wireless sensor network
A wireless sensor and network security technology, applied in network topology, security devices, wireless communication, etc., can solve problems such as low success rate, increased network load, and single type of malicious nodes, so as to resist malicious attacks and ensure secure communication Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
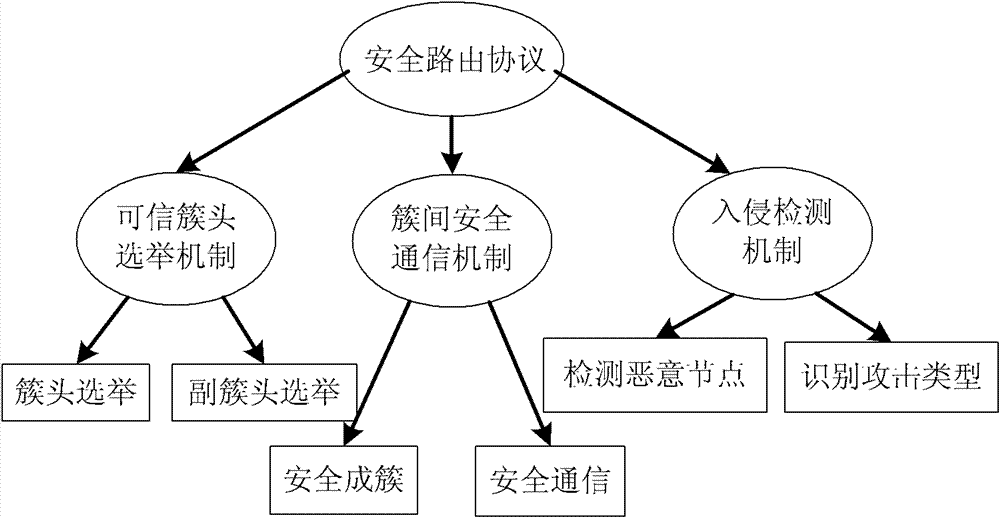
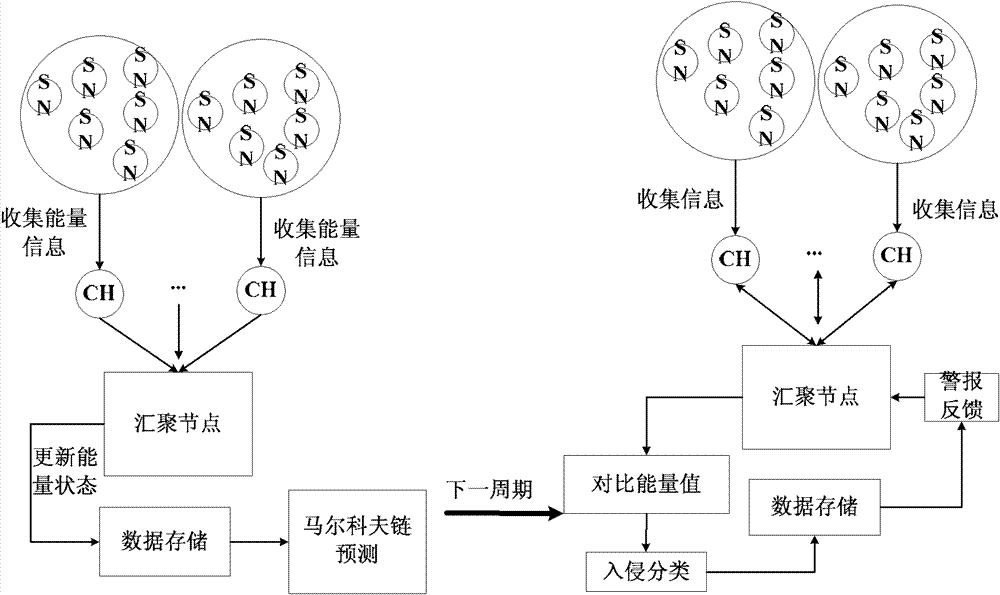
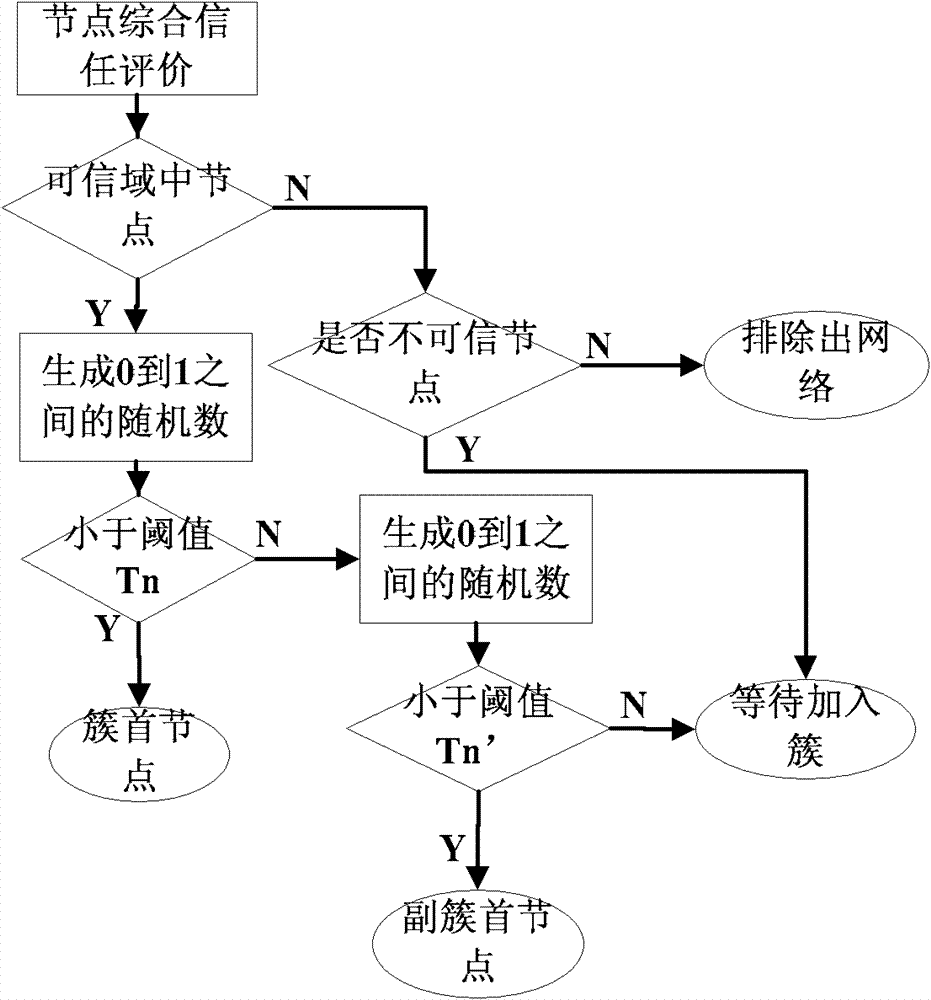
[0053] Such as figure 1 The overall framework of the safety clustering routing management method with energy prediction characteristics proposed by the present invention is based on the classic clustering routing protocol LEACH, so the working status of the protocol is the same as that of the LEACH protocol after the clustering is established. basically the same. The outstanding innovation points in the agreement are mainly divided into three parts in the figure to illustrate.
[0054] The first is to establish an intrusion detection mechanism with energy prediction capabilities to identify malicious nodes that have denial of service attacks. If the energy consumption of a certain node is predicted at a certain time in the future, when the time comes, it can be judged whether the node is captured as a malicious node, and at the same time, malicious attacks can be carried out by increasing its own energy. Considering the environment of cluster routing in wireless sensor netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com